Web applications have become a primary target for cybercriminals, with a staggering 73% of successful corporate breaches exploiting web application vulnerabilities.
As digital transformation accelerates, these applications represent both your organization’s greatest opportunity and its most exposed attack surface.
Traditional manual penetration testing cannot keep pace with modern development cycles, often leaving critical vulnerabilities undiscovered for months.
This blog will walk you through how to do penetration testing for a website using Beagle Security’s agentic AI penetration testing platform. We’ll cover why penetration testing is crucial, step-by-step instructions to get started, and how to interpret test results effectively.
By the end, you’ll have a clear understanding of how to build penetration testing into your development cycle to protect your business from evolving cyber threats.
Why website penetration testing is essential
Website penetration testing goes far beyond a compliance checkbox. It is a proactive strategy to defend against the reality of today’s cyber landscape.
Current threat landscape: More than 25,000 new CVEs are reported every year, with attackers increasingly automating their exploit methods. That means a single missed patch or misconfiguration can become an entry point within hours. In fact, web applications remain the most common initial attack vector.
Compliance requirements: Standards like PCI DSS, SOC 2, and HIPAA mandate penetration testing to ensure data protection. For businesses processing payments or handling sensitive information, regular pentesting is not optional and is legally required. A single compliance failure could cost not just fines, but long-term customer trust.
Cost efficiency: With the average breach costing $4.45 million, even a small vulnerability can be devastating. By contrast, investing in continuous penetration testing costs only a fraction of that and helps avoid reputational and financial damage.
Integration with SDLC: Penetration testing should not be an afterthought. With a “shift-left” approach, testing is integrated into the development pipeline, meaning vulnerabilities are detected before reaching production. This saves time, money, and effort compared to patching systems after release.
How to do penetration testing for a website using Beagle Security
Beagle Security streamlines website penetration testing with automation, AI-driven intelligence, and developer-friendly reporting. Here’s a breakdown of how to use the platform effectively.
Getting started
Sign up for your new Beagle Security account.
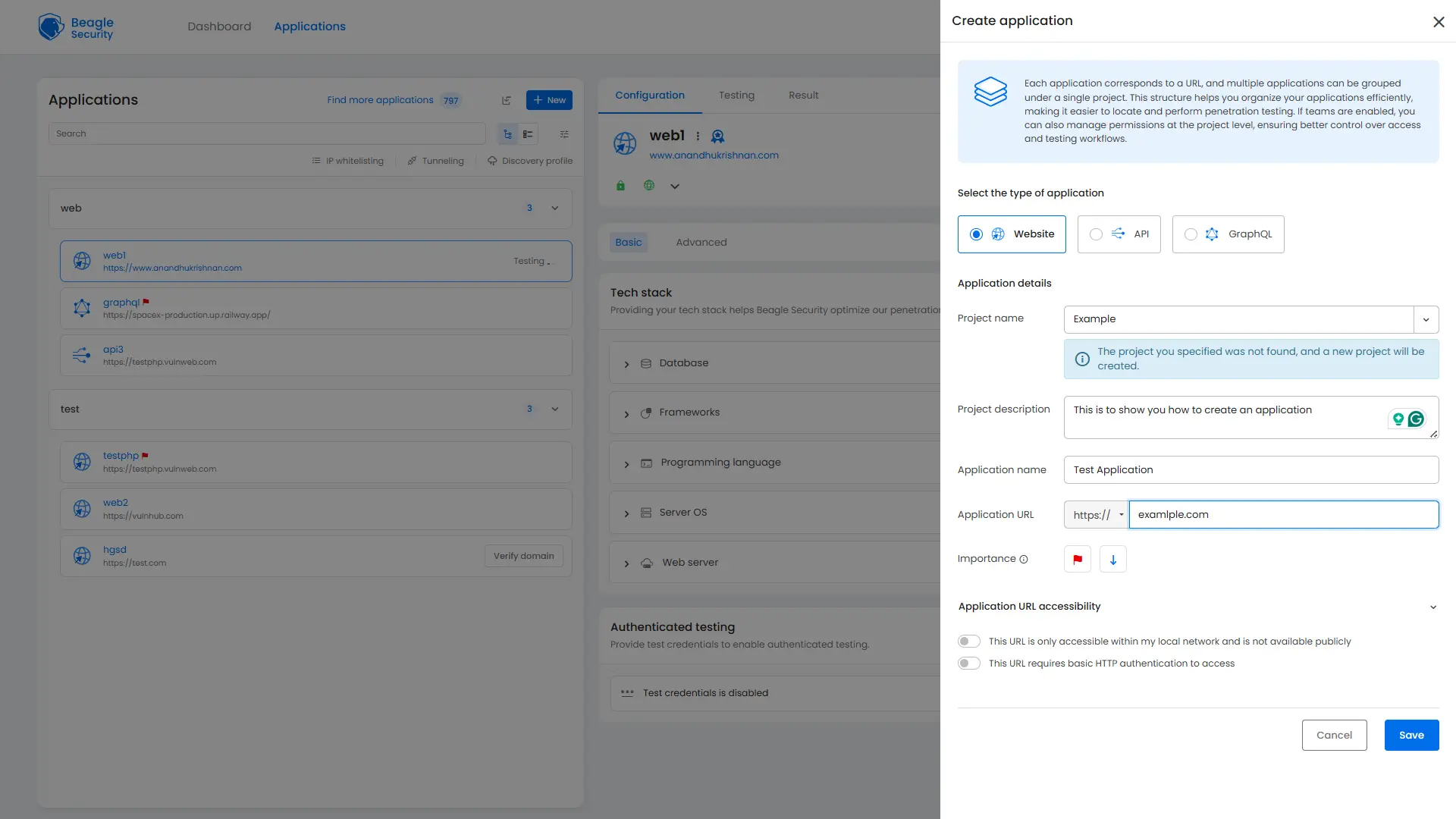
Create a new project with your application’s name and base URL.
Decide whether you want to run a black box or grey box penetration test.
Before launching a test, you need to verify domain ownership. Beagle Security supports:
File upload verification - upload a verification file to your server root
DNS record addition - add a TXT record to your domain’s DNS
HTML tag placement - insert a meta tag in your homepage
WordPress plugin installation - install and activate the official plugin for quick setup
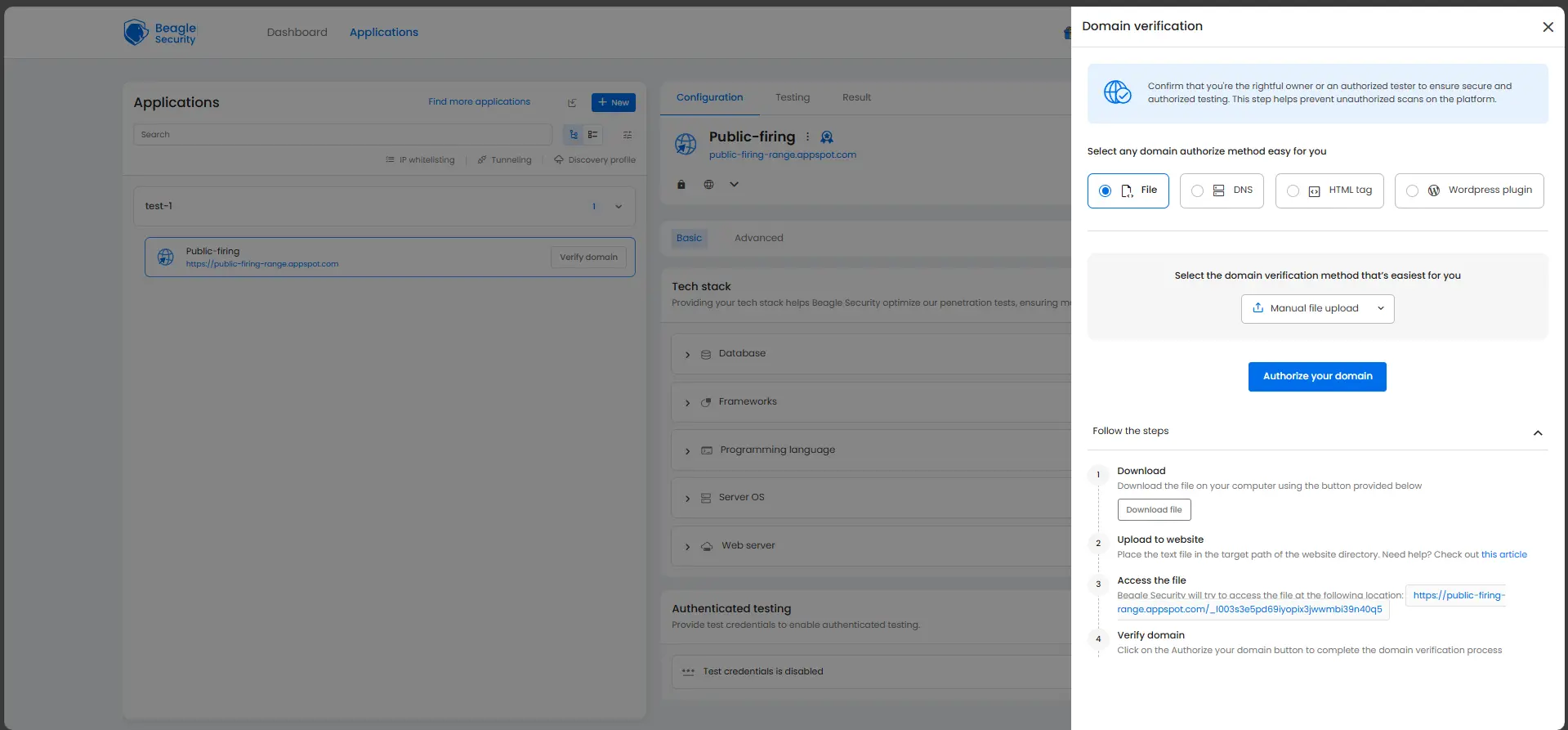
This ensures only authorized users can initiate penetration tests.
Deciding between black box and grey box penetration testing
Black box pentesting simulates an external attacker who has no prior knowledge of the system. It is ideal for understanding how your website appears to outsiders and what vulnerabilities could be exploited without authentication.
Grey box pentesting gives testers partial knowledge, such as user credentials, to explore deeper into workflows and business logic. This approach uncovers vulnerabilities in areas that authenticated users can access.
Most organizations benefit from running both approaches periodically: Black box for external threats, grey box for insider or authenticated risks.
Additional configurations for a grey box penetration test
Grey box testing gives you more control by allowing authenticated testing, tech stack optimization, business logic recording, and scope definition. Let’s walk through each.
Authenticated testing
Authenticated testing allows Beagle Security to assess vulnerabilities in restricted areas of your website that require login access.
This is critical for identifying risks in user dashboards, checkout processes, or internal portals. Beagle Security provides four methods of authentication setup, with Recorded Login being the recommended approach.
Method 1: Recorded login (recommended)
This method records your actual login process, ensuring that Beagle Security can accurately reproduce the steps to access authenticated areas.
Steps:
1. Install the plugin - Add the Beagle Sequence Recorder from the Chrome Web Store.
2. Access the plugin - After installation, locate the Beagle Security icon in the extensions section near your browser’s address bar.
3. Set up tokens - Open the extension and enter your Access Token (found in the dropdown menu of the profile button in the top right corner) and Application Token (found in your project settings).
4. Select sequence type - From the dropdown, choose Login as the sequence type.
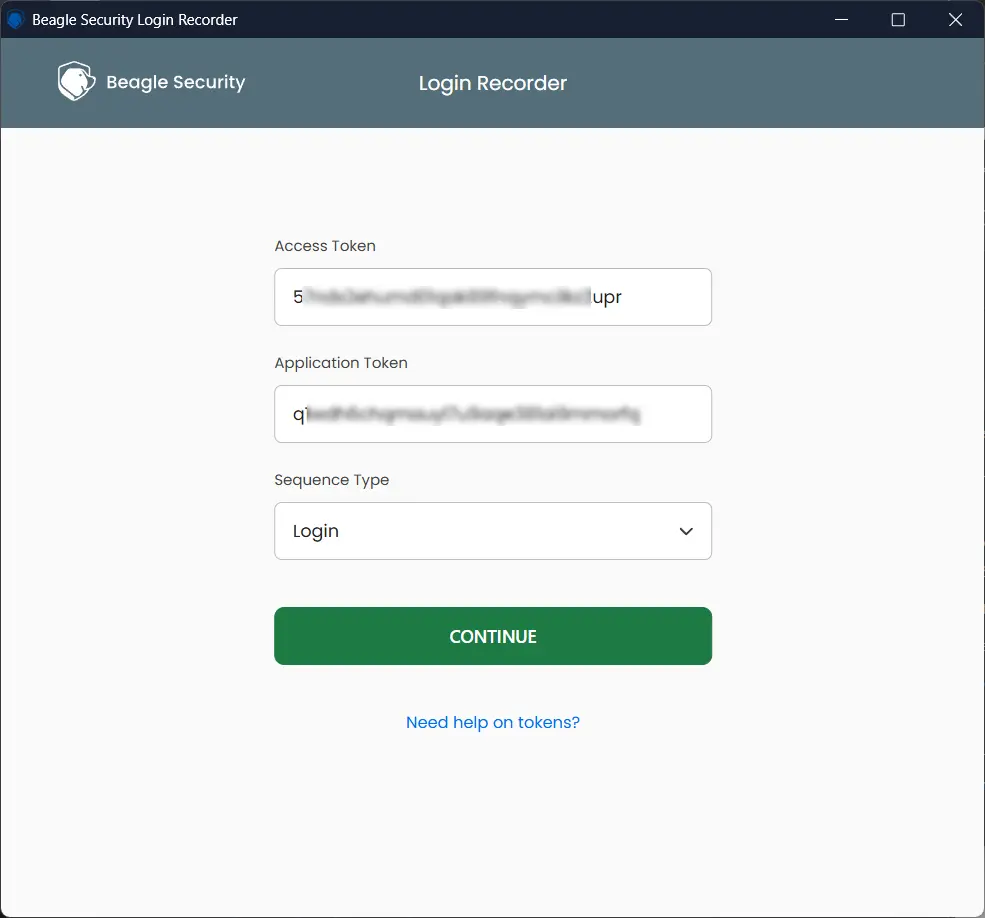
5. Start recording - Click Record to begin capturing your login sequence. A browser window linked to your application token will open.
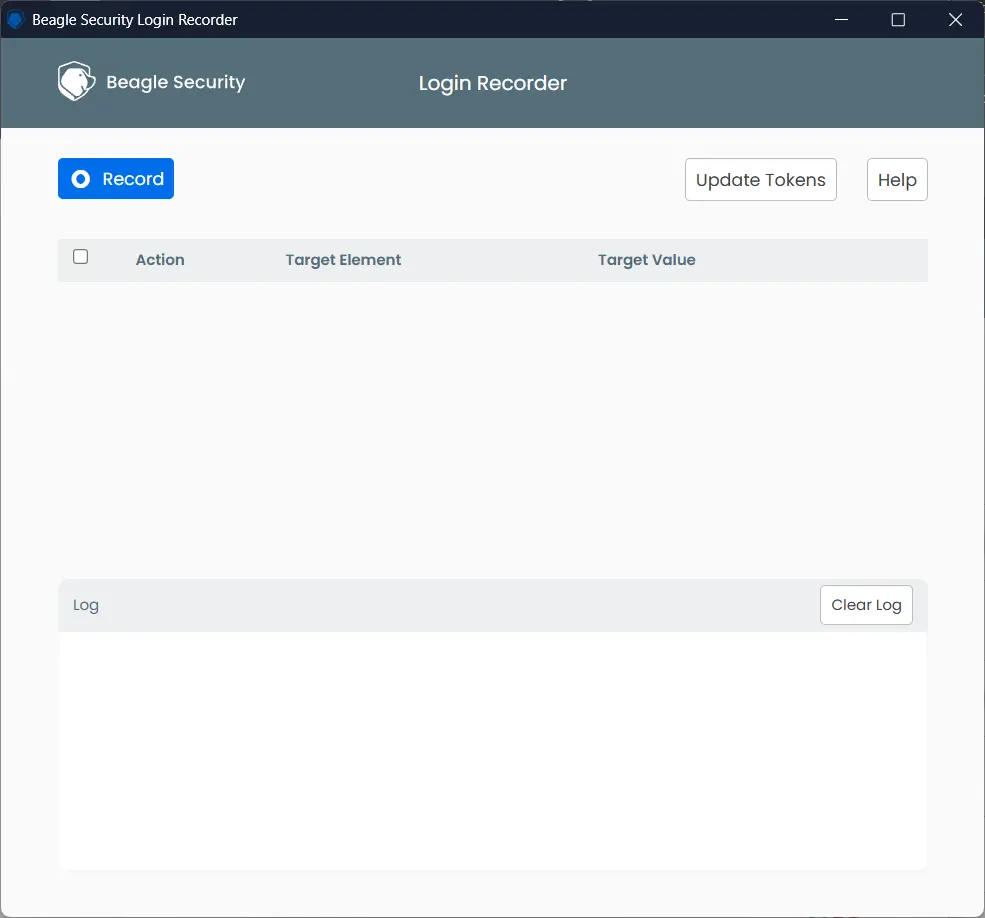
6. Complete login steps - Perform your normal login process with test credentials. All interactions are recorded automatically.
7. Stop recording - Once logged in, click Stop to finish.
8. Replay for verification - Use the Play option to confirm the sequence works as expected.
9. Integrate with Beagle Security - Submit the sequence to enable authenticated penetration testing.
Method 2: Login
This method allows you to directly provide static login credentials within Beagle Security. The system uses these details during tests.
Steps:
Navigate to your application configuration in Beagle Security.
Go to the Authentication section.
Select Login from the authentication options.
Enter the required fields such as username/email and password.
Save the configuration to apply the credentials for penetration testing.
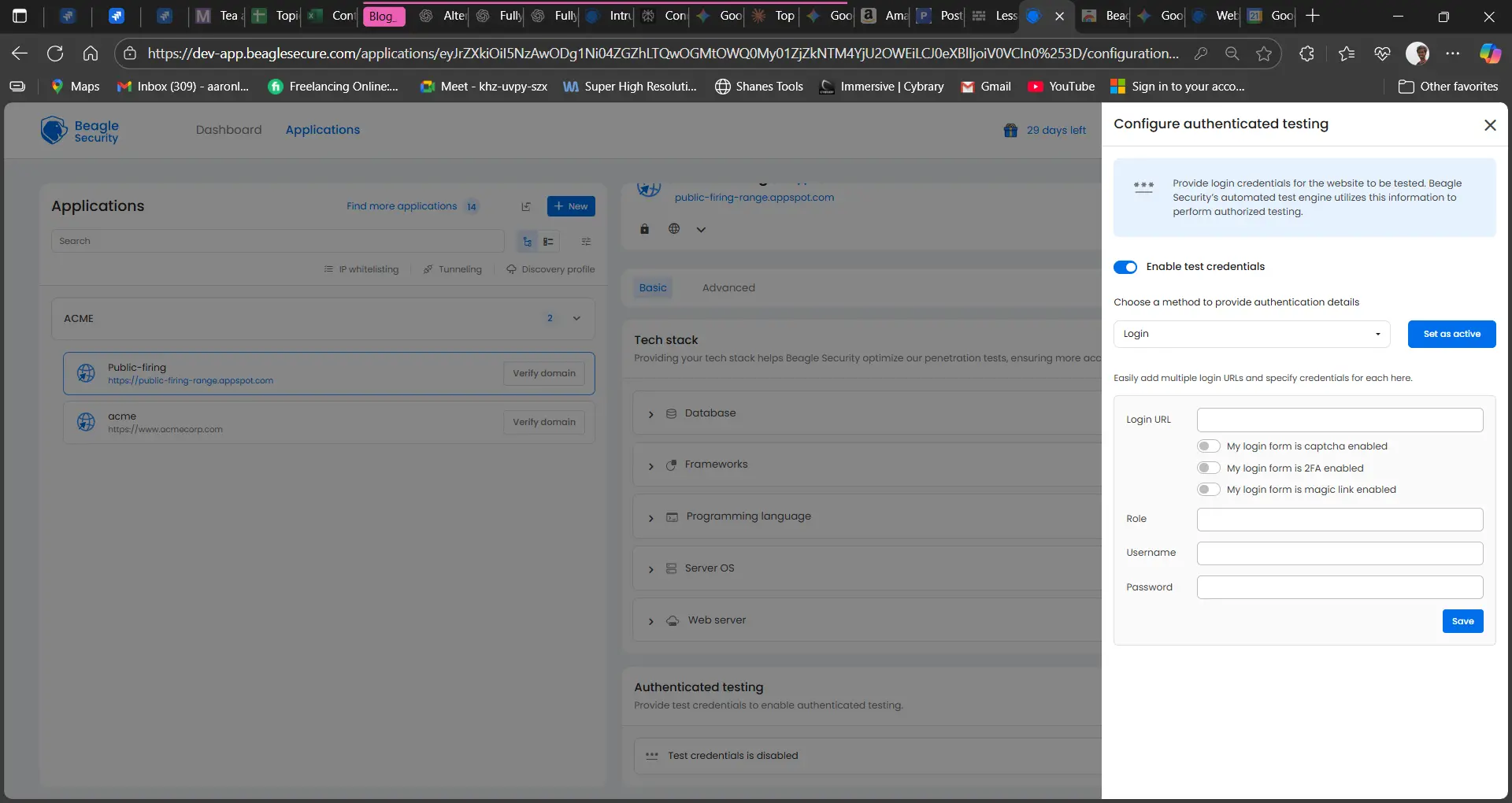
This method is simple but less flexible than recorded login, as it only works for straightforward login flows.
Method 3: Sign up
If your application requires a new account registration instead of static credentials, Beagle Security can simulate the sign-up process.
Steps:
Open the Authentication section in your project settings.
Choose Sign-Up as the authentication method.
Provide the sign up URL for the application.
Save the configuration.
Beagle Security will then use these details to automatically register a new test account during penetration testing.
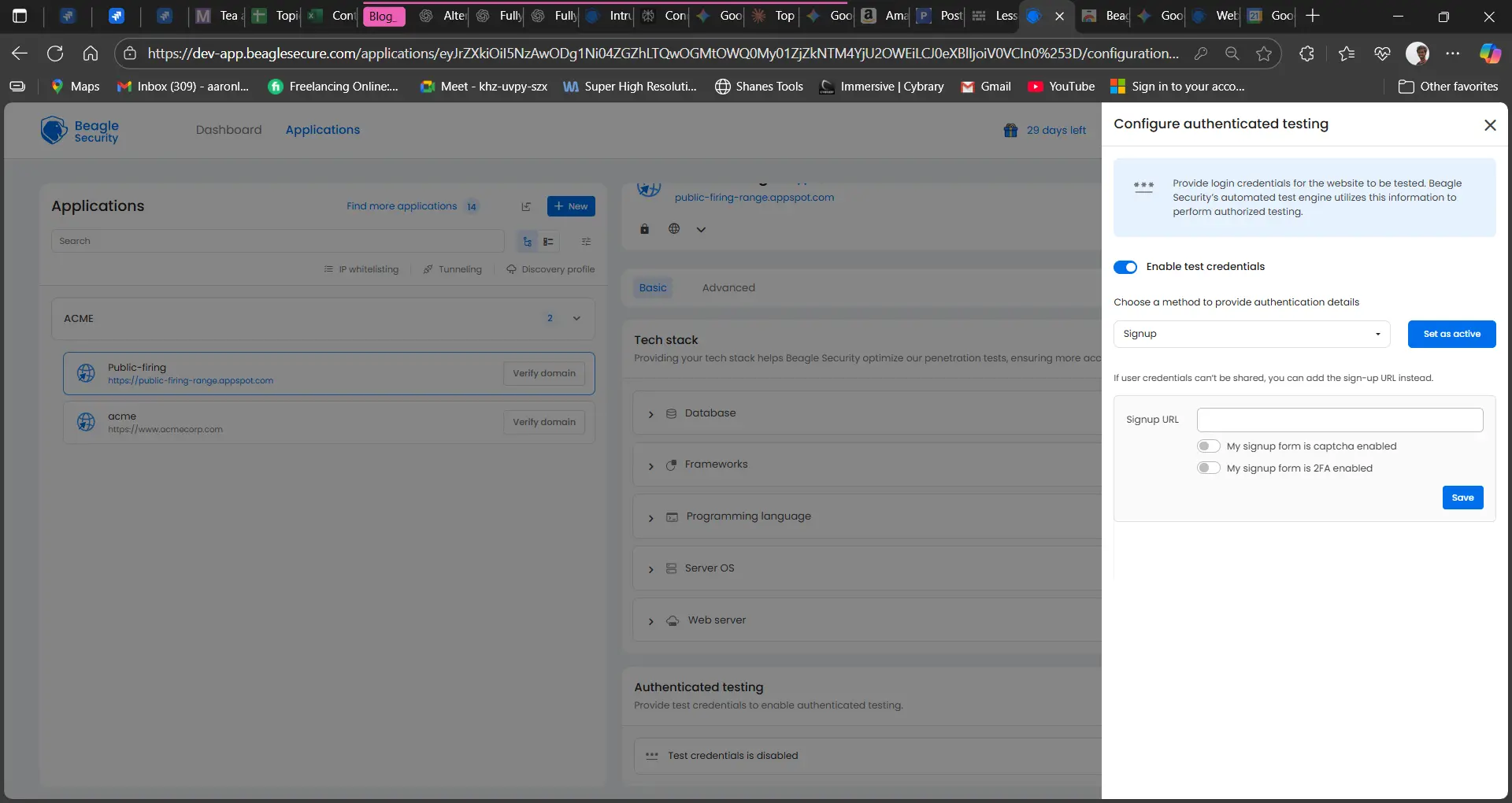
This is useful for applications where account creation is mandatory before login, such as SaaS trial platforms or e-commerce sites.
Method 4: Third-party login
For applications using third-party authentication providers (e.g., Google, GitHub, or Microsoft), Beagle Security supports configuring OAuth-based logins.
Steps:
In the Authentication panel, select Third-party login.
Provide the required client credentials or integration details for your chosen provider.
Configure the redirect URLs if necessary to ensure the test account can complete authentication.
Save and validate the setup.
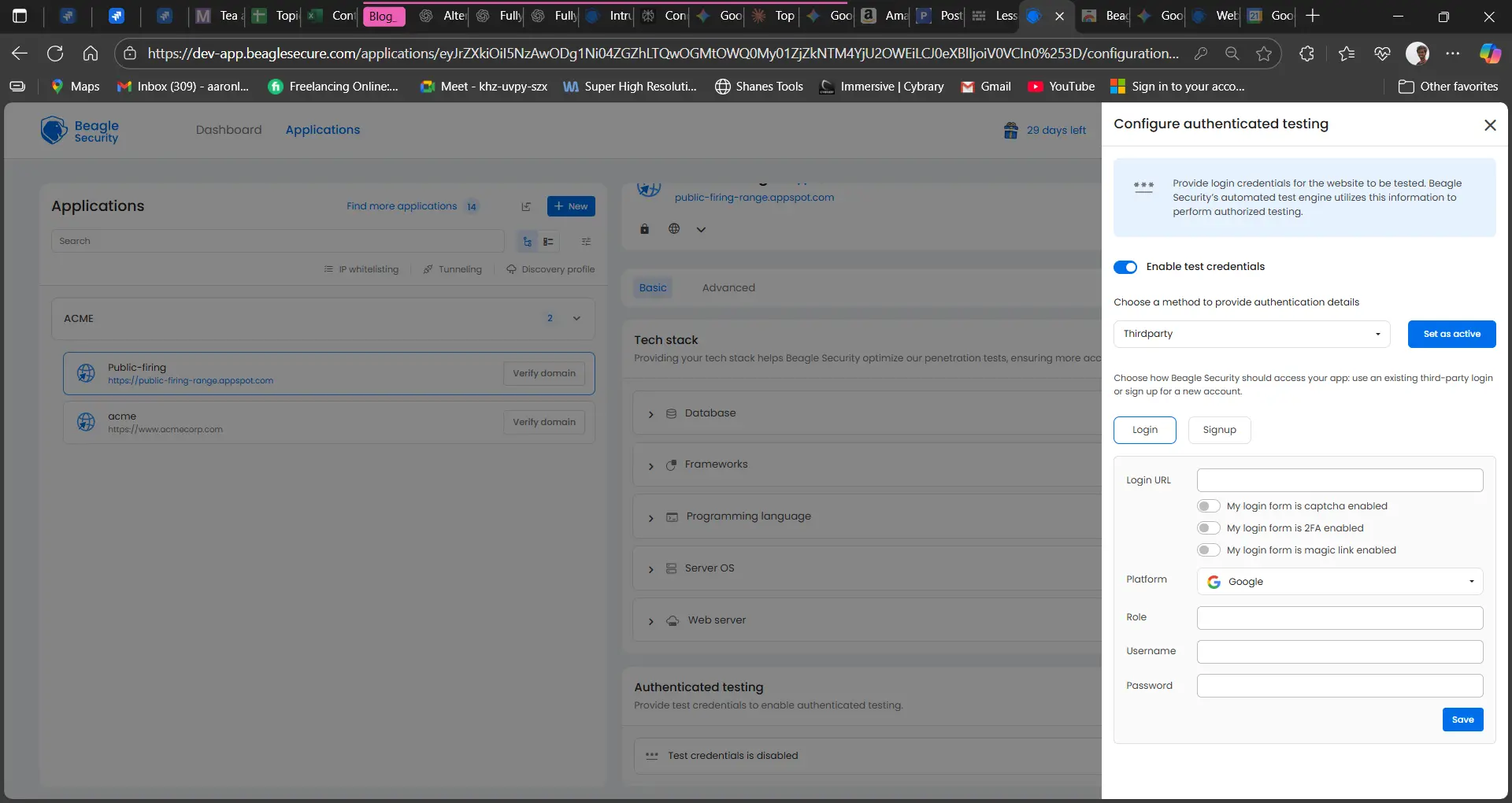
This allows Beagle Security to test authenticated areas even when access is managed through external identity providers.
Together, these four authentication methods give you flexibility to test any type of restricted workflow. For most scenarios, Recorded Login is the recommended choice because it captures complex login processes with accuracy.
Tech stack configuration
Configuring your tech stack in Beagle Security ensures the penetration test is tailored to the technologies powering your website. This enables the platform to run context-aware security checks, reducing false positives and uncovering vulnerabilities unique to your environment.
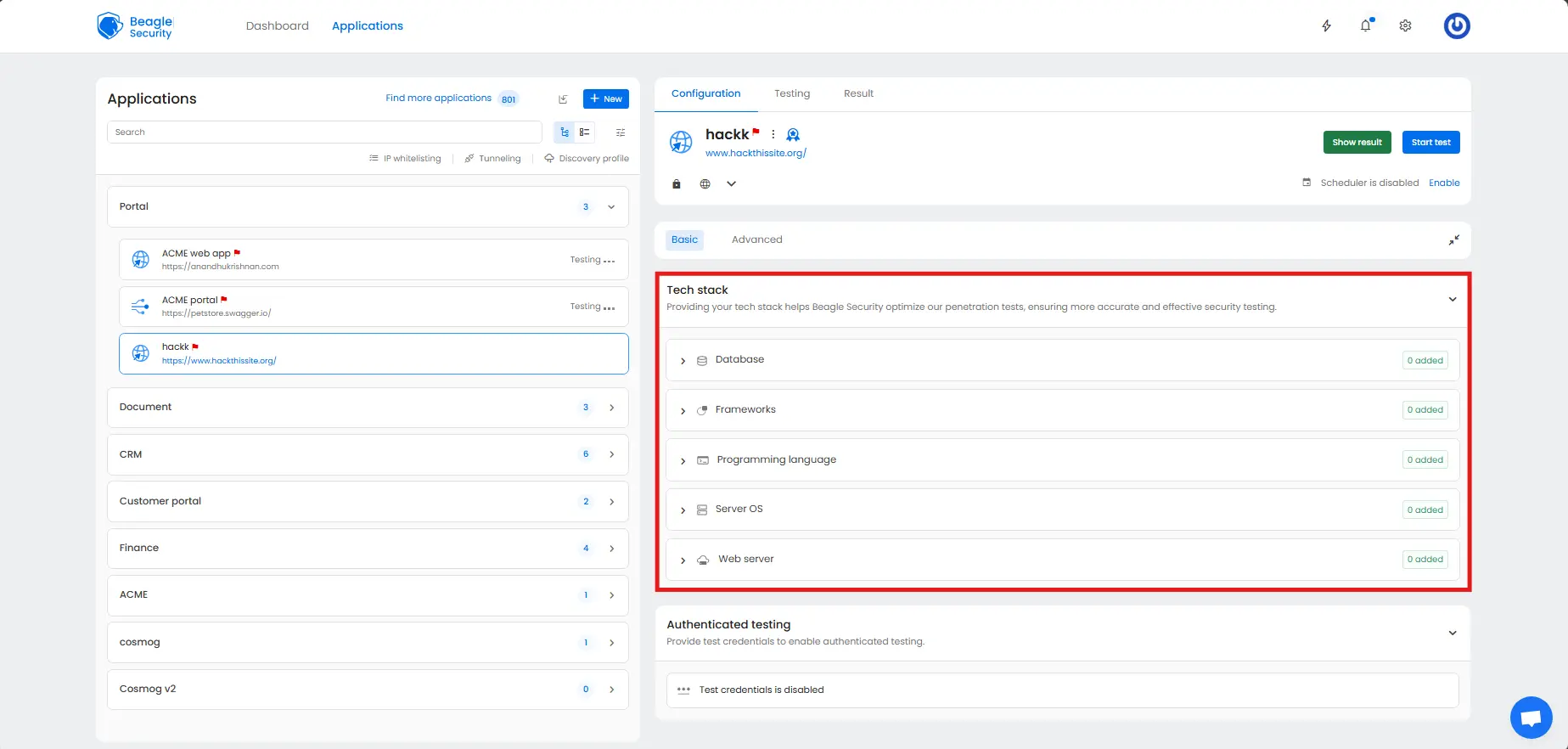
When setting up your application in Beagle Security, you can define your database, frameworks, programming language, server operating system, and web server. Each layer plays a role in shaping your security posture, and Beagle Security’s engine adapts its test cases accordingly.
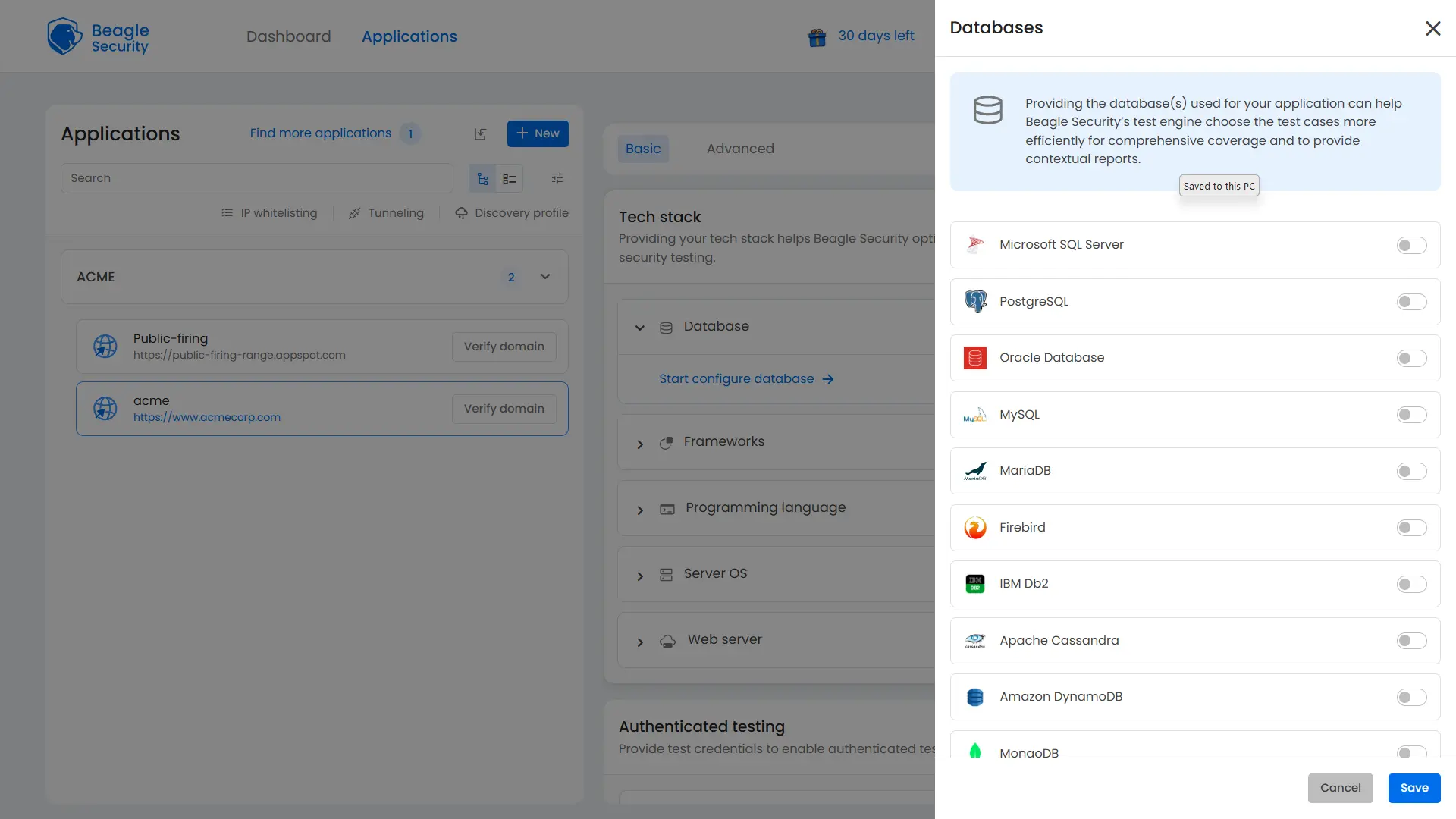
Business logic recording
Web applications often include complex workflows like shopping carts or multi-step forms. Business logic recording ensures these scenarios are tested accurately.
Steps:
Use the Beagle Sequence Recorder Chrome plugin.
From the dropdown, choose Scenario as the sequence type.
Go to your website and click Record in the extension to begin capturing your business logic sequence and continue to perform the workflow (e.g., add items to cart - checkout - payment).
Stop and review the recording.
Save it with a descriptive name (e.g., E-commerce Checkout Flow).
By capturing these workflows, you ensure penetration tests evaluate how attackers could manipulate logic flows, not just input fields.
Scope of test selection
Beagle Security automatically identifies and maps your application’s attack surface, but you can fine-tune the testing scope by identifying additional subdomains for the website and then including it in the testing scope.
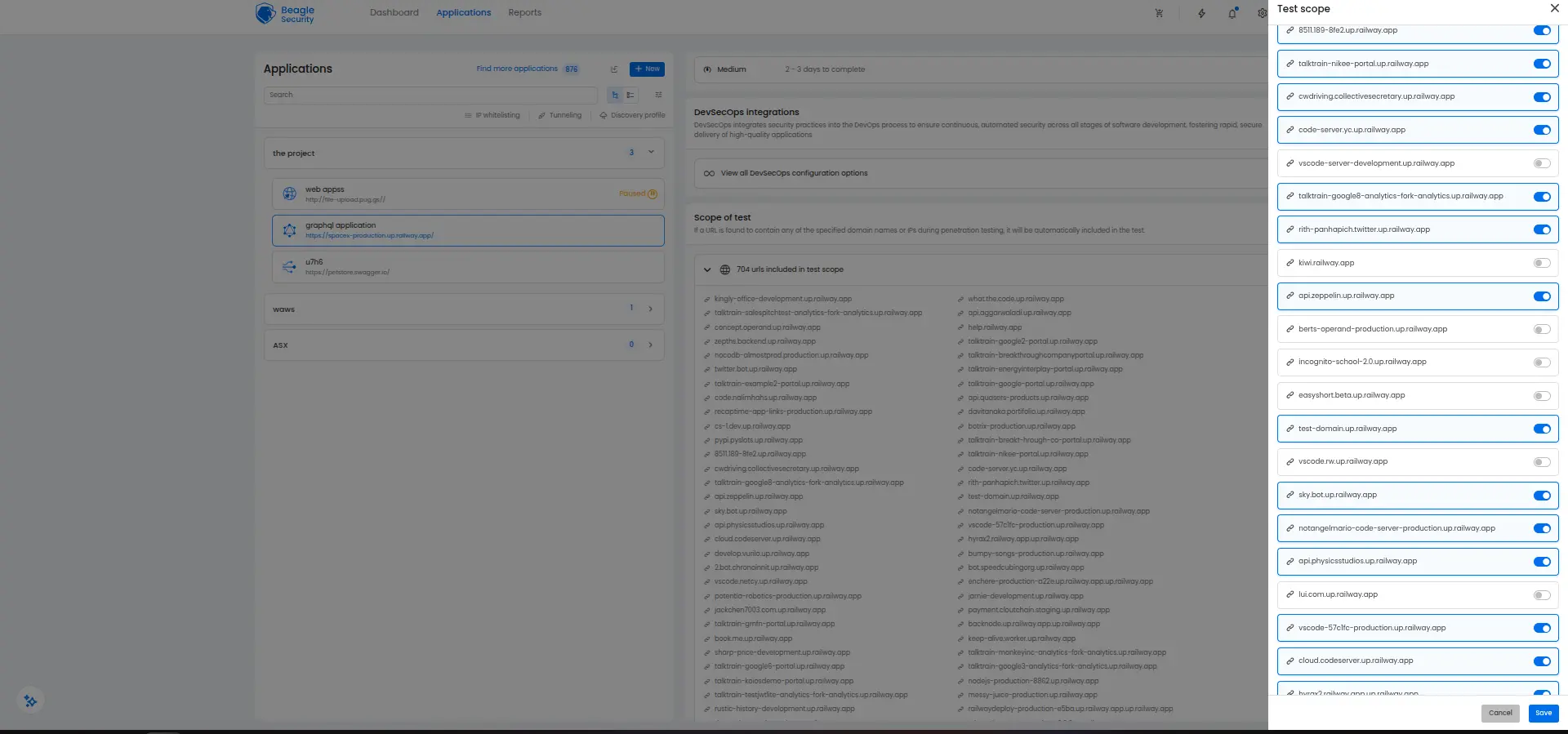
Viewing the penetration test results and reports
Beagle Security provides two primary reporting views: The application dashboard and the results dashboard.
Application dashboard
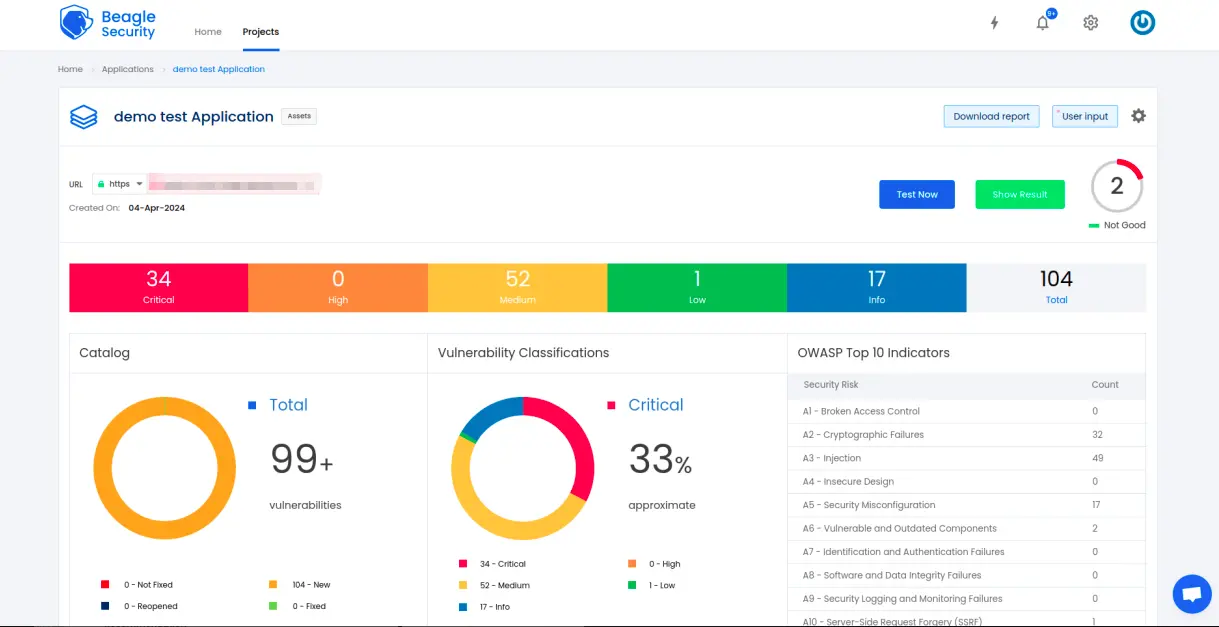
The application dashboard serves as your primary security command center, providing visibility into your website’s security posture.
This centralized view enables security teams, developers, and management to quickly assess current risk levels, track remediation progress, and make informed decisions about security priorities.
The dashboard consolidates complex security data into actionable insights, making it accessible for both technical and non-technical stakeholders.
Open vulnerabilities by severity
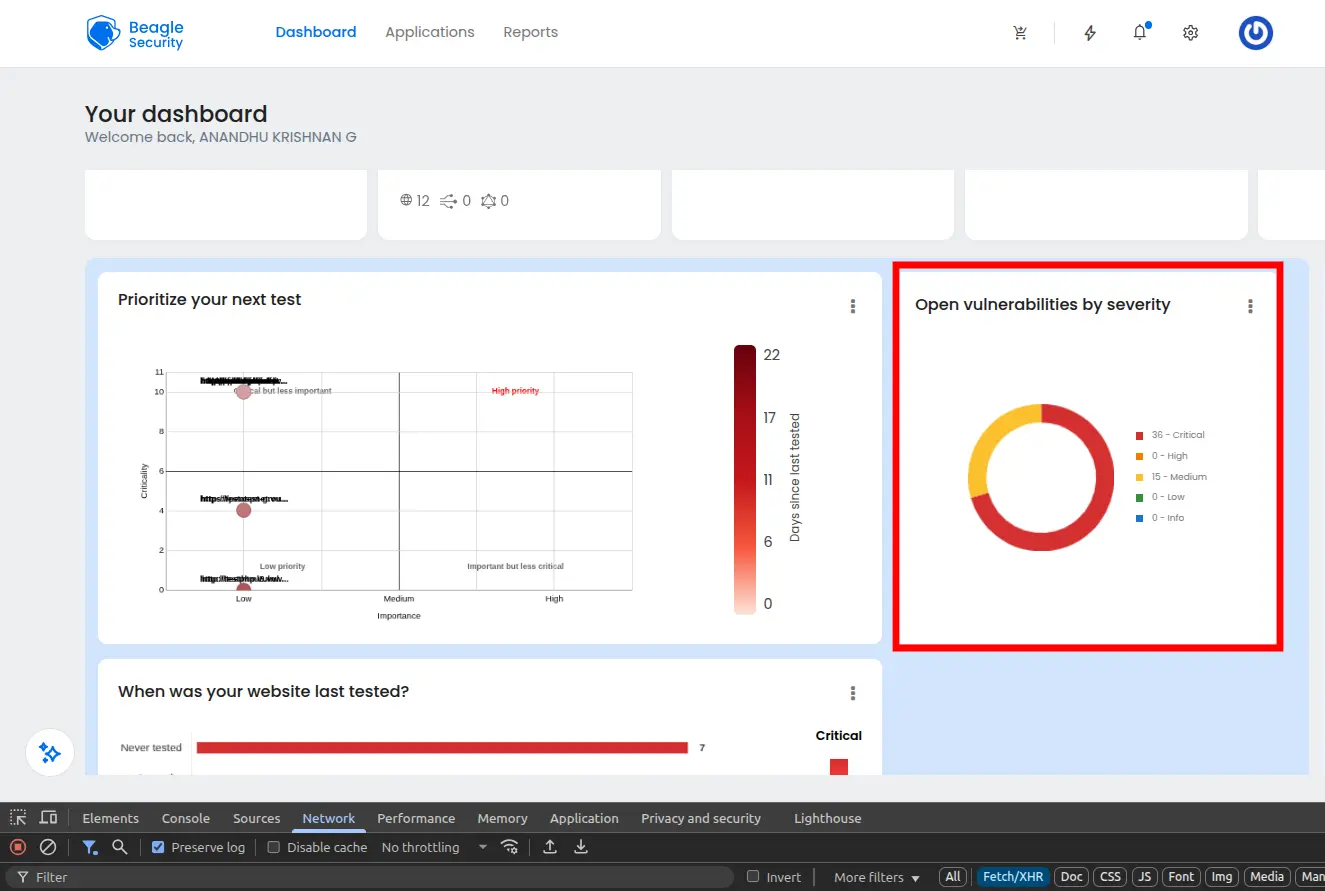
The severity-based vulnerability breakdown provides immediate risk prioritization through color-coded categories:
Critical vulnerabilities (red indicators) represent immediate threats requiring emergency remediation, such as SQL injection or remote code execution flaws that could lead to complete system compromise.
High vulnerabilities (orange indicators) are serious security issues that should be addressed within days, including authentication bypasses or sensitive data exposure risks.
Medium vulnerabilities (yellow indicators) represent moderate risks suitable for planned remediation cycles, such as cross-site scripting or information disclosure issues.
Low vulnerabilities (green indicators) are minor security concerns that can be addressed during regular maintenance cycles.
Informational findings (blue indicators) provide security awareness without immediate risk, such as version disclosures or security headers recommendations. This categorization enables teams to allocate resources effectively and address the most critical threats first.
Open vulnerabilities by age
The vulnerability age tracker provides crucial insight into your security debt and remediation effectiveness.
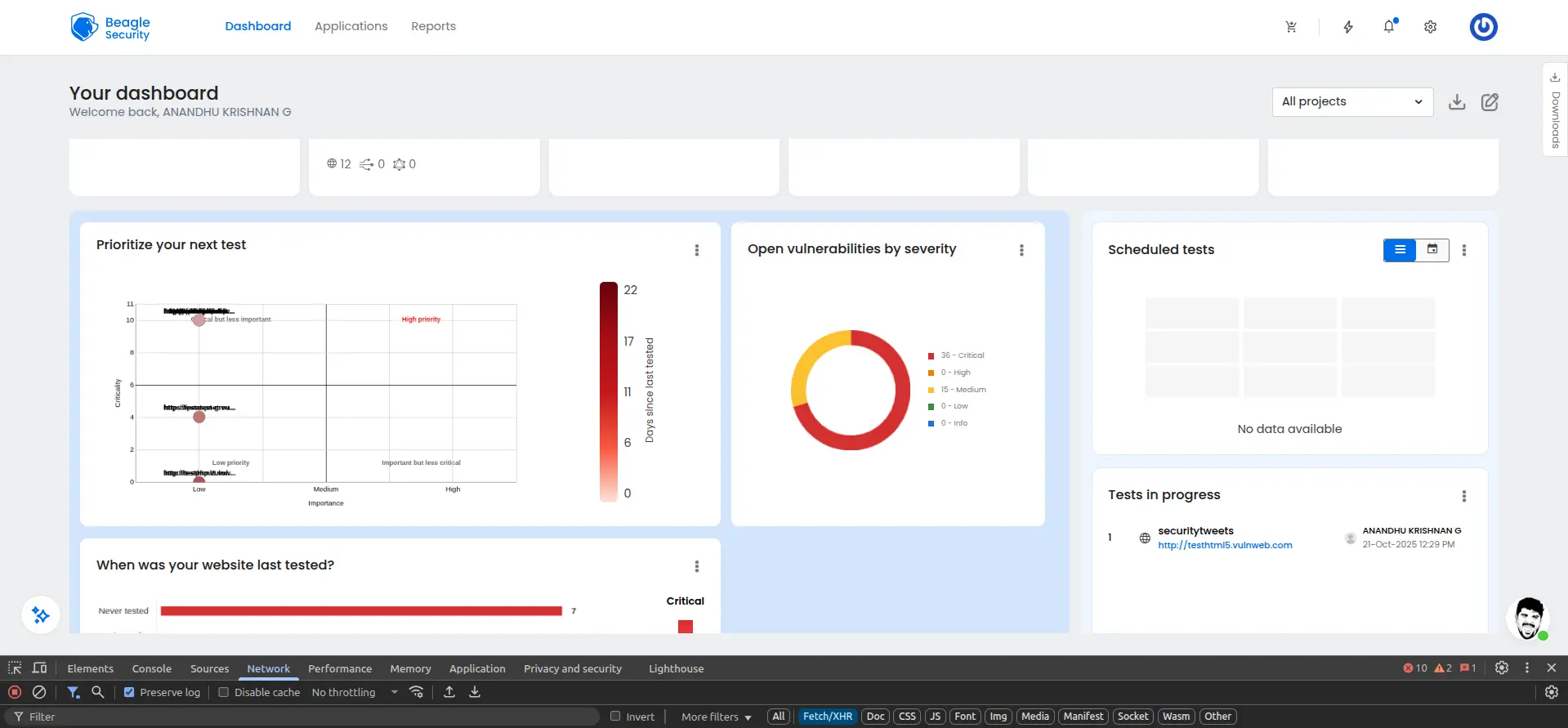
This age-based tracking helps security teams identify bottlenecks in their remediation process and demonstrate the impact of resource allocation decisions to management.
OWASP top 10 indicators
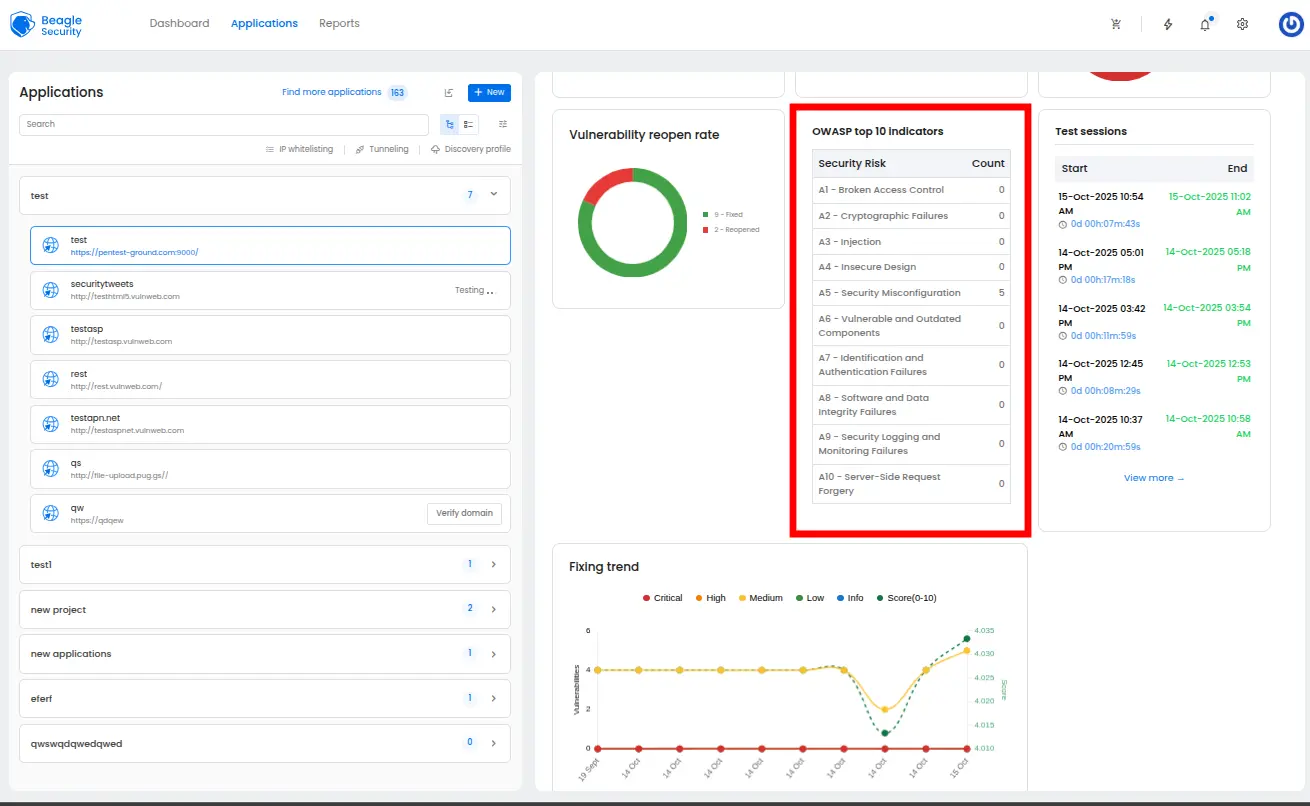
The OWASP Top 10 indicators provide standardized security risk assessment against the most critical web application security risks.
Each indicator shows current vulnerability counts and compliance status, enabling teams to understand their risk profile against globally recognized security standards.
Fixing trend
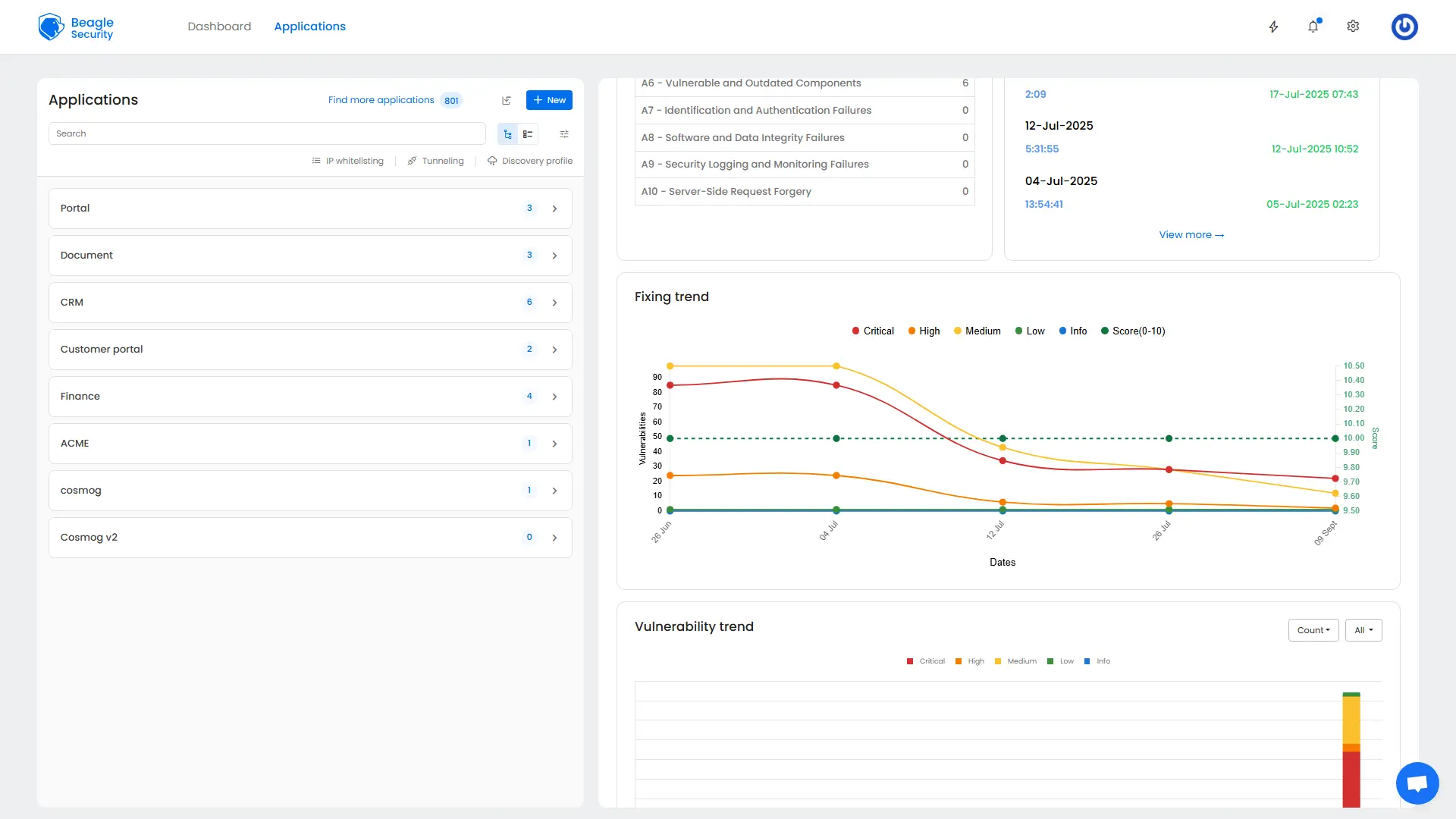
The fixing trend visualization tracks your organization’s remediation velocity over time, displaying key metrics:
Resolution rate shows the number of vulnerabilities fixed per time period, indicating team productivity and resource effectiveness.
This trending data enables security managers to demonstrate program effectiveness, justify resource requests, and identify periods requiring additional support or process changes.
Vulnerability trend
The vulnerability trend chart provides a historical analysis of security findings across multiple dimensions:
Monthly vulnerability discovery patterns help identify seasonal variations or correlation with development cycles.
Severity distribution changes over time show whether your application’s risk profile is improving or deteriorating.
Category-specific trends reveal whether certain vulnerability types are increasing, indicating potential training needs or architectural issues.
Result dashboard
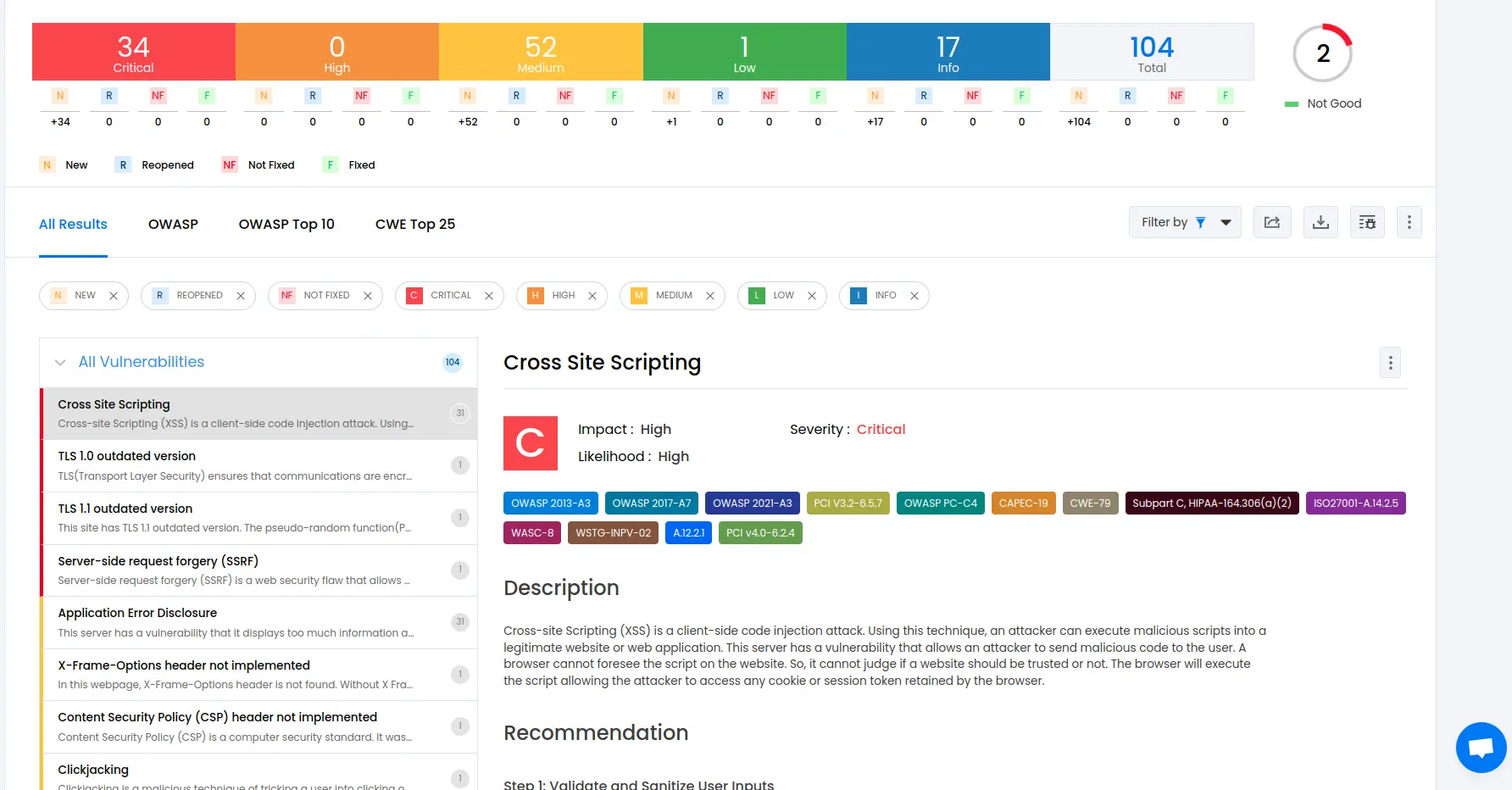
The results dashboard provides comprehensive technical analysis and compliance reporting capabilities, serving as the primary interface for security professionals conducting detailed vulnerability assessment and remediation planning.
This dashboard transforms raw security findings into actionable intelligence through standardized frameworks and detailed technical guidance.
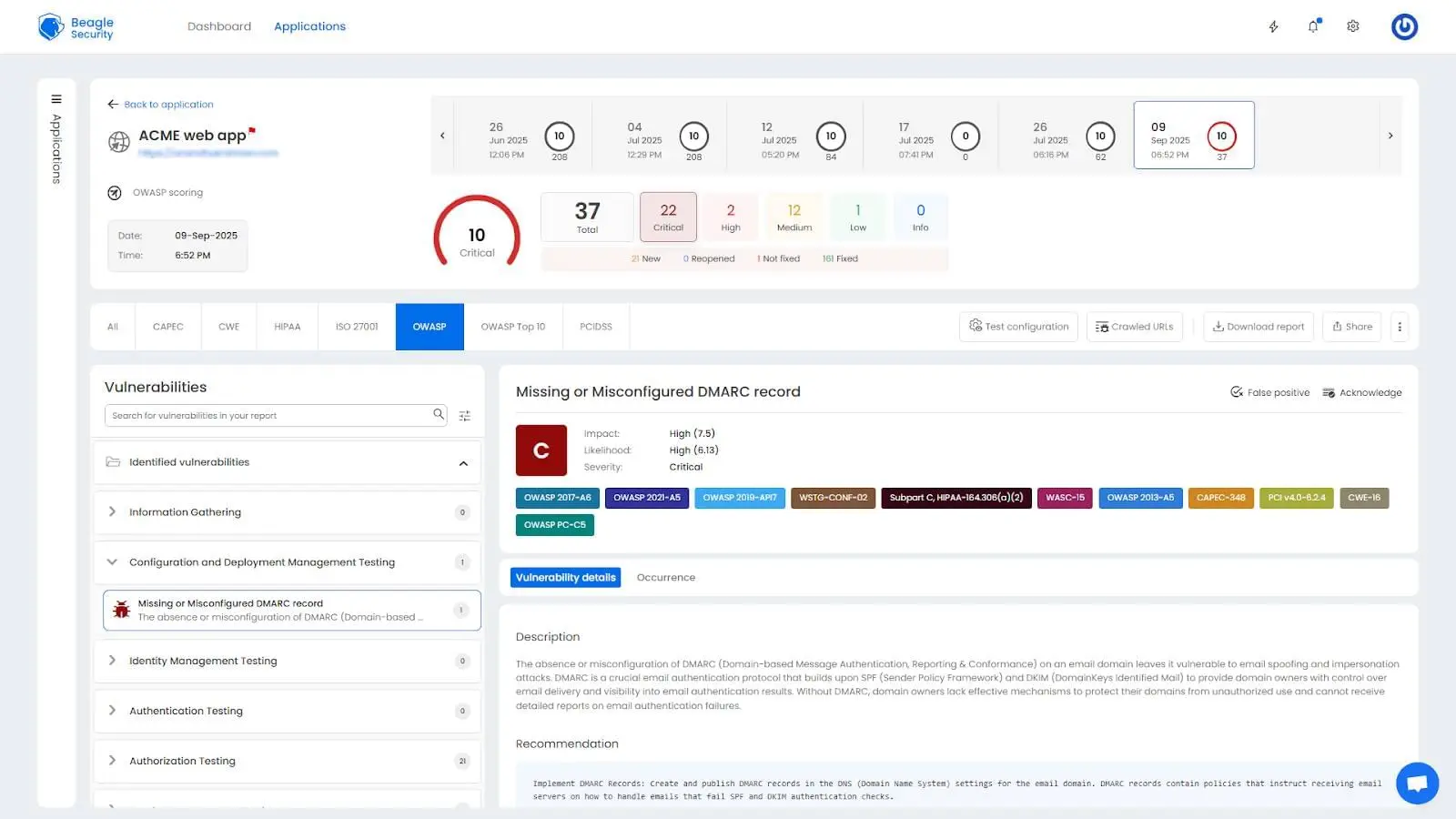
Mapping with ISO27001, OWASP & OWASP Top 10
The compliance mapping feature automatically aligns discovered vulnerabilities with multiple security frameworks:
ISO 27001 mapping correlates findings with specific information security management controls, enabling organizations to demonstrate compliance with international standards and identify control gaps requiring attention.
OWASP standard alignment maps vulnerabilities to the comprehensive OWASP Testing Guide methodology.
OWASP Top 10 correlation directly links findings to the most critical web application security risks, enabling teams to prioritize remediation based on globally recognized threat patterns and communicate risk in terms understood by security professionals worldwide.
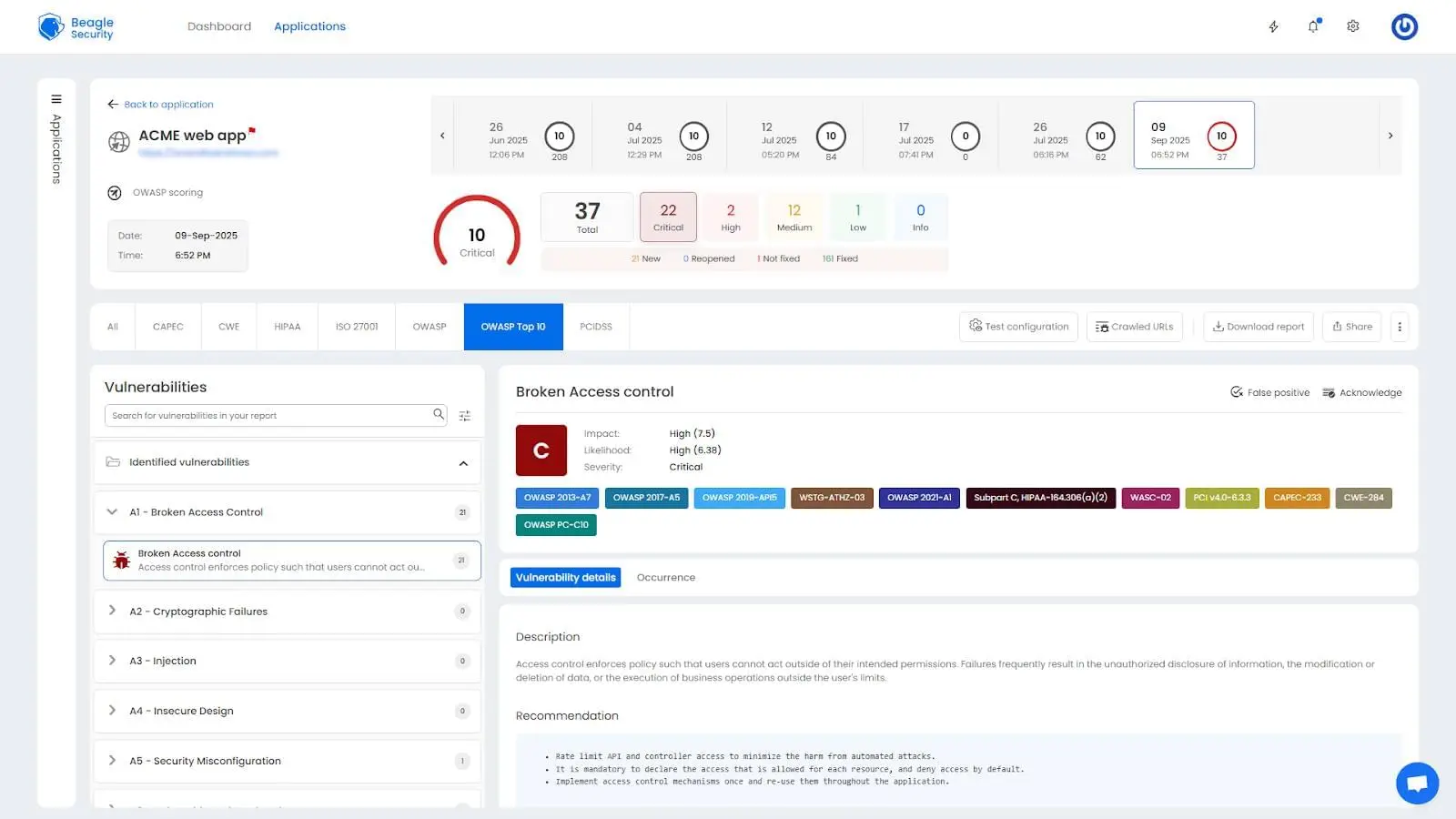
This multi-framework mapping ensures comprehensive compliance coverage and enables organizations to satisfy multiple audit requirements simultaneously.
Detailed findings, fix recommendations & occurrence details
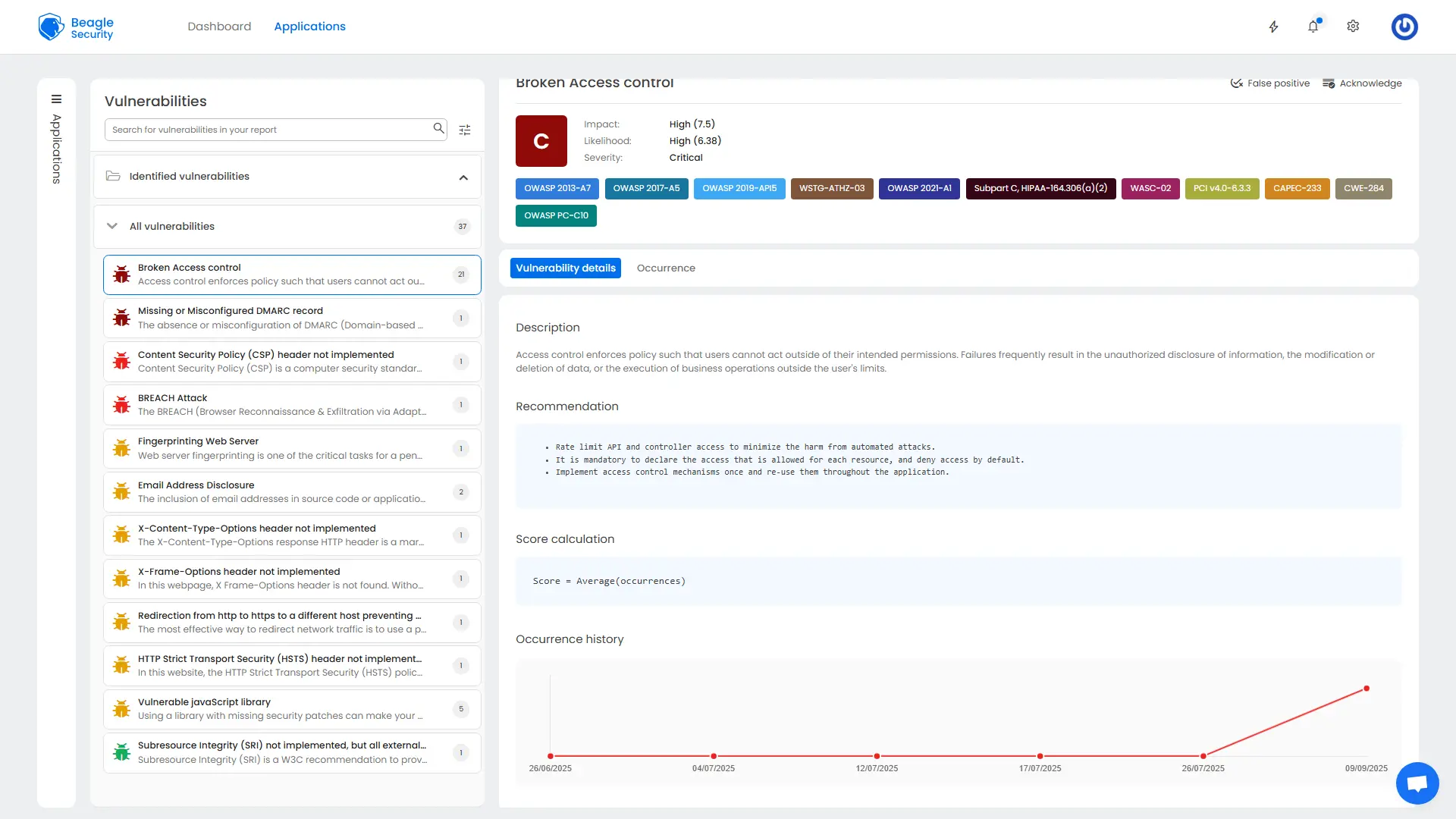
Each identified vulnerability provides comprehensive technical analysis including:
Vulnerability description explains the security issue in technical detail, including attack vectors and potential impact scenarios.
Risk assessment combines likelihood and impact ratings to provide business-relevant risk scoring.
Remediation guidance provides step-by-step fixing instructions, including code examples and configuration changes.
Occurrence details specify exact locations where vulnerabilities exist, including URLs, parameters, and request/response examples.
This detailed analysis enables developers to understand both the technical aspects and business implications of each security finding.
OWASP reports
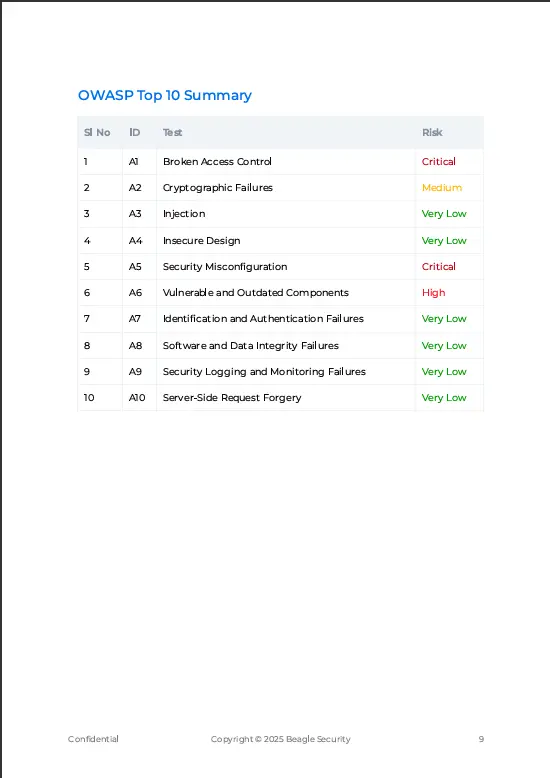
The OWASP reports organize findings according to the OWASP Testing Guide methodology:
Each category provides specialized remediation guidance tailored to the specific vulnerability type and testing methodology.
Compliance reports - HIPAA, PCI DSS
Specialized compliance reports address industry-specific security requirements:
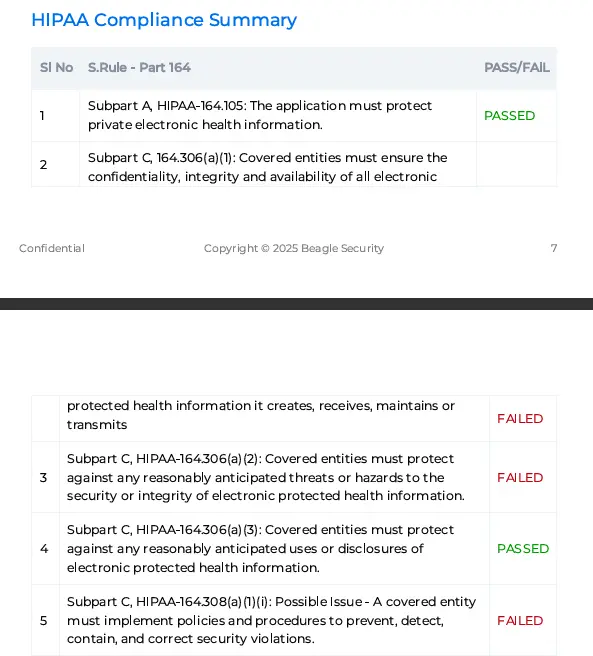
HIPAA compliance reporting maps vulnerabilities to specific HIPAA sub-rules requirements.
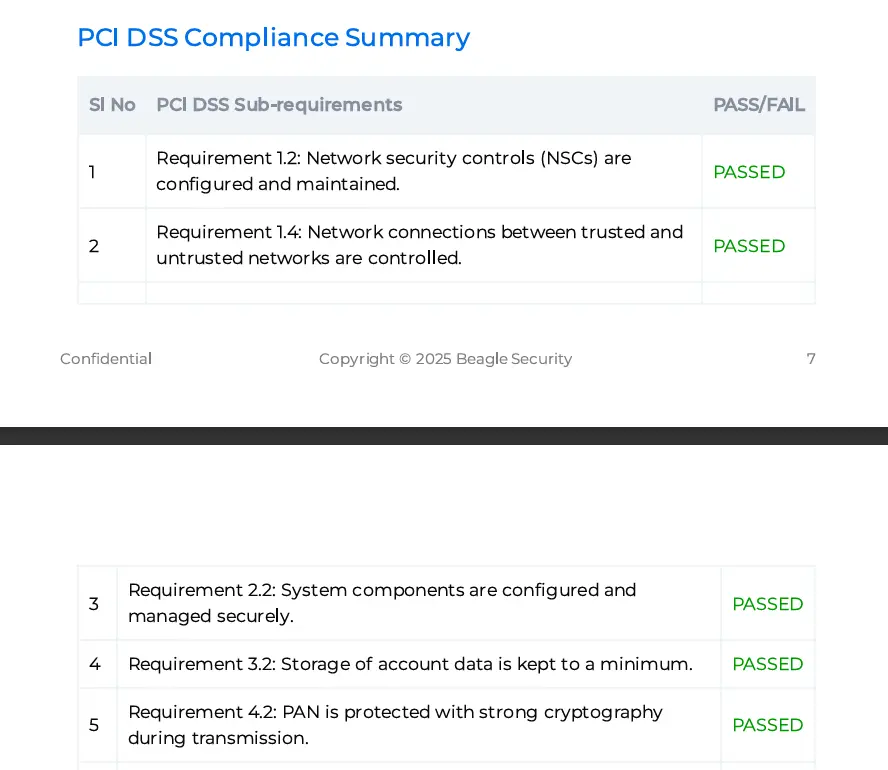
PCI DSS compliance reports align findings with PCI DSS sub-requirements.
These specialized reports enable organizations to demonstrate compliance readiness and identify specific remediation priorities for regulatory audit preparation.
Final thoughts
Website penetration testing isn’t about achieving perfect security, it’s about maintaining continuous visibility into your attack surface as your application evolves. Every new feature, API endpoint, or third-party integration creates potential entry points that automated scans miss and manual reviews can’t keep pace with.
The difference between effective and ineffective penetration testing comes down to integration. Running quarterly manual tests leaves your application exposed for months between assessments. Beagle Security’s approach enables testing on every significant change, catching vulnerabilities before they reach production rather than discovering them after breach attempts.
The organizations that avoid breaches aren’t the ones with zero vulnerabilities, they’re the ones that consistently identify and fix security issues faster than attackers can discover them. Start testing your application with Beagle Security’s platform to build that capability into your development workflow.
FAQ
1. How much does website penetration testing cost?
Website penetration testing cost depends on several factors: the size of your website, whether you use manual or automated testing, and the scope of testing required. Traditional manual penetration tests can cost anywhere from $5,000 to $50,000 per engagement and may take weeks to complete. Automated solutions like Beagle Security, however, provide continuous testing at a much lower cost, often starting at under $119 per month. This makes advanced penetration testing accessible for small businesses while still scaling to enterprise requirements.
2. How often should I perform penetration testing on my website?
The frequency depends on your industry and regulatory environment. At a minimum, organizations should run penetration tests twice a year. However, if your business handles sensitive data such as financial or healthcare information, quarterly testing is often required by compliance frameworks like PCI DSS and HIPAA. It is also best practice to run penetration tests after any major releases, system migration, or infrastructure change. Continuous automated penetration testing platforms like Beagle Security make this possible without overwhelming your development team.
3. How long does a typical website penetration test take?
The duration of a penetration test depends on the scope and method. Manual tests can take 2-6 weeks as security experts manually probe your application. Automated solutions like Beagle Security reduce this drastically, with many tests completing within a few hours to a couple of days. Larger applications with thousands of endpoints may take longer, especially if advanced configurations like business logic testing are included. However, because automated platforms can run continuously, you get near real-time vulnerability detection without waiting weeks for a final report.
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)