What is AI penetration testing?
AI penetration testing combines machine learning algorithms with traditional security testing approaches to automatically discover vulnerabilities in web applications and APIs.
These systems simulate attacker behavior at scale, identifying security gaps that manual testing often misses during compressed development cycles.
Unlike traditional penetration testing, which is often manual and time-bound, AI-driven penetration testing methods continuously learn and evolve, offering quicker and more adaptive security assessments.
AI in penetration testing allows systems to mimic attacker behavior at scale.
It can identify security weaknesses in web applications & APIs with greater efficiency. This reduces human error and resource dependency.
This intelligent approach to security testing involves AI systems that can learn from previous attacks and adapt to different environments.
The AI algorithms analyze system responses and make real-time decisions about which attack vectors to pursue. It simultaneously documents findings and provides detailed vulnerability reports.
The core components of AI-driven penetration testing can be summarized as:
Automated reconnaissance
Intelligent vulnerability scanning
Adaptive attack simulation
Continuous learning capabilities
These systems can process vast amounts of data and execute multiple testing scenarios concurrently.
How does AI improve the efficiency of penetration testing?
AI dramatically transforms penetration testing efficiency through several key mechanisms.
Speed
Speed represents one of the most significant improvements, as AI systems can conduct tests 24/7 without fatigue, processing multiple attack vectors simultaneously.
AI also automates repetitive tasks such as vulnerability scanning, payload generation, and exploit execution, thus increasing coverage and speed.
Development teams benefit from faster feedback cycles.
Security assessments that previously delayed release schedules by weeks now complete within sprint cycles, enabling continuous security validation without disrupting development velocity.
Scalable simulations and automation
AI systems can simultaneously test hundreds of API endpoints and applications. Usually this would require large teams of human testers and significantly more time when using traditional methods.
Machine learning algorithms process application responses to build comprehensive target profiles.
They identify technology stacks through response header analysis, detect framework versions through error message patterns, and discover administrative interfaces through intelligent directory traversal.
This automated intelligence gathering produces more thorough reconnaissance than manual methods while freeing security teams to focus on complex vulnerability analysis and remediation strategy development.
Reduced human error and effort
Intelligence gathering and reconnaissance become exponentially more effective with AI. These systems can automatically collect and analyze information from various sources, including public databases, social media, and technical documentation. They help create detailed target profiles that inform more precise attack strategies.
The AI can correlate seemingly unrelated information pieces to identify potential attack paths that human testers might miss.
Adaptive learning and 24/7 monitoring
AI penetration testing systems maintain persistent knowledge bases that improve with each assessment cycle.
Machine learning models learn application-specific vulnerability patterns, successful exploit techniques, and false positive indicators.
These systems adapt testing strategies based on discovered application characteristics. For example, AI identifies that a target application uses specific input validation libraries, then automatically selects payloads optimized for bypassing those particular security controls.
This continuous approach ensures that security assessments remain current and relevant, rather than representing point-in-time snapshots.
What is the difference between traditional penetration testing and AI penetration testing?
Traditional penetration testing and its limitations
Traditional penetration testing follows a manual, methodical approach where human experts simulate cyberattacks using their knowledge and experience.
These tests typically follow structured frameworks like OWASP or NIST, requiring significant time for planning, execution, and reporting.
Manual testing excels at creative attack vector development and complex business logic vulnerability discovery. Human testers identify subtle security flaws that emerge from understanding application purpose and user workflow patterns. They adapt testing strategies based on discovered application characteristics and pursue unconventional attack paths that automated tools might miss.
However, manual approaches face significant scalability limitations in continuous deployment environments.
A single penetration tester can thoroughly assess 5-10 applications per month, creating bottlenecks for organizations managing hundreds of applications across multiple development teams.
Resource constraints force trade-offs in testing scope.
Manual assessments often focus on high-priority applications while leaving secondary systems with minimal security validation. This selective coverage creates security gaps that attackers exploit through lateral movement techniques.
Advantages of AI-powered penetration testing
- Comprehensive application coverage without resource scaling: AI penetration testing maintain exhaustive testing coverage across application portfolios without proportional increases in security team size.
These systems automatically discover and assess new API endpoints, test parameter combinations across thousands of input variations, and validate security controls against comprehensive attack libraries.
- Security feedback in development workflows: AI systems integrate with development environments to provide immediate vulnerability detection during deployment processes.
These systems automatically trigger security assessments when applications deploy to staging environments, delivering security feedback within CI/CD pipeline.
- Proactive vulnerability prevention: Continuous testing enables proactive vulnerability prevention rather than reactive remediation.
Development teams identify and fix security issues during active development rather than discovering problems weeks later through scheduled penetration tests.
- Cost efficiency for continuous validation: Organizations practicing continuous deployment achieve significant cost advantages through AI penetration testing compared to repeated manual assessments.
AI systems amortize their implementation costs across unlimited testing cycles, while the cost of penetration testing is high as it requires fresh resource allocation for each assessment.
The following table provides a snapshot of the feature differences between traditional and AI-driven penetration testing:
| Feature | Traditional penetration testing | AI penetration testing |
|---|---|---|
| Frequency | Periodic (quarterly or annually) | Continuous or on-demand |
| Human Involvement | High | Minimal, with human oversight |
| Speed | Slower due to manual execution | Much faster with automated workflows |
| Adaptability | Limited | Learns and adapts to new attack patterns |
| Coverage consistency | Varies by tester expertise | Standardized across all applications |
| Cost-effectiveness | Expensive due to time and expertise | More efficient over time |
How to run AI penetration tests using Beagle Security
Beagle Security makes AI-powered penetration testing easy to implement and scale. Here’s a step-by-step guide:
Step 1: Application setup
Create new application: Click “Add Application” and select the application type from three options: Website (traditional web applications), API (REST), or GraphQL (modern API implementations).
Application details: Enter the specific application name and complete URL that will serve as the primary target for AI penetration testing.
Step 2: Black box vs grey box penetration testing selection
Black box penetration testing (immediate start): For external security assessment without internal system knowledge, proceed directly to test launch after application registration to simulate attacker perspective with no privileged access.
Grey box penetration testing setup: Enable “authenticated testing” and provide test credentials to allow AI module to assess post-login functionality, user role permissions, and authenticated attack surfaces.
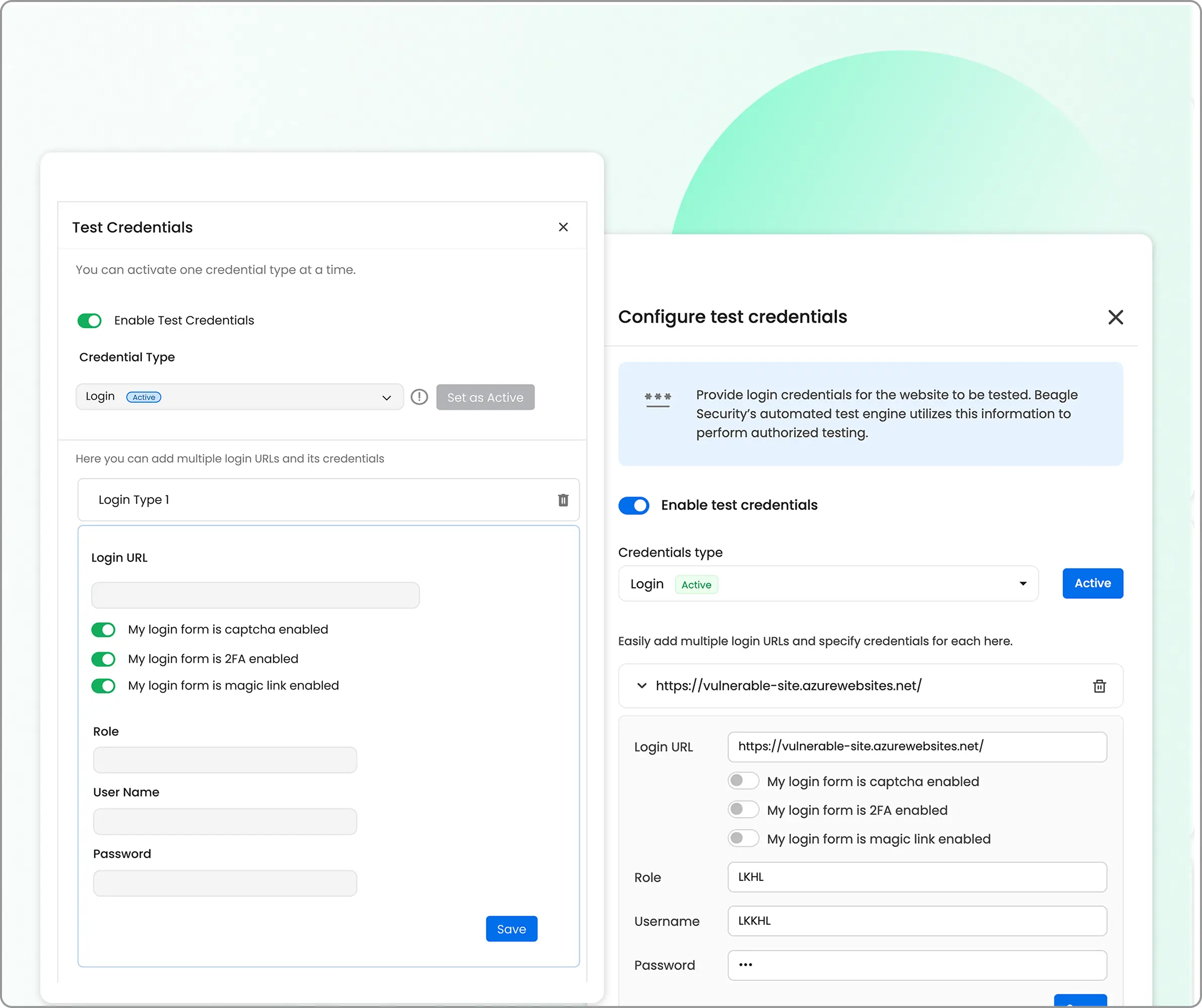
Step 3: Advanced configuration (optional)
- Business logic recording: Enable “Scenario recording” using the Beagle Security browser plugin to capture complex user workflows, multi-step transactions, and application-specific business processes for targeted security assessment.
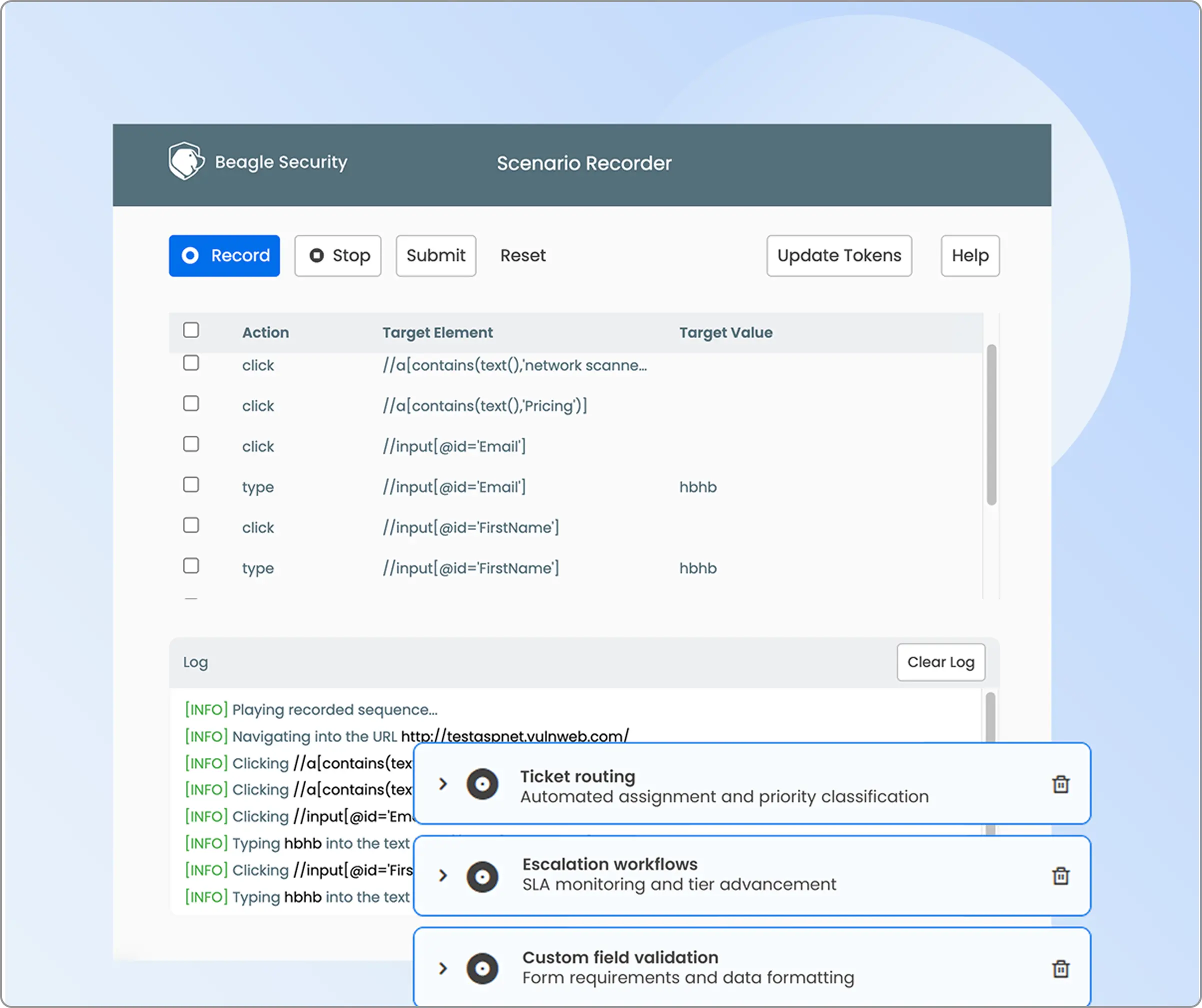
Technology stack optimization: Configure frameworks, programming languages, databases, server OS, and web server details to optimize AI attack strategies for specific application architectures and for contextual reports.
Test speed and scope selection: Choose testing speed (slow, medium, or fast) and define scope boundaries to balance thoroughness with testing timeline requirements.
Step 4: Real-time progress and results
Live progress tracking: Monitor AI penetration testing execution through the real-time dashboard interface, observing attack vector progression and exploitation attempt results as they occur during the assessment.
Comprehensive dashboards: Review detailed security reports after testing completion, including specific vulnerability classifications, severity ratings, CVSS scores, proof-of-concept demonstrations, and targeted remediation guidance for each discovered security issue.
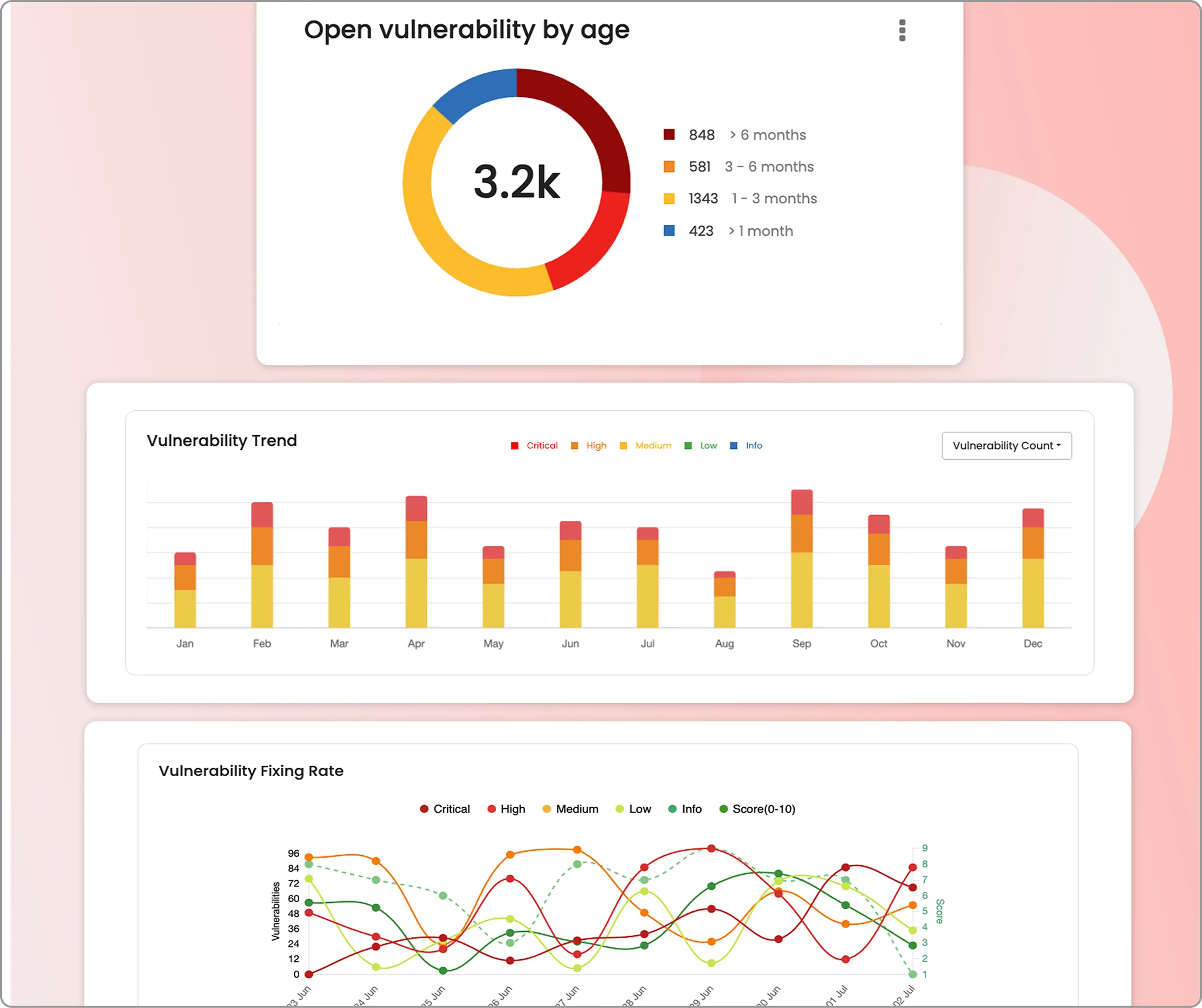
Step 6: Deeper integrations
CI/CD pipeline integration: Configure DevSecOps integrations to automatically trigger AI penetration tests based on deployment events.
Result integrations: Enable automatic vulnerability synchronization with development platforms (Jira, Slack, Azure Boards) to streamline issue tracking and remediation workflows.
Schedule and execute: Set up recurring test schedules or launch immediate assessment, with AI systems automatically adapting attack strategies based on discovered application characteristics and response patterns.
Final thoughts
AI penetration testing is redefining how organizations approach application security. It brings speed, intelligence and consistency to a process that was traditionally manual and episodic. By integrating an AI-powered AppSec platform like Beagle Security, your organization can:
Detect vulnerabilities faster
Automate compliance reporting
Strengthen defenses without overloading your security team
Stay secure in real time not just at audit time
AI penetration testing represents a fundamental shift in cybersecurity assessment methodologies. It offers organizations capabilities to identify and address security vulnerabilities like never before.
As cyber threats continue evolving in sophistication and frequency, AI penetration testing provides the scalability and adaptability necessary to maintain robust security postures.
Organizations considering AI penetration testing should evaluate their current security testing capabilities and identify gaps in coverage or frequency. This would help them assess how AI-powered solutions could enhance their overall security programs. The investment in AI penetration testing technology reduces testing costs, enhances security and regulatory compliance.
The future of cybersecurity testing lies in intelligent, adaptive systems that can keep pace with evolving threats while providing organizations with actionable insights for improving their security postures.
FAQs
Why is AI penetration testing important?
AI penetration testing is crucial because it provides continuous, comprehensive security assessment capabilities that traditional methods cannot match. It identifies vulnerabilities faster, covers more attack surfaces simultaneously, and adapts to emerging threats in real-time, ensuring organizations maintain robust security postures against evolving cyber risks.
What is the process of AI penetration testing?
The process involves automated testing and intelligence gathering, followed by dynamic vulnerability scanning and exploitation attempts. The AI system continuously learns and adapts its strategies based on findings, ultimately generating comprehensive reports with recommendations.
Can AI perform penetration tests on its own?
Yes, AI systems can autonomously conduct comprehensive penetration tests, including reconnaissance, vulnerability identification, and exploitation attempts. However, the most effective implementations combine AI automation with human oversight for strategic decision-making.
How much is the cost of AI penetration tests compared to traditional penetration tests?
AI penetration testing provides cost advantages over traditional methods, especially for frequent or continuous testing requirements. While initial platform costs may be comparable, AI testing eliminates recurring consultant fees and reduces testing time. This combined with AI’s continuous testing capabilities, make it more cost-effective long-term.