
Small businesses often face the same cyber threats as big corporations, sometimes even more. With limited IT budgets, growing digital footprints, and heavy reliance on third-party tools, many small companies unintentionally become easy targets for attackers looking for weak spots.
That’s where penetration testing for small businesses comes in. It can be summarized as a simulated cyber attack designed to test your defenses and fix issues before they’re exploited. Whether you’re running an online store, managing a financial service, or building a SaaS product, regular pentesting helps you uncover vulnerabilities, tighten your security posture, and protect your business reputation all without overspending.
What is penetration testing?
Penetration testing is a controlled cybersecurity assessment where ethical hackers attempt to exploit vulnerabilities in your network, web applications, or infrastructure, just like real attackers would.
The goal isn’t to cause harm but to reveal weaknesses and provide actionable recommendations to fix them before a real breach occurs.
Penetration testing includes:
Defining which systems or applications will be tested.
Ethical hackers using tools and manual techniques to simulate real-world attack scenarios.
Detailed reports outlining discovered vulnerabilities, their severity, and steps to remediate them.
Retesting to ensure that the vulnerabilities have been properly resolved.
Why small businesses need it
Many small business owners assume that cybercriminals only target large corporations. In reality, attackers often see smaller organizations as low-hanging fruit since they’re often less protected, easier to breach, and more likely to pay ransoms quickly.
Here are a few reasons why you should take pentesting more seriously as a small business:
Small does not mean invisible
According to Microsoft’s SMB cybersecurity research (2024), about 33% of small to medium-sized businesses experienced a cyberattack in the last year
Similarly, 53% of Canadian small businesses have experienced a cyber incident according to a 2025 survey conducted by Zensurance.
Top incident types included phishing (46%), malware (23%), fraudulent transfers (19%), ransomware (6%)*, and DDoS disruptions (6%).
Protect customer trust
A single data breach can permanently damage your reputation. 60% of small businesses close within six months of a cyberattack.
43% of cyberattacks target small businesses, (Verizon Data Breach Investigations Report, 2023) yet only 14% are prepared to defend themselves.
Losing customer data such as payment details or personal information not only erodes trust, but can also trigger expensive notification and recovery costs.
Regular penetration testing helps uncover vulnerabilities early, protecting both your customers and your brand image.
Ensure regulatory compliance
Even small businesses are required to meet compliance obligations under frameworks like PCI DSS, HIPAA, and GDPR if they handle payment or customer data.
Non-compliance penalties can reach up to €20 million (or 4% of global turnover) under GDPR.
Penetration testing provides documented proof of due diligence, which is a key requirement for many data protection regulations and industry audits.
Demonstrating compliance not only avoids fines but also builds credibility with clients and partners.
Prevent costly downtime
Average cost of a cyberattack on small business is around $255,000, with some attacks costing as much as $7 million.
Verizon’s 2024 data suggests that the average breach cost for small businesses falls between $120,000 and $1.24 million, depending on severity.
Proactive pentesting identifies potential vulnerabilities that could lead to ransomware, data theft, or service outages, saving your business from operational disruption.
Support business growth and partnerships
Many investors, enterprise clients, and government contracts now require proof of penetration testing or security certification during onboarding.
78% of SMBs fear losing business opportunities due to lack of cybersecurity measures (Connectwise).
A strong security posture can help you qualify for higher-value contracts and build confidence among stakeholders.
By implementing regular penetration tests, you not only secure your systems but also position your business as a trustworthy and compliant partner in the marketplace.
Preparedness & risk perception
Only 46% of SMBs have implemented multi-factor authentication (MFA), and just 13% require it for most accounts
60% of small business owners view cybersecurity threats as a top concern, yet only 23% say they are very prepared to handle a cyberattack.
Major challenges include lack of staff training (83%), insecure personal device use (80%), limited budget and resources, and lack of in-house cybersecurity professionals (72%). (BD Emerson)
Penetration testing vs vulnerability scanning
It’s easy to confuse penetration testing with vulnerability scanning, but they serve different purposes and provide different depths of insight.
| Aspect | Vulnerability scanning | Penetration testing |
|---|---|---|
| Purpose | Automated scan to detect known vulnerabilities. | Simulated attack to exploit and validate vulnerabilities. |
| Depth | Surface-level identification. | Deep, manual verification and exploitation. |
| Output | List of potential issues. | Detailed report with proof of exploit and remediation steps. |
| Use case | Regular maintenance and compliance checks. | Strategic security validation and risk assessment. |
In short, vulnerability scanners tell you what might be wrong, while penetration testing confirms what can actually be exploited. A mature security program uses both in tandem.
Types of penetration tests for small businesses
Different types of penetration testing provide different levels of visibility depending on your goals and the data available to testers.
Here are the most common approaches:
Black box testing
The tester has no prior knowledge of your systems, just like an external hacker. This simulates real-world attacks from the outside and helps identify weaknesses in public-facing assets such as websites, login portals, and APIs.
Black box testing makes sure that you are prepared for real-world attack scenarios.
White box testing
The tester has full access to system architecture, credentials, and source code. This allows for in-depth security validation of internal processes, APIs, and logic flaws.
White box testing is best for businesses developing custom software or managing complex internal systems.
Grey box testing
The tester has limited knowledge, such as basic credentials or system documentation. This hybrid approach helps uncover vulnerabilities that external attackers or malicious insiders could exploit.
Grey box testing shines when you need to balance realism with thorough coverage.
For most small businesses, grey box testing offers the ideal balance between realism, depth, and cost-effectiveness.
How penetration testing for small business works
While each provider may have its own process, most penetration testing engagements follow a similar lifecycle.
1. Scoping and planning
The first step is to define your testing goals, scope, and risk tolerance. This includes identifying assets to test and outlining rules of engagement to ensure business operations aren’t disrupted.
2. Reconnaissance and mapping
Ethical hackers gather intelligence about your systems such as IP addresses, open ports, or publicly exposed assets to understand your attack surface.
3. Vulnerability discovery
Next, automated scanners and manual analysis identify weaknesses such as misconfigurations, outdated software, or insecure endpoints.
4. Exploitation and privilege escalation
Testers attempt to exploit vulnerabilities to see how deep they can go. This includes accessing sensitive data, escalating privileges, or pivoting to other systems. The goal is to prove exploitability without damaging data.
5. Reporting and recommendations
After testing, you’ll receive a comprehensive report highlighting:
Vulnerabilities found and their severity
Proof-of-concept evidence
Risk ratings and potential business impact
Clear, prioritized remediation steps
6. Remediation and retesting
Once fixes are implemented, the system is retested to verify all vulnerabilities are resolved. This helps ensure lasting security and supports compliance documentation.
How to choose the right penetration testing platform for your small business
Choosing the right pentesting provider is crucial, especially when working with limited budgets and resources. Here’s what to look for:
- Scalable pricing and scope
Opt for providers that offer tiered packages so you can start small (e.g., testing your website or web app) and expand later as your business grows.
- Comprehensive coverage
Ensure the provider covers both external and internal testing, web and API assessments, and post-fix verification.
- Automation with expert oversight
Automated tools accelerate testing, but human validation ensures accuracy. Choose a platform that combines both.
- Compliance alignment
Look for platforms that map findings to frameworks like PCI DSS, HIPAA, NIST, or ISO 27001, especially if you process payments or handle sensitive data.
- Actionable reporting
The report should be clear, business-friendly, and actionable, not just a technical dump. Executive summaries and remediation prioritization are key.
- Ongoing testing options
Cybersecurity isn’t one-and-done. Consider continuous pentesting or periodic retesting to maintain resilience as your business evolves.
How Beagle Security can help you
Beagle Security makes enterprise-grade penetration testing accessible to small and medium-sized businesses. Its automated pentesting platform continuously scans your web apps and APIs to uncover real-world vulnerabilities before they can be exploited.
Getting started
Create new application: Click “Add Application” and select the application type from three options: Website (traditional web applications), API (REST), or GraphQL (modern API implementations).
Application details: Enter your details such as specific application name and complete URL that will serve as the primary target for AI penetration testing. You can also set the importance of said application and configure application URL accessibility.
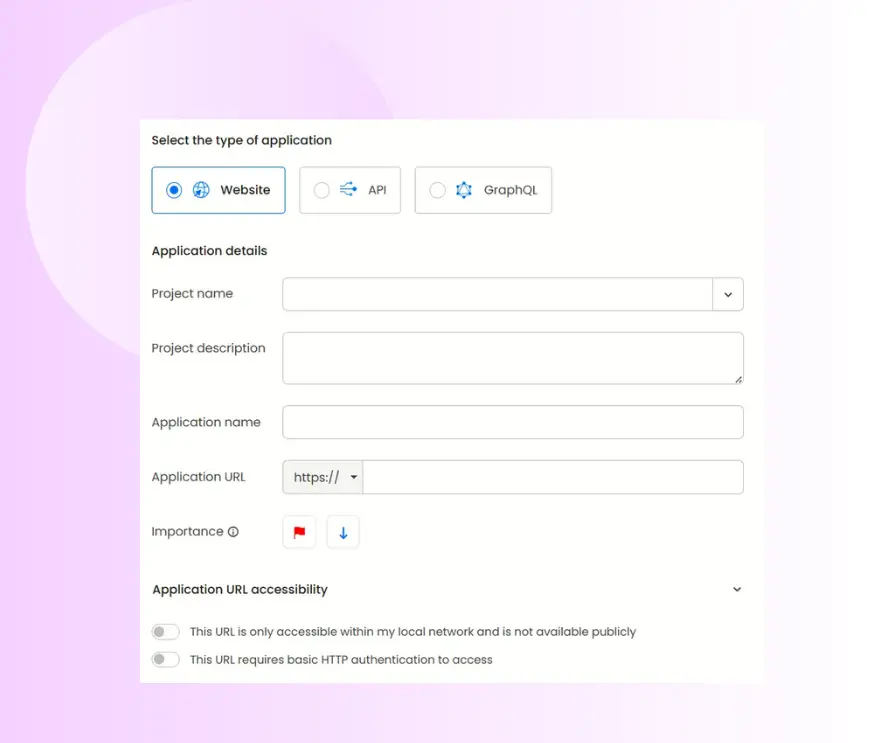
Setting up a black box penetration test
A black box penetration test simulates attacker perspective with no privileged access. To do this, proceed directly to the ‘start test’ button after adding your application.
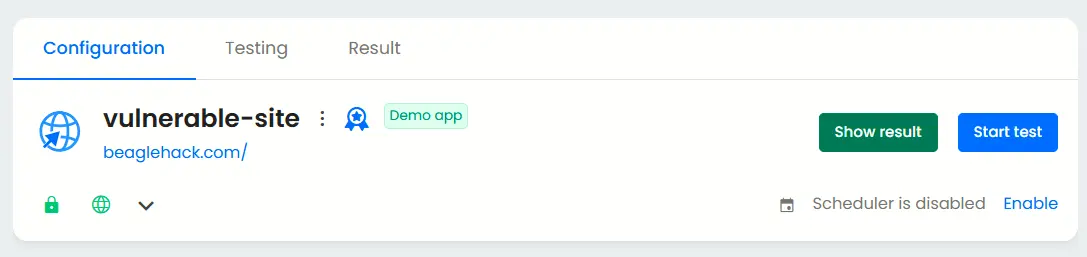
Setting up a grey box penetration test
As a small business, grey box testing is the best method to ensure you have all your bases covered. In order to do this, you must set up authenticated testing which simulates an attack with limited credentials and information.
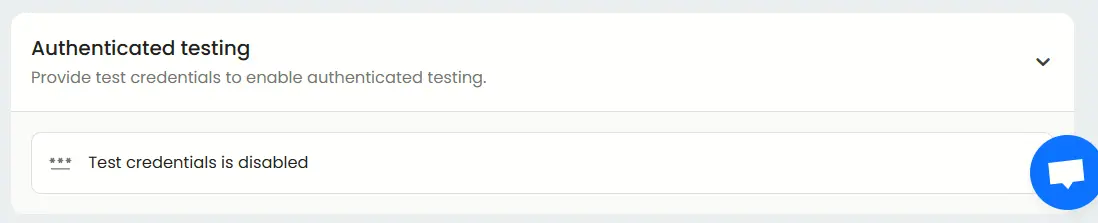
Authenticated testing
Enable “authenticated testing” at the bottom of basic tab and provide your test credentials. This allows AI modules to assess post-login functionality, user role permissions, and authenticated attack surfaces.
Here you can set up credential type which includes logins, signup and third-party log in.
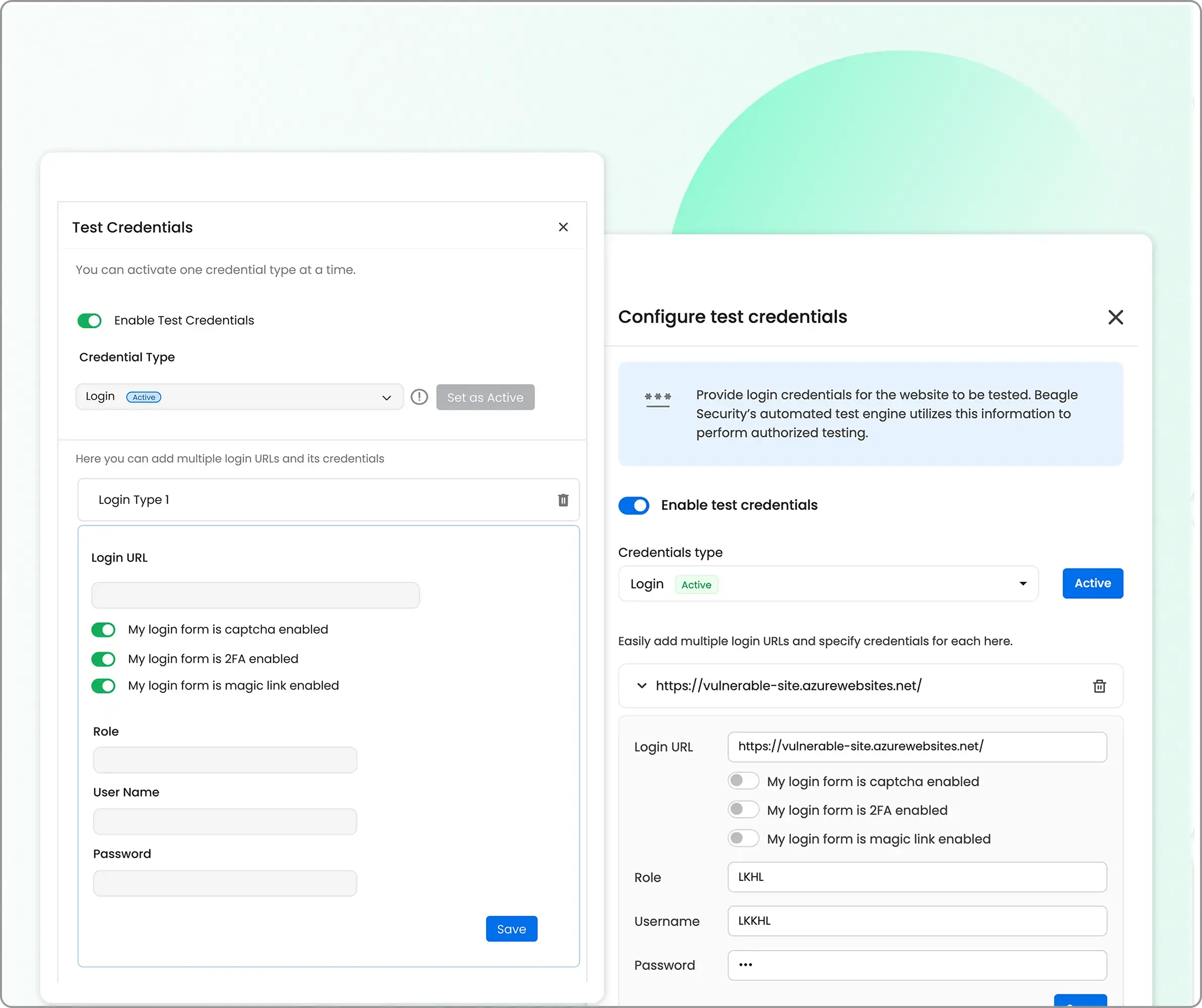
The recommended login is the “recorded login” option which can be set up by Beagle Security’s chrome extension.
Advanced configuration (optional)
- Business logic recording: Enable “Scenario recording” using the Beagle Security browser plugin to capture complex user workflows, multi-step transactions, and application-specific business processes for targeted security assessment.
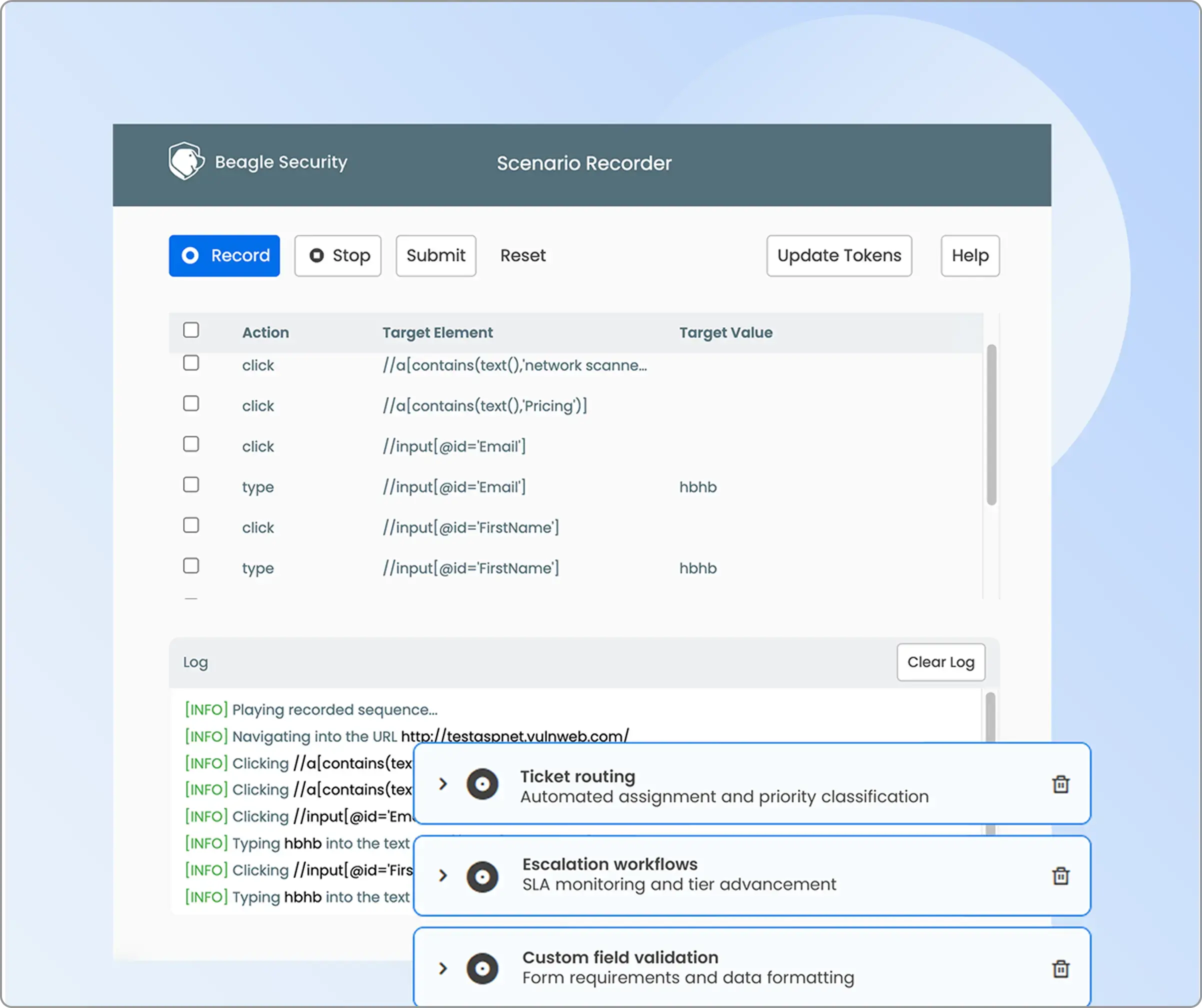
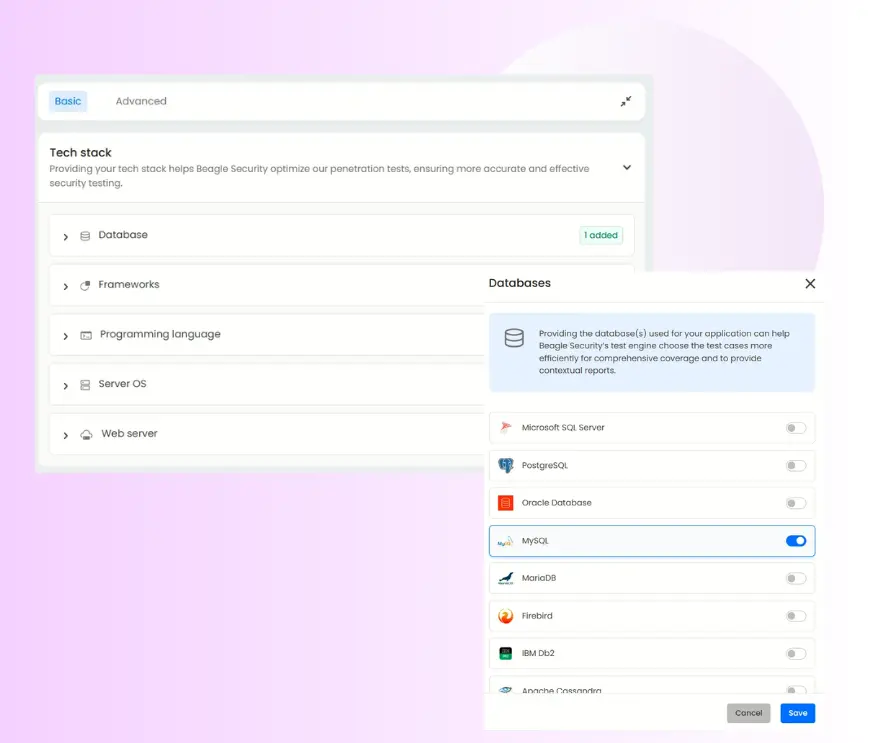
- Technology stack optimization: The tech stack section is found under the ‘basic’ tab. Here you can configure frameworks, programming languages, databases, server OS, and web server details to optimize AI attack strategies.
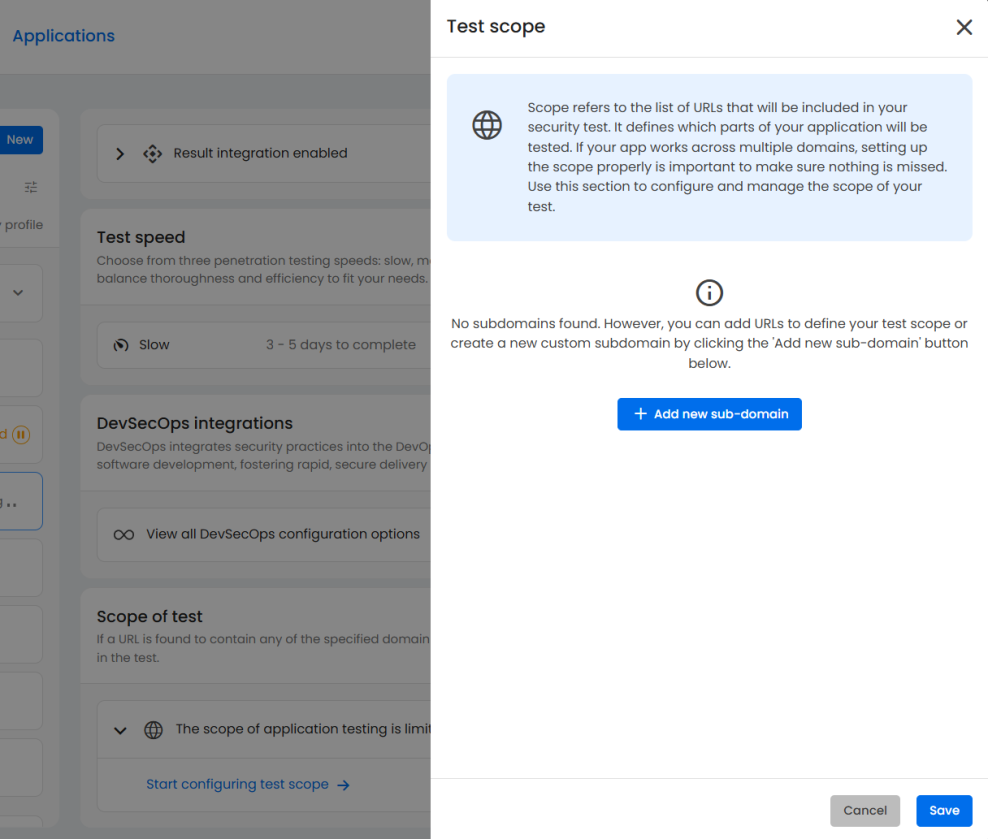
- Test speed and pentesting scope: Choose testing speed (slow, medium, or fast) and define scope boundaries to balance thoroughness with testing timeline requirements.
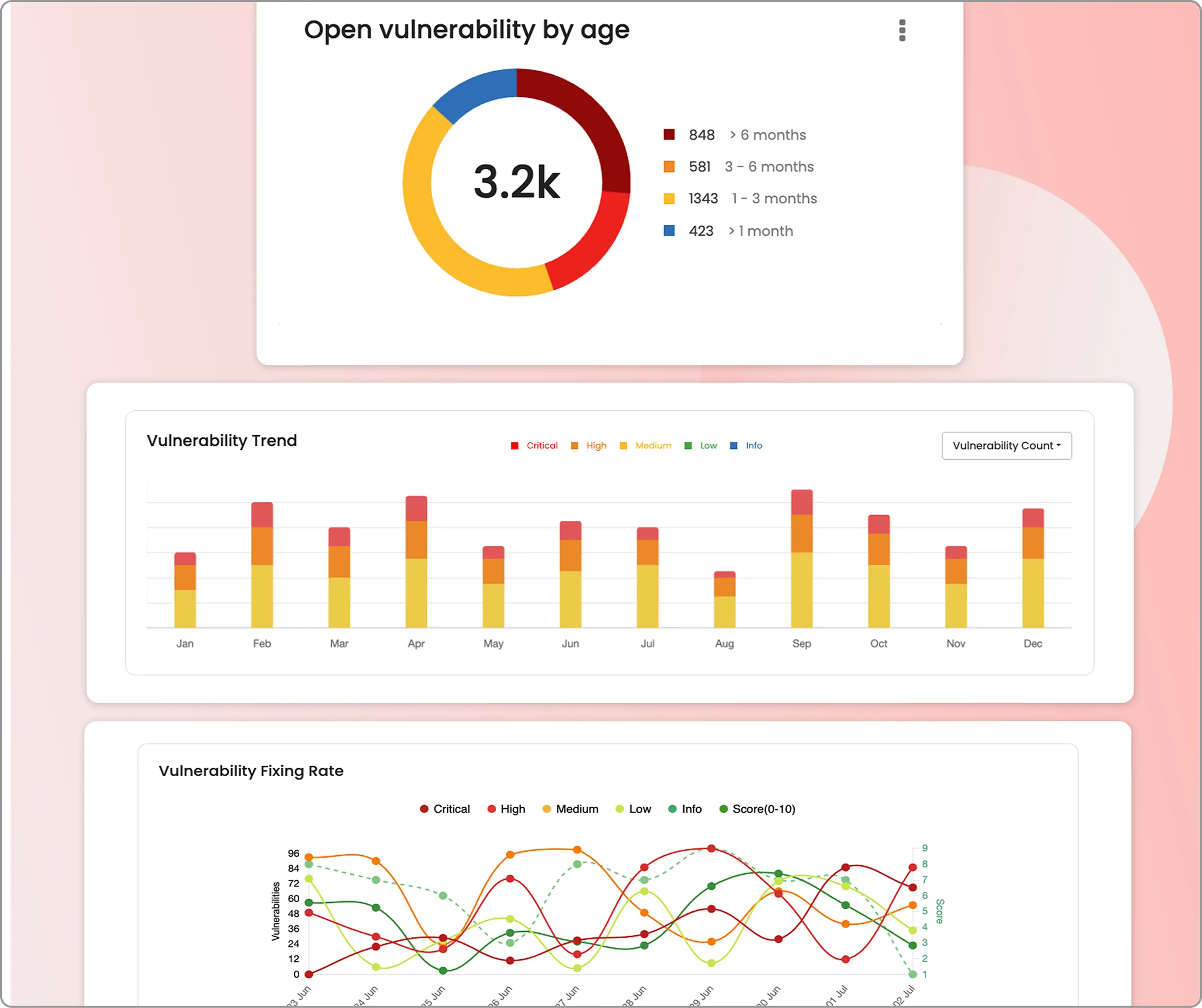
Real-time progress and results
Live progress tracking: Watch the AI penetration test in real time on a dashboard, seeing which attack methods are being tried and what succeeds as the test happens.
Comprehensive dashboards: After the test, view a detailed report showing all found vulnerabilities, how serious they are, CVSS scores, example proof-of-concepts, and step-by-step advice on how to fix each issue.
Final thoughts
For small businesses, cybersecurity isn’t a luxury, it’s a business enabler. The cost of one data breach or ransomware attack often exceeds years of preventive security testing.
Penetration testing for small business helps you identify vulnerabilities, improve resilience, and build customer trust. It bridges the gap between awareness and action, giving you confidence that your systems, data, and reputation are protected.
Still unsure about how to protect your small business? Try Beagle Security’s 14-day advance trial or check out our interactive demo environment.
FAQ
How often should a small business conduct penetration testing?
Most experts recommend conducting a penetration test at least once a year or after any major system change, new product launch, or infrastructure upgrade to ensure evolving threats are continuously addressed.
How much does penetration testing cost for a small business?
Penetration testing for small businesses typically costs between $3,000 and $15,000, depending on the scope, complexity, and depth of testing.
Investing in an automated penetration testing platform like Beagle Security can help you avoid costly breaches and downtime, delivering significant savings in the long run. Our VFM plan start at just $99, offering a smarter and more value-for-money security solution.
Do we need a pentest if we already use vulnerability scanners?
Yes. Vulnerability scanners only identify surface-level issues, while penetration testing simulates real-world attacks to test how your systems, people, and processes hold up against an active threat.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)