
When planning a penetration test, one of the most critical steps is defining your penetration testing scope. Without clear boundaries, even the most advanced test can miss key assets, overlook real-world risks, or unintentionally disrupt operations.
A well-defined scope ensures your test aligns with your business goals, regulatory needs, and technical realities. It sets the rules of engagement such as what’s tested, how it’s tested, and under what conditions so that both your internal teams and external testers know exactly what’s expected.
In this guide, we’ll explore what penetration testing scope means, why it matters, and how to create a clear, effective framework that drives actionable results.
What is penetration testing?
Penetration testing (or ethical hacking) is a controlled simulation of cyberattacks conducted to identify vulnerabilities in your systems, applications, and infrastructure before malicious attackers can exploit them.
Unlike automated vulnerability scans, penetration testing goes deeper. It combines manual exploitation, contextual analysis, and attacker-like behavior to validate the impact of security weaknesses.
A typical penetration test involves:
Reconnaissance: gathering information about the target
Exploitation: attempting to breach systems or data
Post-exploitation: evaluating the potential damage
Reporting: documenting findings, risks, and remediation recommendations
The ultimate goal is to provide visibility into your true risk exposure and guide your security investments effectively.
What is penetration testing scope?
Your penetration testing scope defines what will be tested, how it will be tested, and to what extent. It’s essentially the blueprint of your engagement specifying all in-scope systems, applications, environments, and test boundaries.
In practical terms, the scope of a penetration test determines:
Which assets are included (web apps, APIs, cloud systems, networks, etc.)
Which assets are explicitly excluded (production databases, sensitive systems, or third-party components)
What kind of testing approach will be used (black box, white box, or gray box)
The testing conditions, such as time windows, access levels, and reporting expectations
A well-scoped engagement ensures that your penetration testing effort delivers relevant, actionable results, not just raw data or incomplete findings.
Why defining your penetration testing scope matters
A precisely defined penetration testing scope is the foundation of a successful security assessment. Here’s why it’s critical:
1. Ensures alignment with business objectives
Every organization has unique risk priorities. For a fintech company, the focus might be payment gateways; for a SaaS startup, it’s likely application security and data privacy.
Defining your penetration testing scope ensures that the test targets the systems that matter most to your operations and compliance requirements.
2. Avoids operational disruption
An unclear or overly broad scope can lead to unintentional downtime, data corruption, or service interruptions. By defining what’s off-limits and setting testing conditions, you ensure your systems remain stable during testing.
3. Improves efficiency and cost-effectiveness
Penetration testing is resource-intensive. A focused scope allows teams to allocate time and budget efficiently, targeting high-value assets instead of spreading efforts too thin across low-risk areas.
4. Facilitates compliance and audit readiness
Frameworks like SOC 2, ISO 27001, and HIPAA often require proof of periodic security testing. A clear scope helps ensure your penetration test covers the right control areas, making audit preparation smoother and faster.
5. Enables consistent, repeatable testing
A well-documented scope provides a baseline for future assessments. When your team runs subsequent tests, having a consistent scope makes it easier to track progress, validate fixes, and measure security improvements over time.
How to create a clear penetration testing scope
Defining your penetration testing scope is a collaborative process involving security teams, business stakeholders, and your testing provider. It typically involves several key steps:
1. Defining in-scope assets
Start by listing all the assets you want included in the test. These may include:
Web applications: URLs, subdomains, APIs, and backend services
Network systems: External and internal IP ranges, VPN gateways, or cloud infrastructure
Mobile apps: iOS and Android builds, along with associated APIs and authentication services
Cloud environments: AWS, Azure, GCP configurations, and IAM policies
Endpoints and users: Workstations, privileged accounts, and access management systems
It’s essential to ensure your scope covers production and staging environments appropriately with the right safeguards to prevent unintended outages.
A practical tip: use your asset inventory or CMDB (Configuration Management Database) to identify critical components tied to sensitive data or business operations.
2. What to exclude from pen test scope (the out-of-scope list)
Not every asset should be tested during a penetration engagement. Some systems might be too sensitive or not relevant to your goals.
Common exclusions include:
Third-party-managed services such as payment processors or SaaS tools
Legacy systems pending decommissioning
Internal-only systems unrelated to customer data
Production databases or systems with fragile uptime dependencies
Defining an out-of-scope list prevents unnecessary testing risks and helps focus resources where they matter most.
It’s also good practice to document why certain assets are excluded since it demonstrates due diligence to auditors and regulators.
3. Choosing your test type: black box, white box, or gray box
The next step in defining your penetration testing scope is selecting the right testing approach.
Black box testing: The tester has no prior knowledge of your systems and hence, simulating an external attacker’s perspective. Ideal for assessing perimeter defenses and real-world threat exposure.
White box testing: Full access is granted to the tester, including credentials and architecture documentation. Useful for validating code-level and configuration security.
Gray box testing: A hybrid model where testers have partial knowledge or limited credentials. It balances realism with efficiency, ideal for assessing both external and internal risks.
Your choice depends on your security maturity, testing objectives, and compliance requirements. For instance, black box tests help evaluate resilience against unknown threats, while white box tests are often favored for regulatory audits and deep infrastructure analysis.
How Beagle Security can help you define your pentesting scope
Without well-defined boundaries, your team risks overlooking key assets or wasting time testing irrelevant systems. This is where Beagle Security simplifies and strengthens the process. We ensure you test what truly matters, while maintaining compliance and audit readiness.
Scope of test is located under the advanced tab of the configuration section
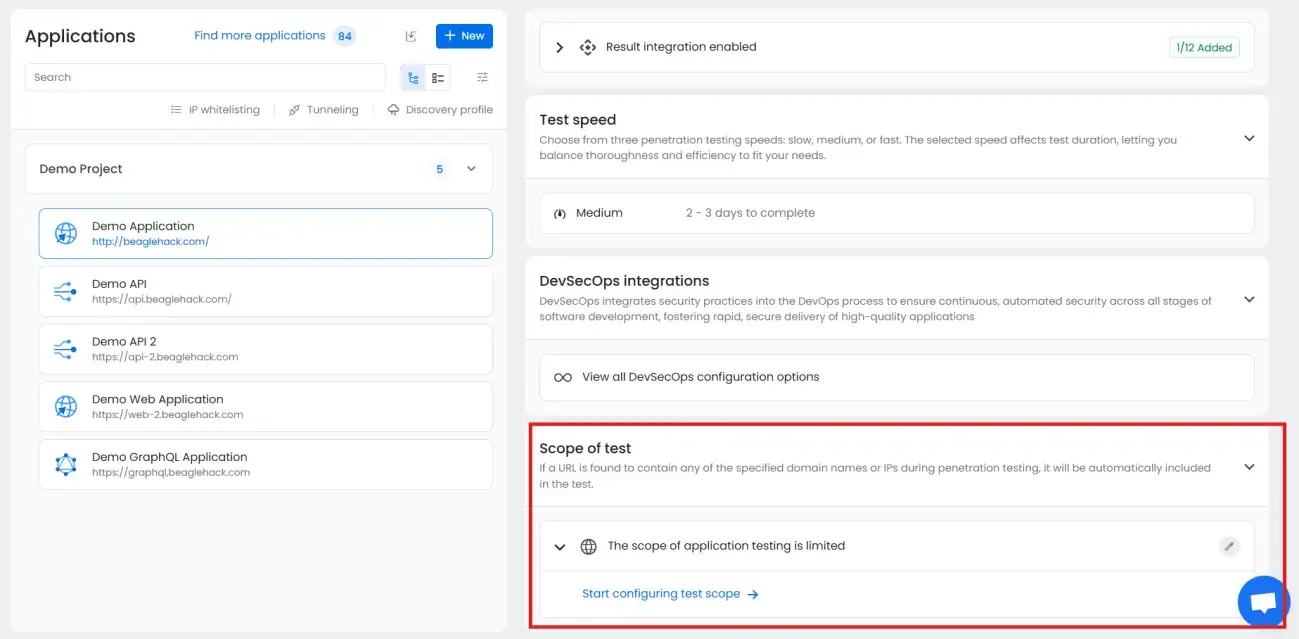
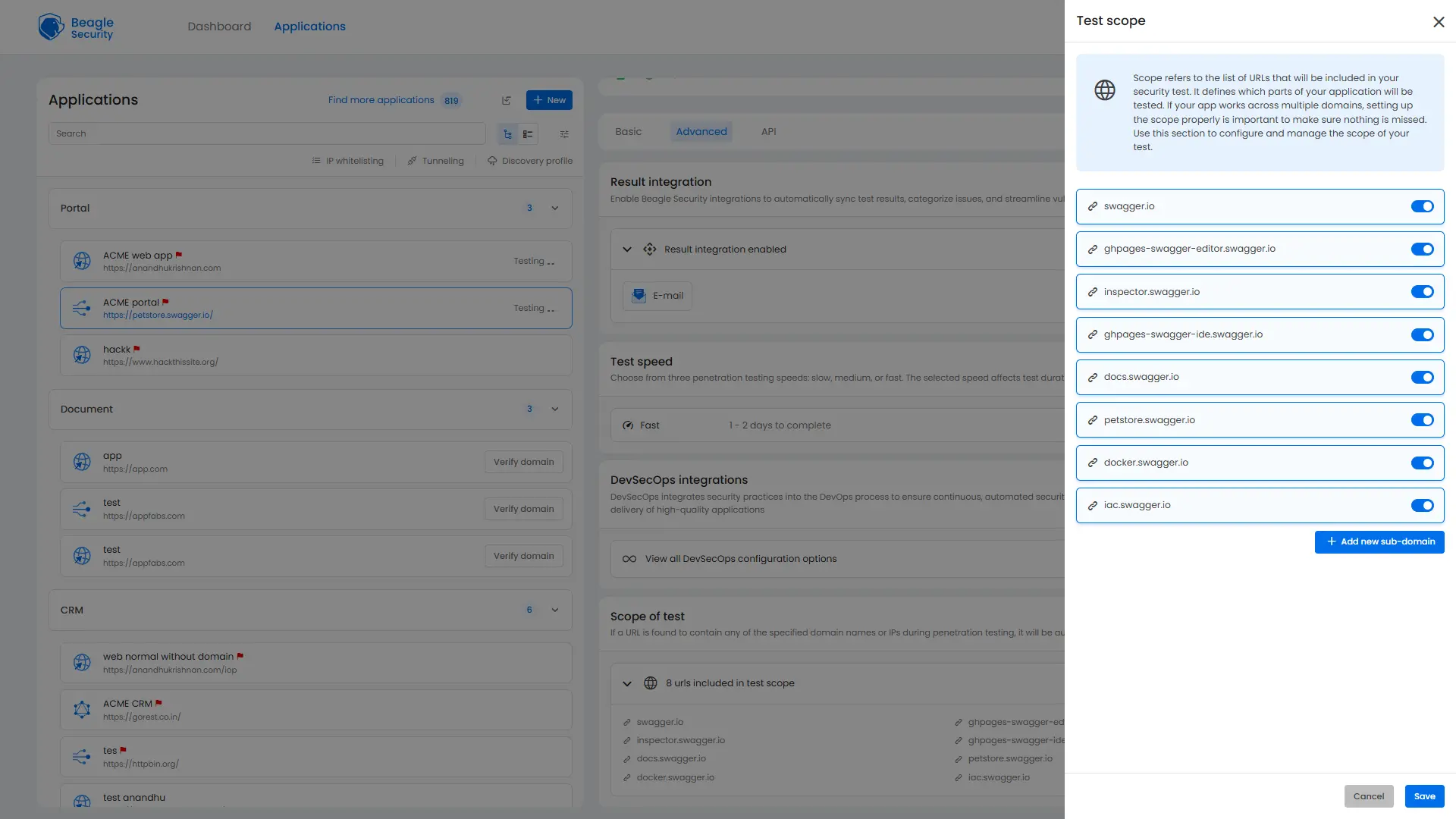
Beagle Security automatically discovers all associated subdomains as soon as you add your application. You can then easily review them and toggle each one on or off based on what you want to include in your tests.
Final thoughts
Defining your penetration testing scope isn’t just about setting boundaries, it’s about building a structured, strategic approach to assessing your security posture. A well-scoped test gives your organization the clarity and confidence to invest in the right areas, fix critical weaknesses, and demonstrate compliance to stakeholders.
By clearly identifying in-scope and out-of-scope assets, selecting the right testing type, and aligning with business objectives, you ensure every test produces meaningful results.
Ready to take your security to the next level? Run an automated penetration test to validate your defined scope instantly with Beagle security. Check out our 14 day free trial with all advanced features included or play around with our interactive demo to see what we have to offer.
FAQ
What factors affect the penetration testing scope?
The penetration testing scope depends on factors like the number of in-scope assets (web apps, IPs, APIs), testing approach (black box, white box, or gray box), and your organization’s compliance or business objectives. Larger environments and complex systems generally require broader, more detailed scopes.
Can scope influence the cost of a pentest?
Yes, the penetration testing scope directly affects cost. Broader scopes with multiple environments, user roles, or integrations take more time and expertise to assess, while focused scopes targeting critical assets can optimize both budget and outcomes.
Does pentesting time depend on the scope?
Absolutely. The size and complexity of your penetration testing scope determine the testing duration. It can range from a few days for small web apps to several weeks for multi-layered enterprise infrastructures.
A clear, well-defined scope ensures accurate timelines and efficient execution.
Who defines the penetration testing scope, the client or the tester?
The penetration testing scope is defined collaboratively between the client and the penetration testing provider. The client defines what matters most, and the tester defines how best to test it.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)