![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four.webp)
Enterprise AppSec in 2026 is no longer about running isolated scans at the end of a release cycle. Modern software delivery involves cloud-native architectures, AI-powered code generation, distributed development teams and increasingly complex supply-chain dependencies. This shift has forced security and engineering leaders to adopt platforms that can provide unified visibility, automated testing, and policy-driven governance across the entire SDLC.
The tools in this guide represent the strongest enterprise-grade AppSec solutions used for static analysis, dynamic testing, API security, SBOM generation, supply-chain protection and runtime defense. No organization uses a single tool; instead, they assemble a portfolio that fits their architecture, compliance obligations and development velocity.
This comparison highlights the top platforms that enterprises rely on in 2026, what each tool does best, how they differ, and how to choose the right one for your AppSec strategy. Each section includes category classification, concise explanations, strengths, pricing expectations, G2 ratings, and important considerations to note when evaluating the tool.
Comparison table
| Tool | Starting price | What it does | Target audience |
|---|---|---|---|
| Beagle Security | $119/mo for basic plans, Enterprise pricing is custom | Automated web & API vulnerability testing | Engineering teams needing automated attack simulation |
| Veracode | Enterprise pricing is custom | SAST, SCA, DAST, governance | Large enterprises with compliance-heavy SDLC |
| Checkmarx | Enterprise pricing is custom | SAST-led AppSec platform | Enterprises prioritizing deep static analysis |
| Snyk | Free tier; business plans from $25/user/mo | Developer-first SCA, IaC, container security | Cloud-native teams |
| Cycode | Enterprise pricing is custom | ASPM + supply chain security | Organizations needing SDLC-wide visibility |
| Mend.io | Enterprise pricing is custom | SCA, license compliance, SBOM | Open-source heavy companies |
| Contrast Security | Enterprise pricing is custom | IAST + RASP runtime instrumentation | Teams needing real-time application protection |
| GitHub Advanced Security | $19/user for Secret protection tier $30/user for Code security tier | CodeQL, secret scanning, dependency security | GitHub Enterprise users |
| Black Duck | Enterprise pricing is custom | SCA + license and compliance management | Large regulated enterprises |
| Fortify | Enterprise pricing is custom | SAST + governance dashboards | Large enterprises needing on-premise governance |
Beagle Security
Category: Automated web and API vulnerability testing
Beagle Security specializes in automated vulnerability testing for web applications, APIs and GraphQL endpoints using real-world attack simulation. Unlike traditional scanners, it focuses on producing actionable remediation guidance in developer-friendly formats, making it accessible to teams without a dedicated AppSec department. Its continuous testing model allows organizations to run assessments automatically during each release cycle or on new deployments. Teams rely on Beagle for fast feedback loops, realistic attack paths and automated reporting that can be shared with engineering leadership. It is particularly effective for growing companies modernizing their testing processes.
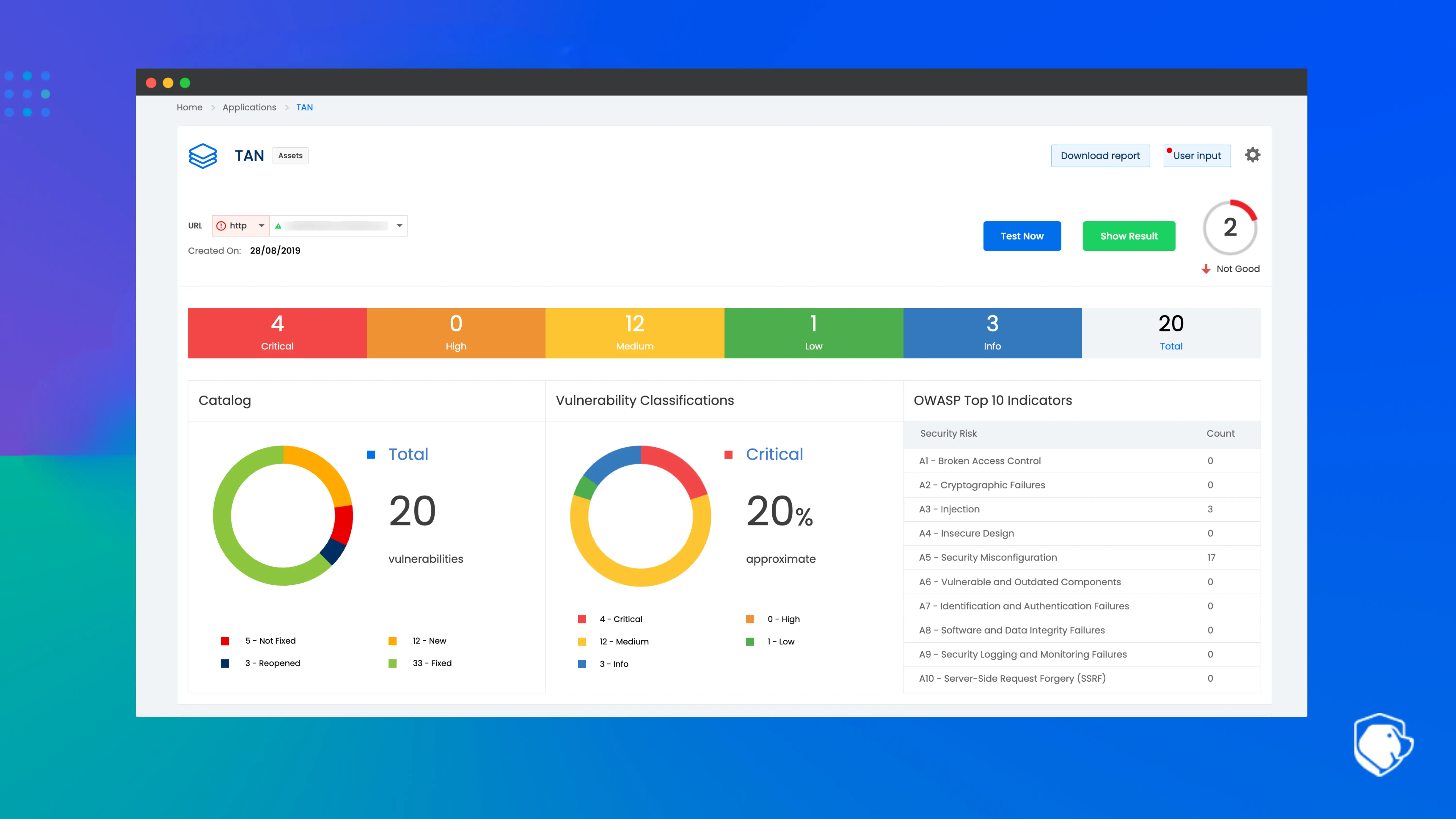
Strengths
Real-world attack simulation
Strong API and GraphQL coverage
Clean, developer-ready reports
CI/CD integration
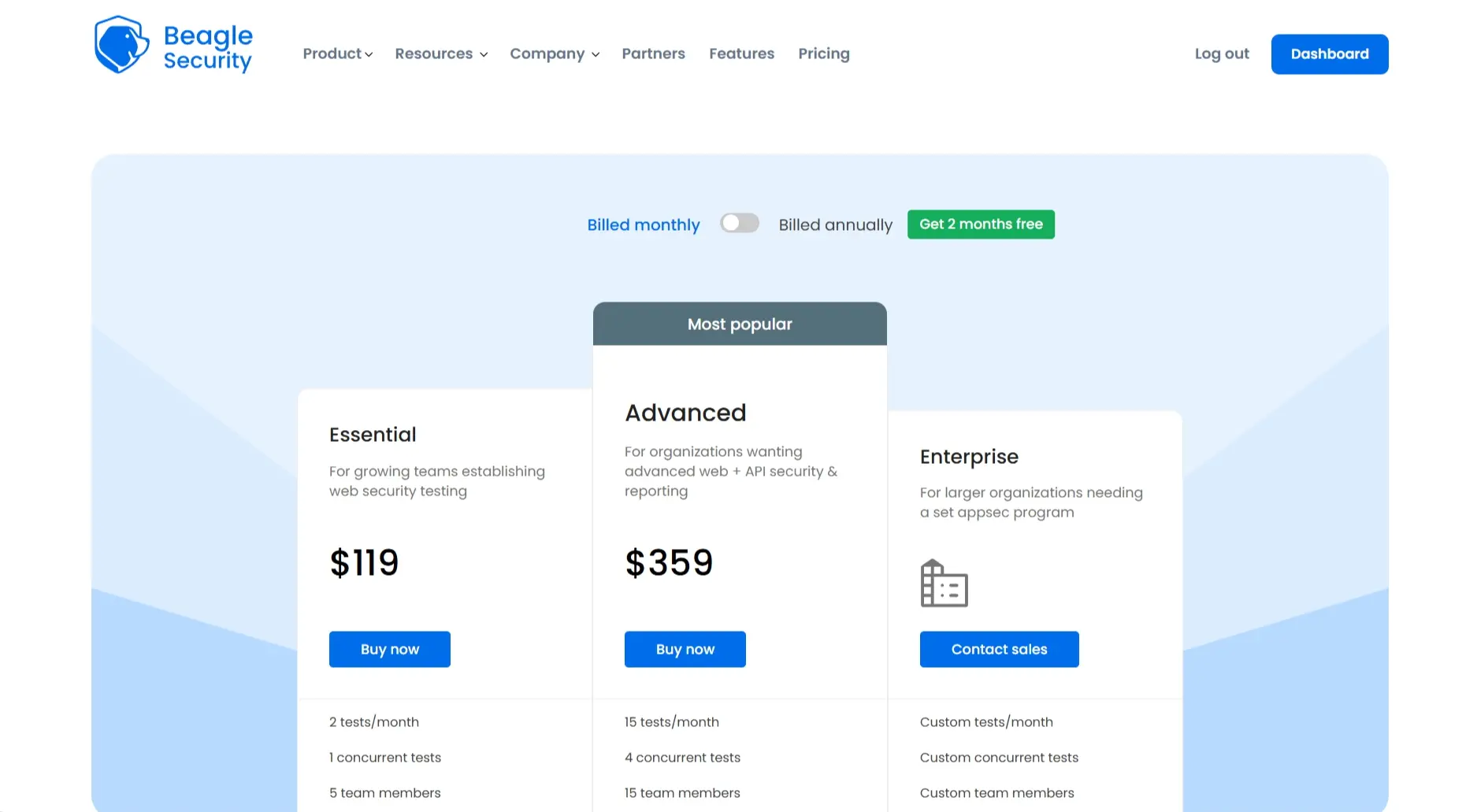
Pricing
essential tier: $119/mo
Advanced tier: $359
Custom pricing for enterprises typically starts around $6,850/year
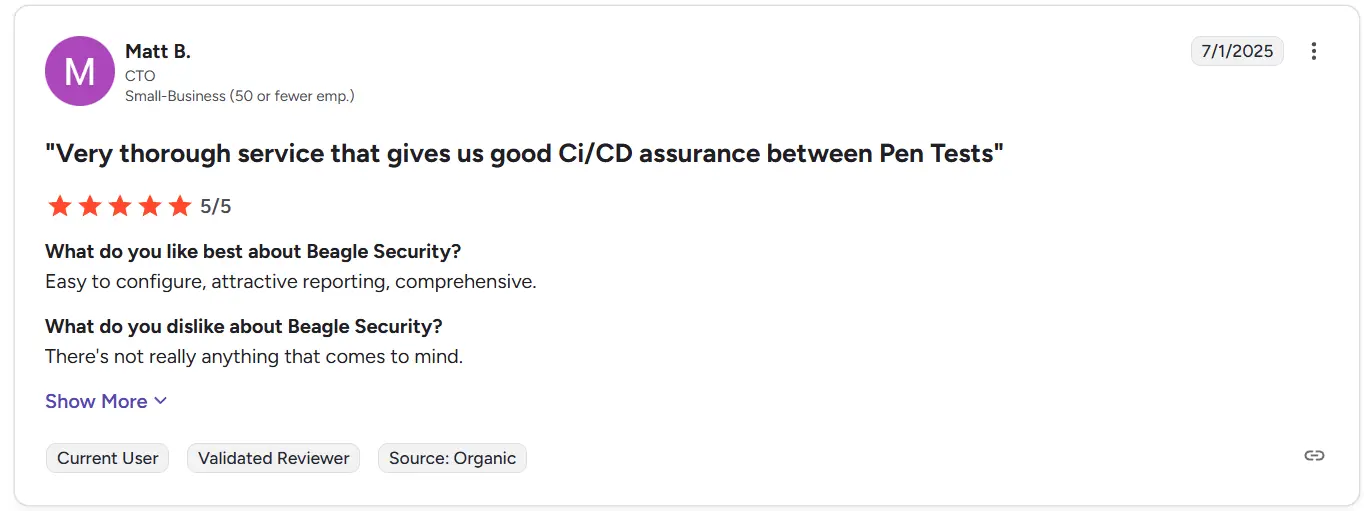
G2 rating
Beagle Security holds a 4.7/5 rating on G2, with users consistently praising its ease of use and automated vulnerability testing capabilities. Reviewers highlight how quickly teams can begin scanning web apps, APIs and GraphQL endpoints, often without needing any prior security expertise.
Veracode
Category: Enterprise SAST + SCA + policy governance
Veracode is one of the most established enterprise AppSec platforms, offering SAST, SCA, DAST and mature governance frameworks. Its centralized management console enables security leaders to enforce policies consistently across hundreds of teams, making it strong for large enterprises with regulated SDLC requirements. Veracode’s architecture is designed for scale, with a robust pipeline for onboarding multiple applications and managing large vulnerability datasets. It also offers compliance-focused reporting, which many fintech, healthcare and government organizations rely on during audits. Its training and developer enablement features round out a full enterprise program.
Strengths
Extremely mature governance and reporting
Deep SAST coverage
Large language/framework support
Proven enterprise scalability
Pricing
Fully custom enterprise pricing.
G2 rating
Veracode maintains a solid 3.9/5 G2 rating, reflecting its reputation as one of the most mature and enterprise-ready AppSec platforms. Users appreciate its reliable static and software composition analysis, although some mention a learning curve when configuring scans.
Checkmarx
Category: SAST-led AppSec platform
Checkmarx is known for its highly sophisticated static analysis engine, customizable rulesets and deep scanning accuracy. The Checkmarx One platform integrates SAST, SCA, API security scanning and IaC analysis under one umbrella. Its customization capabilities stand out, allowing advanced AppSec teams to fine-tune rules for internal coding conventions and proprietary frameworks. Enterprises choose Checkmarx when they need precise detection of code-level vulnerabilities across large repositories. It integrates well with Git, CI/CD pipelines and modern IDEs, making it a developer-friendly yet enterprise-durable solution.
Strengths
Highly accurate and customizable SAST
Wide language support
Strong for monorepos and large systems
Mature enterprise deployment model
Pricing
Enterprise pricing is custom, contact vendor for more details.
G2 rating
Checkmarx carries a strong 4.4/5 rating on G2, driven by user praise for its highly accurate and configurable SAST engine. Many reviewers say Checkmarx stands out when scanning large or complex codebases, where its customizable rules help reduce false positives while uncovering deeply rooted issues. Some reviews also mention that teams get the most from Checkmarx when a dedicated AppSec engineer fine-tunes configurations
Snyk
Category: developer-first SCA + container + IaC security
Snyk focuses on enabling developers to fix vulnerabilities early with minimal friction. Its coverage spans open-source dependencies, containers, IaC templates and cloud configurations. Snyk’s ecosystem of integrations is one of the strongest on the market, with seamless connections to GitHub, GitLab, Jenkins, VS Code and cloud providers. The platform excels at identifying actionable fixes, offering upgrade suggestions and pull requests that remediate issues automatically. For cloud-native and agile teams, Snyk provides rapid scanning and highly contextual vulnerability data that maps directly to developer workflows.
Strengths
Excellent developer experience
Fast scans with actionable fixes
Great for cloud-native stacks
Wide ecosystem integration
Pricing
Free tier available; business plans from $25/user/month.
G2 rating
Snyk enjoys an impressive 4.5/5 G2 rating, reflecting its strong adoption among developers and DevOps teams. Users love how seamlessly Snyk fits into everyday workflows, offering fast SCA, container and IaC scans along with automated PRs for dependency upgrades. Some reviewers also note that pricing scales with team size.
Cycode
Category: ASPM + software supply chain security
Cycode takes a unified, SDLC-wide approach by correlating signals from source control, build pipelines, artifacts, cloud environments and deployments. This provides a single-pane view of application security posture. Its ASPM (Application Security Posture Management) capabilities allow teams to prioritize vulnerabilities based on context, such as exploitability, asset value, exposure and pipeline weaknesses. Cycode is especially effective in enterprises running multiple CI/CD tools, as it centralizes governance and enforces policies at every stage. It helps organizations reduce supply-chain risk by protecting the integrity of code, pipelines and dependencies.
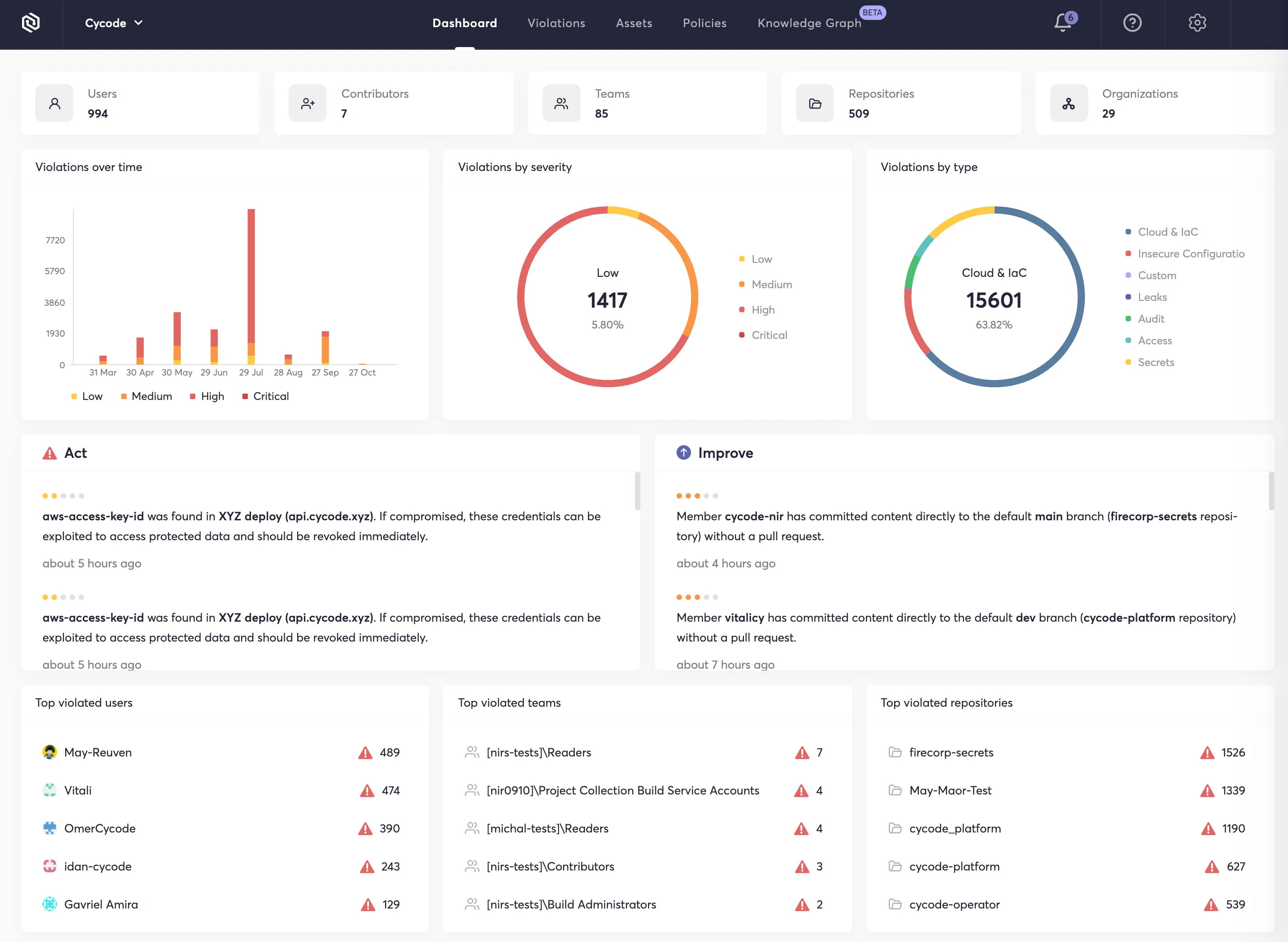
Strengths
Best-in-class SDLC visibility
Strong supply-chain protection
Centralized policy enforcement
Correlation-driven prioritization
Pricing
Enterprise pricing is custom, contact vendor for more details.
G2 rating
Cycode is rated 4/5 on G2, with users praising its SDLC-wide visibility and ability to correlate risks across source control, CI/CD pipelines, cloud infrastructure and deployment environments.
Mend.io
Category: SCA + license compliance + SBOM management
Mend.io excels at open-source dependency management, license compliance and automated policy creation. It provides SBOM generation at scale, helping enterprises meet security and regulatory requirements. Mend’s automation engine can enforce policies across repositories, blocking risky dependencies and guiding teams toward secure alternatives. Its dashboard gives visibility into open-source vulnerabilities across hundreds of applications. Enterprises choose Mend when they need strong legal compliance, accurate component tracking and integration into complex build environments.
Strengths
Deep license and compliance management
Automated dependency governance
Clear SBOM and inventory reporting
Solid enterprise integrations
Pricing
Custom enterprise pricing.
G2 rating
Mend.io holds a 4.3/5 rating on G2, largely due to its accuracy in SCA scanning, detailed open-source license compliance and enterprise-grade SBOM support. Users highlight how Mend automates dependency governance across large portfolios and provides clear insights into legal, security and compliance risks.
Contrast Security
Category: IAST + RASP runtime instrumentation
Contrast Security uses instrumentation inside applications rather than external scans. This gives real-time detection of vulnerabilities with high accuracy, since findings are based on actual runtime behavior. Its IAST engine detects exploitable flaws during testing, while RASP extends protection into production environments. This approach reduces noise and provides actionable evidence developers can use immediately. Enterprises with microservices or distributed application architectures value Contrast for continuous insight into how apps behave under real workloads.
Strengths
Runtime-based accuracy
Low false positives
Continuous assessment
Strong for microservice architectures
Pricing
Enterprise pricing is custom, contact vendor for more details.
G2 rating
Contrast Security maintains an excellent 4.5/5 G2 rating, driven by extremely positive feedback about its runtime-based accuracy. Reviewers emphasize that Contrast’s IAST and RASP instrumentation significantly reduce false positives because findings are validated in real application execution.
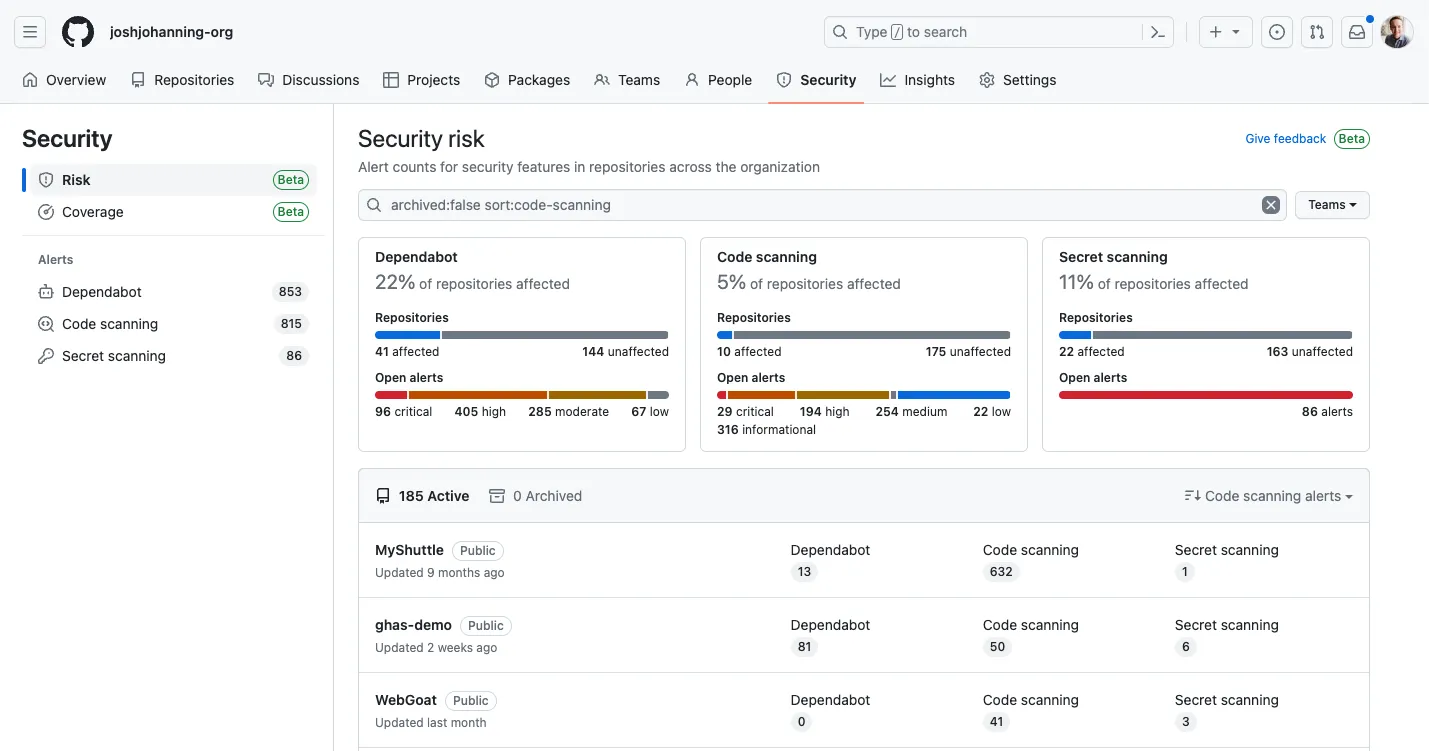
GitHub Advanced Security
Category: code scanning + secret scanning + dependency security
GitHub Advanced Security integrates security into the platform developers already use daily. Its CodeQL engine is known for precision and flexibility, enabling deep semantic code analysis. Secret scanning prevents credential leakage, while Dependabot helps maintain secure dependency versions. GHAS offers organization-wide insights, making it easy for security teams to monitor risk across hundreds of repositories. Because it is native to GitHub, adoption is straightforward, reducing tool fragmentation.
Strengths
Frictionless GitHub-native integration
Accurate CodeQL scanning
Automated dependency updates
Centralized organization security overview
Pricing
$19/user for Secret protection tier
$30/user for Code security tier
G2 rating
GitHub Advanced Security has one of the highest G2 scores in the AppSec category at 4.7/5, with reviewers praising how seamlessly security is woven into daily development workflows. Because GHAS operates directly inside GitHub, teams report dramatically lower friction compared to external tools.
Black Duck
Category: enterprise SCA + compliance management
Black Duck is a leading enterprise SCA tool favored in highly regulated sectors. It provides rigorous compliance checks, open-source risk identification and deep policy enforcement. Its license management engine is one of the most comprehensive on the market, making it suitable for companies managing strict legal frameworks. Black Duck integrates across repos, build systems and artifact repositories to produce detailed SBOMs and vulnerability inventories. For large organizations managing thousands of components, it offers unmatched governance capabilities.
Strengths
Strong license compliance engine
Large enterprise adoption
Deep SBOM and inventory reporting
Works well in regulated industries
Pricing
Enterprise custom.
G2 rating
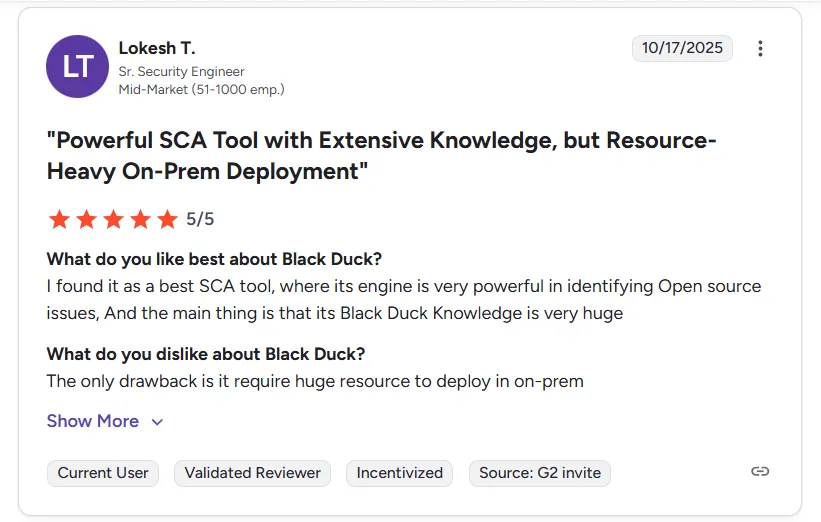
Black Duck carries a 4/5 G2 rating, particularly valued by enterprises that need rigorous open-source compliance, license governance and SBOM generation. Users praise its broad component database, policy enforcement capabilities and deep visibility across applications and build ecosystems.
OpenText Fortify
Category: enterprise SAST + governance dashboards
OpenText Fortify has long been a trusted name in enterprise static analysis. Its Software Security Center (SSC) provides powerful dashboards for managing vulnerabilities across large portfolios. Fortify is known for strong on-premise support, making it a top choice for government, finance and critical infrastructure sectors. It delivers deep scanning capabilities, broad language support and extensive customization. Its governance features ensure compliance across multiple development teams, making it ideal for large, structured organizations.
Strengths
Robust SAST engine
Strong on-premise support
Centralized governance features
Ideal for large enterprises
Pricing
Enterprise pricing is custom, contact vendor for more details.
G2 rating
OpenText Fortify holds a 4.7/5 rating on G2, with users praising its robust static analysis, extensive language support and strong on-premise deployment options. Reviewers highlight the Software Security Center (SSC) as a valuable dashboard for tracking vulnerabilities across large portfolios and enforcing enterprise-wide policies.
Final thoughts
Enterprise AppSec in 2026 requires a layered approach. Each tool in this list solves a different part of the security equation, whether it be code analysis, open-source risk, runtime visibility, attack simulation or supply-chain integrity. The best strategy is selecting tools that complement each other, align with your SDLC and scale to your engineering organization’s needs. A strong AppSec program blends governance, developer enablement and automation, supported by platforms that give clear insight into risk across the entire application lifecycle.
Platforms like Beagle Security strengthen this layered approach by focusing on continuous, attack-driven testing across web applications and APIs. By simulating real-world exploits rather than relying solely on static findings, Beagle Security helps teams validate whether vulnerabilities are actually exploitable in production-like environments. Its CI/CD-friendly automation, clear risk prioritization, and developer-ready reports make it easier to turn security signals into fixes without slowing delivery. Check out our 14-day advanced trial or the interactive demo to see if we fit all your AppSec needs.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)
![Top GitLab DAST alternatives [2026] Top GitLab DAST alternatives [2026]](/blog/images/blog-banner-four-cover.webp)