![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026.webp)
Vulnerability management has shifted significantly over the last few years. Security teams are no longer dealing with a small number of static servers protected by a network perimeter. Instead, modern environments consist of cloud workloads, containerized services, CI/CD pipelines, third-party integrations, and constantly changing web applications and APIs. This shift has expanded the attack surface and made it harder to rely on a single category of security tooling.
Two tools that frequently appear in vulnerability management evaluations are Acunetix and Nessus. While both aim to identify security weaknesses, they operate at very different layers of the stack. Nessus is widely adopted for infrastructure and host-based vulnerability scanning, whereas Acunetix focuses on dynamic application security testing for web applications and APIs.
Choosing between these tools is not simply a matter of feature checklists. It depends on where your primary risk lies, how your teams work, and whether you are securing infrastructure, applications, or both. This comparison breaks down Acunetix vs Nessus in detail and also introduces Beagle Security as an alternative automated web and API penetration testing platform for teams that need deeper, exploit-focused application security testing.
Overview of Acunetix and Nessus
Acunetix, developed by Invicti Security, is a dynamic application security testing (DAST) platform designed to identify vulnerabilities in web applications and APIs while they are running. It scans applications by crawling pages, discovering inputs, and actively testing them for vulnerabilities such as SQL injection, cross-site scripting, insecure authentication, and misconfigurations. Acunetix is particularly known for its proof-based scanning approach, which attempts to safely verify vulnerabilities to reduce false positives.
Nessus, developed by Tenable, is a commercial vulnerability scanner focused on identifying known vulnerabilities across infrastructure assets. It scans servers, operating systems, network devices, and services to detect missing patches, exposed services, insecure configurations, and known CVEs. Nessus is widely used in enterprise environments and is often part of compliance and audit-driven security programs.
While both tools are used under the broad umbrella of vulnerability management, they are designed to answer different security questions.
Acunetix vs Nessus at a glance
| Area | Acunetix | Nessus |
|---|---|---|
| Tool category | Web application and API DAST | Infrastructure vulnerability scanner |
| Vendor | Invicti Security | Tenable |
| Primary focus | Application-layer vulnerabilities | Network, host, and OS vulnerabilities |
| Deployment | Cloud or on-prem | On-prem or cloud |
| Scan methodology | Dynamic, proof-based scanning | Plugin-based CVE detection |
| False positive handling | Automated validation | Manual verification |
| Compliance support | Web-focused standards | Broad infrastructure compliance |
| Best suited for | AppSec and DevSecOps teams | Enterprise infrastructure teams |
An alternative web and API penetration testing platform for comparison: Beagle Security
Traditional vulnerability scanners and DAST tools play an important role, but many real-world breaches exploit gaps that these tools do not fully cover. Infrastructure scanners do not understand application logic, and traditional DAST tools often struggle with complex authentication, multi-step workflows, and chained attack paths.
Beagle Security is an automated web and API penetration testing platform designed to simulate how a real attacker would attempt to exploit an application. Instead of focusing solely on vulnerability detection, Beagle Security emphasizes exploitability, attack paths, and contextual reporting.
This makes Beagle Security a complementary or alternative option for teams that want deeper application-layer coverage, especially in SaaS, API-first, and CI/CD-driven environments.
Why Beagle Security might be a better fit
Modern development teams ship code frequently, rely heavily on APIs, and implement complex authentication flows. In these environments, traditional tools often generate findings that are technically correct but difficult to prioritize or act upon.
Beagle Security may be a better fit for teams that:
Need exploit-focused testing rather than raw vulnerability lists
Rely on authenticated workflows and APIs
Want findings developers can immediately understand and fix
Integrate security testing directly into CI/CD pipelines
By focusing on real attack simulation, Beagle Security helps teams identify vulnerabilities that are most likely to be exploited in production.
Acunetix vs Nessus vs Beagle Security: Feature comparison
| Feature | Acunetix | Nessus | Beagle Security |
|---|---|---|---|
| Web application testing | Yes | Limited | Advanced |
| API security testing | Yes | Limited | Yes |
| Infrastructure scanning | No | Yes | Limited |
| Authenticated testing | Yes | Yes | Advanced |
| Proof of exploitability | Yes | No | Yes |
| Business logic testing | Limited | No | Yes |
| CI/CD integration | Moderate | Limited | Strong |
| Developer-friendly reporting | Strong | Moderate | Strong |
Acunetix web application security features
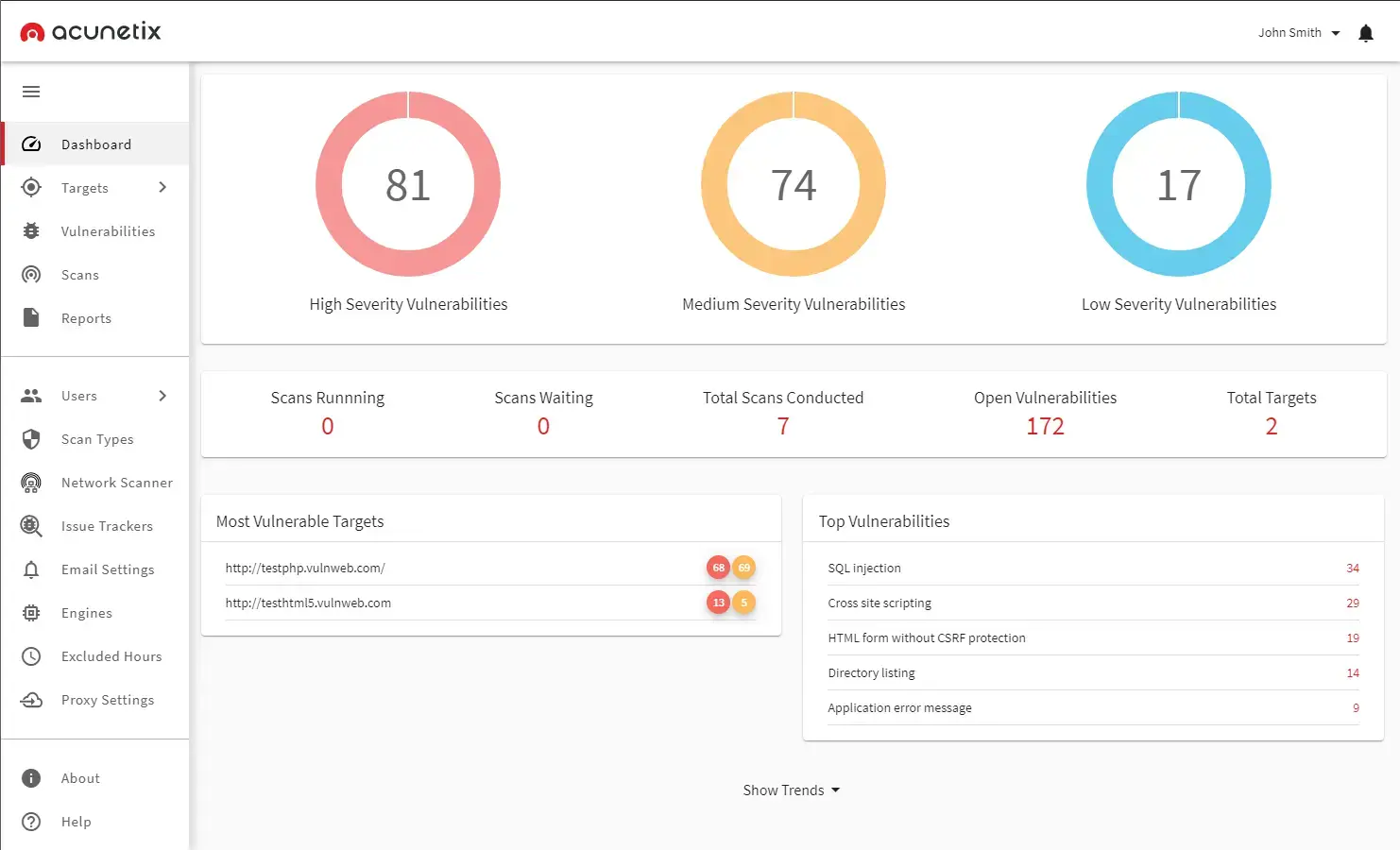
Acunetix is purpose-built for scanning web applications and APIs. It automatically crawls applications to identify pages, parameters, and endpoints before launching dynamic tests to uncover vulnerabilities.
Key capabilities include:
Detection of OWASP Top 10 vulnerabilities
Proof-based vulnerability validation
Automated crawling of modern web apps
API scanning support for REST services
Compliance-oriented reporting
Acunetix performs well for identifying common and well-known application vulnerabilities. However, it can struggle with deeply customized business logic and multi-step attack chains that require attacker intuition.
Nessus vulnerability scanning features
Nessus focuses on identifying known vulnerabilities across infrastructure assets using a large and frequently updated plugin database.
Key capabilities include:
Detection of CVEs across operating systems and services
Credentialed scanning for deeper host visibility
Configuration and compliance audits
Broad coverage across diverse environments
Nessus excels at infrastructure hygiene and compliance readiness. Its limitation lies in its lack of visibility into application logic and runtime behavior.
Beagle Security features
Beagle Security focuses on automated penetration testing rather than passive scanning.
Key capabilities include:
Automated attack simulation for web apps and APIs
Support for REST and GraphQL APIs
Advanced authentication and session handling
Context-rich reports with exploit evidence
Retesting workflows and CI/CD integration
This approach helps teams prioritize vulnerabilities based on real risk rather than volume.
Acunetix vs Nessus vs Beagle Security: Pricing comparison
| Tool | Pricing model | Cost considerations | Example published costs |
|---|---|---|---|
| Acunetix (by Invicti) | Subscription / quote-based | Scales with number of targets (FQDNs/web apps) and edition; pricing tends to rise quickly with more targets | Estimated $4,500–$26,000+ per year depending on number of targets/edition (entry-to-enterprise range) |
| Nessus (Tenable) | License / subscription | Costs vary by edition and assets; free tier available for very small scans | Free (Nessus Essentials); $4,390/year for Nessus Professional (annual license) |
| Beagle Security | Subscription | Usage-based test quotas and team add-ons; transparent tiered pricing | Free trial + plans from $119/month (Essential) and $359/month (Advanced); Enterprise starts around $6,850/year |
Acunetix vs Nessus vs Beagle Security: Customer reviews comparison
| Aspect | Acunetix | Nessus | Beagle Security |
|---|---|---|---|
| G2 rating | 4.1 / 5 | 4.5 / 5 | 4.7 / 5 |
| Ease of use | High | High | High |
| Accuracy | High for web applications | High for infrastructure | High with application context |
| Reporting clarity | High | Moderate | Very high |
| False positives | Low (proof-based) | Moderate | Low |
| Common criticism | Pricing increases with scale | Asset-based licensing, limited AppSec depth | Focused primarily on apps and APIs |
Acunetix reviews
G2 rating: 4.1 / 5
Acunetix (by Invicti Security) is frequently praised for its proof-based scanning, which helps confirm exploitability and reduce false positives in web application testing. Reviewers highlight strong detection of OWASP Top 10 vulnerabilities, clear reporting, and reliable automation for DAST workflows.
Common feedback themes include:
Accurate identification of web vulnerabilities
Reduced false positives compared to traditional DAST
Clean and usable reports
Higher cost as the number of targets or scan scope increases
Nessus reviews
G2 rating: 4.5 / 5
Nessus is consistently reviewed as a reliable and mature infrastructure vulnerability scanner. Users value its extensive plugin library, regular updates, and ease of deployment across networks and hosts. It is commonly used for vulnerability management and compliance-driven scanning.
Common feedback themes include:
Broad vulnerability and CVE coverage
Strong credentialed scanning
Useful compliance and audit reporting
Asset-based licensing costs
Limited visibility into application-layer and business-logic issues

Beagle Security reviews
G2 rating: 4.7 / 5
Beagle Security reviews often emphasize actionable, developer-friendly reporting and ease of setup for web and API penetration testing. Users highlight its ability to handle authenticated workflows, simulate real attack paths, and provide contextual evidence that helps prioritize fixes.
Common feedback themes include:
Clear remediation guidance for developers
Automated authenticated testing
Strong focus on web and API security
Improved collaboration between security and engineering teams
Acunetix vs Nessus vs Beagle Security: Which is best for you?
Choose Acunetix if:
Your primary focus is web application vulnerability scanning
You want proof-based validation
You follow a traditional AppSec workflow
Choose Nessus if:
Your priority is infrastructure vulnerability management
Compliance and asset visibility are critical
You need a mature enterprise scanning tool
Choose Beagle Security if:
You need exploit-focused web and API testing
Developer-friendly, contextual findings matter
Continuous testing in CI/CD is a priority
Many organizations use a layered approach, combining infrastructure scanners with application-focused penetration testing.
Try Beagle Security for free to see how it compares to Acunetix and Nessus
Beagle Security provides automated penetration testing designed specifically for modern web applications and APIs, going beyond traditional vulnerability scanners that focus primarily on known signatures or infrastructure-level issues. By simulating real-world attack scenarios, Beagle helps teams identify exploitable security gaps, business logic flaws, and API-specific risks that are often missed by conventional tools.
Teams can start with a 14-day free trial, which includes full access to Beagle Security’s application and API testing capabilities. This allows security and engineering teams to run scans against real environments, review contextual findings, validate false positives quickly, and assess reporting quality before committing to a paid plan. For organizations with more complex environments or specific evaluation needs, Beagle Security also offers an interactive demo, where teams can walk through features, workflows, and integrations in detail with product experts.
This trial-and-demo approach makes it easier to directly compare Beagle Security’s accuracy, usability, and reporting clarity against tools like Acunetix and Nessus in a practical, hands-on way.



![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)