
Cyberattacks don’t knock before they break in. Instead, attackers begin by probing your external defenses. This includes testing your public-facing websites, scrutinizing your network perimeter, and searching for any weakness visible from the outside world.
External penetration testing simulates exactly this real-world attack scenario, helping you discover and fix vulnerabilities before malicious actors exploit them.
In this blog, we will break down what external pentesting involves, when your organization needs it, and how to approach it strategically.
What is external penetration testing?
External penetration testing, sometimes called external pentesting, is a controlled simulation of a cyberattack on your organization’s publicly accessible assets.
Unlike general vulnerability scans, external penetration tests are conducted by ethical hackers who use the same tactics, techniques, and procedures as real-world attackers.
The purpose is to find and exploit potential weaknesses just like a hacker would to give your security team a proper overview.
Core concepts of external pentesting:
- Simulated real-world attacks: External pen testers mimic cybercriminals by probing your systems from the outside.
- Targets external-facing systems: This includes websites, VPNs, firewalls, DNS servers, cloud environments, and exposed APIs.
- Risk validation: Testers don’t just report vulnerabilities, they exploit them in a safe, controlled manner to prove impact.
- Actionable insights: The final report includes detailed findings, risk ratings, and remediation guidance.
Internal vs external penetration testing
Internal vs external penetration testing is not a matter of choosing one or the other, they answer different security questions. For most organizations, both are essential parts of a strong cybersecurity strategy since they focus on different attack surfaces.
| Category | Internal penetration testing | External penetration testing |
|---|---|---|
| Attack origin | Simulates an insider threat or compromised employee | Simulates an outside attacker |
| Access assumption | Tester begins with network access (e.g., through VPN or LAN) | Tester has no privileged access if blackbox testing and limited if grey box |
| Primary focus | Internal systems, lateral movement, privilege escalation | Firewalls, web apps, open ports, exposed credentials |
| Typical goals | Identify risks post-breach (e.g., ransomware spread) | Identify initial access points to prevent a breach |
What gets covered in an external pentest?
Before launching a test, it’s critical to define which assets will be tested and what kind of activities are allowed.
Here’s what’s typically covered in a standard external penetration testing scope:
Public-facing web applications
These are prime targets for attackers. Testers assess for common vulnerabilities like SQL injection, cross-site scripting (XSS), broken access controls, and authentication flaws.
Exposed network services
Open ports, exposed databases, FTP servers, and VPN gateways are examined to uncover vulnerabilities.
Cloud infrastructure (AWS, Azure, GCP)
Misconfigured storage buckets, overly permissive IAM roles, and exposed APIs can all be leveraged in real-world attacks.
Email and DNS services
Phishing attacks often start with email. Pentesters may examine SPF, DKIM, and DMARC records for weaknesses, as well as DNS configurations that can be abused for subdomain takeovers.
Credential leaks and dark web exposure
External pentesters may hunt for stolen employee credentials or sensitive data leaked on the dark web that could aid an attacker.
Firewall and perimeter defense evasion
Testing often includes attempts to bypass firewalls or intrusion prevention systems to identify any gaps in perimeter controls.
The final scope depends on your business size, industry, threat model, and budget. A reputable provider will work with you to define a scope that matches your risk appetite and regulatory obligations.
How is an external pentest done?
Unlike internal tests that may require on-site access or VPN credentials, external penetration testing can be conducted remotely by a third-party security firm. The key is to collaborate closely before the test begins to define goals and expectations.
The external pentesting process can be explained in 5 key steps:
- Scoping & planning
- Identify which IPs, domains, and applications will be tested
- Set clear rules of engagement (e.g., testing hours, no-go zones, legal constraints)
- Agree on test depth (black-box vs gray-box)
- Reconnaissance
- Passive and active scanning of external assets
- Mapping subdomains, DNS entries, open ports, services, and software versions
- Vulnerability discovery
- Manual and automated techniques to find exploitable flaws
- Examples: outdated software, weak encryption, logic flaws, misconfigurations
- Exploitation (safely)
- Ethical hackers attempt to exploit discovered vulnerabilities
- Controlled proof-of-concept attacks show real-world impact
- Reporting & remediation guidance
- Detailed technical report with severity ratings and recommended fixes
- Executive summary for non-technical stakeholders
- A retest to validate fixes
When should you conduct an external penetration test?
External pentesting is typically done in the following scenarios:
- Annual security assessments
- Before major product launches
- After significant infrastructure changes
- Post-merger or acquisition
- For compliance requirements
- After security incidents
- When expanding internet-facing services
The recommended frequency for external pentesting is annually at the minimum but you can conduct more based on the scope and size of your organization.
How to run an external application pentest using the Beagle Security platform
Beagle Security makes external application pentesting very easy to implement and scale. Here’s how to do it.
Getting started
Create new application: Click “Add Application” and select the application type from three options: Website (traditional web applications), API (REST), or GraphQL (modern API implementations).
Application details: Enter your details such as specific application name and complete URL that will serve as the primary target for AI penetration testing. You can also set the importance of said application and configure application URL accessibility.
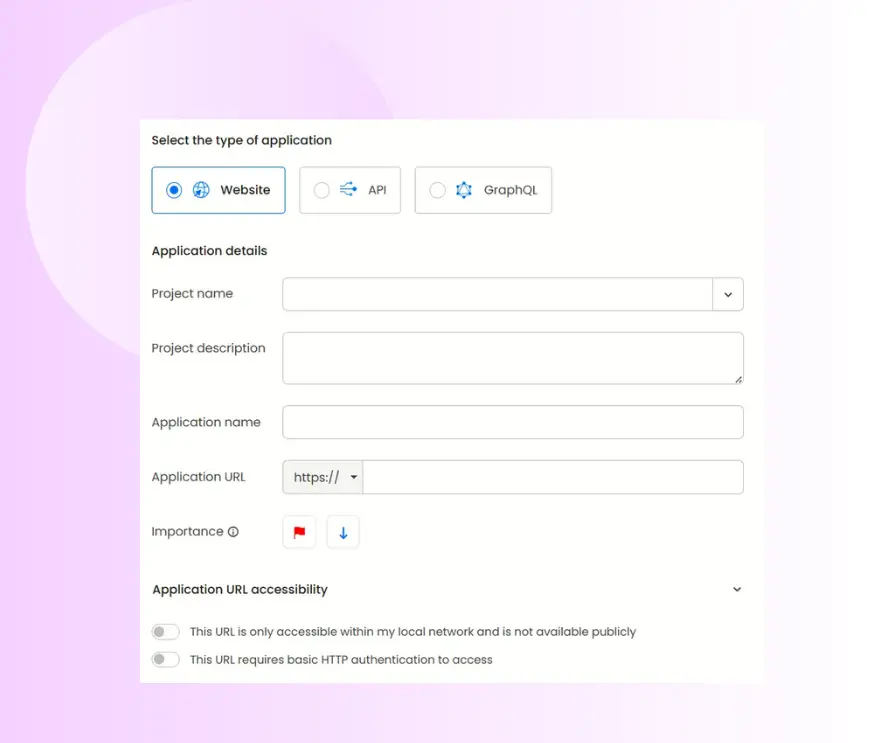
Black box vs grey box penetration testing selection
When planning a penetration test, one of the first decisions you’ll need to make is what kind of testing approach suits your goals: black box or grey box.
Black box testing simulates an attack by an outsider with no inside knowledge of your systems while Grey box testing gives the tester partial knowledge of the system.
When it comes to external penetration testing, black box testing is the immediate start. To do this, proceed directly to the ‘start test’ button after adding your application.
This simulates attacker perspective with no privileged access.
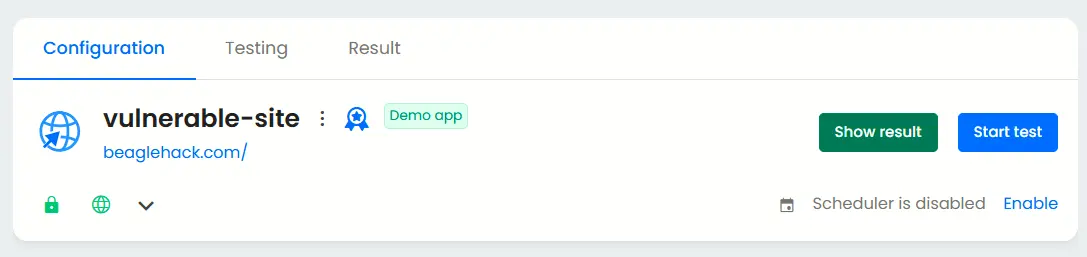
Additional configurations for grey box penetration test
Now that we’ve covered black box testing, we can now look into grey box testing which involves various types of login credentials.
Authenticated testing
Enable “authenticated testing” at the bottom of basic tab and provide test credentials. This allows AI modules to assess post-login functionality, user role permissions, and authenticated attack surfaces.
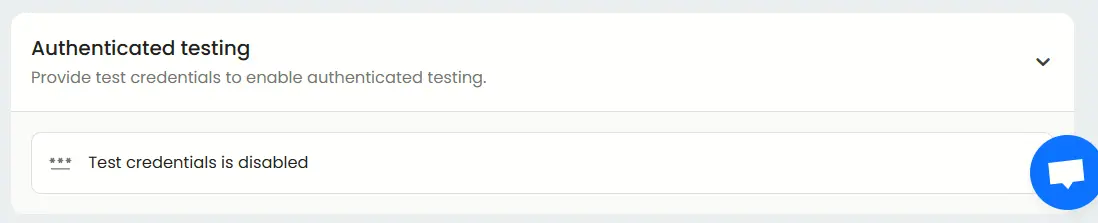
Here you can set up credential type which includes logins, signup and third-party log in.
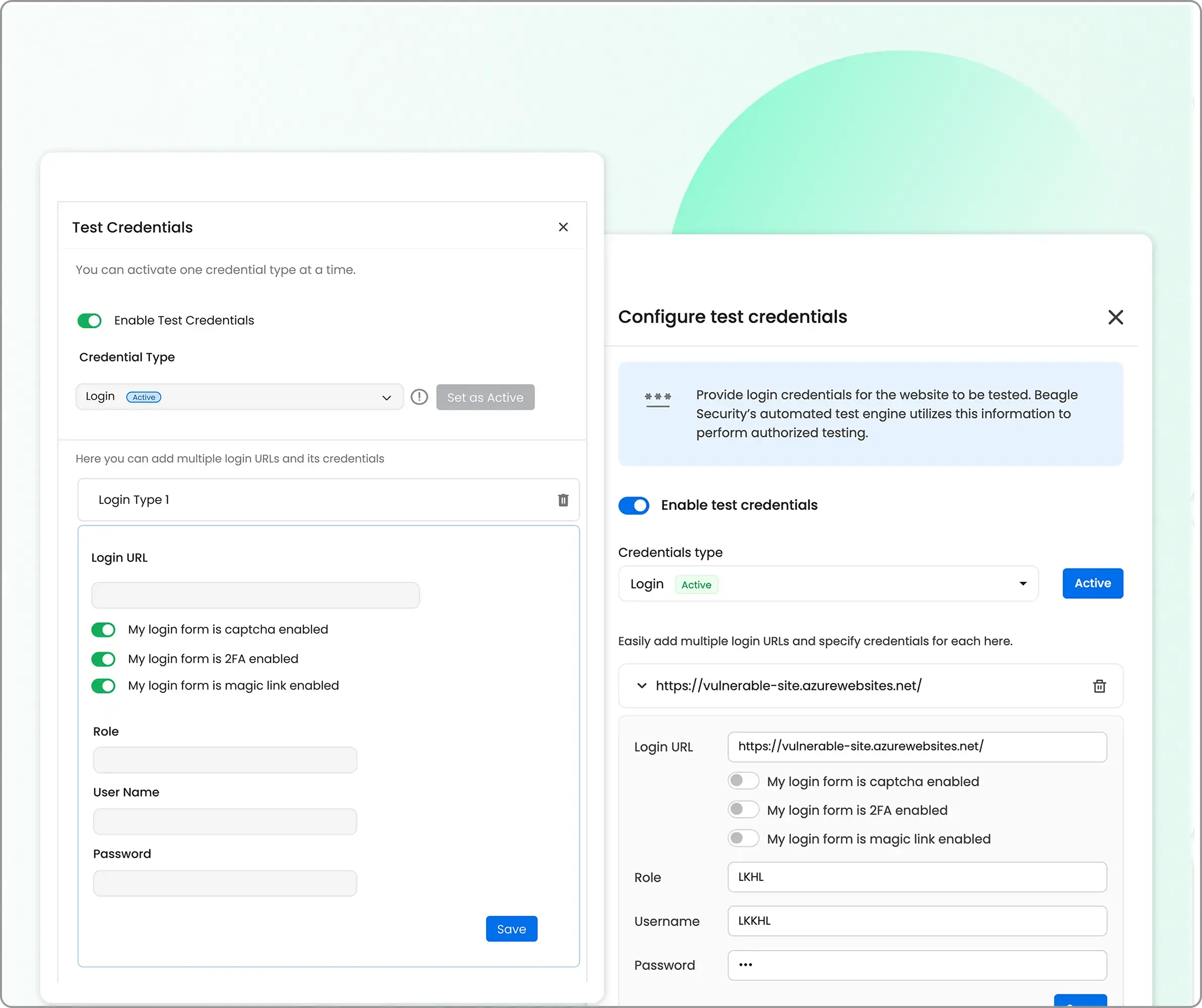
The recommended login is the “recorded login” option which can be set up by Beagle Security’s chrome extension.
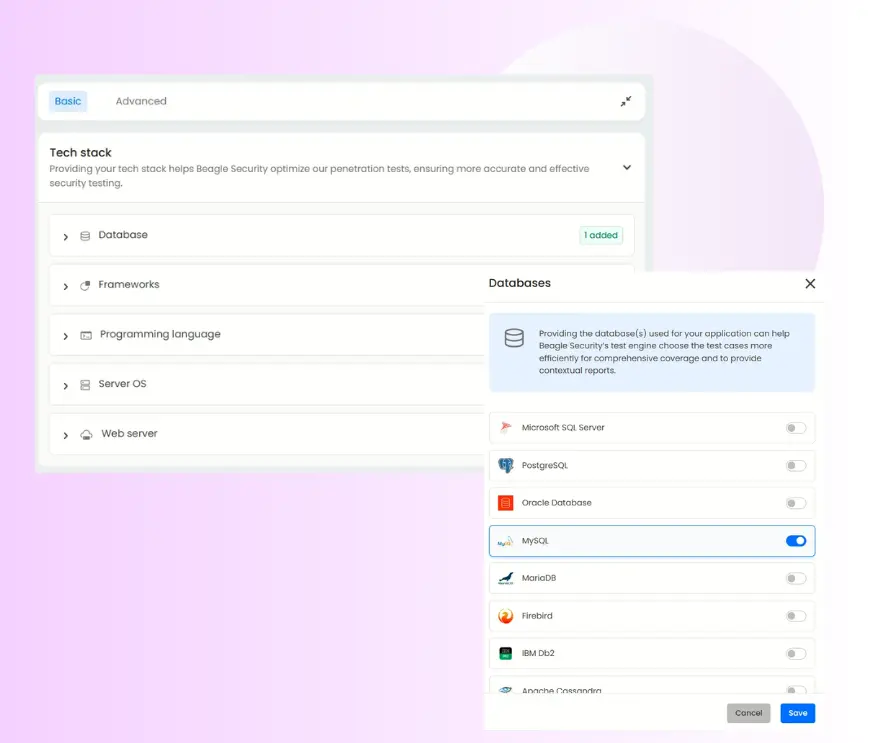
Tech stack configuration
The tech stack section is found under the ‘basic’ tab. Here you can add the necessary stacks which helps Beagle Security optimize our penetration tests for your application.
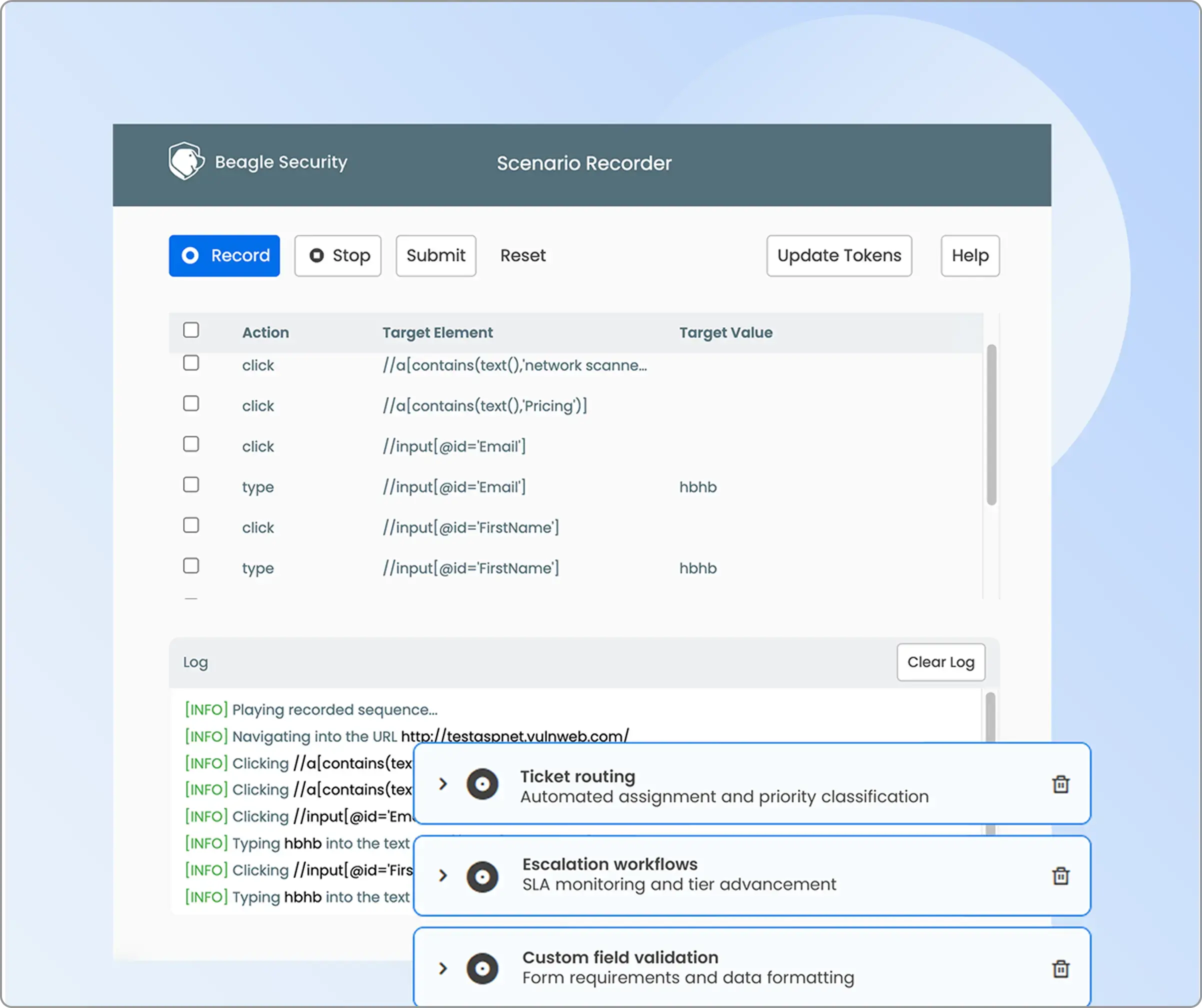
Business logic recording
The business logic recording section is located under the advanced tab.
Enable “Scenario recording” using the Beagle Security browser plugin to capture user workflows, multi-step transactions, and application-specific business processes for targeted security assessment.
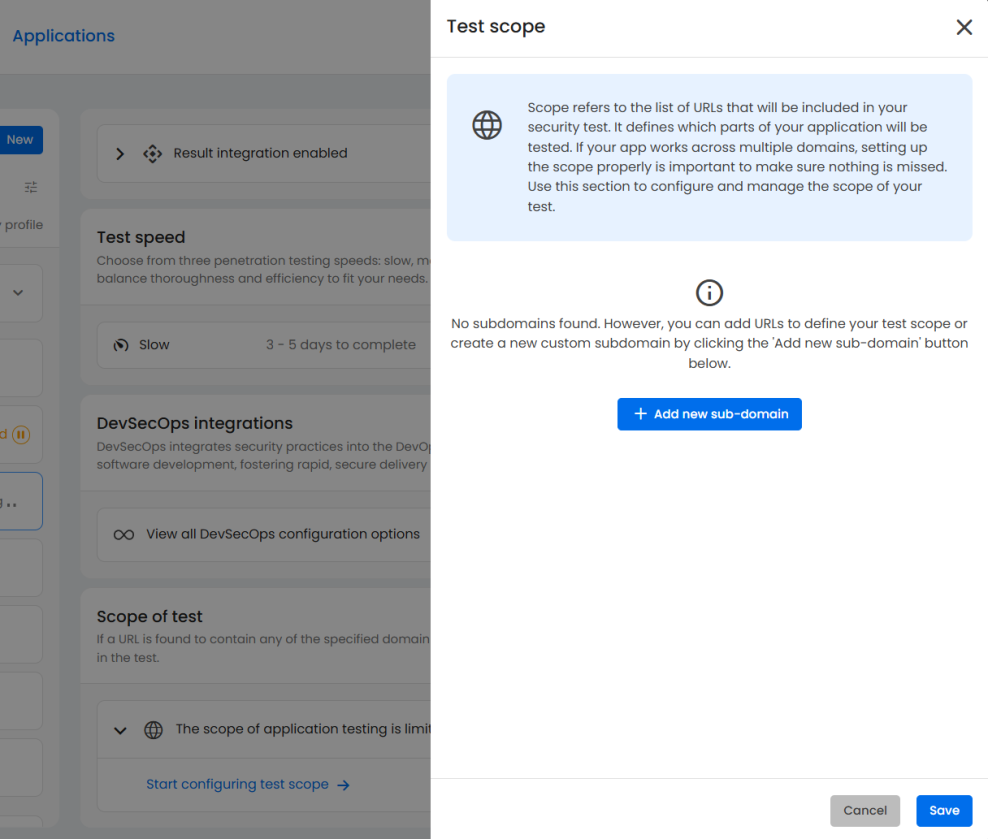
Pentesting scope
In penetration testing, scope refers to the list of subdomains and associated URLs that will be included in the security assessment. It defines the boundaries of what can and cannot be tested.
If your application works across multiple domains, this makes sure that nothing is missed.
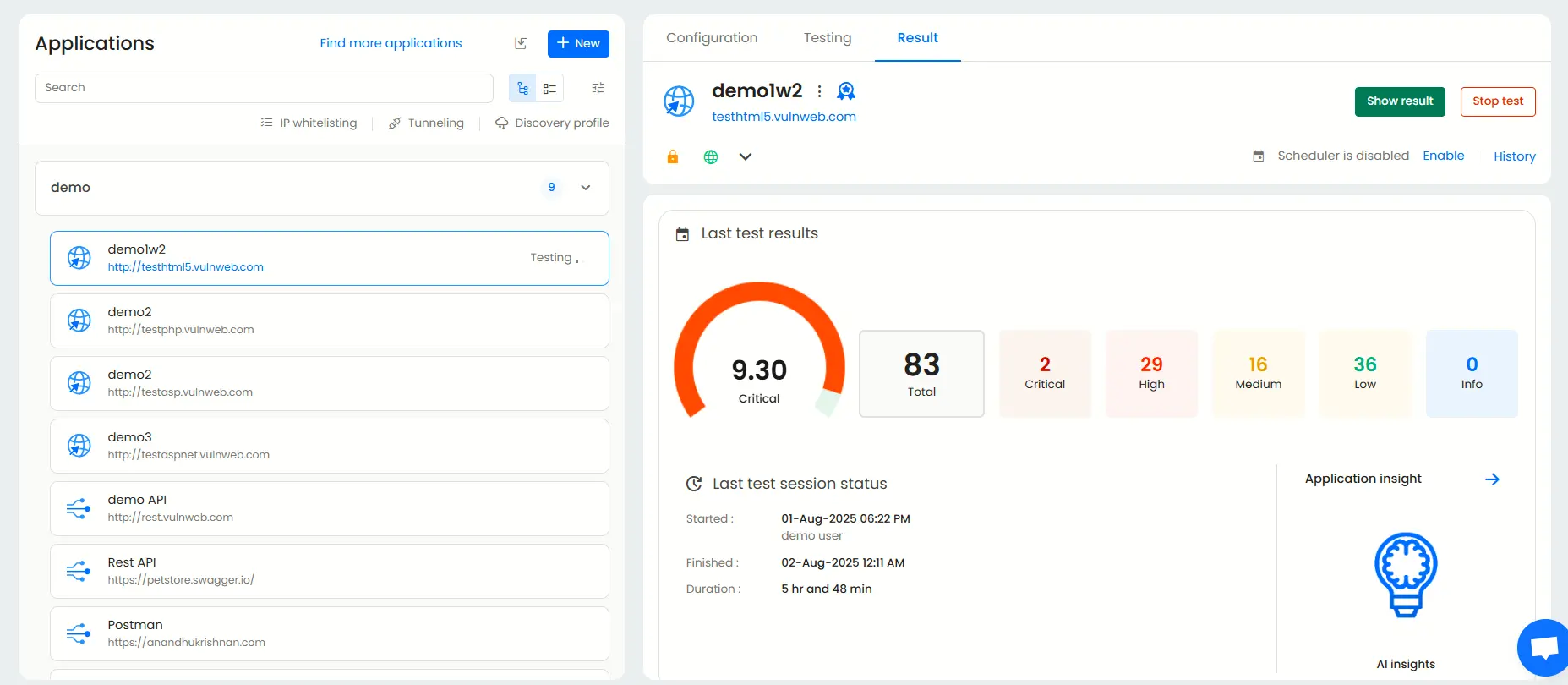
Viewing the penetration test results and reports
Application dashboard
This is where you can get an overview of each individual application.
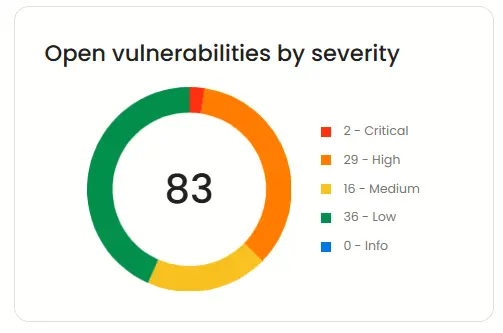
Open vulnerabilities by severity
This widget allows you to see vulnerabilities that exist currently and how severe they are.
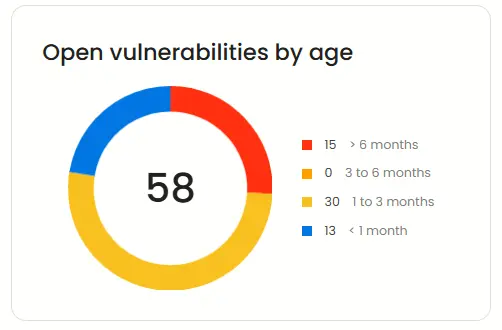
Open vulnerabilities by age
Beagle Security also categorizes risks present in your application based on how long they have been in your application, as shown in the dashboard widget below.
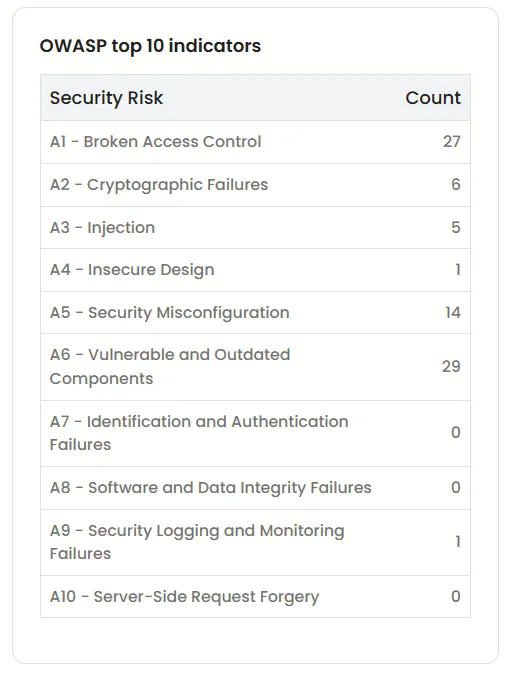
OWASP top 10 indicators
The OWASP Top 10 is a standard that represents a broad consensus of the ten most critical security risks to web applications. Beagle Security provides you with a list of OWASP vulnerabilities and their count present in your application.
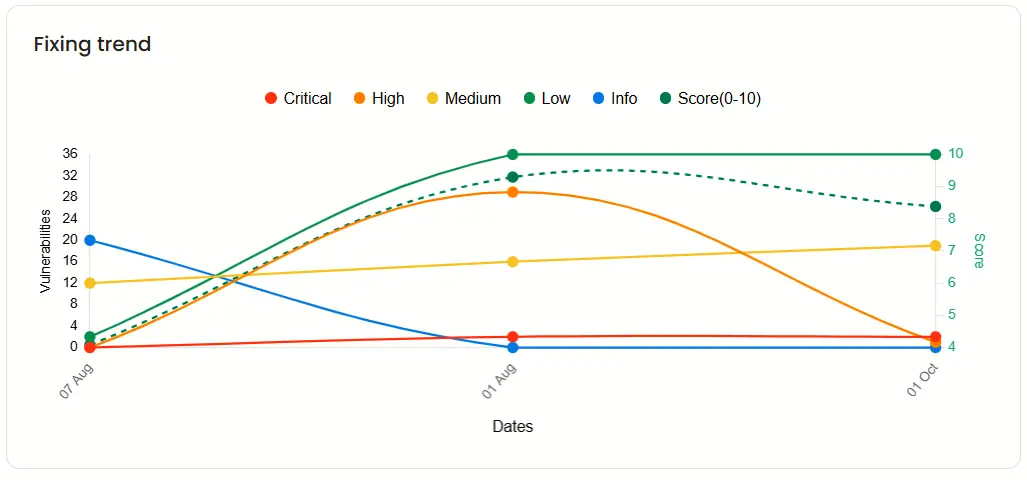
Fixing trend
This enables you to see the timeline and severity of vulnerabilities you’ve fixed, helping you keep track of your progress so far.
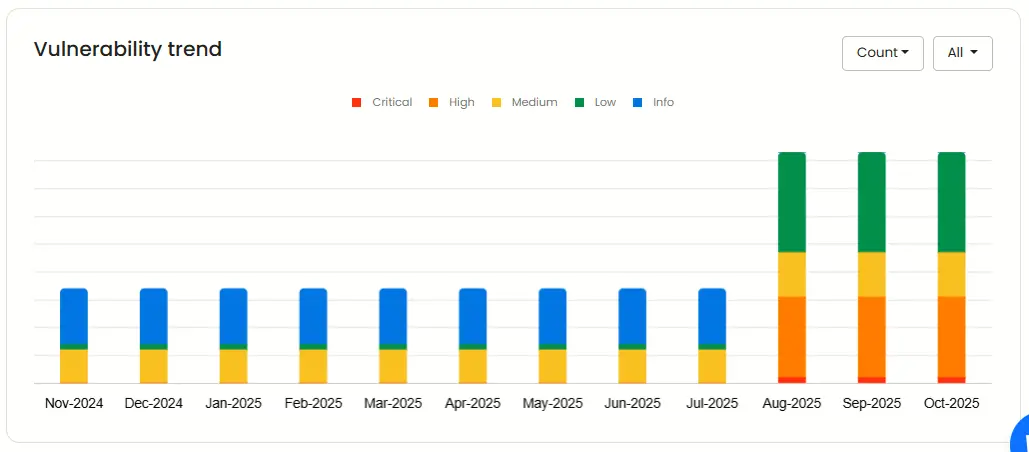
Vulnerability trend
This shows the trend of your vulnerabilities over the past year. It also provides the option to sort by severity and count.
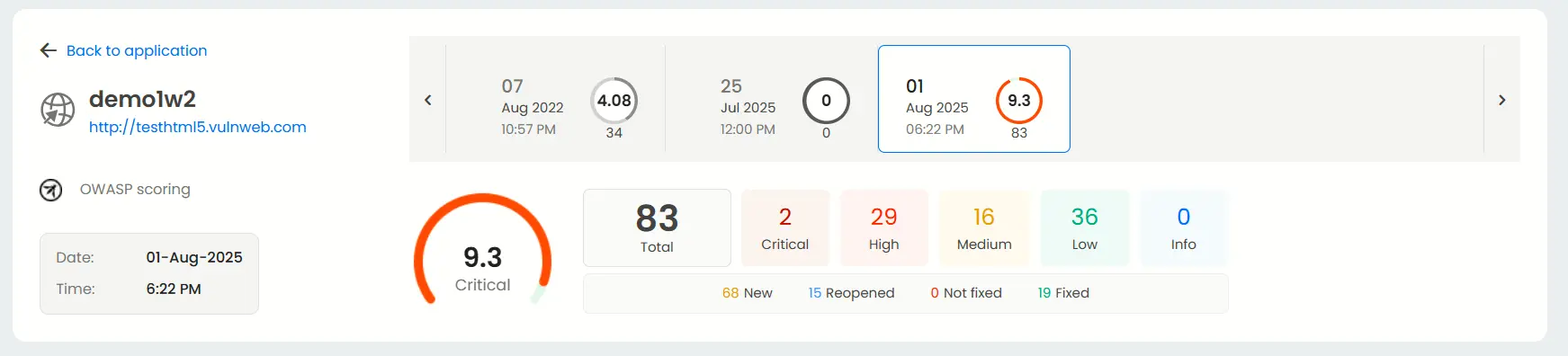
Result dashboard
The result dashboard is unique to each application and shows you the overview. Keep track of how many vulnerabilities are present, the severity of each one, and the date and time of your previous scans.
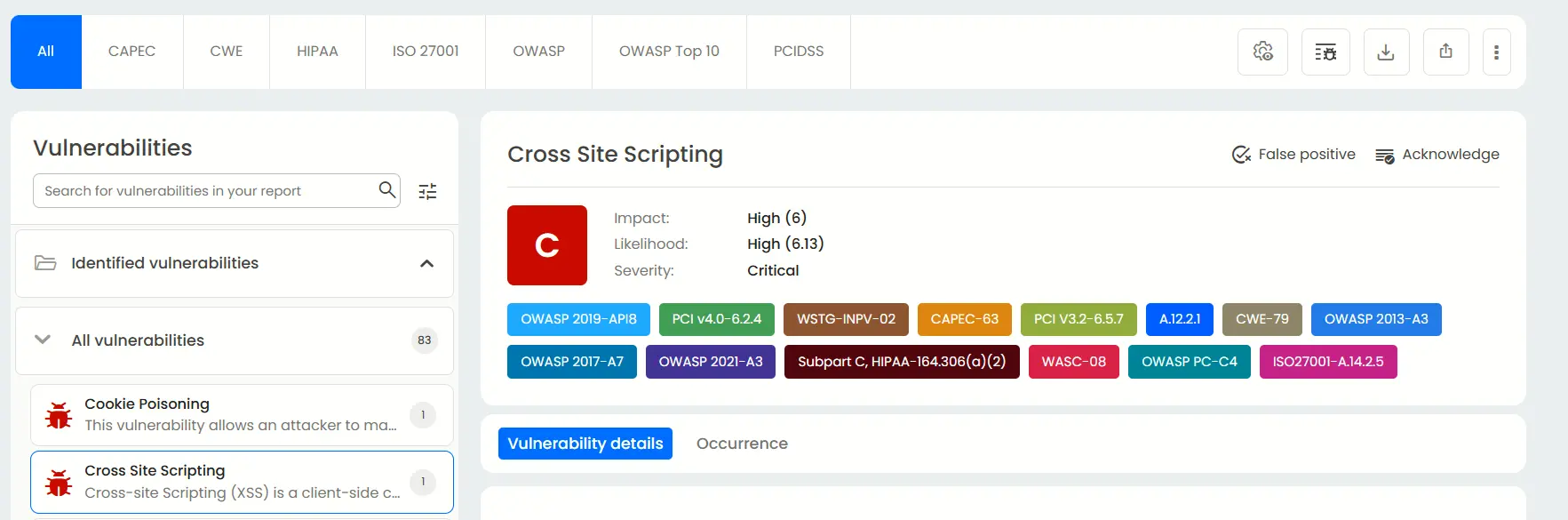
Mapping with ISO27001, OWASP & OWASP Top 10
In addition to OWASP and OWASP Top 10, Beagle Security provides you various compliance reports with other compliance metrics such as ISO 27001, HIPAA and PCIDSS.
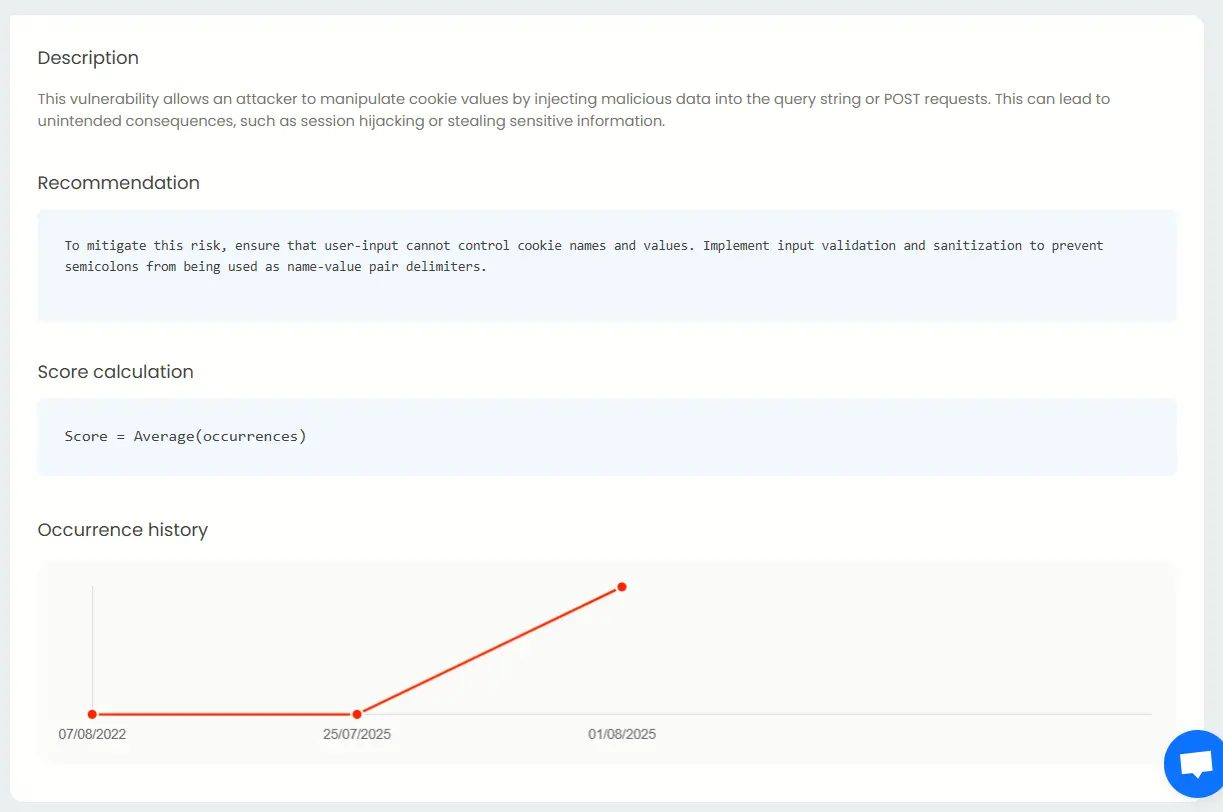
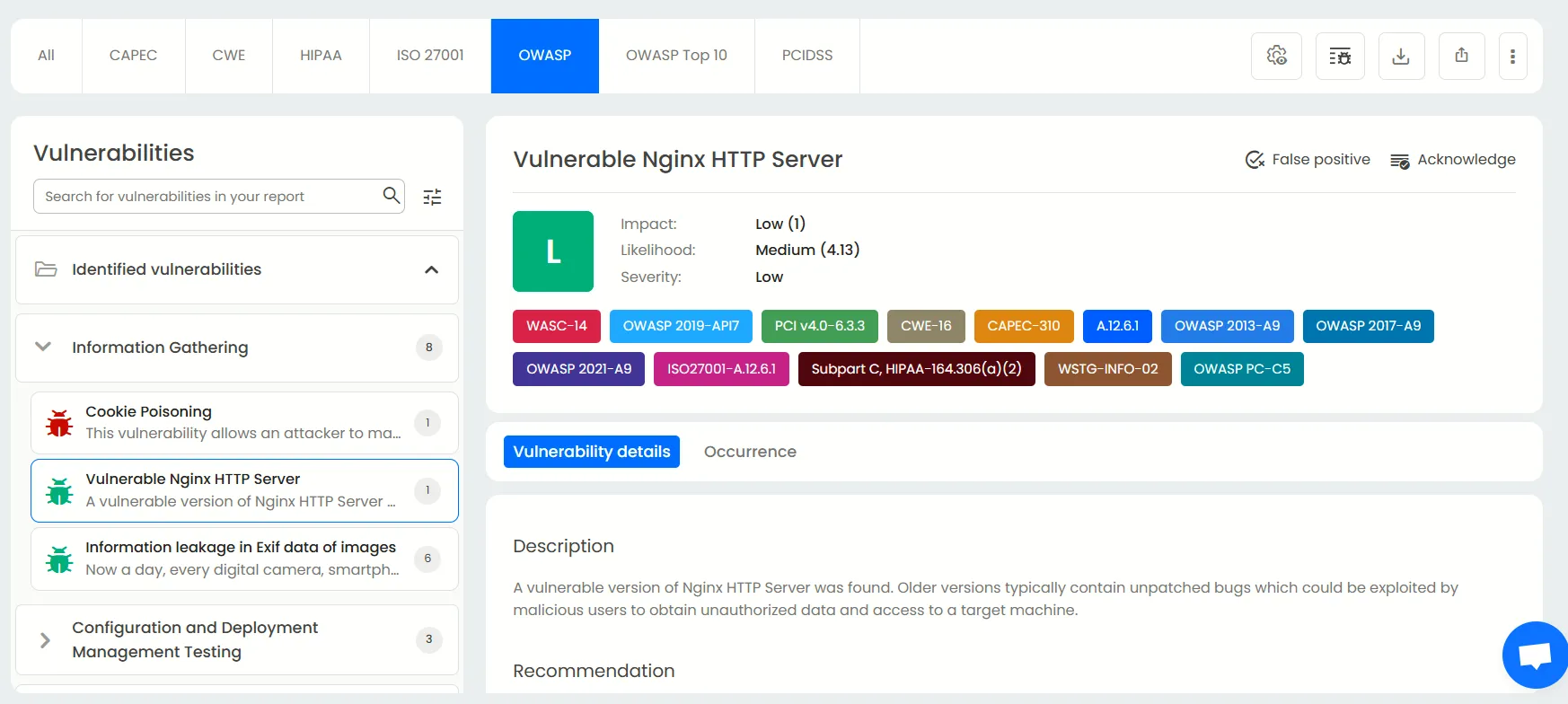
Detailed findings, fix recommendations & occurrence details
For each vulnerability detected in your application, Beagle Security gives you a description, a recommendation on how to mitigate it, and an occurrence history.
OWASP reports
While OWASP top 10 focuses on the ten most common vulnerabilities, the OWASP report focuses more on all vulnerabilities highlighted by OWASP regardless of their popularity. This ensures you don’t miss any type of threat no matter how niche they are.
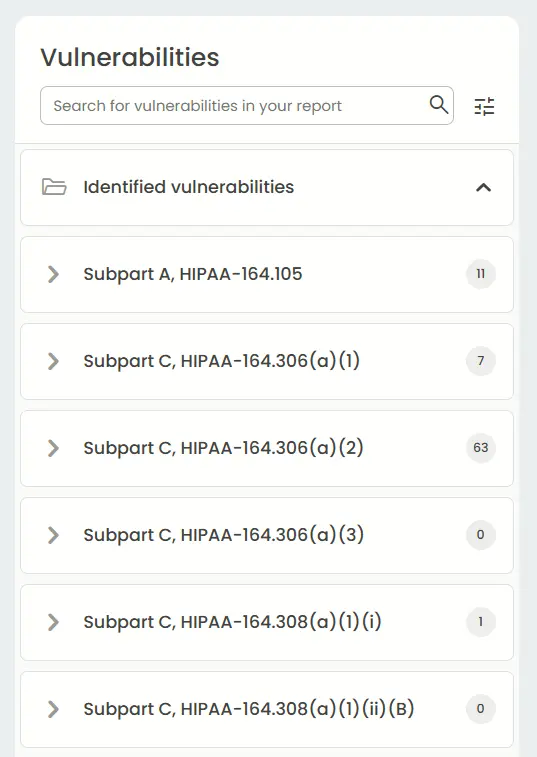
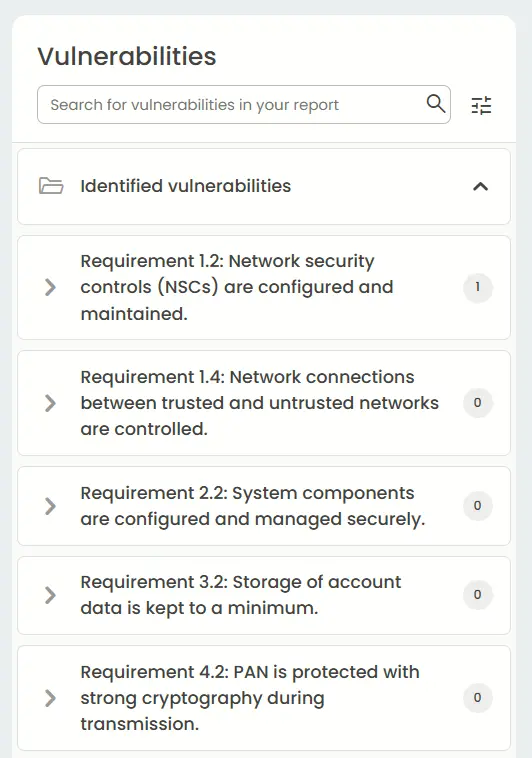
Compliance reports – HIPAA, PCI DSS
HIPAA and PCI DSS compliance reports help organizations demonstrate that they are meeting industry-specific security and privacy requirements. HIPAA is for protecting healthcare data, while PCI DSS for safeguarding payment card information.
These reports not only reduce regulatory risk but also build trust with customers, partners, and auditors by showing that proper controls are in place.
HIPAA report:
PCI DSS report:
Final thoughts
External penetration testing is a proactive way to identify and fix the security gaps that real attackers would target first. It’s not just for tech giants, small and mid-sized businesses are frequent targets too.
If you are ready to take action against hackers and vulnerabilities, try Beagle Security’s 14 day advanced trial that will let you know if we’re the right fit for your pentesting needs.
FAQ
How long does external pentesting take?
Traditional pentesting typically takes 2-3 weeks. Beagle Security’s AI-powered automated penetration tests however, take around 48-72 hours after configuration which is significantly faster.
How much does external penetration testing cost?
The external penetration testing cost varies depending on the complexity of your infrastructure, the depth of the test, and the vendor’s expertise. Manual testing is much more expensive than automated security platforms.
Beagle Security offers subscription plans starting at $119/month for their automated testing, providing a highly cost-effective and frequent testing alternative to traditional, expensive penetration testing engagements.
Do we need an external pentest if we already use vulnerability scanners?
Yes, because an external pentest goes beyond the surface level vulnerability detection of a scanner to exploit weaknesses and confirm the actual real-world risk and impact to your system.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)