Switch to Beagle Security:
The Probely alternative
Beagle Security provides advanced AI-driven penetration tests compared to Probely’s vulnerability scanning, delivering contextual reports tailored towards your unique tech stack.
14-day free trial with Advanced plan features
No credit card required
Loved by over 1800+ dev & security teams
















Beagle Security vs Probely
Users prefer Beagle Security on G2. More reviews, more trust, and a consistently smoother user experience.
Beagle Security Probely
Ease of use Ease of setup Ease of admin Quality of support Overall G2 score No. of reviews
95%
96%
93%
97%
4.7
86 reviews
92%
98%
93%
95%
4.7
19 reviews
Comparison data from G2 as of May 2025
Why choose Beagle Security
over Probely?
over Probely?
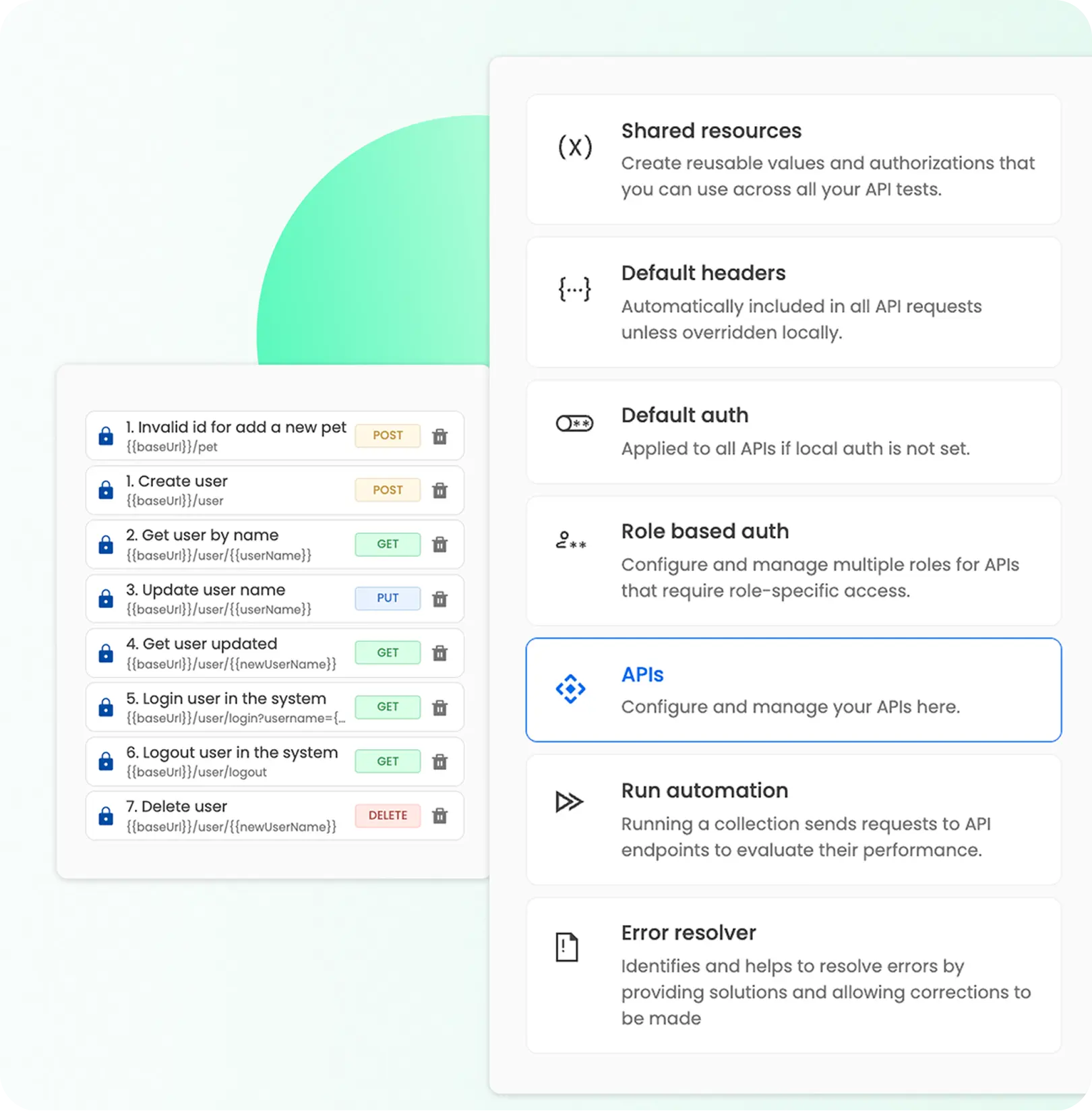
Go beyond basic API security
GraphQL ready: GraphQL-native penetration testing to help you address critical gaps in your GraphQL APIs.
Integrate Postman: Easily plug in your existing Postman collections and automate deep API pentesting workflows.
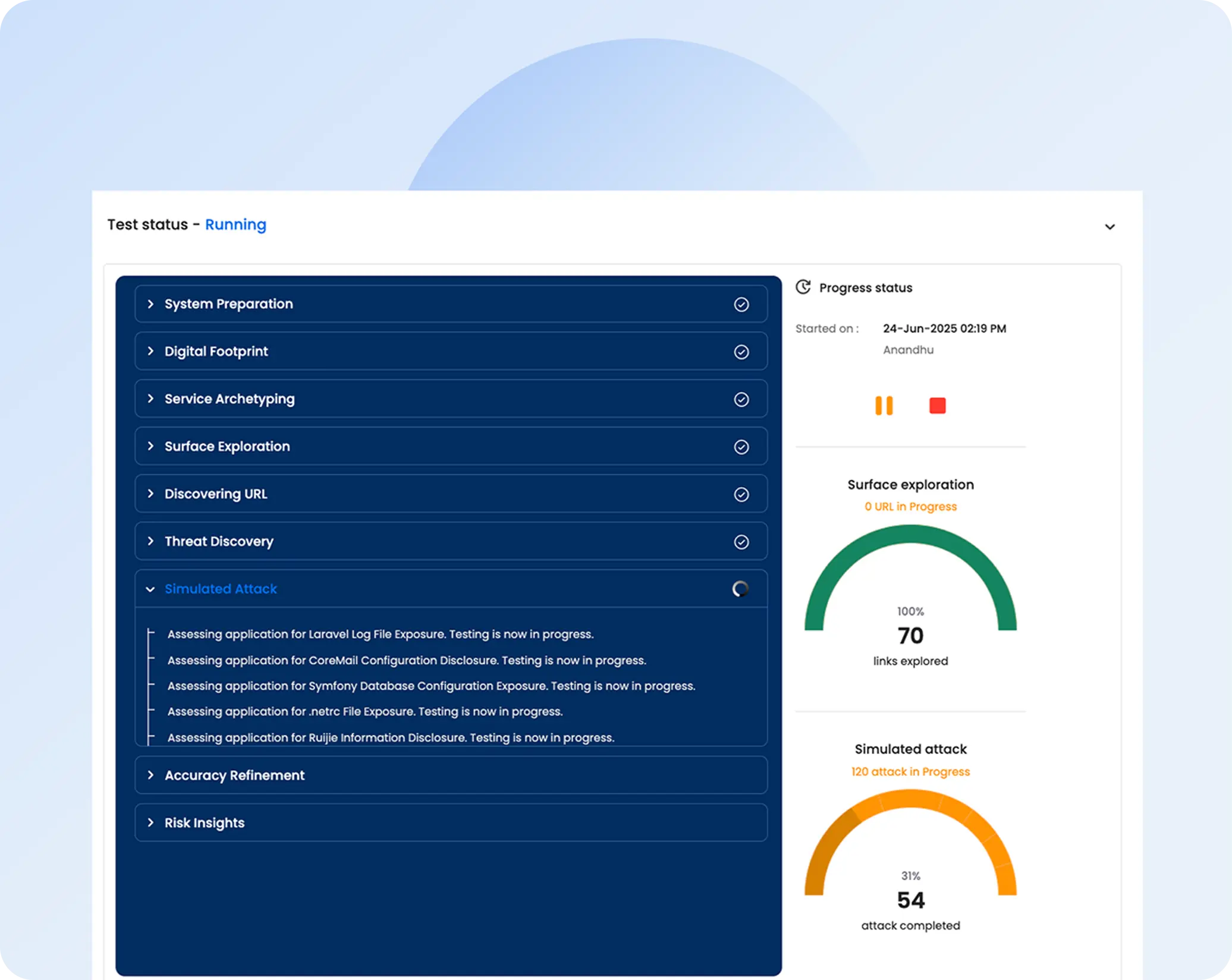
Truly automated penetration testing
Realistic attack simulations: Go beyond basic vulnerability scans with dynamic, real-world attack scenarios.
Effortless dynamic login handling: Test complex login flows with minimal manual setup.
Complex business logic support: Accurately test and validate applications with intricate business logic workflows and multi-step operations.
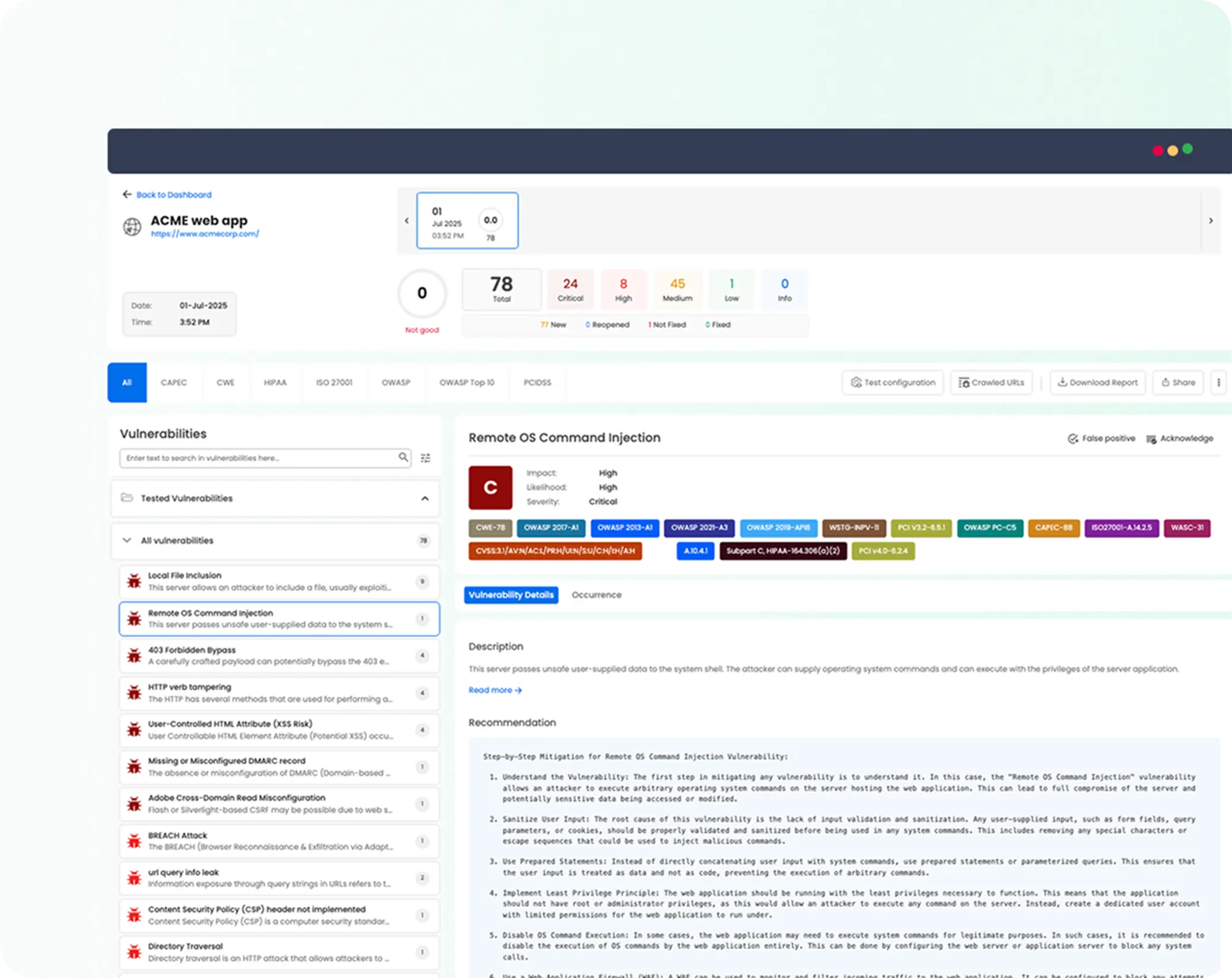
Context-rich security reports
Testing tuned to your tech stack: Providing your application's frameworks, programming languages, etc enables highly targeted penetration tests.
Developer-friendly contextual reports: Deliver vulnerability findings with step-by-step fix instructions—so developers know exactly what to fix without security expertise.
Transparent pricing for predictable security budgets
Our billing model ensures you only pay for the number of tests you run, not the number of applications/targets you manage.
Billed monthly
Billed annually
Get 2 months free
Essential
$99
Billed $1188 annually
What's included
2 tests/month
1 concurrent tests
5 team members
Popular
Advanced
$299
Billed $3588 annually
What's included
15 tests/month
4 concurrent tests
15 team members
Enterprise
What's included
Custom tests/month
Custom concurrent tests
Custom team members
Trusted by the world’s fastest scaling teams
Easy to set up, the reporting is detailed and well explained, making suggestions easy to action.

Tim Chorlton
Director at The Factory
We use Beagle Security to submit external penetration scans to customers and keep them happy.

Brad Slavin
CTO at DuoCircle
Beagle Security helps reduce the cost of security compliance and integrates well into the DevOps cycle.

Nidhin Tamil
CISO at Boral
Ready to experience Beagle Security – the sensible Probely alternative?
14-day free trial with Advanced plan features
No credit card required