
Shipping software fast is exhilarating, but doing so without a robust security process is like building a race car without brakes. As organizations accelerate development cycles and expand digital operations, the attack surface grows with every new API, dependency, and integration.
Security can no longer be an afterthought. Yet, for most teams, understanding the alphabet soup of tools such as DAST, SAST, SCA, IAST, RASP, feels overwhelming. Each serves a unique purpose, operates at different stages of the software development life cycle (SDLC), and addresses distinct classes of risk. Choosing the right set of tools is critical to building a strong and efficient security posture.
This guide aims to bring clarity. We’ll explain the core categories of software security audit tools, highlight what makes them different, and review the ten leading solutions shaping the security landscape in 2025. Whether you are part of a DevSecOps team, a security engineer, or a CTO looking to enhance your organization’s security testing capabilities, this article will help you make an informed choice.
Types of software security audit tools
Security audit tools generally fall into three main categories: Dynamic Application Security Testing (DAST), Static Application Security Testing (SAST), and Software Composition Analysis (SCA). Together, they form the foundation of a comprehensive security program.
Dynamic application security testing (DAST)
DAST tools simulate real-world attacks against running applications. They operate externally, scanning for vulnerabilities in a live environment without access to the source code. Think of DAST as a penetration tester probing your application’s defenses to find misconfigurations, injection flaws, and logic vulnerabilities.
These tools are especially useful for discovering issues that only appear at runtime, such as authentication weaknesses, API misconfigurations, or session management errors. They help organizations understand how attackers could exploit a live system and provide actionable insights for remediation.
DAST solutions are ideal for QA and security teams, integrating testing into pre-production environments. Their main strength lies in replicating attacker behavior across web and API surfaces, ensuring that security assessments reflect real operational risks.
However, DAST cannot identify coding errors or insecure design patterns before deployment. To address those gaps, teams often complement it with static analysis tools that scan the codebase itself.
Static application security testing (SAST)
SAST tools analyze source code, bytecode, or binaries to detect security flaws before execution. They serve as an automated code review mechanism that identifies potential vulnerabilities such as hardcoded secrets, injection points, or insecure encryption implementations.
This “shift-left” approach enables developers to fix issues early in the SDLC, reducing cost and rework. SAST integrates directly into IDEs and CI/CD pipelines, flagging issues during development or build stages.
Its main advantage is precision at the code level. It tells you exactly which line introduces the vulnerability. However, static analysis can produce false positives and lacks visibility into runtime behavior, making it insufficient on its own.
That’s where Software Composition Analysis tools come in to ensure the components you build upon are secure.
Software composition analysis (SCA)
SCA tools focus on open-source and third-party components. They identify dependencies, monitor vulnerabilities in public databases like NVD, and flag outdated or insecure libraries.
In modern development, where over 80 percent of codebases rely on open-source components, SCA is essential. These tools help organizations manage supply chain risks, track license compliance, and ensure timely patching.
Their strength lies in continuous monitoring and integration with build pipelines. Yet, SCA cannot detect logic flaws or vulnerabilities in custom code; It must be paired with SAST and DAST for complete coverage.
Together, these three categories, DAST, SAST, and SCA, form the backbone of a layered software security testing strategy.
Top software security audit tools at a glance
| Tool | Type | Key features | Limitations / considerations |
|---|---|---|---|
| Beagle Security | DAST | AI-powered vulnerability detection, business logic testing, CI/CD integration | Primarily web and API-focused |
| ZAP (Checkmarx ZAP) | DAST | Open-source scanner, active and passive scans, plugin architecture | Requires manual configuration and expertise |
| Burp Suite | DAST | Manual + automated testing, BApp extensions, SPA crawling | Limited automation and scalability |
| Invicti | DAST | Proof-based scanning, CI/CD integrations, enterprise reporting | High cost for small teams |
| Semgrep | SAST | Lightweight static analysis, custom rule creation, CI/CD ready | Coverage depends on community rules |
| Checkmarx SAST | SAST | Enterprise-grade code scanning, deep IDE integration | Expensive and resource-intensive |
| Veracode SAST | SAST | Cloud-native analysis, compliance reporting, multi-language support | Slower analysis time for large codebases |
| Coverity | SAST | Deep static analysis, precise defect detection, strong governance | Complex setup for smaller teams |
| Mend.io | SCA | Continuous dependency monitoring, license compliance, real-time alerts | Focused mainly on open-source components |
| Snyk | SCA | Developer-friendly interface, automated fixes, container and IaC support | Limited manual control in free tier |
Ratings are based on G2 reviews as of October 2025. Pricing varies by organization size and requirements.
Top software security audit tools
1. Beagle Security (DAST)
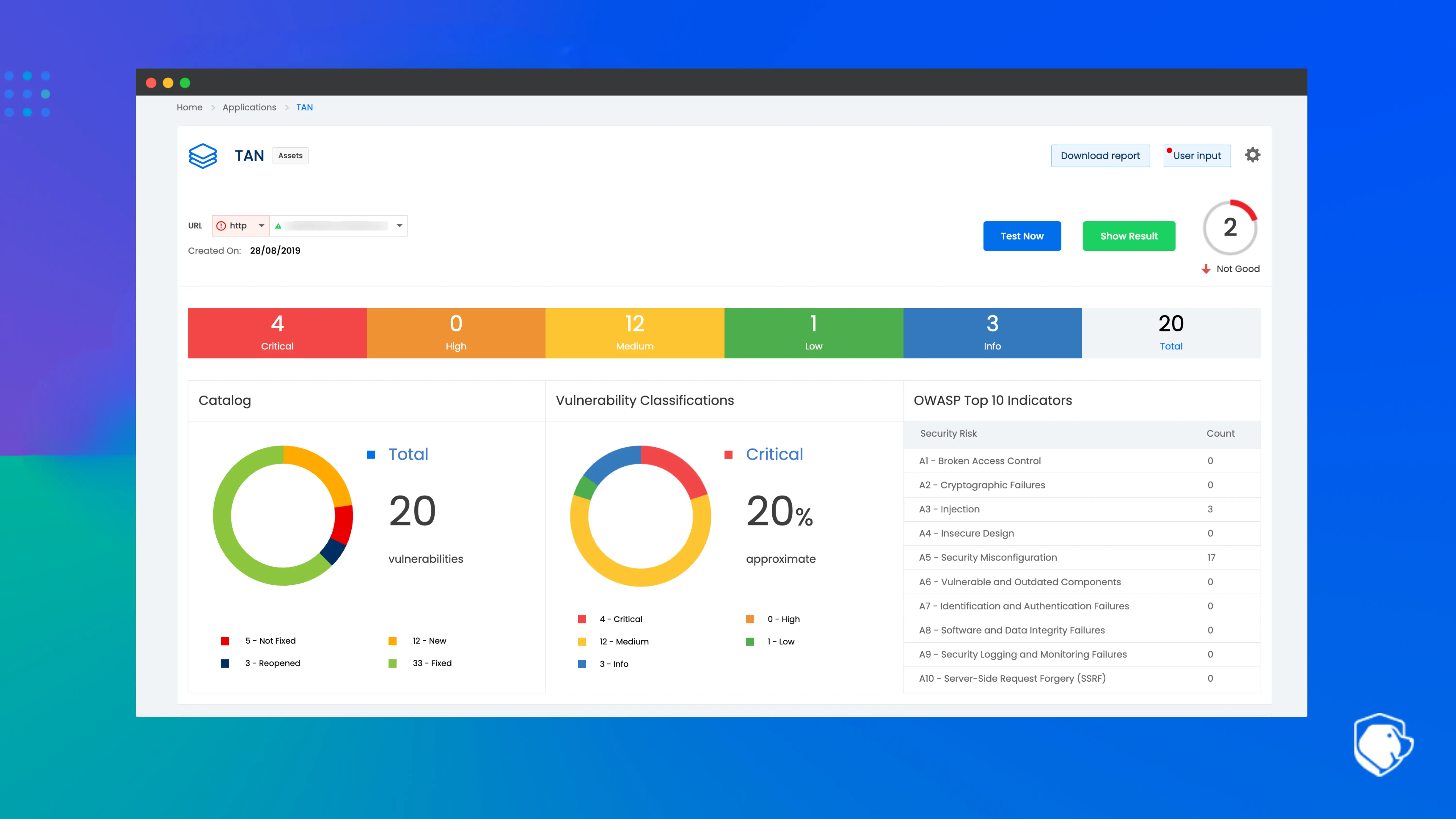
Beagle Security is an AI-driven DAST platform designed for modern development teams. It specializes in automated web and API security testing, enabling organizations to identify business logic flaws and runtime vulnerabilities before attackers do. The platform integrates seamlessly into CI/CD pipelines, providing continuous testing without disrupting workflows.
Its standout capability lies in intelligent attack simulation. Beagle Security doesn’t just check for known issues. It replicates real-world attacker behavior using machine learning models that adapt to application context.
Key features
AI-powered vulnerability validation with zero false positives
Native support for REST, GraphQL, and SOAP APIs
Business logic and access control testing
Pre-built integrations for GitHub Actions, GitLab, Jenkins, and Azure DevOps
Developer-friendly reports with remediation guidance.
Automated compliance reports (PCI DSS, SOC 2, HIPAA)
Pricing:
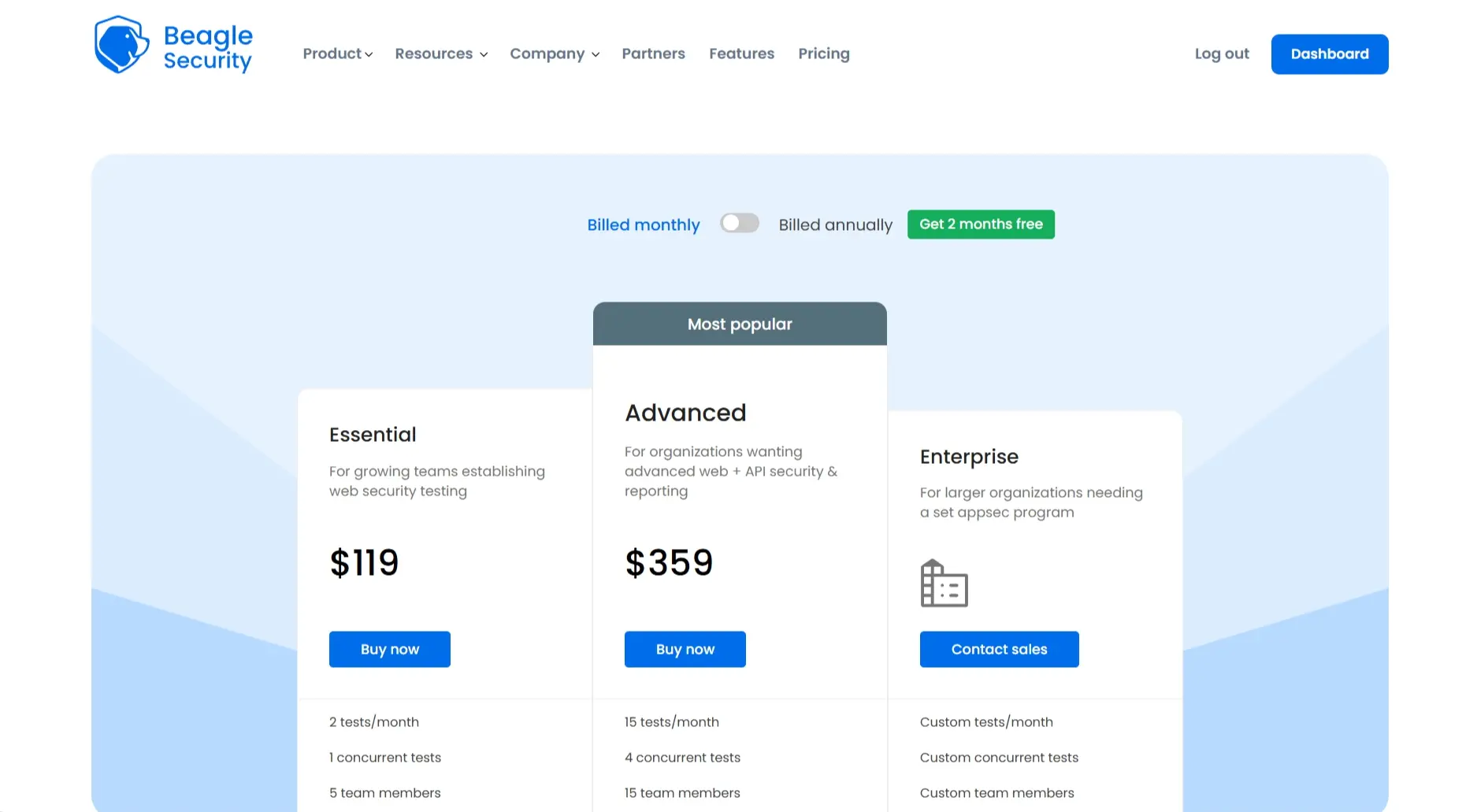
Starting at $119 per month
Enterprise plans with usage-based scaling
Ratings and reviews:
Beagle Security maintains a strong G2 rating of 4.7 out of 5, with users consistently praising its ease of use, API coverage, and AI-powered vulnerability detection. Many reviewers highlight its near-zero false positives and smooth CI/CD integrations, which make it a favorite among DevSecOps teams. Feedback often emphasizes its excellent support and balanced value for both startups and enterprises
2. Checkmarx ZAP (DAST)
Originally known as OWASP ZAP, this open-source tool is now maintained by Checkmarx and continues to be one of the most popular dynamic testing frameworks worldwide. ZAP provides both automated scanning and manual testing modes, making it suitable for teams that want flexibility and community-backed extensibility. It’s often used by developers and penetration testers who prefer open-source control with plugin-based customization. While it’s not the easiest to set up, its power lies in flexibility and community-driven innovation.
Key features
Active and passive scanning modes
Powerful plugin ecosystem for automation
Proxy-based interception for manual testing
Cross-platform support with frequent updates
Scripting interface for custom scan policies
Pricing:
Free open-source version
Enterprise support available through Checkmarx
Ratings and reviews:
Checkmrx ZAP holds a commendable G2 rating of 4.7 out of 5, reflecting its popularity as a robust open-source DAST solution. Users appreciate its flexibility, community-driven enhancements, and strong automation support in CI/CD pipelines. Reviews frequently mention its impressive capabilities for a free tool, though some note that large-scale management features may require additional setup.
3. Burp Suite (DAST)
Developed by PortSwigger, Burp Suite remains the gold standard for manual web application testing. It’s a favorite among penetration testers and security researchers due to its deep inspection capabilities and modular tools such as Intruder, Repeater, and Proxy.
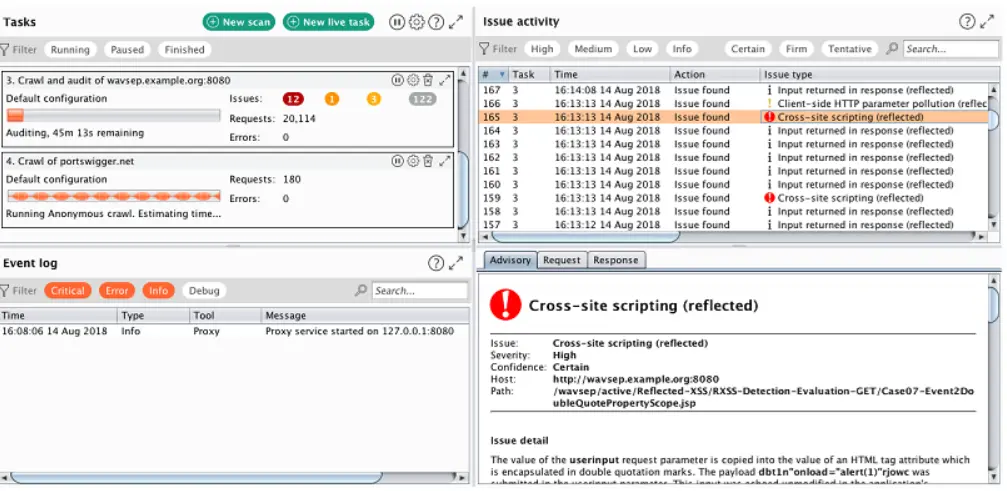
Burp Suite balances manual and automated testing well, offering professional extensions through its BApp Store to enhance functionality and coverage.
Key features
Manual testing toolkit (Proxy, Repeater, Intruder, Scanner)
JavaScript and SPA crawling support
BApp Store with hundreds of community extensions
Reporting and vulnerability tracking features
Integrations with CI/CD through Burp Suite Enterprise
Pricing:
Community Edition: Free
Professional Edition: $475 per year
Enterprise Edition: Custom pricing
Ratings and reviews:
Burp Suite enjoys one of the highest ratings in this category, with a G2 score of 4.8 out of 5. Professionals value its deep manual testing capabilities, advanced interception proxy, and extensive library of community extensions. Many reviewers praise its precision and control, calling it an indispensable tool for both professional pentesters and application security researchers.
4. Invicti (DAST)
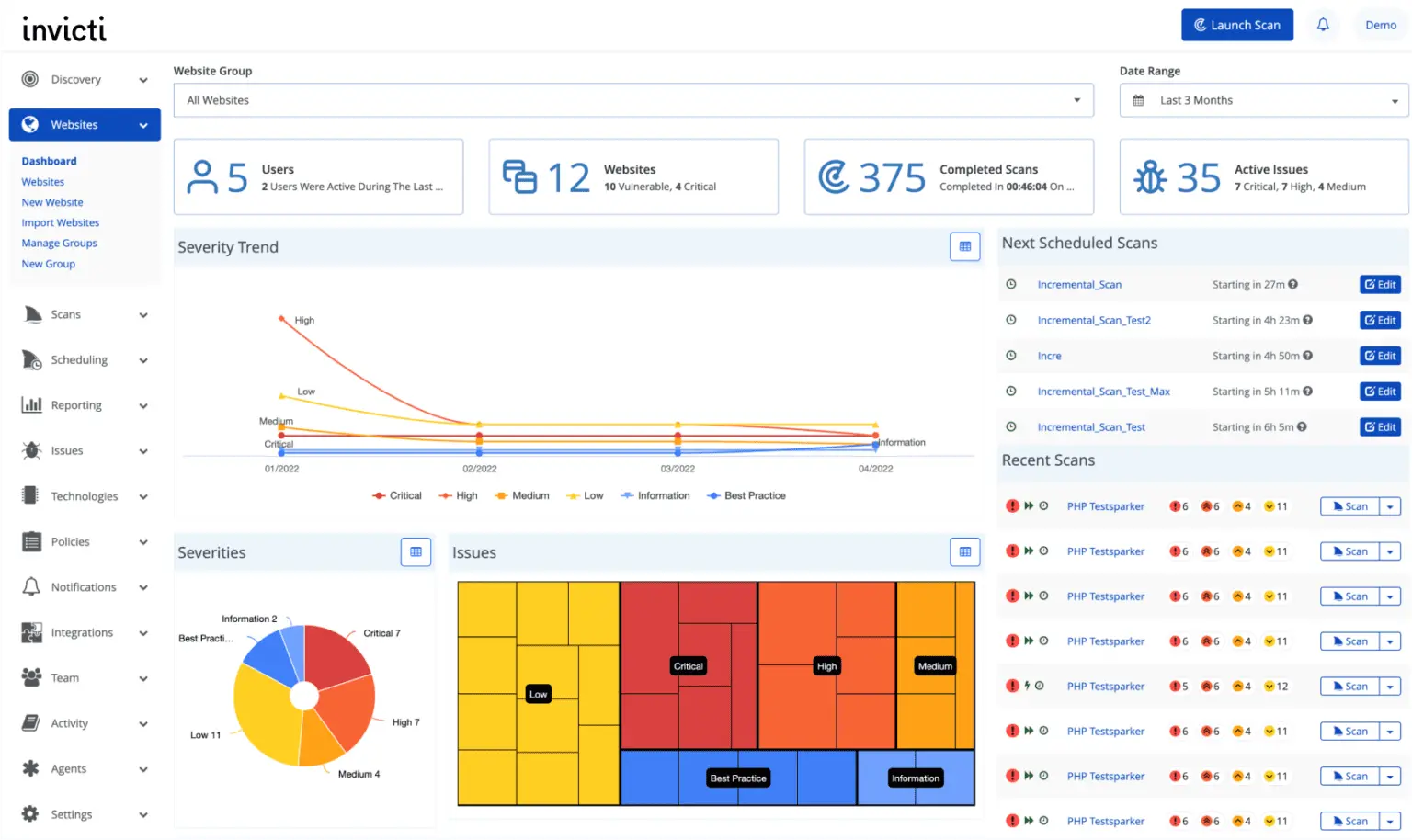
Invicti, formerly Netsparker, is an enterprise-grade DAST solution known for its proof-based scanning technology. It automatically confirms vulnerabilities by safely exploiting them in a controlled environment, reducing false positives dramatically.
It’s particularly suited for large organizations needing governance, compliance, and reporting at scale. Invicti integrates with issue trackers, CI/CD pipelines, and ticketing systems for seamless workflow alignment.
Key features
Proof-based scanning for validated results
Role-based access and audit management
Integration with Jira, Jenkins, GitHub, and Azure DevOps
Detailed technical and executive reporting
Centralized dashboard for large-scale monitoring
Pricing:
- Custom enterprise pricing based on scope
Ratings and reviews:
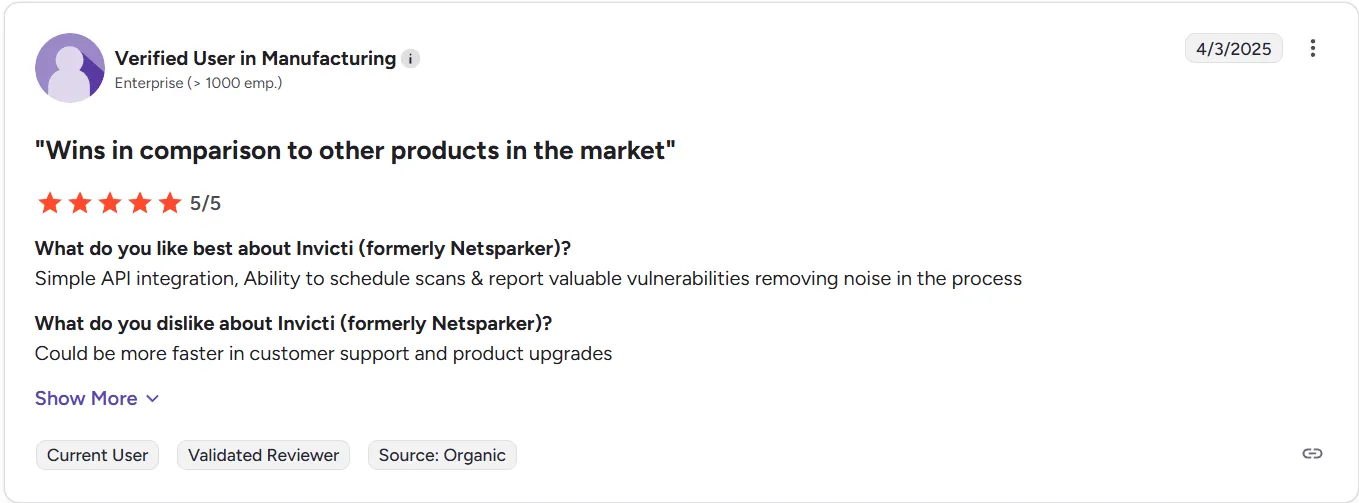
Invicti carries an excellent G2 rating of 4.6 out of 5, with users appreciating its proof-based scanning that eliminates false positives. Reviewers highlight its automation, accuracy, and seamless integration into CI/CD pipelines. Teams frequently mention that Invicti helps them validate vulnerabilities quickly and streamline their remediation workflow.
5. Semgrep (SAST)
Semgrep brings a developer-first approach to static analysis. It allows teams to write and customize rules in simple YAML syntax, offering unmatched flexibility in scanning source code for security issues, code smells, and policy violations.
It’s fast, lightweight, and integrates easily into developer workflows, making it a preferred choice for engineering-driven security teams.
Key features
2,000+ prebuilt community rules
Custom rule engine for organization-specific checks
CI/CD and IDE integrations
Support for 30+ programming languages
Policy-as-code support for consistent enforcement
Pricing:
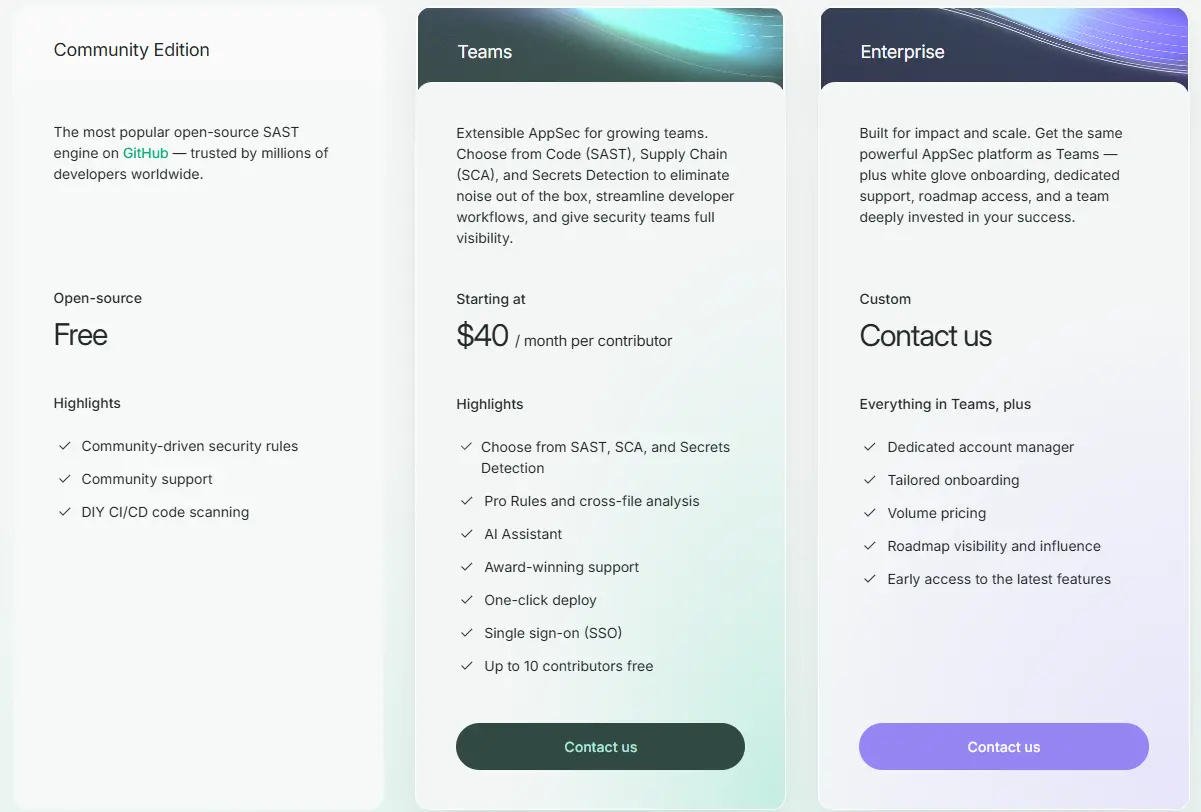
Community Edition: Free
Team Plan: From $40 per developer per month
Enterprise: Custom pricing
Ratings and reviews:
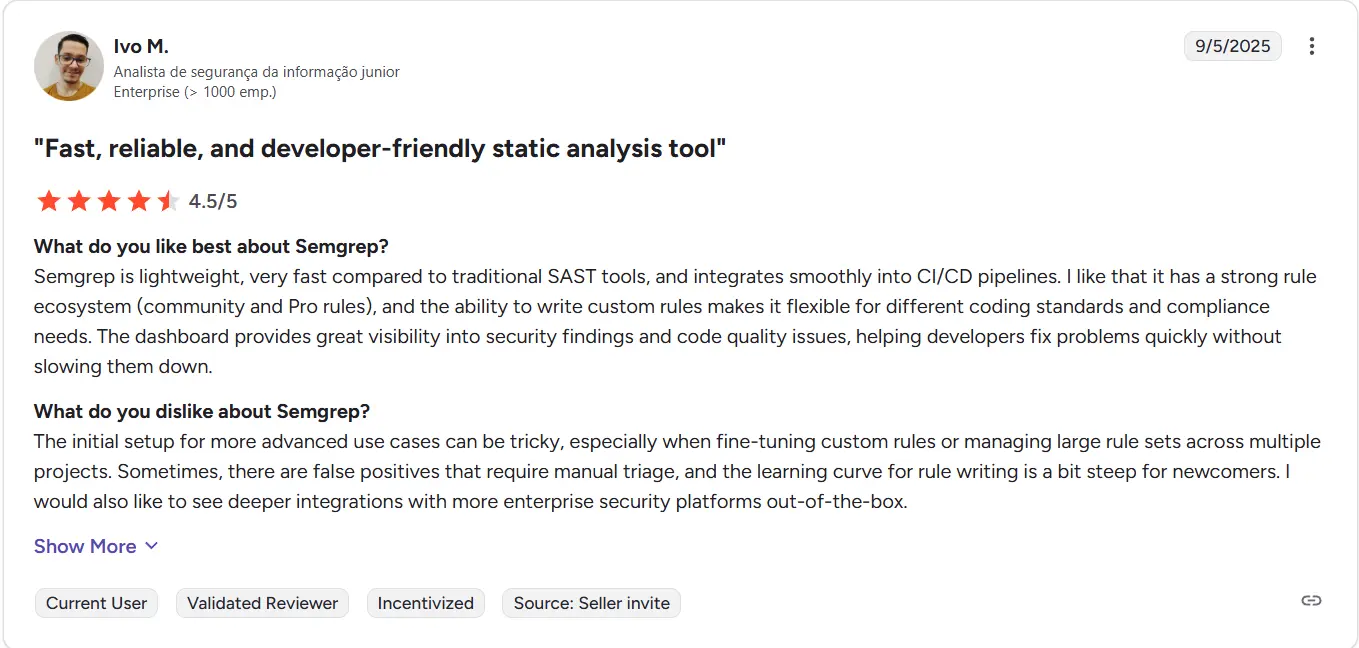
Semgrep holds a solid G2 score of 4.6 out of 5, with developers commending its fast and customizable static analysis. Users particularly value its simple rule syntax and extensive library of prebuilt checks that support multiple programming languages. Reviews often describe it as lightweight, developer-friendly, and ideal for integrating security earlier in the SDLC.
6. Checkmarx SAST (SAST)
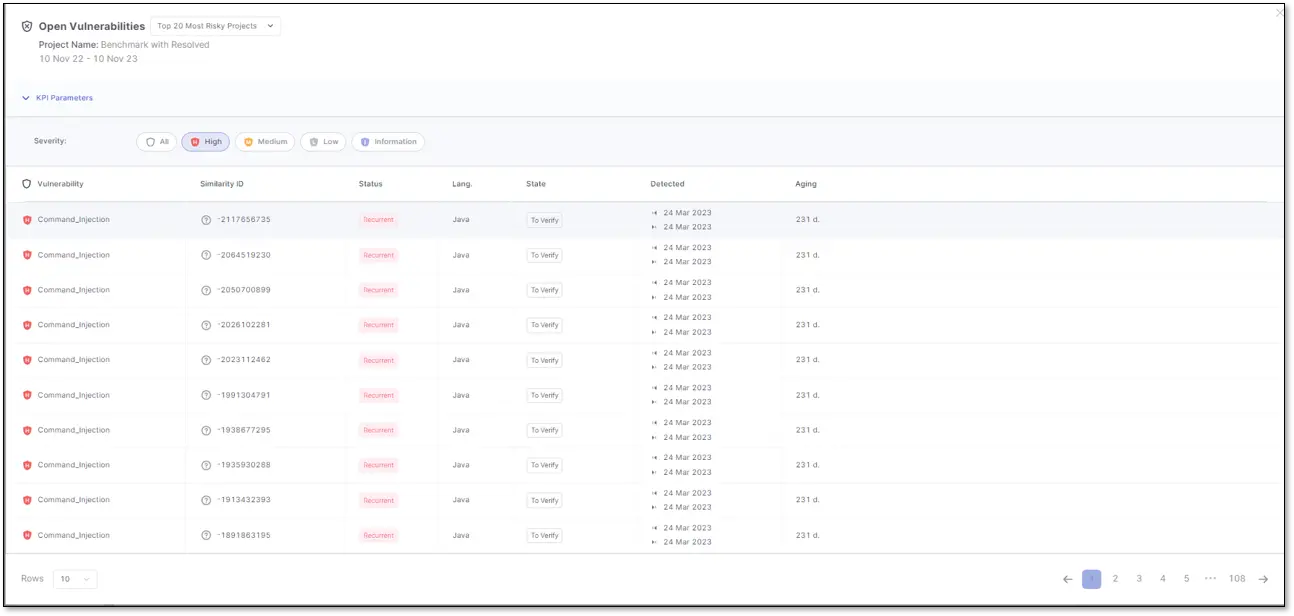
Checkmarx SAST is an enterprise-grade static analysis solution built for deep code inspection. It scans source code and binaries across multiple languages and frameworks, providing detailed insights into security weaknesses.
With strong CI/CD integrations and compliance support, it’s favored by large organizations prioritizing governance and centralized management.
Key features
Comprehensive multi-language support
Deep IDE integration for shift-left testing
Centralized policy and compliance management
Advanced reporting and risk visualization
Integration with SCMs and build tools
Pricing:
- Custom enterprise pricing
Ratings and reviews:
Checkmarx SAST maintains a G2 rating of 4.3 out of 5, receiving consistent praise for its comprehensive code scanning and policy management. Users appreciate its ability to identify complex security flaws and compliance issues at scale. Some mention that scan speed can be slower on very large projects, but most agree it is a mature and feature-rich enterprise solution.
7. Veracode SAST (SAST)
Veracode offers a cloud-based SAST platform tailored for enterprises requiring scalable, policy-driven security assessments. It provides code analysis, compliance reporting, and integrations across development environments.
Its managed service model appeals to organizations seeking operational simplicity without maintaining on-premise infrastructure.
Key features
Cloud-native SAST scanning
Integrated compliance reporting (SOC 2, ISO 27001)
Multi-language and framework support
IDE plugins for real-time feedback
Centralized policy enforcement
Pricing:
- Custom enterprise pricing
Ratings and reviews:
Veracode SAST scores a respectable G2 rating of 4.2 out of 5, with users valuing its cloud-based scanning and detailed vulnerability remediation guidance. Reviewers note that it integrates well into enterprise workflows, offering strong governance and reporting features. Some mention that results interpretation requires training, but most appreciate its accuracy and breadth of language support.
8. Coverity (SAST)
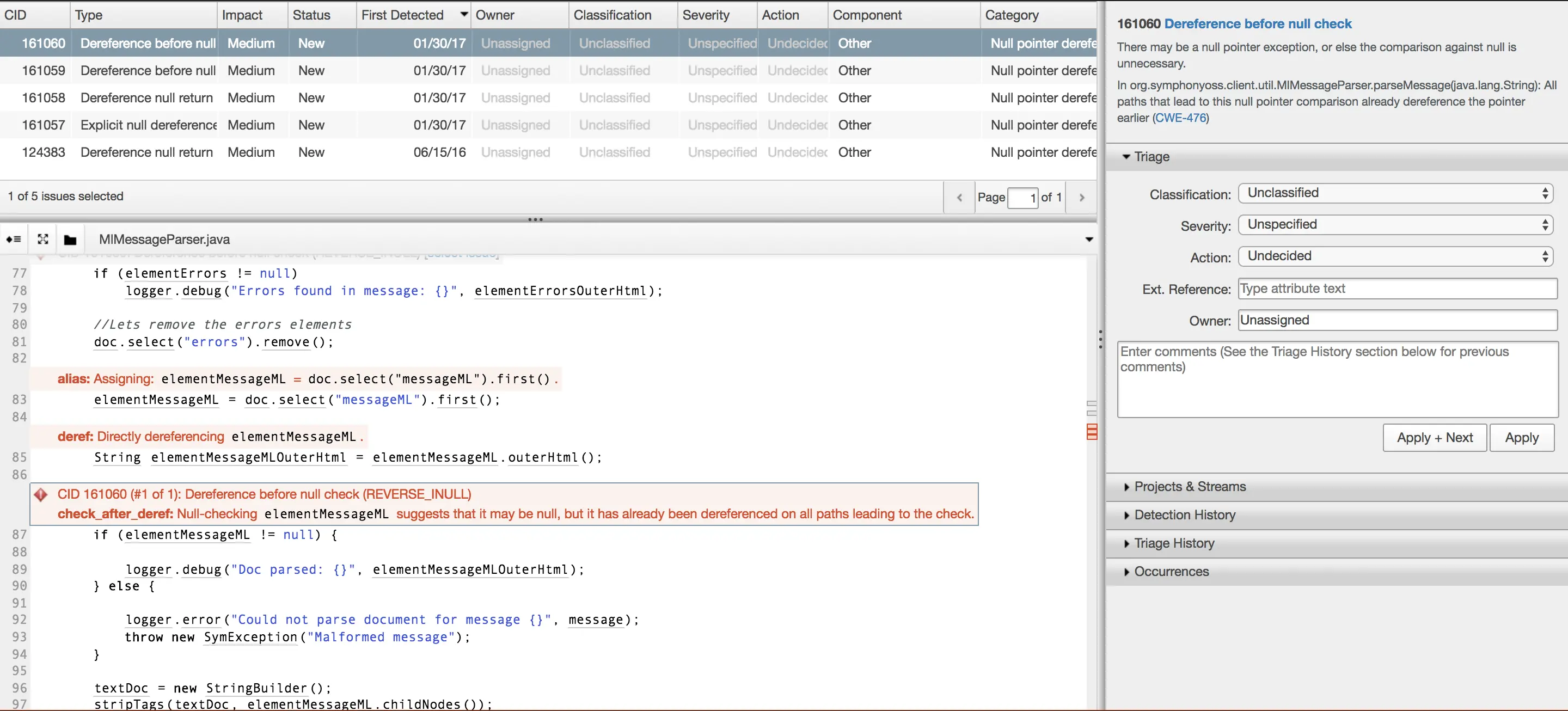
Coverity by Synopsys is a mature static analysis tool trusted for its precision in identifying complex software defects and security vulnerabilities. It supports large-scale enterprise environments and is widely used in safety-critical industries.
Its strength lies in advanced dataflow analysis that minimizes false positives while providing detailed remediation guidance.
Key features
Deep static analysis with contextual insights
Enterprise governance and audit trail support
Integrations with major build systems and IDEs
High scalability for large codebases
Accurate defect classification and remediation guidance
Pricing:
- Custom enterprise pricing
Ratings and reviews:
Coverity from Synopsys earns a G2 rating of 4.4 out of 5, with feedback highlighting its precision in identifying code-level vulnerabilities and reliability in large-scale enterprise environments. Users praise its deep static analysis capabilities and integration options for CI/CD pipelines. Some note that it has a steeper learning curve, but once configured, it provides highly accurate results.
9. Mend.io (SCA)
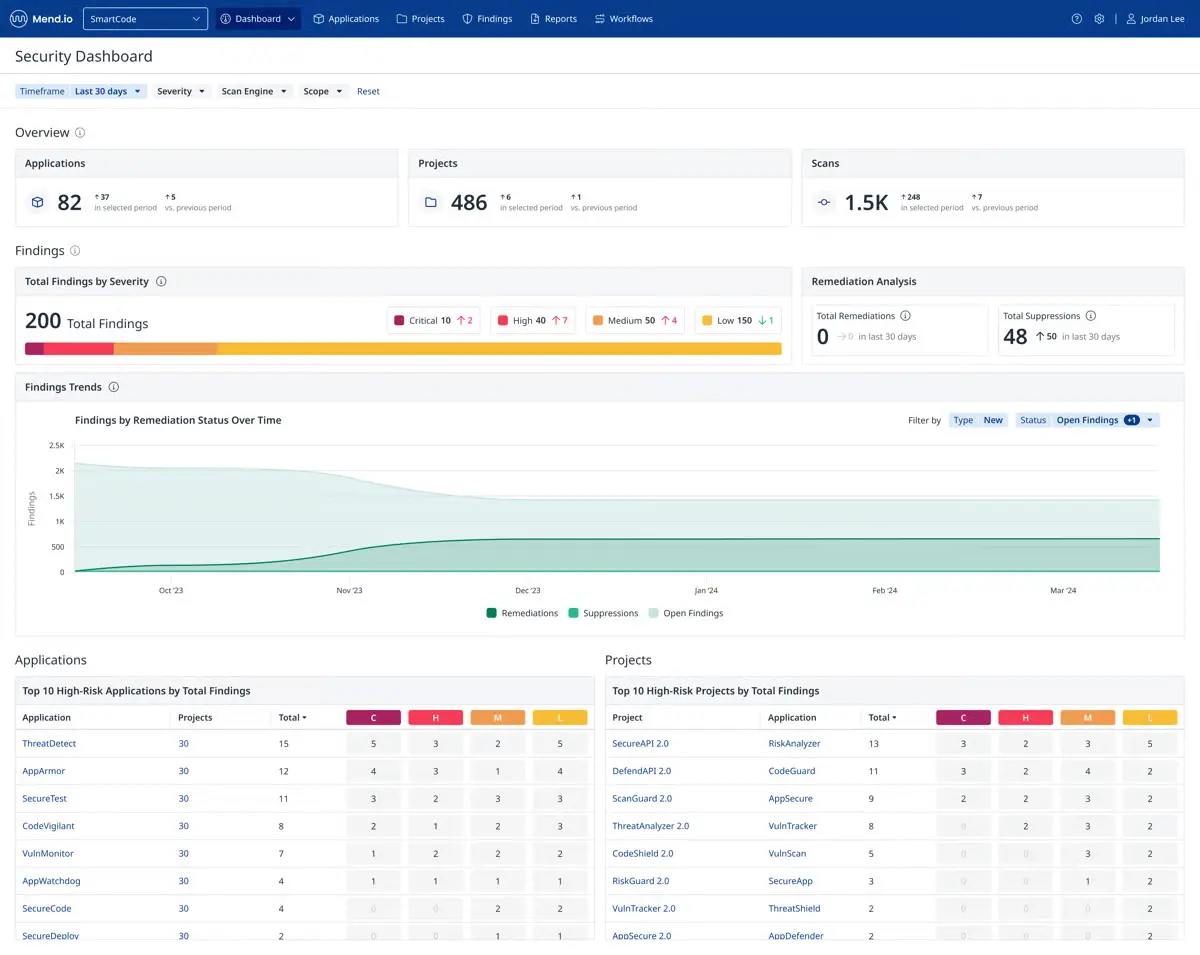
Mend.io, formerly WhiteSource, focuses on managing open-source risk. It automates dependency scanning, license compliance, and vulnerability alerts across complex codebases.
The platform’s continuous monitoring ensures that teams are notified as soon as a new vulnerability affects any dependency, supporting proactive remediation.
Key features
Continuous dependency and license scanning
Real-time alerts for new CVEs
Integration with GitHub, Bitbucket, and CI/CD tools
Policy management for license compliance
Automated remediation suggestions
Pricing:
- Custom enterprise pricing
Ratings and reviews:
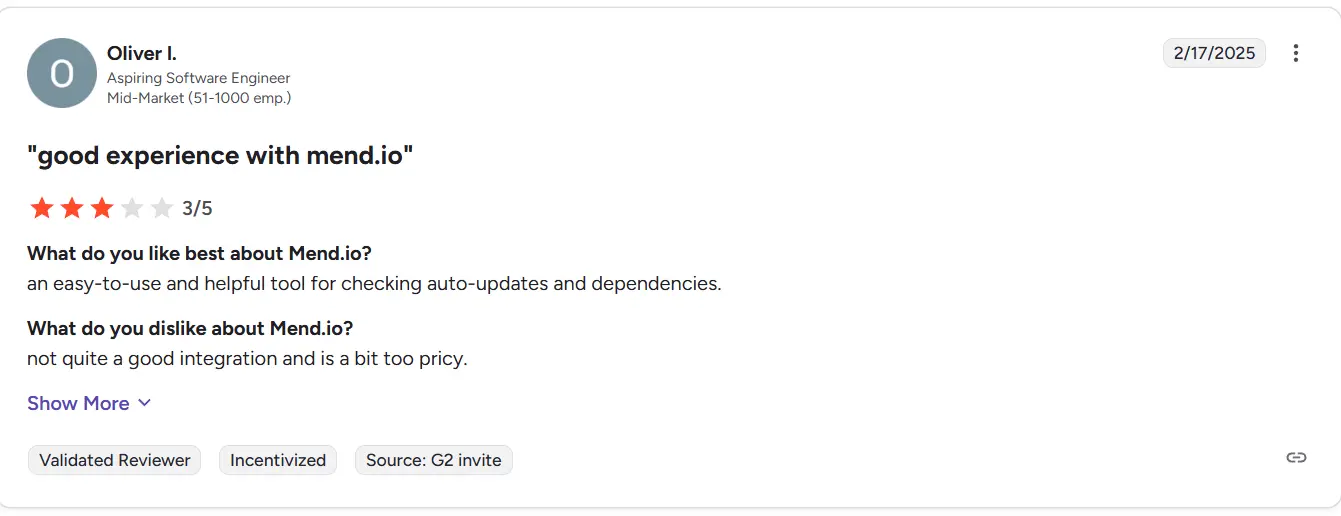
Mend.io, formerly known as WhiteSource, holds a G2 score of 4.5 out of 5, with users praising its effective open-source vulnerability management and license compliance tracking. Many reviewers highlight its automation and continuous monitoring features that help teams maintain visibility across software dependencies. Some users mention that the interface can be dense, but overall satisfaction remains high.
10. Snyk (SCA)
Snyk is a developer-friendly SCA platform that extends into container, IaC, and open-source scanning. It’s widely adopted by DevOps teams for its automation and intuitive user experience.
Its strength lies in actionable remediation. Snyk not only detects vulnerabilities but also suggests and applies fixes automatically through pull requests.
Key features
Automated fix suggestions and pull requests
Container, IaC, and open-source scanning
Integration with GitHub, GitLab, and Bitbucket
Developer-first CLI and IDE support
Real-time vulnerability database updates
Pricing:
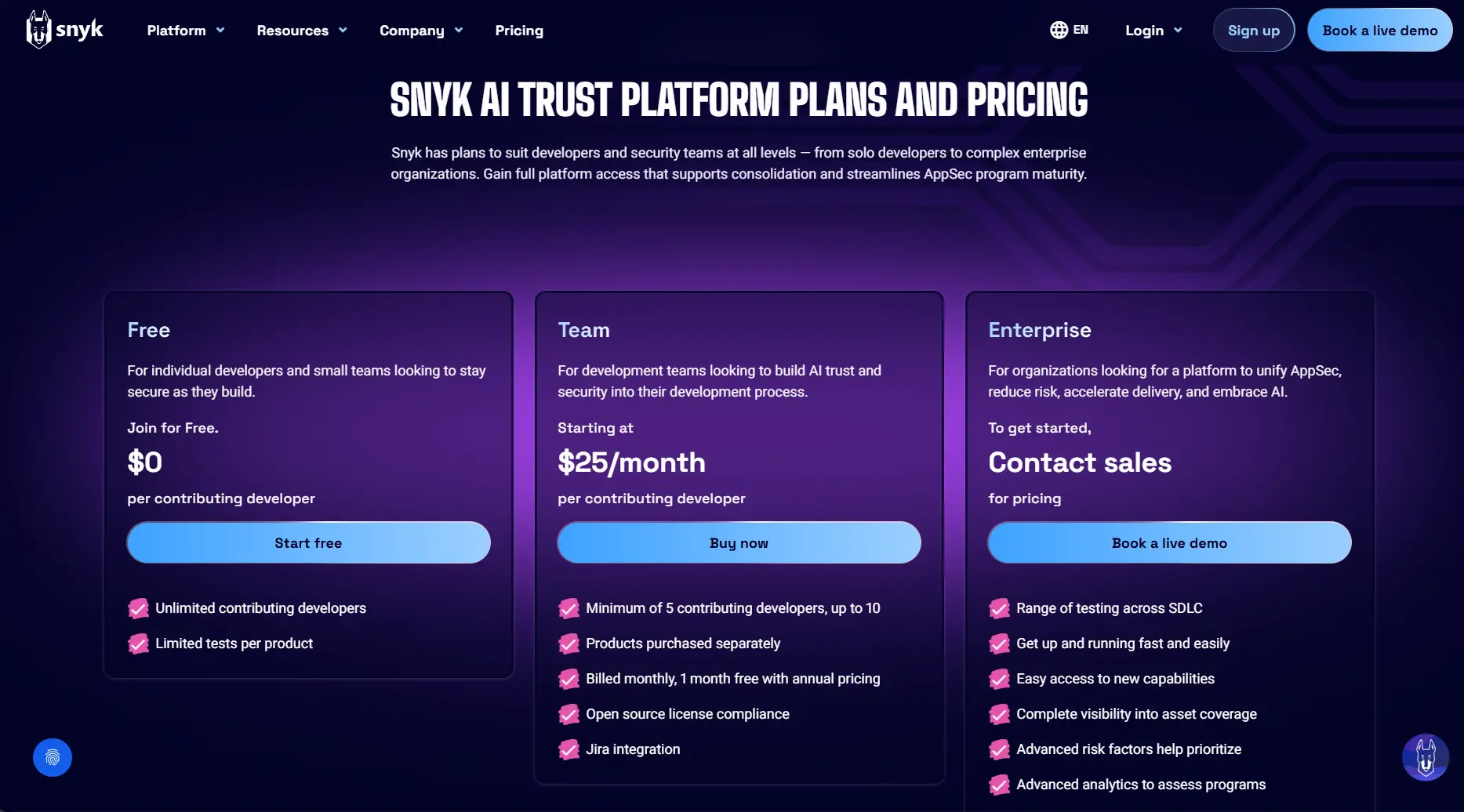
Free tier available
Team Plan: From $25 per developer per month
Enterprise: Custom pricing
Ratings and reviews:
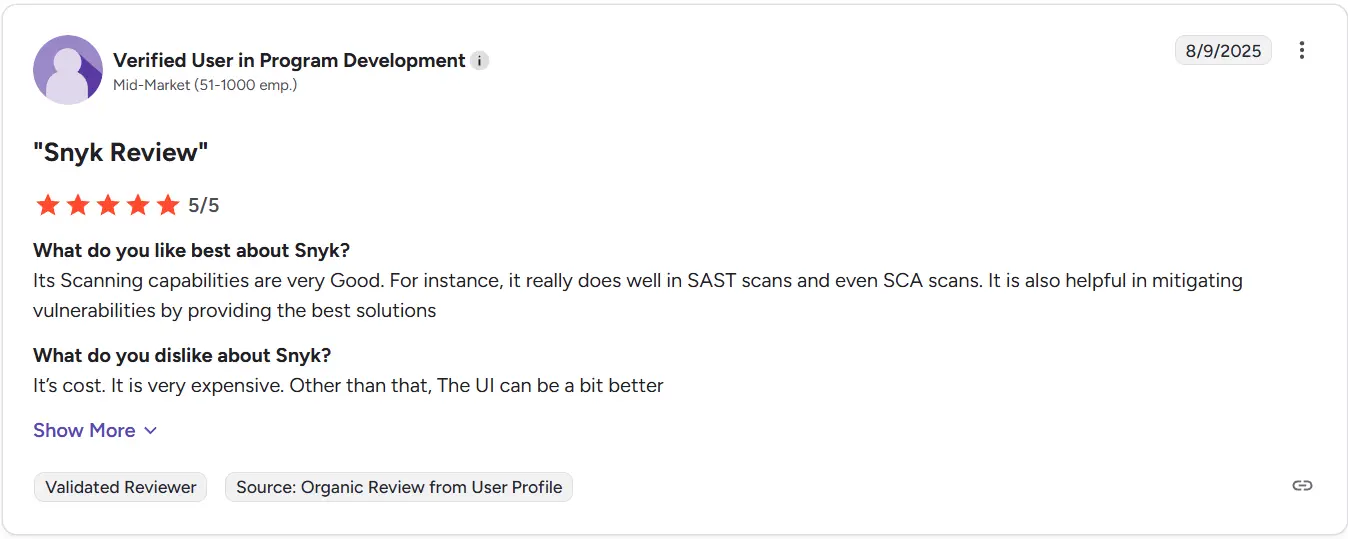
Snyk maintains a strong G2 rating of 4.6 out of 5, widely recognized for its developer-first approach to security scanning and open-source dependency management. Reviewers frequently highlight its seamless IDE integration, fast feedback loops, and actionable fix suggestions. While some users mention pricing increases for larger teams, most agree it delivers exceptional value for securing modern development workflows.
What makes a good software security audit tool
As you evaluate security audit tools, consider the following factors to ensure the solution fits your workflow and organizational needs.
Platform support
Look for tools that support diverse environments, from on-premise to cloud-native and containerized systems. Compatibility with multiple OS and deployment models ensures flexibility as your architecture evolves.
Integration with CI/CD tools
Modern DevSecOps pipelines demand seamless integration. Tools that connect directly with Jenkins, GitHub Actions, or GitLab CI allow automated scans and fail builds when vulnerabilities exceed thresholds.
False positive ratio
Accuracy matters. High false positive rates waste developer time and reduce trust. Leading tools employ AI-driven validation or proof-based scanning to ensure results are reliable and actionable.
Coverage
Comprehensive vulnerability coverage, including OWASP Top 10, CWE, and zero-day patterns, ensures resilience against emerging threats. Tools with custom rule support provide better adaptability.
Licensing model
Transparent and predictable pricing helps with budget planning. Consider whether the tool charges per application, developer, or scan frequency.
Reporting
Effective reporting bridges the gap between developers and executives. The best tools provide both technical remediation details and compliance-ready summaries.
Ease of use
A good tool should deliver results without steep learning curves. Intuitive interfaces, strong documentation, and quick onboarding significantly enhance adoption.
Conclusion
Software security audit tools are essential in 2025 for organizations that want to protect their expanding digital ecosystems. Each category brings unique strengths to the table.
DAST tools like Beagle Security, ZAP, Burp Suite, and Invicti focus on runtime vulnerabilities and real-world attack simulations. SAST tools, including Semgrep, Checkmarx, Veracode, and Coverity, empower developers to catch security issues directly in the code. Meanwhile, SCA tools such as Mend.io and Snyk safeguard open-source dependencies and supply chain integrity.
However, if you’re looking for a tool that combines automation, AI-driven attack simulation, developer-friendly integration, and affordability, Beagle Security stands out as a well-balanced choice for teams of all sizes.
In short:
For enterprises seeking broad integrations, Invicti and Checkmarx are solid picks.
For developer-centric workflows, Semgrep and Snyk shine.
For comprehensive testing at scale without breaking the budget, Beagle Security offers the most balanced value in 2025.
Building a strong security program isn’t about choosing one tool. It’s about selecting the right combination that complements your development lifecycle and security goals.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)