![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six.webp)
Vendor applications are now embedded across every enterprise workflow, from identity systems to finance automations to customer experience platforms. This interconnected landscape increases efficiency, but it also expands the attack surface. A single untested vendor integration can expose sensitive data, API keys, authentication tokens, and privileged workflows. This reality has made vendor application security testing essential for modern organizations.
In 2026, security leaders are focusing on tools that can test vendor applications without requiring source code, support API-heavy architectures, and integrate with DevSecOps pipelines. This guide explores the top vendor application security testing tools for 2026 and helps you choose the right option for your environment.
Comparison table
| Tool | Starting price | Strengths | Best for |
|---|---|---|---|
| Beagle Security | From 119 USD/month (Starter) | Automated DAST and API testing, logic-based workflows, continuous monitoring, AI-assisted analysis | Vendor testing, API-first applications, continuous assessment |
| Veracode | Custom pricing | SAST, DAST, SCA, enterprise governance, binary scanning | Regulated industries, large vendor ecosystems |
| Checkmarx One | Quote-based | Unified SAST, SCA, API scanning, strong CI/CD integration | Enterprises with deep code-level access |
| Fortify | Quote-based | Mature SAST and DAST, hybrid deployment, policy-heavy workflows | Highly regulated environments and legacy systems |
| Snyk | Free tier, paid plans start at 25 USD/month | SCA + SAST, developer-first workflow, fast scans | Vendor components, plugin ecosystems, dependency audits |
| Mend.io | AI Native AppSec Platform: up to $1,000 AI Premium add-on: up to $300 Renovate Enterprise: up to $250 | Strong SCA, policy enforcement, supply chain visibility | Open-source dependency auditing for vendor software |
Beagle Security
Beagle Security is a cloud-based application security testing platform built for automated DAST and API penetration testing. It focuses on real attack simulations that mimic active threat behavior, making it particularly effective for vendor application assessments where organizations do not have access to the vendor’s internal codebase. Its logic-based testing and API discovery features help uncover deeper vulnerabilities, including business logic flaws and hidden endpoints that traditional scanners may overlook. Beagle Security is designed for continuous testing, which is important for monitoring vendor software updates or silent changes.
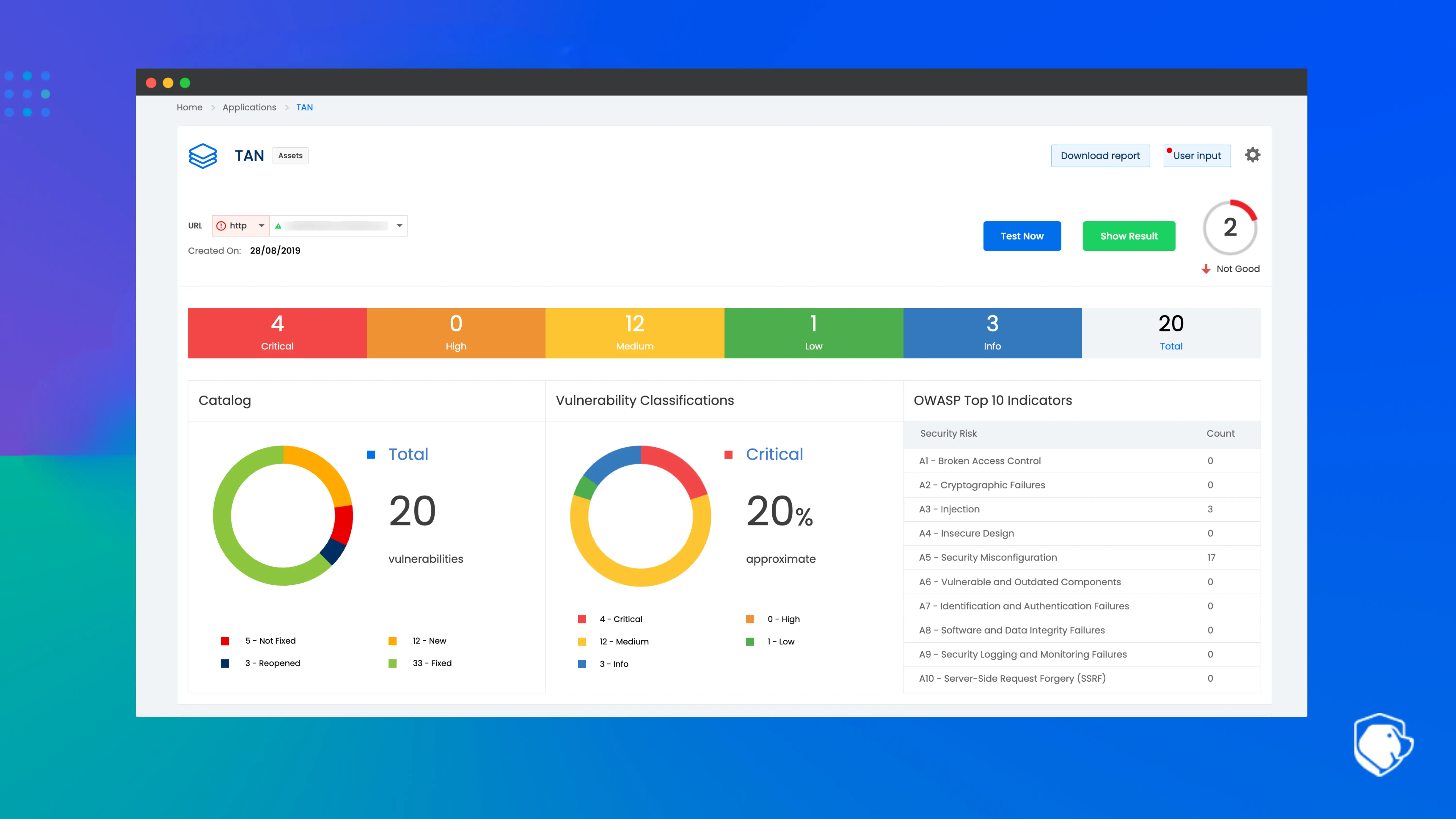
Key features
Automated DAST for web and SaaS applications
API security testing for REST and GraphQL
Logic-based scenarios for business workflow validation
API discovery for hidden or undocumented endpoints
CI/CD and SCM integration
AI-assisted remediation recommendations
Continuous monitoring to detect new risks introduced during software updates
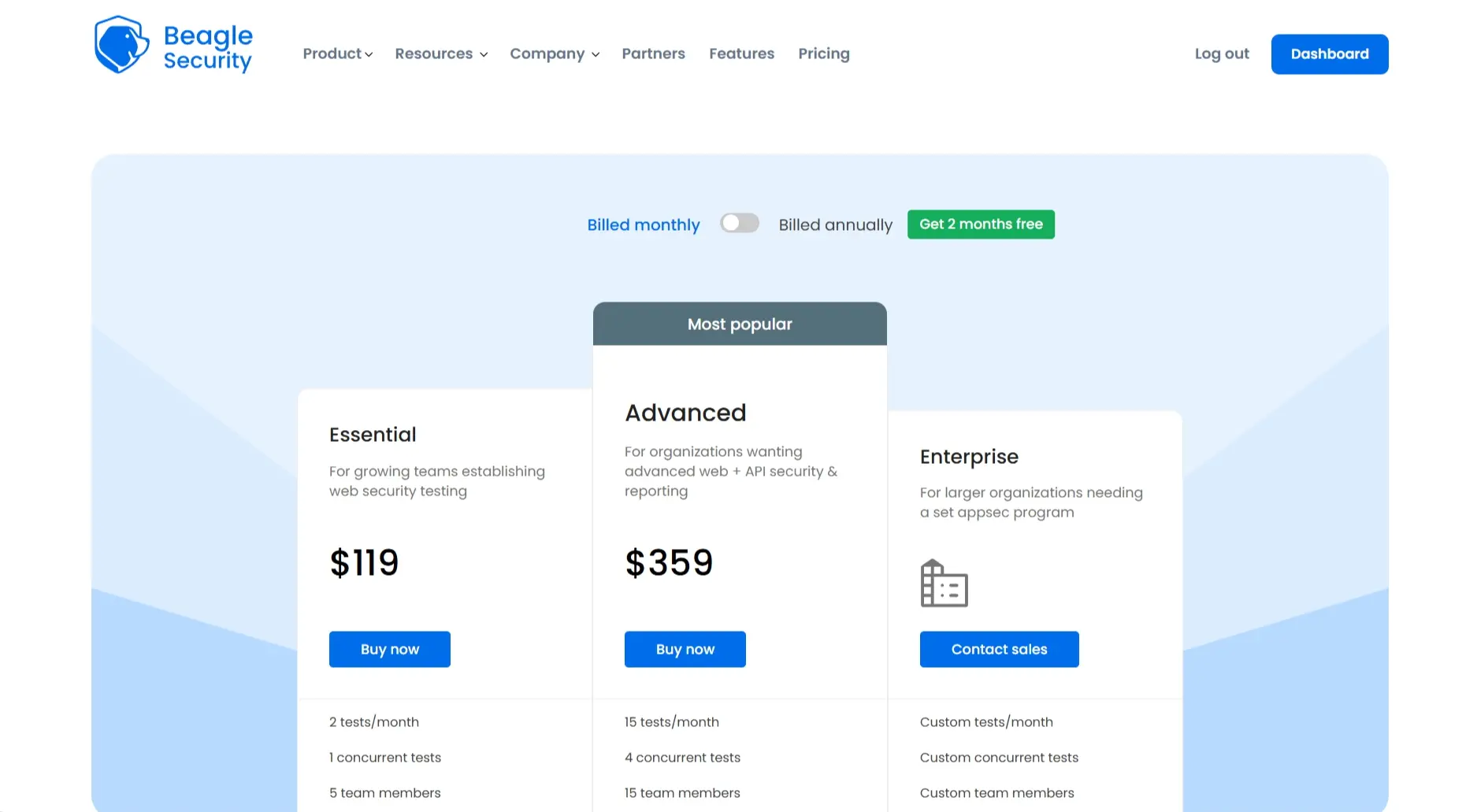
Pricing (2026)
Free tier
Essential: 119 USD/month
Advanced: 359 USD/month
Custom enterprise plans available
G2 rating
4.7 out of 5
Why consider it
Beagle Security is well suited for vendor assessments because it tests running applications from the outside, just like an attacker. It does not require source code, supports frequent testing, and identifies risks introduced during vendor updates. The API discovery feature is useful for identifying unlisted vendor endpoints that could expose sensitive data.
Veracode
Veracode is an enterprise-grade application security testing platform known for its comprehensive SAST, DAST, SCA, and manual penetration testing capabilities. Its cloud-native architecture supports consistent and scalable testing across large development ecosystems. Veracode is deeply embedded in compliance-heavy sectors because of its strong governance workflows, detailed reporting, and standardized testing methodologies. It supports both source code and binary analysis, making it effective for evaluating vendor-provided code even when source access is limited.
Key features
SAST, DAST, SCA, and manual penetration testing available in one platform
Binary and compiled code analysis for vendor applications without source-level access
Detailed reporting and compliance dashboards aligned with SOC 2, PCI DSS, and ISO requirements
Deep language and framework support across enterprise tech stacks
Governance workflows for managing vendor risk at scale
Enterprise integrations with CI/CD pipelines and SDLC tools
Pricing (2026)
- Quote-based depending on modules and scale. Based on public values, pricing starts approximately $15000/year for basic solutions and can go beyond $100000 for full enterprise suites.
G2 rating
4.4 out of 5
Why consider it
Veracode is best for organizations evaluating vendor-provided code or binaries. It offers strong compliance-focused reporting and is frequently used in sectors like BFSI, healthcare, and government.
Checkmarx One
Checkmarx One is a unified AppSec platform that consolidates SAST, SCA, IAST, API scanning, and IaC analysis under a single cloud-based console. It is widely recognized for its developer-centric ecosystem, customizable scanning rules, and ability to secure complex development pipelines. Checkmarx One recently maintained its position as a Leader in the Gartner Magic Quadrant for Application Security Testing, further strengthening its enterprise credibility.
Key features
Customizable SAST rules with broad language and framework support
SCA for open-source dependency insights and licensing risks
API scanning for OpenAPI-based and non-standard API specifications
CI/CD, SCM, and IDE integrations
Intelligent prioritization to reduce noise and highlight high-impact risks
Unified dashboard for all application security testing activities
Pricing (2026)
- Enterprise quote-based, public minimums ~US$30,000/year.
G2 rating
4.5 out of 5
Why consider it
Checkmarx excels when vendors provide source code or when you handle outsourced development. It is especially useful when you need deep scanning combined with governance and reporting.
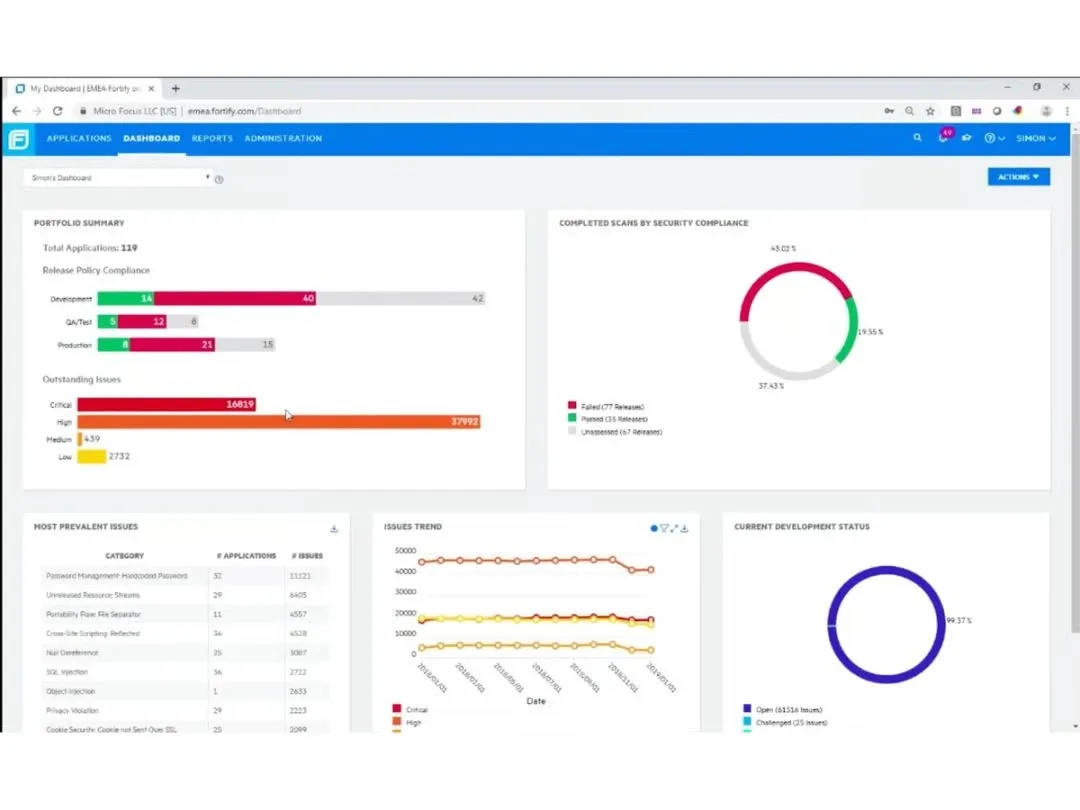
Fortify
Fortify by OpenText is one of the most established application security testing tools, offering both SAST and DAST. It is known for its policy-driven workflows, strong support for legacy systems, and ability to operate in on-premise or hybrid environments. Its WebInspect product provides dynamic testing, while Fortify Static Code Analyzer supports a wide range of programming languages.
Key features
SAST with extensive language coverage
Fortify WebInspect for DAST
On-premise, cloud, and hybrid support
Custom rulepacks and policy enforcement
Strong reporting and audit trail management
Pricing (2026)
- Quote-based, dependent on deployment model
G2 rating
4.2 out of 5
Why consider it
Fortify is ideal for organizations with legacy applications or strict regulation requirements. It fits well into environments needing on-premise scanning for vendor-delivered applications.
Snyk
Snyk is a developer-focused application security platform known for its SCA and SAST capabilities. It integrates directly into Git repositories, IDEs, and CI/CD workflows, making it convenient for engineering teams to fix issues during development. Snyk’s dependency scanning and license analysis are particularly strong, which is crucial when auditing vendor software that includes third-party packages.
Key features
Deep SCA with license compliance
Fast SAST with AI-powered suggestions
Direct integration into GitHub, GitLab, Bitbucket, and IDEs
Policy and compliance controls
Strong ecosystem coverage for open-source software
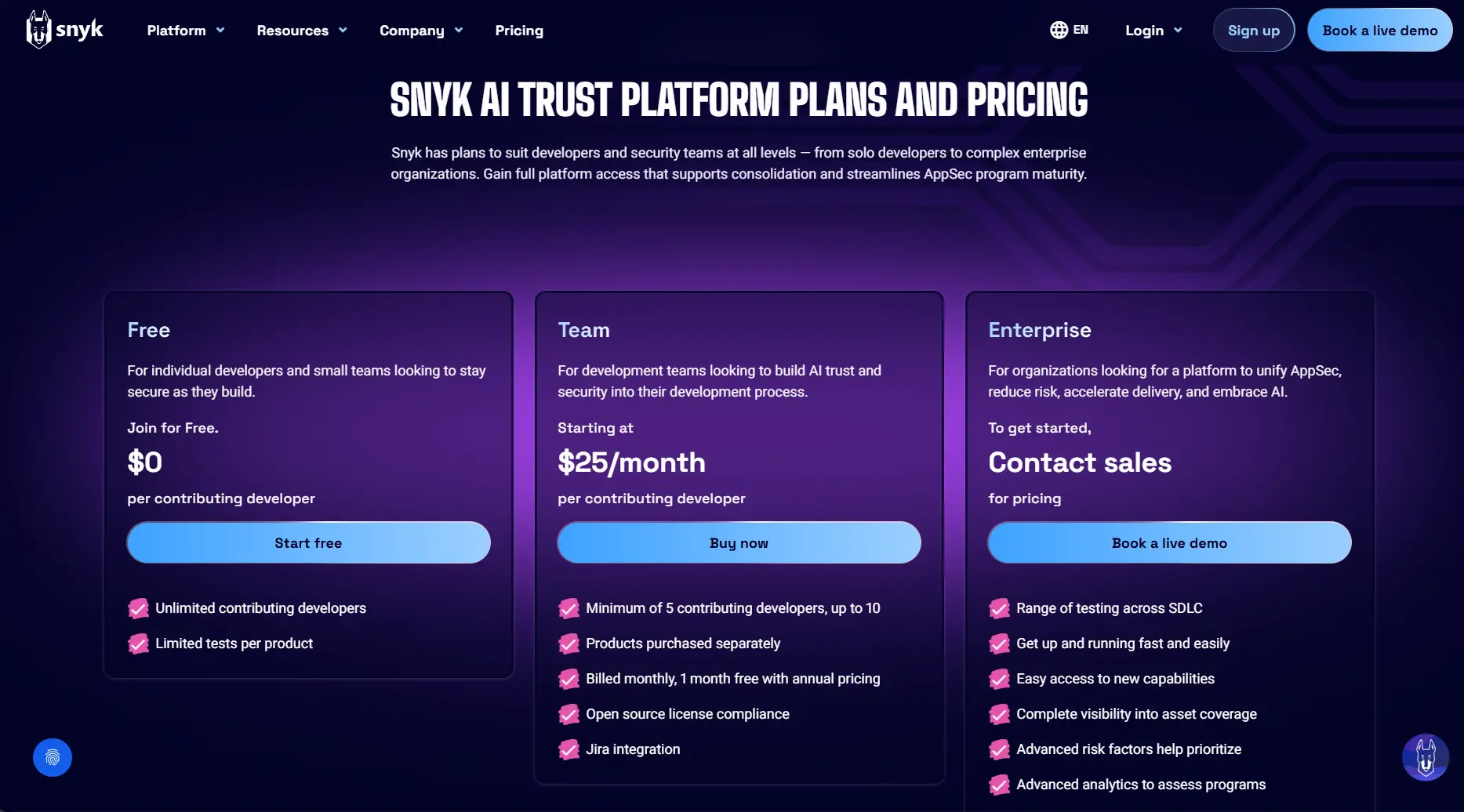
Pricing (2026)
Free tier available
Paid plans start around 25 USD/month for teams
Enterprise: Custom quote
G2 rating
4.6 out of 5
Why consider it
Snyk is ideal for analyzing vendor-supplied code components, SDKs, plugins, or integration libraries. It is especially valuable for dependency-heavy applications.
Mend.io
Mend.io (formerly WhiteSource) specializes in software composition analysis and open-source risk management. It provides deep visibility into the dependencies within vendor software and automates policy enforcement around licensing and version control. Mend.io is widely used in large enterprises with heavy open-source usage and complex supply chains.
Key features
Comprehensive SCA with vulnerability and dependency tracking
Policy-based enforcement for licensing and versioning
Continuous monitoring of open-source components
Integration with Git-based workflows and enterprise CI/CD tools
Detailed license analysis for compliance and governance
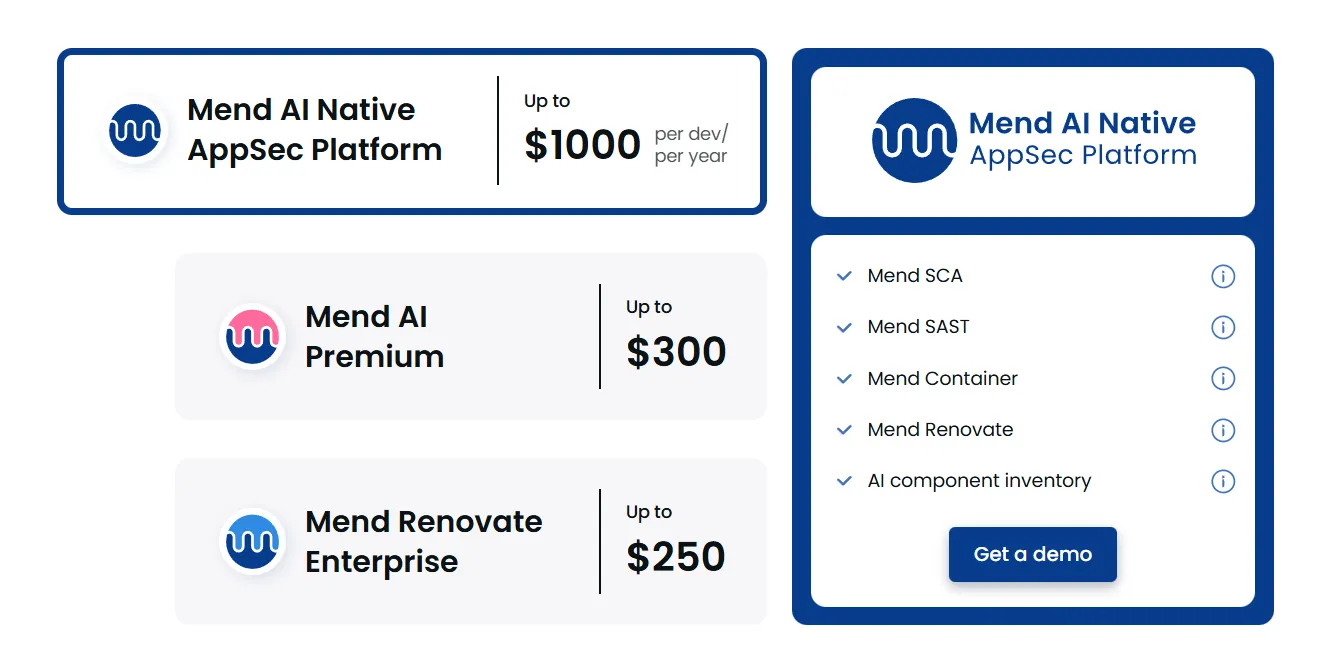
Pricing (2026)
Pricing is based on cost per contributing developer, not per scan or project.
AI Native AppSec Platform: up to 1000 USD per developer per year.
Mend AI Premium add-on: up to 300 USD per developer per year.
Mend Renovate Enterprise (dependency management): up to 250 USD per developer per year.
G2 rating
4.5 out of 5
Why consider it
Mend.io is a strong choice for organizations evaluating vendor software dependencies. It helps identify whether the vendor is introducing outdated libraries or high-risk components.
Final thoughts
Vendor applications now sit at the center of enterprise operations, making vendor application security testing a critical component of modern risk management. As supply chains become more interconnected and vendors integrate more deeply with core business systems, the exposure created by insecure third-party software increases significantly. A well-structured testing strategy allows security leaders to identify vulnerabilities early, validate vendor security claims with real evidence, and maintain confidence in the systems their organization depends on. This approach also supports compliance with SOC 2, ISO 27001, and other frameworks that require continuous oversight of third-party risk.
If you are building or improving your vendor testing workflow, Beagle Security offers a practical starting point with automated DAST and API testing, continuous monitoring, and logic-based scenarios that reveal issues traditional scanners often miss. These capabilities help you evaluate vendor applications the same way an attacker would, without requiring source code or specialized deployment access. You can explore its full functionality through the 14-day advanced trial or use the interactive demo to understand how automated vendor assessment fits into your existing AppSec and third-party risk processes.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Acunetix vs Qualys: Which is the best choice for you? [2026] Acunetix vs Qualys: Which is the best choice for you? [2026]](/blog/images/blog-banner-six-cover.webp)
![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)