![Top AWS security tools by category [2025] Top AWS security tools by category [2025]](/blog/images/top-aws-security-tools-by-category.webp)
Amazon Web Services (AWS) powers millions of applications globally, making comprehensive security tooling essential for protecting cloud infrastructure and workloads. From cloud posture management to threat detection, securing AWS environments requires a layered approach across multiple security categories.
This guide explores the top AWS security tools across seven critical categories, combining AWS-native services with best-in-class third-party solutions.
Best AWS security tools by category [2025] TL;DR
| Category | Platform | Best for | Starting price |
|---|---|---|---|
| CSPM | SentinelOne Singularity Cloud | Multi-account cloud posture & runtime visibility | Quote-based |
| CNAPP | Wiz | Full stack cloud workload and runtime protection | $24,000/year for 100 workloads |
| Application security (DAST) | Beagle Security | Web app/API testing in AWS hosted environments | Starts at $1,188/year |
| Network security | Amazon Shield | DDoS protection for AWS apps on CloudFront/ALB | Standard tier free; Advanced from $3,000/month* |
| Data protection | Amazon Macie | Sensitive data discovery & classification in S3/dbs | Specific per-GB pricing |
| IAM | AWS Identity and Access Management (IAM) | Core identity & permissions controls in AWS | Free (with AWS account) |
| Threat detection & response (TDR) | Amazon GuardDuty | Continuous threat detection with AWS native logs | Free trial; pay-as-you-go |
Top 7 AWS security tools by category [2025]
AWS security tools for cloud security posture management (CSPM)
Cloud Security Posture Management (CSPM) tools continuously monitor AWS environments for misconfigurations, compliance violations, and security risks. With AWS’s vast array of services and complex permissions model, CSPM solutions help maintain security hygiene across multi-account setups. These tools assess configurations against frameworks like the CIS AWS Foundations Benchmark and provide visibility and automated remediation.
SentinelOne Singularity Cloud

SentinelOne Singularity Cloud is a cloud workload posture and runtime security platform that extends from workloads into AWS-native services for cloud posture and runtime protection. For AWS environments, it provides visibility into AWS Organizations, CloudTrail, AWS Config, EKS, ECS, Lambda, and runtime workloads for misconfiguration, compliance drift, and exploit paths.
Key features
Support for AWS Organizations and multi-account linkage for unified cloud inventory
Integrations with AWS CloudTrail, AWS Config, Amazon GuardDuty data and EKS/ECS containers
Automated remediation workflows and “Verified Exploit Paths” to prioritize real attack surfaces
Runtime visibility into containers and serverless functions inside AWS environments
Built-in compliance benchmarking (CIS AWS Foundations, PCI, ISO) and reporting
Pros
Strong multi-account visibility ideal for complex AWS organizations
Good runtime coverage of containers and serverless in AWS context
Unified agentless and agent-based scanning reduces blind spots
High marks in G2 for ease of use and support
Shortcomings/considerations
Quote-based pricing may be high for smaller teams
Setup for full multi-account AWS environments can require professional services
Some users note learning curve for full feature set in large AWS estates
SentinelOne pricing
SentinelOne Singularity Cloud offers custom enterprise pricing based on AWS resources, accounts, and workloads monitored. Contact SentinelOne for a tailored AWS-specific quote.
SentinelOne ratings & reviews
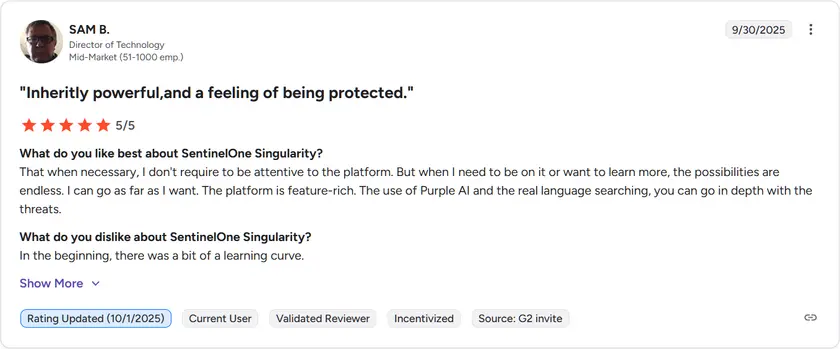
SentinelOne Singularity Cloud holds a strong 4.5 out of 5 rating on G2 based on hundreds of verified reviews. Users frequently highlight its robust AWS integrations such as support for CloudTrail, Config, and AWS Organizations, which make it especially suitable for large multi-account deployments.
Some reviews mention that the platform’s advanced capabilities can result in a steeper learning curve during initial setup and may require careful configuration to control costs in complex AWS environments.
Cloud native application protection platform for AWS security (CNAPP)
Cloud Native Application Protection Platforms (CNAPPs) provide comprehensive security coverage across AWS workloads, from EC2 instances to EKS containers and Lambda functions. CNAPPs unify multiple security capabilities like vulnerability management, configuration analysis, runtime protection into a single platform. For AWS environments running modern cloud-native architectures, CNAPPs offer visibility and protection at scale.
Wiz

Wiz is a full-stack cloud security CNAPP built for AWS, Azure, and GCP, designed to detect risks across infrastructure, containers, serverless, and IaC before and during runtime. For AWS customers, Wiz integrates via AWS Marketplace, supports discovery of unmanaged workloads, and covers container/ Kubernetes security, IAM risk, and runtime threat context.
Key features
Agentless scanning of AWS workloads, containers (EKS/ECS), Lambda functions, and Kubernetes environments
Infrastructure-as-Code (IaC) scanning for AWS CloudFormation and Terraform
Unified risk visibility across AWS workload types, privilege risks, misconfigurations
Integrates with AWS Marketplace for deployment and billing within AWS environment
Runtime context and AWS threat detection for cloud workloads
Pros
Broad AWS workload coverage (EC2, ECS/EKS, Lambda, IaC)
Agentless method can simplify deployment
Excellent ratings and reputation in cloud security category
Strong AWS Marketplace support and private pricing alignment
Shortcomings/considerations
High cost for large environments, pricing often cited as large enterprise scale
Alert volume may be high unless tuned
Some smaller teams may find full CNAPP scope beyond their current needs
Wiz pricing

Source: AWS Marketplace
Wiz Essential: $24,000/year(100 workloads)Wiz Advanced: $38,000/year (100 workloads) as reference pricing.
The actual pricing depends on workload volume and usage.
Wiz ratings & reviews
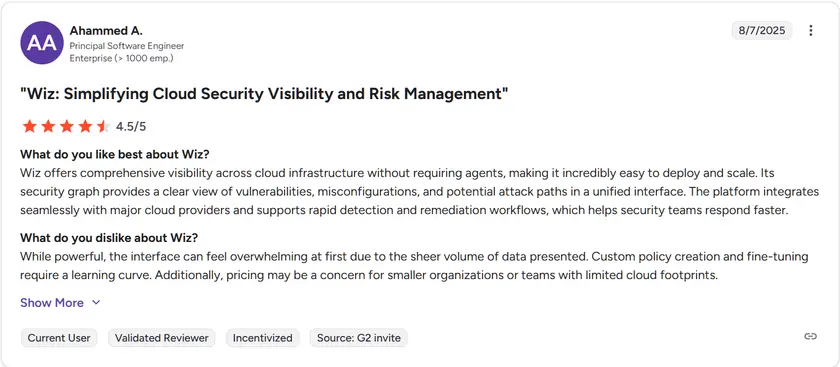
Wiz is rated 4.7 out of 5 on G2 and is one of the highest-rated CNAPP platforms available today. Customers appreciate its agentless scanning model and its ability to secure AWS workloads across EC2, ECS, Lambda, and Kubernetes environments without impacting performance. A few users mention that alert volume can be high until policies are tuned properly, and that pricing can increase for very large AWS organizations.
AWS security tools for application security/DAST
Applications and APIs hosted on AWS require continuous security testing to identify vulnerabilities before attackers do. Dynamic Application Security Testing (DAST) simulates real attacks against running applications, uncovering security flaws in AWS-hosted web apps, APIs, and microservices. Integrating DAST into AWS DevOps pipelines enables shift-left security without slowing deployment velocity.
Beagle Security
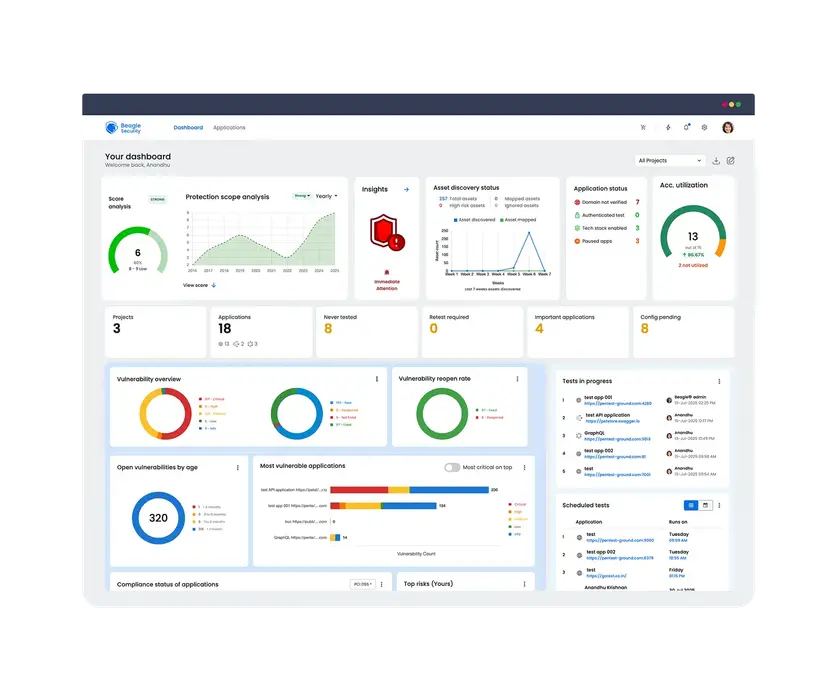
Beagle Security delivers AI-powered penetration testing designed for web applications and APIs hosted on AWS cloud environments. With seamless integration into AWS CodePipeline and AWS DevOps tools, Beagle enables automated security testing throughout the development lifecycle.
The platform supports applications running on Amazon EC2, Amazon ECS, Amazon EKS, and behind Amazon API Gateway, providing vulnerability discovery tailored to AWS-hosted architectures.
Key features
Automated penetration testing of web apps and APIs on AWS environments
Integration with AWS CodePipeline, AWS CodeBuild, and CI/CD workflows for AWS-centric DevSecOps
Support for AWS-hosted containers, microservices behind Amazon ECS/EKS, and API Gateway endpoints
AI-driven vulnerability validation to reduce false positives and speed remediation
Compliance-ready reporting including OWASP Top 10, ISO 27001, and AWS best practices
Pros
Strong AWS integration and DevOps friendly workflow for AWS-hosted applications
Fast setup for AWS web apps behind standard services
Developer-friendly reports and actionable fix guidance
Good G2 ratings and positive user feedback
Shortcomings/considerations
As DAST-focused, it may not cover infrastructure or container runtime threats
Larger enterprise AWS architectures may require additional custom configuration
Pricing is quote-based which means variable cost transparency
Beagle Security pricing
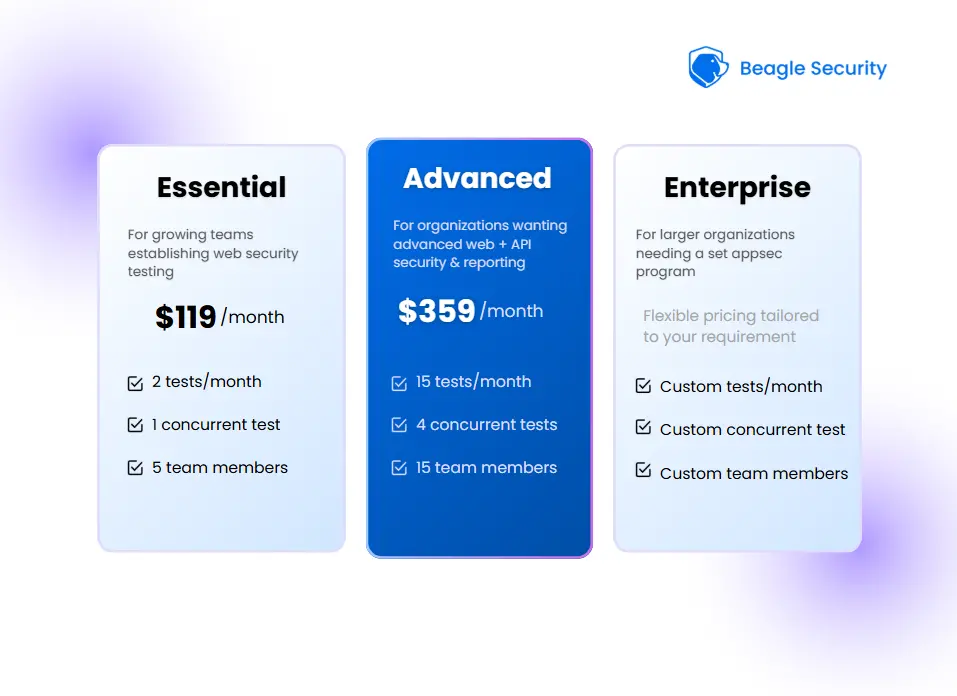
Essential plan: $1,188/year
Advanced plan: $4,308/year
Enterprise plans: Starting at $6,850/year
Beagle Security ratings & reviews
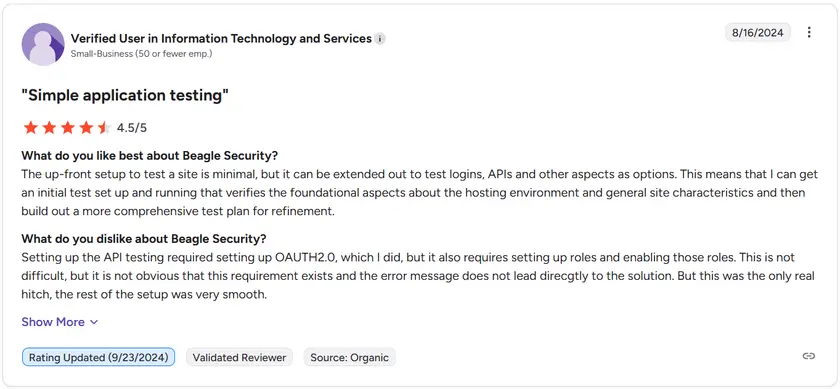
Beagle Security currently maintains a 4.7 out of 5 rating on G2 from around 87 verified users. Reviewers frequently praise its simplicity, automation depth, and strong AWS compatibility, particularly for AWS CodePipeline integration and continuous testing of EC2, ECS, and API Gateway workloads.
Some feedback points out that while it excels in application and API testing, organizations with highly customized AWS environments may want more tailored configuration options.
AWS security tools for network security
Network security forms the first line of defense for AWS infrastructure, protecting against DDoS attacks, unauthorized access, and network-based exploits. AWS Shield provides managed DDoS protection for applications running on AWS, automatically detecting and mitigating attacks. Combined with AWS Web Application Firewall (WAF), Shield safeguards applications at the network edge through Amazon CloudFront and Application Load Balancers.
Amazon Shield
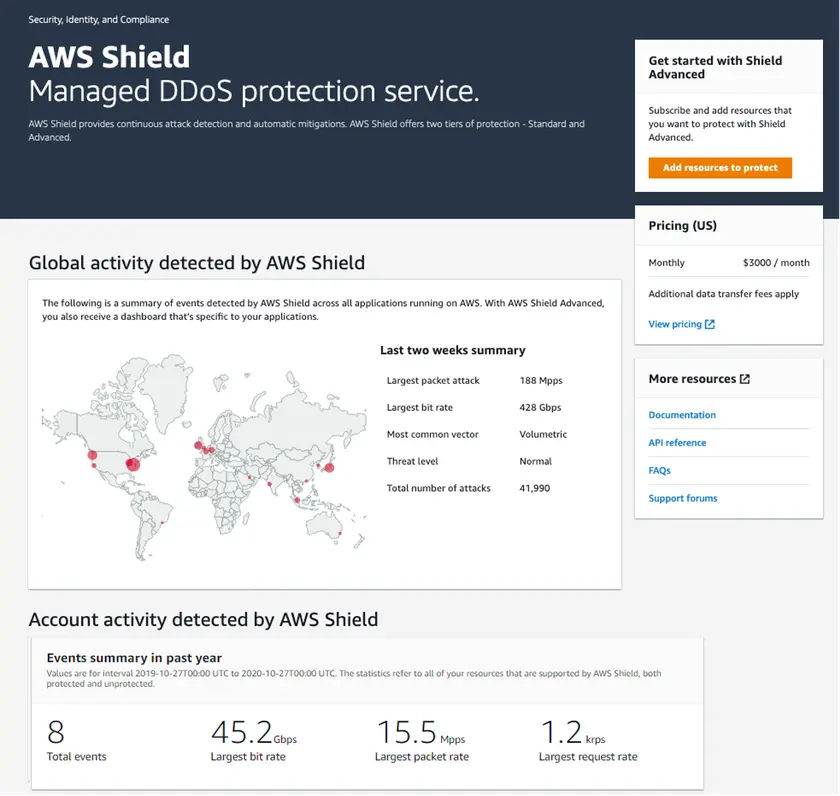
Amazon Shield is an AWS-native managed DDoS protection service. In AWS security architecture, Shield Standard is automatically applied to all AWS customers at no extra cost and protects against most common layer-3 and layer-4 attacks. Shield Advanced offers additional protections, cost-cap management, and visibility for AWS assets such as Application Load Balancers, CloudFront distributions, and Route 53.
Key features
Automatic DDoS protection for AWS resources in Standard tier
For Shield Advanced: advanced traffic engineering, cost-protection, and access to AWS DDoS Response Team (DRT)
Integration with AWS WAF, CloudFront, and Route 53 for comprehensive network layer defense
Detailed metrics and attack telemetry via Amazon CloudWatch and AWS WAF logs
Pros
Seamless protection for AWS customers (Standard tier)
Deep integration with AWS network services
Useful for high-availability web apps and public-facing services
AWS native billing and support model
Shortcomings/considerations
Shield Advanced adds significant cost for smaller applications
Focus is on network/DDoS layer; does not cover application logic vulnerabilities
Some configuration and alert fine-tuning required for optimum benefit
Amazon Shield pricing
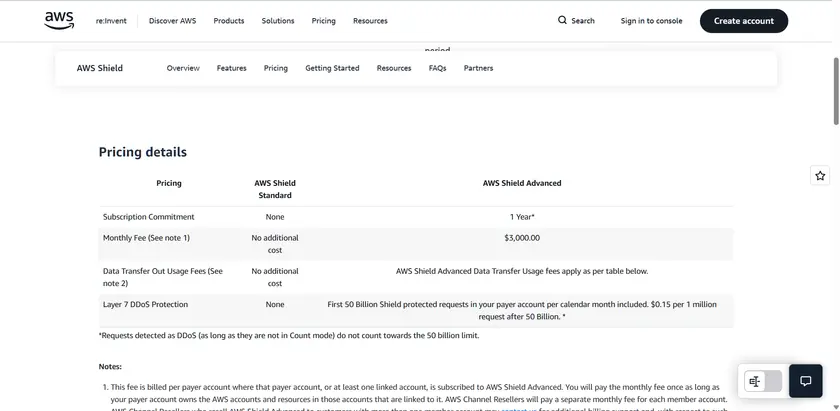
Shield Standard: No additional cost.
Shield Advanced: $3,000/month plus usage-based fees (per AWS published details).
Contact AWS for multi-region enterprise pricing.
Amazon Shield ratings & reviews
Amazon Shield does not have a formal G2 listing but receives consistently positive feedback across AWS forums and customer testimonials. Users appreciate that Shield Standard offers built-in DDoS protection at no additional cost, while Shield Advanced provides enhanced visibility and 24x7 DDoS response support. Some customers note that tuning alerts and understanding billing for the Advanced tier can take time, especially for teams new to AWS network security.
Data protection tools for AWS security
Protecting sensitive data in AWS requires automated discovery and classification across S3 buckets, databases and data lakes. Amazon Macie uses machine learning to identify personally identifiable information (PII), financial data and other sensitive content stored in Amazon S3. With data breaches increasingly targeting cloud storage, Macie helps organizations meet compliance requirements and prevent unauthorized data exposure.
Amazon Macie
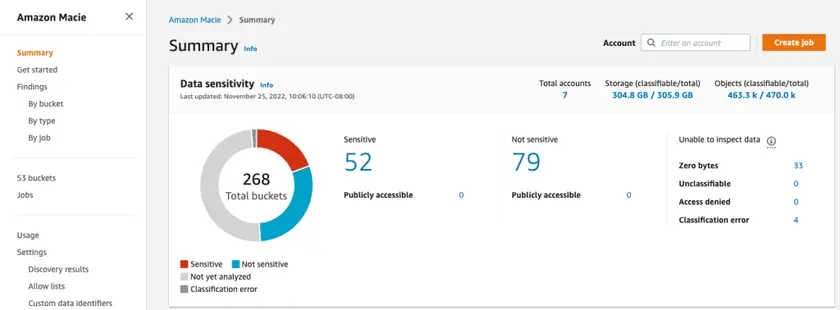
Amazon Macie is a dedicated AWS service to discover, classify and protect sensitive data in Amazon S3, Amazon RDS and other AWS data stores. For AWS users it offers context-aware classification, automated sensitive-data alerts, and integration with AWS Security Hub and AWS CloudTrail.
Key features
Automatic discovery of PII and sensitive information in S3 buckets and AWS data stores
ML-based classification and risk scoring of AWS stored data
Automated alerts for risky data exposure and anomalous behavior
Integration with AWS Governance, Risk & Compliance workflows and AWS Security Hub
Pros
Native AWS service with seamless account integration and minimal setup
Helps meet compliance obligations for GDPR, HIPAA, PCI when used with AWS data
Continuous monitoring of data exposure and anomalies in AWS data stores
Shortcomings/considerations
Cost can grow significantly with large data volumes scanned
Focus is on stored data rather than runtime or use-path threats
Some users may require additional third-party tooling for advanced DSPM (Data Security Posture Management) features
Amazon Macie pricing
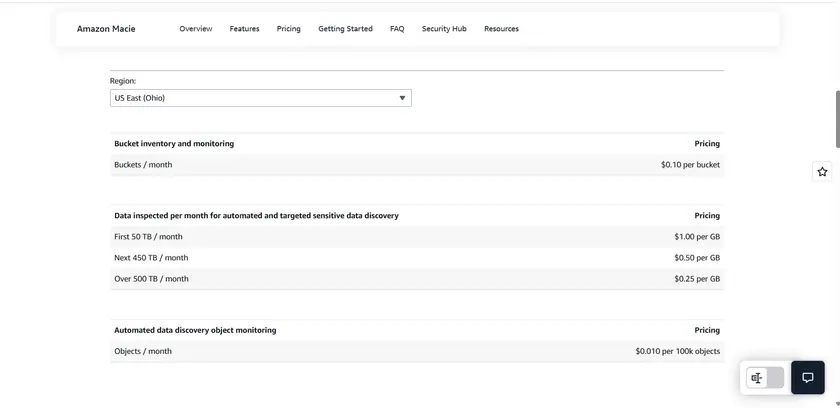
Pricing is based on the amount of data processed and custom classification jobs. AWS publishes specific per-GB pricing.
Contact AWS for tailored estimate.
Amazon Macie ratings & reviews
Amazon GuardDuty has a 4.1/5 rating out of 56 reviews in G2. It is widely praised in the AWS community for its data discovery and classification accuracy. Security professionals value its ability to automatically identify sensitive data within S3 buckets and align findings with compliance frameworks such as GDPR and HIPAA. The main drawback mentioned by users is that costs can grow quickly for large-scale data scanning, requiring careful budget monitoring.
AWS tools for IAM
AWS Identity and Access Management (AWS IAM) serves as the foundation of AWS security, controlling who can access which resources and what actions they can perform. Implementing least-privilege access through IAM policies, roles, permission boundaries and attribute-based access control prevents unauthorized access and limits the blast radius of compromised credentials. Proper IAM configuration is essential for every AWS deployment, regardless of size or complexity.
AWS IAM
AWS IAM is the core AWS service that manages identities, access, roles, and permissions across AWS accounts, services and resources. AWS IAM Access Analyzer, role-based trust policies and cross-account permissions give security teams fine control over access in AWS Organizations.
Key features
User, role and group management, permission policies and conditions
Role-based cross-account access and integration with AWS Organizations
AWS IAM Access Analyzer for identifying unintended access paths
Integration with AWS CloudTrail and AWS Config to detect policy changes and risky permissions
Pros
Free with AWS account; deep integration with all AWS services
Fine-grained control over access and trust relationships inside AWS
Continuous evolution and AWS native support
Shortcomings/considerations
Complexity grows quickly in large environments; misconfiguration risks are high
Requires strong governance and monitoring beyond the service itself
IAM alone does not enforce runtime security or detect attacks. Must be complemented by other tools
AWS IAM pricing
AWS IAM is free to use within standard AWS accounts; charges may apply for resources used by IAM features (e.g., AWS Directory Service) but not for basic IAM functions.
AWS IAM ratings & reviews
AWS Identity and Access Management, while not rated on G2, is universally recognized as a cornerstone of AWS security. Users highlight its granular access control, policy flexibility, and integration with all AWS services as core strengths for building secure environments. The most common challenge cited is managing complexity at scale, as large organizations must maintain disciplined governance and regular policy audits to prevent privilege mismanagement.
AWS security tools for threat detection & response (TDR)
Real-time threat monitoring, AWS-native detection and security event correlation are key to modern AWS security operations. Amazon GuardDuty provides continuous threat detection for AWS accounts and workloads, analyzing billions of events across AWS CloudTrail, VPC Flow Logs and DNS logs. Using machine learning and threat intelligence, GuardDuty identifies suspicious activity like cryptocurrency mining, credential compromise and reconnaissance attempts. As an AWS-native service, GuardDuty requires no agents or additional infrastructure, enabling threat detection within minutes of activation.
Amazon GuardDuty
Amazon GuardDuty is an AWS native threat detection service that continuously monitors AWS accounts, workloads and data stores for malicious or unauthorized behavior. It leverages AWS CloudTrail, Amazon VPC Flow Logs, Amazon DNS logs and other sources to generate findings, and integrates with AWS Security Hub, Amazon EventBridge and AWS Lambda to orchestrate responses.
Key features
Agentless threat detection across AWS account activity and workloads
Integration with AWS CloudTrail, VPC Flow Logs, DNS logs and S3 data events
Automated remediation with AWS Lambda + Amazon EventBridge workflows
Native integration with AWS Security Hub for centralized visibility
Pros
Rapid deployment and minimal configuration required
Native AWS service with seamless billing and support
Good value for continuous monitoring of AWS activity
Shortcomings/Considerations
Focus is on threat detection not prevention and requires action automation
Does not replace full incident response platform or SOAR solution
AWS logs volume can generate many findings and requires tuning and process
Amazon GuardDuty pricing
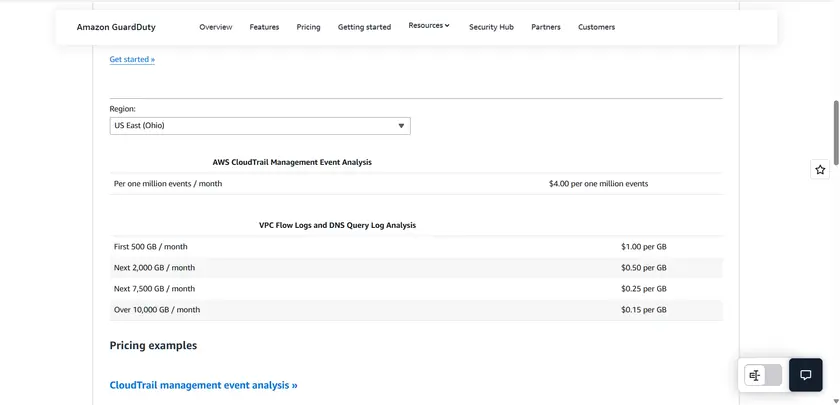
Amazon GuardDuty costs vary by region and data volume (CloudTrail events, VPC Flow Log 1:1 metric).
Customers should consult AWS pricing pages for exact amounts.
Amazon GuardDuty ratings & reviews
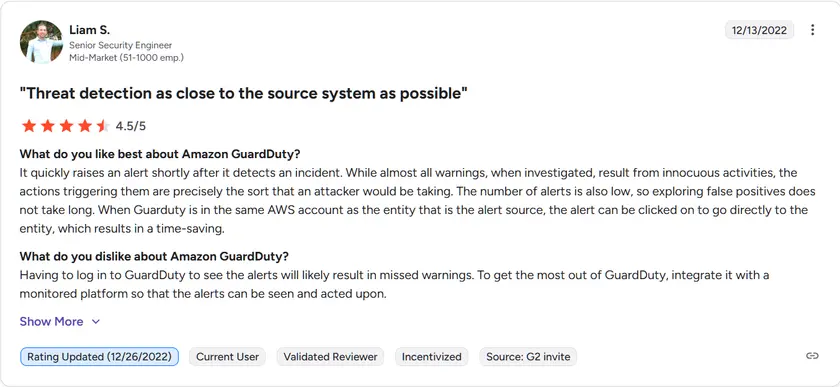
Amazon GuardDuty has a 4.1/5 rating out of 56 reviews in G2. User feedback from AWS Marketplace and professional forums is consistently positive. Organizations appreciate its ability to deliver actionable security findings almost immediately after activation, using data sources such as CloudTrail logs and VPC Flow Logs. Some users mention that GuardDuty works best when paired with automated workflows for response and that managing large volumes of alerts can require fine-tuning to avoid fatigue.
Top considerations when choosing AWS security tools
When choosing from among the top AWS security tools, here are key decision criteria:
- Specific use case
Match your security tool selection to your specific AWS challenges. If you’re primarily concerned with S3 data protection, Amazon Macie provides native integration. For comprehensive application security testing across EC2, ECS, and EKS deployments, solutions like Beagle Security offer specialized DAST capabilities with AWS DevOps integration.
- Integration
Prioritize tools that integrate seamlessly with your existing AWS services. AWS-native tools like Amazon GuardDuty and AWS IAM require no additional authentication and feed directly into AWS Security Hub. Third-party solutions should offer AWS Marketplace deployment, CloudFormation templates, and API-level integration with CloudTrail and AWS Config.
- Ease of use
Consider how tools integrate with the AWS Management Console and existing workflows. AWS-native services provide familiar interfaces and consistent user experience. Third-party tools should offer intuitive dashboards and minimize context switching between platforms.
- Reports and analytics
Evaluate reporting capabilities and integration with Amazon CloudWatch for unified monitoring. Look for tools that provide compliance-ready reports mapped to frameworks like CIS AWS Foundations Benchmark, PCI DSS and HIPAA. Custom dashboards and automated alerting help security teams prioritize and remediate risks.
- Support
AWS-native tools include support through AWS Support plans, while third-party vendors offer varying levels of assistance. Evaluate documentation, vendor responsiveness, and community resources. Enterprise deployments may require dedicated technical account managers.
- Budget
Understand pricing models, pay-as-you-go, subscription-based or custom enterprise pricing. AWS-native tools often use consumption-based pricing that scales with usage; third-party solutions may charge per account or per asset. Factor in costs for multi-account AWS Organizations and high-traffic applications.
- Deployment options
AWS-native tools offer instant deployment with no infrastructure overhead, while third-party solutions may require agents, network access or dedicated resources. Consider whether an agentless or fully managed approach meets your needs and evaluate setup complexity across AWS regions and accounts.
Final thoughts
Securing AWS environments requires a multi-layered approach spanning posture management, application security, network protection, and threat detection. While AWS-native tools like Amazon GuardDuty, Amazon Macie and AWS IAM provide essential baseline security, specialized third-party solutions like Wiz for CNAPP and Beagle Security for application testing add depth and advanced capabilities.
The right combination of AWS security tools depends on your specific workloads, compliance requirements and organizational maturity. Organizations running modern cloud-native applications on AWS benefit from integrating DAST solutions like Beagle Security into their CI/CD pipelines, while enterprises with complex multi-account structures may prioritise posture and runtime visibility using SentinelOne or Wiz.
Start by assessing your highest-risk AWS assets and compliance obligations, then build your security stack accordingly. For comprehensive application and API security testing that integrates seamlessly with AWS DevOps workflows, explore how Beagle Security can strengthen your AWS security posture without slowing development velocity.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)