With cyberattacks becoming more advanced and harder to spot, businesses of all sizes are turning to penetration testing to find vulnerabilities before attackers can exploit them. Out of these, Black box penetration testing is one of the most realistic approaches to security. It simulates how an outsider, like a hacker, would try to break into your system.
It also provides a realistic view of your organization’s external security, helping you identify weak spots that might otherwise go unnoticed.
This comprehensive guide will walk you through what black box penetration testing is, when to use it, and how to choose the right approach for your business.
What is penetration testing?
Penetration testing (often called ethical hacking) is a simulated cyberattack conducted by security experts to uncover vulnerabilities in systems, applications, and networks before real attackers do.
Instead of waiting for a data breach, organizations perform penetration testing to identify weaknesses proactively, assess the impact of potential exploits, and strengthen overall defenses.
Key objectives of penetration testing:
Identify exploitable vulnerabilities before malicious actors find them.
Evaluate the effectiveness of existing security controls.
Test incident response procedures and team readiness.
Ensure compliance with frameworks such as SOC 2, ISO 27001, or HIPAA.
Penetration tests are typically categorized into three approaches depending on how much information the tester has before the test begins. These are black-box, grey-box, and white-box.
What is black box penetration testing?
Black box penetration testing (also written as black-box penetration testing) is a method where the tester has no prior knowledge of the system, network, or application being tested.
The goal is to mimic a real-world cyberattack from an external perspective, just as a malicious hacker would attempt to infiltrate your systems without insider access.
In a black box scenario, the tester starts from scratch, gathering information through reconnaissance and scanning, and then tries to exploit vulnerabilities discovered along the way.
Key characteristics of black box penetration testing:
No internal access or credentials are provided.
Focuses on external attack surfaces, such as websites, APIs, and public IPs.
Simulates real-world attack behavior, testing detection and response capabilities.
Ideal for assessing perimeter security and understanding external risk exposure.
By adopting a black-box approach, organizations can see how effective their firewalls, intrusion detection systems, and external configurations are against real attackers.
When do you need a black box penetration testing?
Not every organization needs black-box testing all the time, but there are specific scenarios where it adds significant value.
You should consider a black box penetration test when you want to:
1. Test external resilience
When your goal is to evaluate how secure your public-facing infrastructure (like web apps, APIs, or servers) is against real-world attacks.
2. Validate attack detection and response
Black box penetration testing helps assess how efficiently your security operations center (SOC) or incident response team identifies, analyzes, and mitigates external threats.
3. Meet compliance and regulatory requirements
Many standards like PCI DSS, GDPR, and ISO 27001 recommend regular external penetration testing to ensure your systems are resilient to attacks.
4. After major infrastructure changes
If you’ve recently undergone cloud migration, product releases, or new integrations, a black-box test can reveal vulnerabilities introduced during updates.
5. Conduct pre-launch security assurance
Before deploying a new SaaS product, mobile app, or API, black-box testing helps identify exploitable flaws that could compromise customer data or brand trust.
How to perform black box penetration testing using Beagle Security
Performing black box penetration testing manually can be complex and time-consuming, requiring expert knowledge of tools, scripting, and attack techniques.
However, platforms like Beagle Security automate and simplify the process using AI-driven testing while ensuring accurate, continuous, and standards-aligned assessments.
Here’s how to conduct a black box penetration test effectively using Beagle Security:
Getting started
In the applications tab in the left corner, choose to add a new application or create a new project.
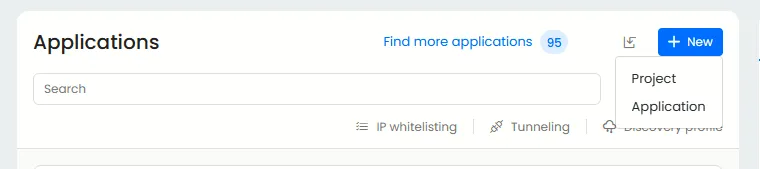
In the ‘create application’ section, you can choose the type of application you wish to create. Currently Beagle Security offers three types which are website, API and GraphQL.
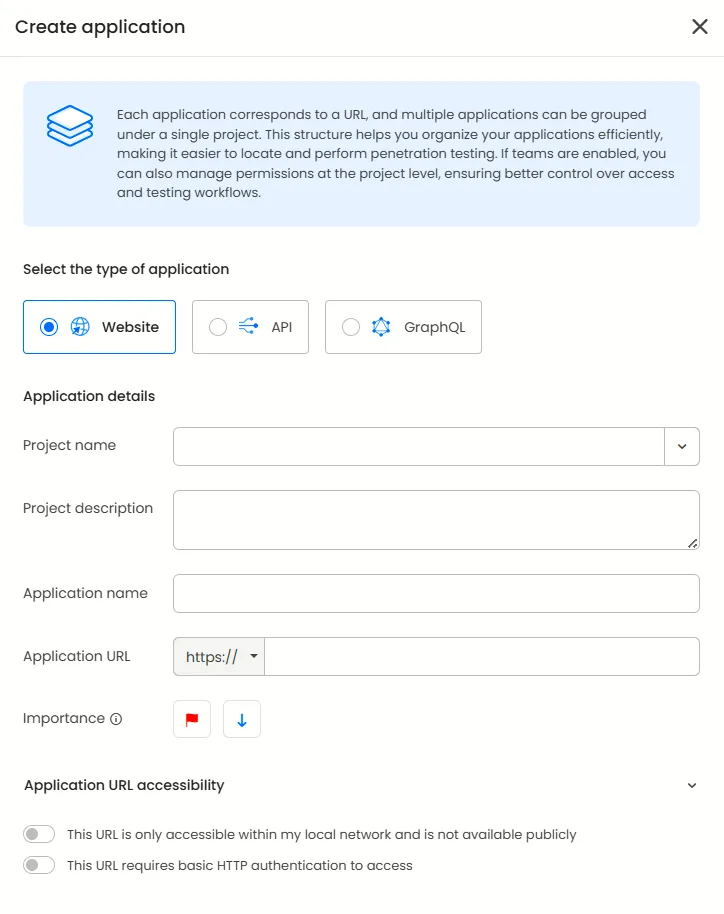
After choosing the application, you can decide the other parameters such as:
The project to which it belongs to
Application name
Application URL
Importance of said application
Accessibility of URL (HTTP authentication requirements and availability on public networks)
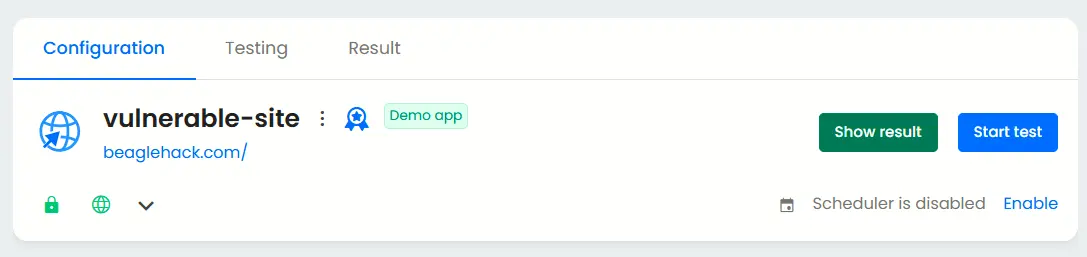
Starting the test
After you have set up your application, click on the ‘start test’ button to commence Black box testing without any privileged access.
Advantages and disadvantages of black box penetration testing
Advantages
Realistic attack simulation: Accurately replicates external hacker behavior.
No insider bias: Provides an unbiased evaluation of external security.
Validates detection & response: Tests real-time security readiness.
Regulatory alignment: Helps meet global compliance standards.
Cost-effective for external testing: Focuses resources on the most exposed areas.
Disadvantages
Limited visibility: Testers cannot access internal systems or code.
Time-intensive: Reconnaissance and exploitation phases can be lengthy.
Incomplete internal coverage: May miss deeper, code-level vulnerabilities.
Potential false negatives: Some vulnerabilities may remain undiscovered due to lack of internal insight.
Despite its limitations, black box penetration testing remains invaluable for organizations seeking realistic threat simulations and continuous external security validation.
Common black-box penetration testing techniques
Black-box penetration testers use a variety of methods to uncover potential entry points. These techniques mirror real-world hacker tactics, helping organizations identify overlooked security gaps.
Fuzzing
Fuzzing involves send large volumes of unexpected, random, or specially crafted inputs (payloads) to web forms, APIs, file parsers, or network services to trigger crashes, errors, or logic failures.
The typical goal is to find input-validation defects, buffer overflows, unhandled exceptions, or malformed-data logic paths.
Syntax testing
Syntax testing injects inputs that violate expected formats. This includes missing fields, extra delimiters, unexpected encodings, truncated JSON/XML, or illegal characters.
The objective is to identify parsing bugs, validation gaps, and inconsistent error handling that attackers can exploit.
Exploratory testing
This means performing ad-hoc tests driven by observations and anomalies rather than a rigid checklist. It also uses outputs from one test to design the next.
This approach is ideal when you have limited target context; it surfaces business-logic issues and unexpected flows.
Data analysis
Analyzing responses, error messages, timing, headers, and payload differences helps to infer backend logic, data structures, or API behavior.
Use response clustering, diffing, and timing analysis to reveal authentication/authorization gaps or info leakage.
Test scaffolding
Test scaffolding means build automated test harnesses that replay sequences, permutations, and edge cases at scale (e.g., scripted workflows, CI jobs).
Scaffolding helps expose race conditions, session issues, and chained vulnerabilities that manual tests miss.
Behavior monitoring
Monitor system stability, logs, error rates, and resource usage while injecting test inputs. Unexpected crashes, slowdowns, or new log entries often signal potential vulnerabilities.
Combine active probing with passive telemetry (server logs, WAF alerts) helps to correlate inputs with effects.
Black-box pentesting checklist
A structured checklist ensures a systematic, thorough assessment. Here’s a simplified black-box penetration testing checklist:
| Action item | Status |
|---|---|
| Define testing scope and targets | |
| Conduct OSINT (open-source intelligence) gathering | |
| Identify live hosts and open ports | |
| Scan web applications and APIs for vulnerabilities | |
| Test authentication and session management | |
| Check for injection flaws (SQLi, XSS, command injection) | |
| Analyze configurations and error handling | |
| Attempt controlled exploitation | |
| Document findings and remediation steps | |
| Perform re-test after fixes |
Black-box vs grey-box and white-box pen testing
In cybersecurity, the main difference between black-box, grey-box, and white-box testing lies in how much the tester knows. Black-box mimics an outsider’s perspective, grey-box offers partial visibility, and white-box provides complete access to code and configurations.
| Aspect | Black-box | Grey-box | White-box |
|---|---|---|---|
| Tester access | No internal knowledge | Partial access (e.g., credentials) | Full access to source code and architecture |
| Focus area | External attack surface | Internal & external components | Code-level vulnerabilities |
| Realism | Highly realistic | Balanced | Low (not attacker-like) |
| Depth of testing | Limited | Moderate | Deep |
| Use case | External web apps, APIs | Application logic flaws | Secure coding validation |
In practice, many organizations combine black-box and grey-box testing for comprehensive coverage across both external and authenticated layers.
How to choose the right pen test provider
Choosing the right penetration testing provider can make the difference between a surface-level assessment and a strategic security investment.
Here’s what to consider:
1. Expertise and certifications
Look for providers with certified testers (CEH, OSCP, or CREST) and proven experience in black-box testing methodologies.
2. Automated and manual balance
The ideal provider combines AI-powered automation (for scale) with manual validation (for accuracy), ensuring high-fidelity results.
3. Transparent reporting
Ensure the provider delivers clear, evidence-backed reports with reproducible test results and remediation advice tailored to your environment.
4. Continuous security validation
Modern security requires ongoing testing. Choose a solution like Beagle Security that supports continuous black-box testing with automated retests after fixes.
5. Compliance alignment
If your organization operates under SOC 2, GDPR, or HIPAA, confirm that the provider’s methodologies align with recognized compliance frameworks.
Final thoughts
Black box penetration testing is one of the most effective ways to measure your organization’s real-world cyber resilience. It helps identify external vulnerabilities before they can be exploited, tests your incident response readiness, and builds a proactive culture of security awareness.
By combining black-box testing with continuous monitoring and periodic grey- or white-box assessments, you can establish a defense-in-depth strategy that safeguards your business from both external and internal threats.
If you’re ready to start, platforms like Beagle Security offer an intelligent and automated way to perform black box penetration testing. Check out our free 14-day advanced trial, or look into our interactive demo to see if we’re the right fit for you.
FAQ
What is black-box penetration testing?
Black-box penetration testing is a security assessment where testers simulate real-world attacks without internal access to the system’s code or architecture. It helps identify vulnerabilities that external hackers could exploit.
How does black-box testing differ from grey-box and white-box testing?
The difference lies in information access. Black-box testers have none, grey-box testers have partial access (like credentials or API documentation), and white-box testers have full visibility into the code and infrastructure.
What types of vulnerabilities can black-box testing detect?
It can uncover authentication flaws, misconfigurations, insecure inputs, logic errors, and other weaknesses exposed through external interfaces such as web apps, APIs, or networks.
How often should companies perform black-box penetration tests?
Ideally, organizations should conduct black-box testing at least once or twice a year, or after major updates, infrastructure changes, or new feature releases.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)