
There are two different methods for assessing vulnerabilities namely authenticated and unauthenticated scanning. Each provides a different perspective on the security posture of a system.
Authenticated scans use legitimate user credentials to perform vulnerability evaluations. This offers a comprehensive internal picture of the system, making it possible to identify vulnerabilities like patch levels and misconfigurations that might be concealed by authentication procedures. Authenticated scans can be more resource-intensive and necessitate careful credential management, despite being more thorough and precise.
On the other side unauthenticated scans mimic the viewpoint of an external attacker by running without any login credentials. These scans concentrate on finding publicly known vulnerabilities that may be exploited without privileged access.
Unauthenticated scans are faster and less invasive, but they only offer a restricted, exterior view, which may cause them to miss internal vulnerabilities and occasionally produce false positives.
The most effective security strategy often involves combining both authenticated and unauthenticated scanning to achieve a more holistic assessment.
| Factor | Authenticated scans | Unauthenticated scans |
|---|---|---|
| Method | Requires valid credentials | No credentials needed |
| Scope | Internal systems and configurations | External-facing systems |
| Vulnerabilities | Internal flaws (misconfig, weak passwords, etc.) | External flaws (open ports, outdated web apps, etc.) |
| Accuracy | High, due to deeper system access | May show false positives |
| Depth | Detailed internal visibility | Broad external overview |
| When to Use | For compliance and in-depth internal analysis | For quick checks of public-facing assets |
What are authenticated scans?
Authenticated scanning, also known as credentialed scanning, involves conducting vulnerability scans while authenticating with valid credentials or user accounts.
This means that the scanning tool or process has access to the system or application being scanned, typically with administrators.
Authenticated scans provide a more comprehensive and accurate assessment of the security posture of a system.
With authenticated access, the scanning tool can analyze the system’s configurations, installed software, and underlying components in greater detail. It can also examine user-specific settings, access controls, and permissions.
By using privileged credentials during authenticated scans, vulnerability scanners can go further into a network and find dangers related to malware, installed apps, weak passwords, and configuration issues.
Authenticated scanning is particularly useful when assessing the security of internal systems, such as servers, databases, and workstations within an organization’s network.
It allows for a detailed examination of system configurations, software versions, and user-specific settings. Here are some pros & cons of authenticated scans:
| Pros of authenticated scans | Cons of authenticated scans |
|---|---|
| Deep visibility into internal settings and software | Getting valid credentials can be difficult |
| Accurately finds hidden vulnerabilities | Risk of accidental disruption if misconfigured |
| Enables targeted remediation | More time- and resource-intensive |
| Often required for compliance | Needs formal authorization and documentation |
Pros of authenticated scanning
1. Deeper visibility
Authenticated scans provide deeper visibility into the target system’s configurations, settings, and installed software. This allows for a more comprehensive assessment of potential vulnerabilities, including those specific to certain user accounts or privileged configurations.
2. Identify vulnerabilities
With privileged access, authenticated scanning can accurately identify vulnerabilities that may be hidden from unauthenticated scans. It can differentiate between legitimate configurations and actual vulnerabilities, reducing the chances of false positives.
3. Prioritize and focus
Authenticated scans provide detailed information on specific configurations and settings that need to be addressed for remediation.
This allows organizations to prioritize and focus their efforts on fixing vulnerabilities that are relevant to their specific systems and configurations.
4. Compliance requirements
Authenticated scanning is often necessary to meet compliance requirements and security standards.
Many regulations and frameworks, such as PCI DSS (Payment Card Industry Data Security Standard), require authenticated scans to assess the security of systems handling sensitive data.
Cons of authenticated scanning
1. Might be challenging
Authenticated scanning requires valid credentials with appropriate permissions.
Obtaining these credentials might be challenging, especially for third-party systems or external services that organizations may not have direct control over. Without proper credentials, conducting authenticated scans is not possible.
2. Affects the stability
Authenticated scanning has the potential to cause unintentional actions or disruptions if not performed correctly.
The scanning process, if misconfigured or conducted without proper knowledge, might inadvertently modify settings or impact the stability of the target system.
3. Time consuming
Authenticated scans can be more resource-intensive and time-consuming compared to unauthenticated scans.
The scanning tool requires additional resources to log in and interact with the target system, which might impact the overall scanning performance or increase the time required to complete the assessment.
4. Authorization procedures
Authenticated scanning may require explicit authorization and proper documentation to meet compliance requirements.
Organizations need to ensure that the scanning activity is authorized, documented, and aligns with any applicable legal and regulatory frameworks.
What are unauthenticated scans?
Unauthenticated scanning is typically performed from an external perspective to evaluate the security of internet-facing systems, such as web applications, websites, and network infrastructure accessible to the public.
It focuses on identifying vulnerabilities that can be exploited without privileged access. It provides a broad overview of the potential vulnerabilities that can be identified externally.
They focus on weaknesses that can be detected without having privileged access, such as open ports, outdated software versions, server misconfigurations, and known web application vulnerabilities.
Here are some pros and cons of unauthenticated scanning:
| Pros of unauthenticated scanning | Cons of unauthenticated scanning |
|---|---|
| Identifies vulnerabilities visible to external attackers | Can't detect internal or user-specific issues |
| Early detection of common/external flaws | May produce false positives |
| Faster and less resource-intensive | Offers only a partial security view |
| Ideal for external system assessments | Often insufficient for compliance checks |
Pros of unauthenticated scanning
1. Understand potential risks
Unauthenticated scanning provides insight into vulnerabilities that can be identified and exploited by external attackers who do not have privileged access to the system.
It helps organizations understand the potential risks and vulnerabilities visible to the public or unauthorized users.
2. Early detection
Unauthenticated scans can quickly identify widespread vulnerabilities that can be addressed early in the development or deployment process.
By detecting these vulnerabilities early on, organizations can prioritize remediation efforts and reduce the potential attack surface.
3. Less resource intensive
Unauthenticated scans are generally less resource-intensive compared to authenticated scans since they do not require logging in or interacting with the target system using credentials.
This can result in faster scan times and less impact on system resources.
4. Great for external-facing systems
Unauthenticated scanning is well-suited for evaluating the security of external-facing systems, such as web applications or network infrastructure accessible from the internet.
It helps identify vulnerabilities that are visible and exploitable by potential attackers without the need for internal access.
Cons of unauthenticated scanning
1. Limited access
Unauthenticated scanning cannot assess the internal configurations, user-specific settings, or vulnerabilities specific to certain user accounts.
It may miss vulnerabilities that can only be identified with privileged access or hidden behind authentication mechanisms.
2. Increase in false positives
Unauthenticated scans may generate false positives if the scanning tool cannot differentiate between legitimate configurations and actual vulnerabilities.
Further manual validation or additional testing may be required to confirm the existence of reported vulnerabilities.
3. Only partial view
Unauthenticated scanning only provides a partial view of the overall security posture.
It focuses on vulnerabilities that can be detected externally but does not address potential internal vulnerabilities or system-specific misconfigurations.
4. Cannot assist in compliance testing
Depending on the industry and specific compliance requirements, unauthenticated scanning may not be sufficient to meet certain regulatory standards.
Authenticated scanning may be necessary to fulfill compliance obligations that require a comprehensive assessment of internal systems and configurations.
Authenticated vs unauthenticated scans: When to use it?
Authenticated scans are usually the better option when you want to perform a thorough examination of your system or network, especially if the target system or network owner has granted you permission and cooperation.
Misconfigurations, outdated software, weak passwords and other internal flaws that might not be immediately apparent can all be found with the use of these scans.
Additionally, authenticated scans are essential for complying with certain security regulations and laws, including PCI DSS or HIPAA, which frequently call for a thorough evaluation of internal systems.
Unauthenticated scans are very useful when you don’t have access to or authority to use credentials, or when you need to quickly evaluate a system or network in general.They can assist you in locating unprotected or vulnerable online programs, services, or other devices that could endanger your system or network.
Moreover, unauthenticated scans can assist you in confirming your security posture and defenses against external threats by simulating an attacker’s attempt to compromise your system or network.
| Scenario | Recommended scan |
|---|---|
| Testing internal security posture | Authenticated |
| Simulating an external hacker | Unauthenticated |
| Compliance audits (e.g., PCI DSS, CIS) | Authenticated |
| Quick initial scan | Unauthenticated |
| Discovering vulnerabilities in web applications behind a login | Authenticated |
| Assessing patch management effectiveness | Authenticated |
How to combine authenticated and unauthenticated scans?
Combining authenticated and unauthenticated scans is the most efficient and thorough method of vulnerability scanning.
The outcomes of the two scans can also be compared to find any differences or gaps that might need more research or correction.
You can raise your security awareness and preparedness by combining authenticated and unauthenticated scans.
How can Beagle Security help you?
Choosing between authenticated and unauthenticated scans depends on the objectives and context of the security testing.
With Beagle Security, you can go one step further and conduct an automated AI penetration test that delves deeper and simulates real-world attack scenarios. This provides a more thorough and insightful assessment of your application’s security posture.
These automated penetration tests can be unauthenticated with a black-box approach when you don’t provide the login credentials. You can also provide the login credentials to convert it to an authenticated penetration test.
How to run unauthenticated penetration tests using Beagle Security
Step 1: Application setup
Create new application: Click “Add Application” and select the application type from three options: Website (traditional web applications), API (REST), or GraphQL (modern API implementations).
Application details: Enter the specific application name and complete URL that will serve as the primary target for AI penetration testing.
Step 2: Unauthenticated penetration testing selection
- Unauthenticated penetration testing (immediate start): For external security assessment without internal system knowledge, proceed directly to launch your test to simulate attacker perspective with no privileged access.
How to run authenticated penetration tests using Beagle Security
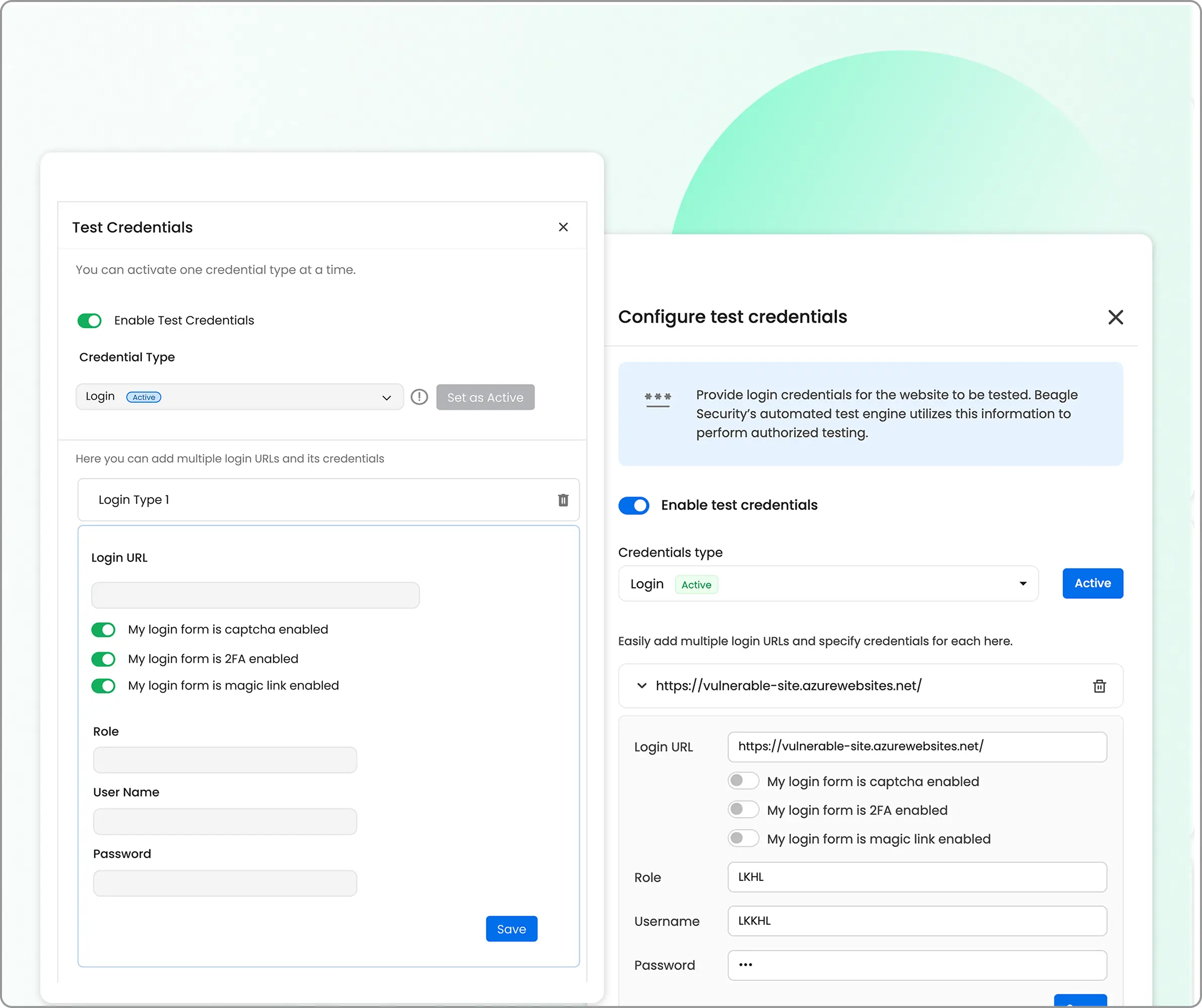
Step 1: Authenticated penetration testing selection
- Authenticated penetration testing setup: Head over the application you have set up and enable “authenticated testing”. Provide test credentials to allow the AI module to assess post-login functionality, user role permissions, and authenticated attack surfaces.
Step 2: Advanced configuration (optional)
- Business logic recording: Enable “Scenario recording” using the Beagle Security browser plugin to capture complex user workflows, multi-step transactions, and application-specific business processes for targeted security assessment.
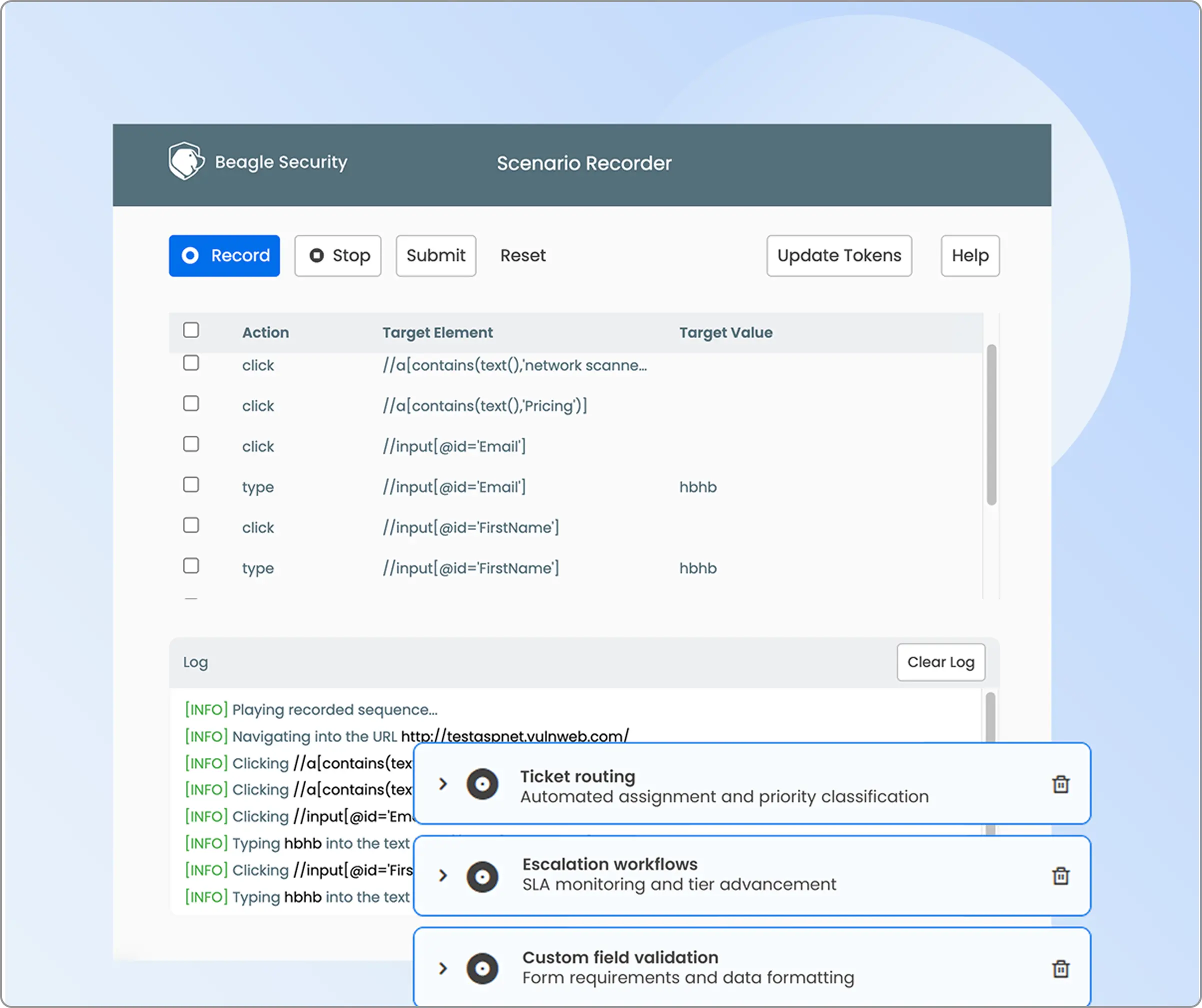
Technology stack optimization: Configure frameworks, programming languages, databases, server OS, and web server details to optimize AI attack strategies for specific application architectures and for contextual reports.
Test speed and scope selection: Choose testing speed (slow, medium, or fast) and define scope boundaries to balance thoroughness with testing timeline requirements.
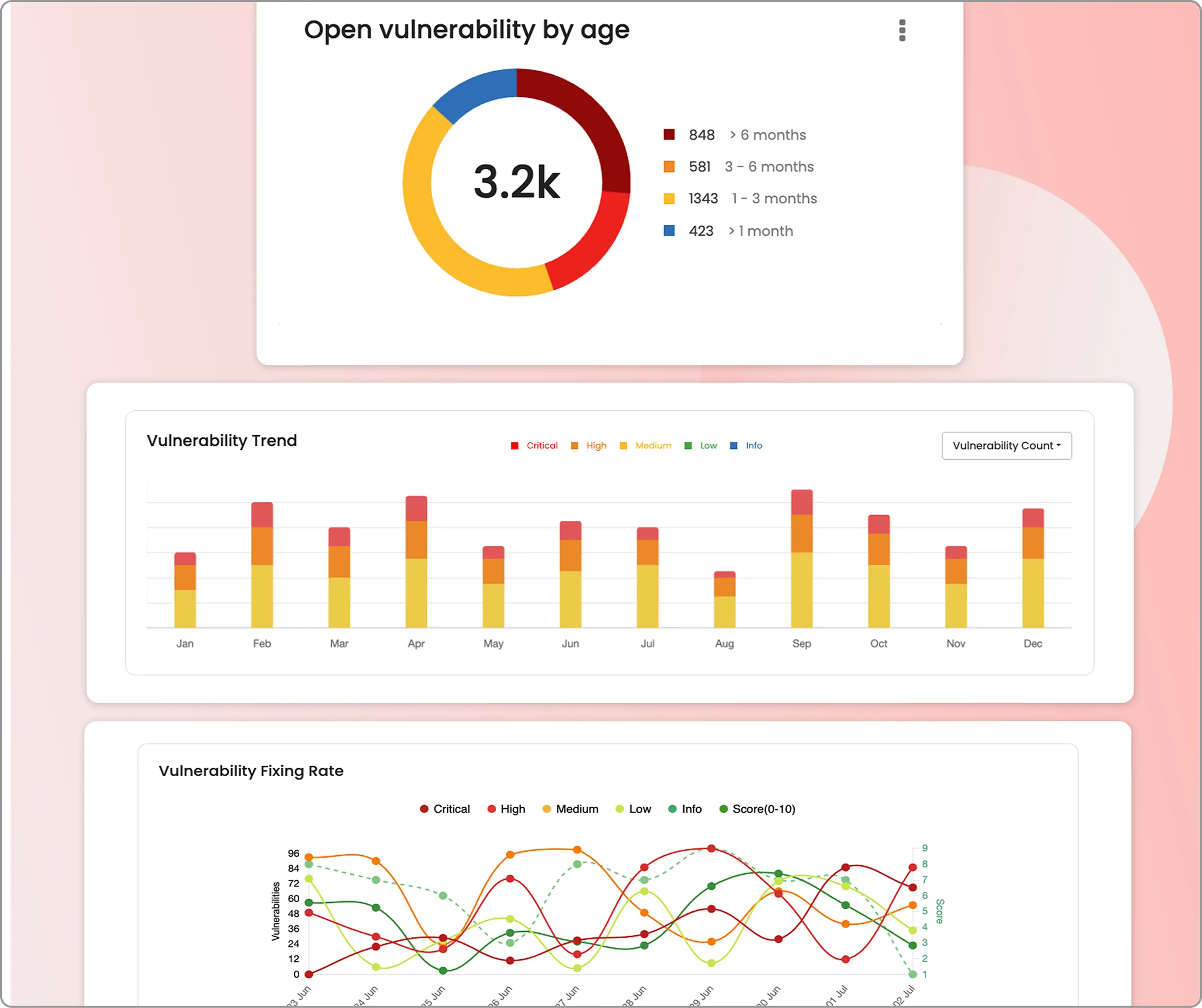
Step 3: Real-time progress and results
Live progress tracking: Monitor AI penetration testing execution through the real-time dashboard interface, observing attack vector progression and exploitation attempt results as they occur during the assessment.
Comprehensive dashboards: Review detailed security reports after testing completion, including specific vulnerability classifications, severity ratings, CVSS scores, proof-of-concept demonstrations, and targeted remediation guidance for each discovered security issue.
Step 4: Deeper integrations
CI/CD pipeline integration: Configure DevSecOps integrations to automatically trigger AI penetration tests based on deployment events.
Result integrations: Enable automatic vulnerability synchronization with development platforms (Jira, Slack, Azure Boards) to streamline issue tracking and remediation workflows.
Schedule and execute: Set up recurring test schedules or launch immediate assessment, with AI systems automatically adapting attack strategies based on discovered application characteristics and response patterns.
You can get started with Beagle Security by signing up for a 14- day Advanced plan trial or playing around with the interactive demo environment.
FAQ
How does the choice between authenticated and unauthenticated scanning impact the results of a vulnerability assessment?
Authenticated scans typically find 3-5x more vulnerabilities because they can access protected functionality, user dashboards, and business logic flows that attackers could exploit after gaining legitimate access.
What is the difference between authenticated and unauthenticated scanning?
Authenticated scanning uses valid credentials to test an application’s internal functions and user-accessible areas, while unauthenticated scanning only tests publicly visible pages outside the login functionality.
Editor's note: This article was originally published on November 21, 2023, and has been refreshed with new insights.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)