![Top AppCheck alternatives [2025] Top AppCheck alternatives [2025]](/blog/images/top-appcheck-alternatives.webp)
Application security continues to evolve as organizations ship software faster and expand digital footprints. AppCheck has gained popularity as a UK-based DAST platform, especially because it offers unlimited users and unlimited scanning. This makes it appealing for teams that need high-frequency testing across large portfolios.
However, unlimited scanning does not always equal the best value. Some teams do not actually use unlimited scan capacity. Others need better CI/CD integration, deeper API testing, or more modern detection methods. Cost structure also matters. Paying for unlimited usage can make sense for a portfolio of 100 applications, but it may not be ideal for organizations with 10 to 30 applications.
This guide compares AppCheck with ten strong alternatives. The list includes developer-focused DAST tools, enterprise security platforms, and traditional vulnerability scanners. The focus is on licensing models, scalability, cost efficiency, and real-world fit.
Best AppCheck alternatives at a glance
| Software | Pricing | Strengths | Best for |
|---|---|---|---|
| Beagle Security | Starting at $119 per month | AI accuracy, usage-based pricing | Teams needing efficient continuous pentesting |
| Veracode DAST | Custom enterprise pricing | Enterprise governance and compliance | Large regulated organizations |
| Checkmarx DAST | Custom pricing | Unified SAST and DAST in one platform | Enterprises building full AppSec programs |
| Tenable WAS | $7,434 per year for 5 FQDNs | Risk-based prioritization | Companies already using Tenable |
| Qualys WAS | Custom pricing | Integration with Qualys VMDR | Security teams standardizing on Qualys |
| Invicti | Custom pricing | Proof-based scanning for validated findings | AppSec teams requiring confirmation of vulnerabilities |
| Burp Suite Professional | $475 per user per year | Manual testing depth and researcher control | Security analysts and pentesters |
| Rapid7 InsightAppSec | $175 per application per month | Native integration with Rapid7 SIEM and SOAR | Organizations using Rapid7 Insight platform |
| Acunetix | Custom pricing | Wide vulnerability coverage and mature crawling | Traditional enterprise web security programs |
| Snyk DAST | Starts from $25/month; Free tier available | Developer-first workflows and platform alignment | Engineering teams already using Snyk products |
Best AppCheck alternatives in 2025
1. Beagle Security
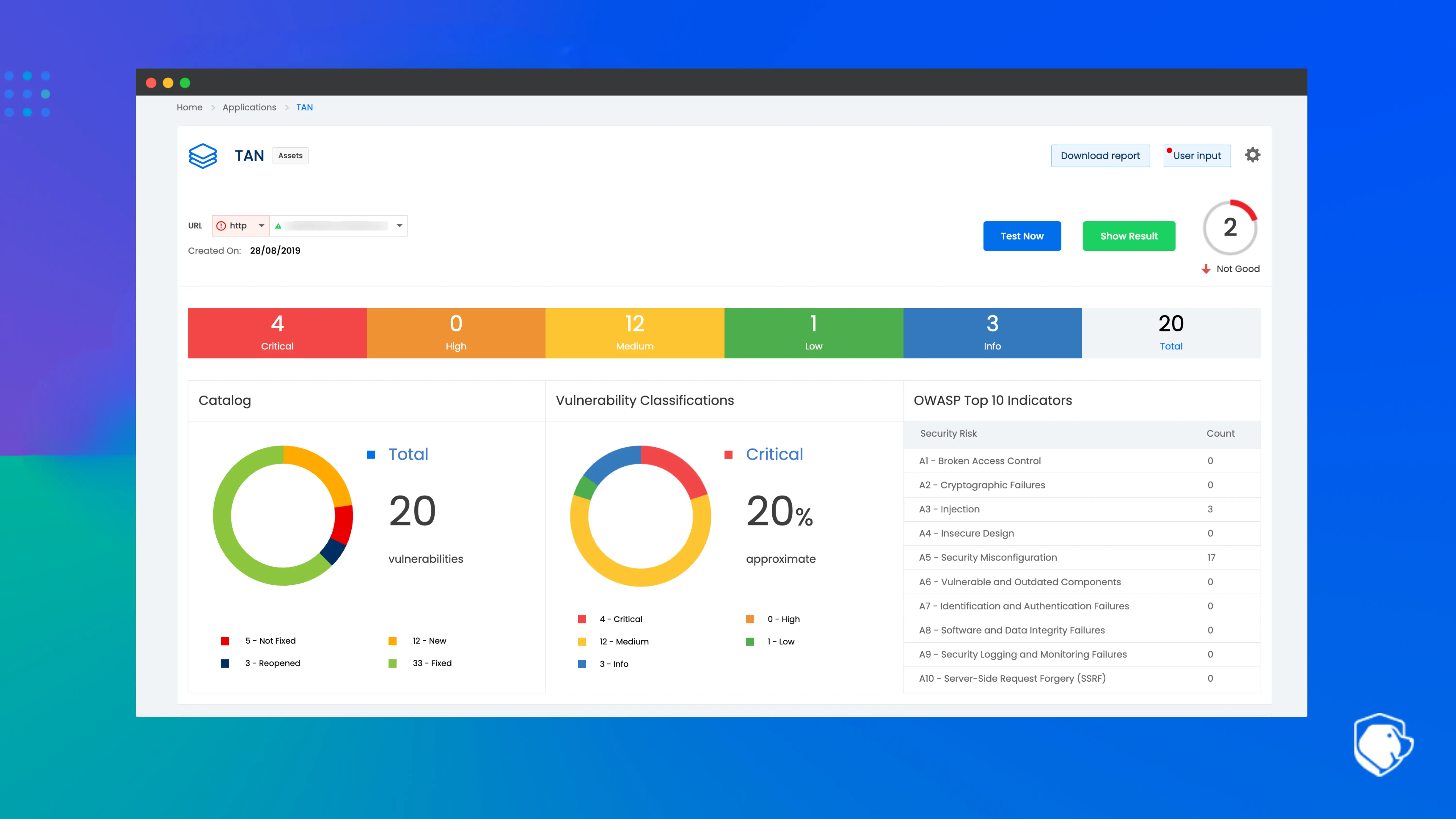
Beagle Security focuses on continuous, automated web application and API security testing with an emphasis on developer adoption. It uses AI-based analysis to reduce false positives and produce clear remediation guidance. The platform is designed to fit into modern CI/CD pipelines and works well for teams who want repeatable testing without manual overhead.
Beagle Security provides a usage-based pricing model, which can be more cost-efficient than AppCheck’s unlimited license for organizations with smaller application portfolios. Teams only pay for what they use, which avoids unused scan capacity. The platform integrates with environments where releases are frequent and testing needs to be automated.
The tool is well suited for product engineering teams, DevSecOps environments, and growing SaaS companies that want scalable testing without large enterprise contract lock-in.
Key features:
AI-driven detection with reduced false positives
Business logic vulnerability testing
Web application and API security testing support
CI/CD integrations with GitHub, GitLab, Bitbucket, Jenkins, Azure DevOps
Detailed remediation guidance designed for developers
Pricing:
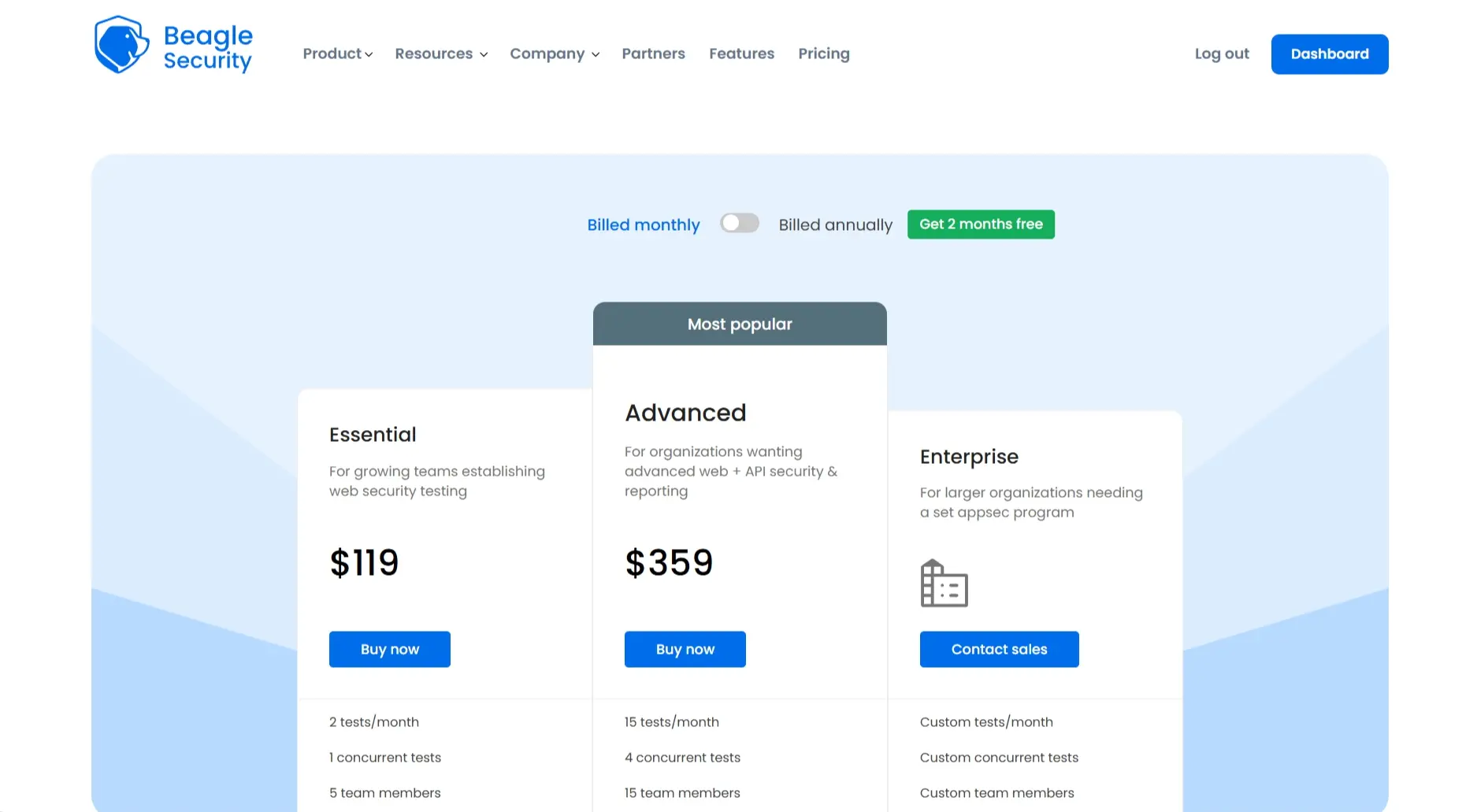
Starts at $119 per month
Usage-based plans scale with application and testing frequency
No long-term enterprise contract required
Ratings and reviews:
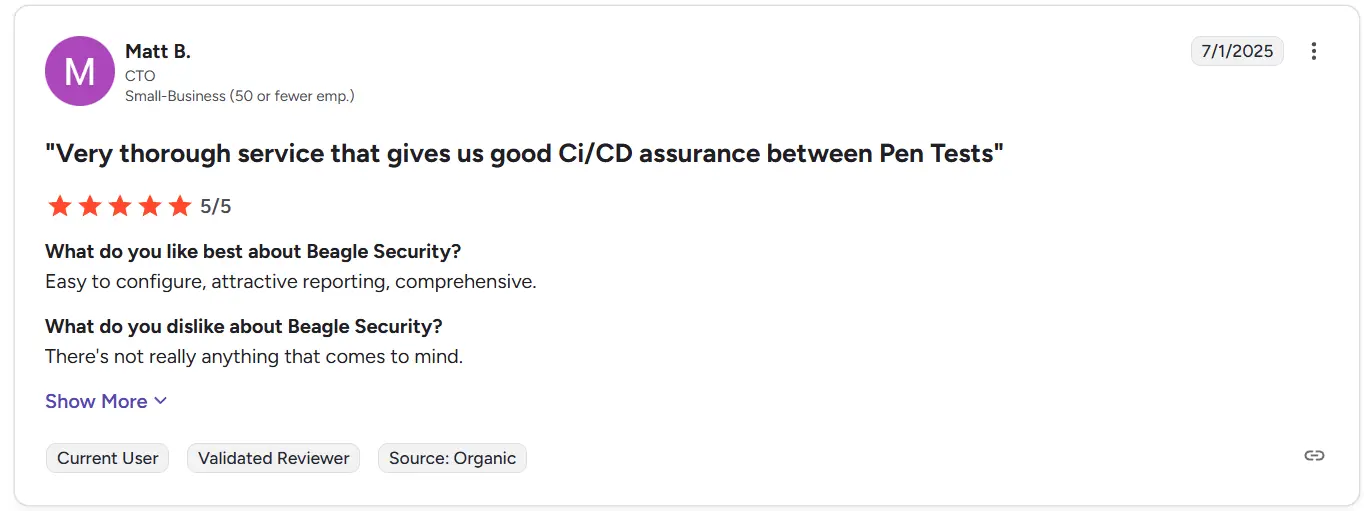
Beagle Security has a 4.7 out of 5 rating on G2. Reviewers highlight accuracy, ease of onboarding, and helpful developer-focused reporting. Teams appreciate the clarity of findings and ability to integrate scans into pipelines.
2. Veracode DAST
Veracode DAST is part of the larger Veracode application security platform, which also includes SAST, SCA, and developer education. It is commonly selected by enterprises with strict compliance requirements and complex governance workflows. The platform emphasizes centralized reporting and policy management.
Veracode’s DAST solution works best in organizations that already use multiple Veracode modules or need strong audit trails. However, onboarding and administration can be more complex than lighter developer-focused tools.
Key features:
Enterprise governance and compliance workflows
Integration with Veracode SAST and SCA
Policy-based vulnerability reporting and control
Portfolio-wide risk dashboards
Pricing:
Custom enterprise pricing
Typically billed by the number of applications
Ratings and reviews:
Veracode holds a 4.2 out of 5 rating on G2. Users value centralized management and long-term enterprise support. Some mention longer onboarding cycles and higher pricing compared to newer DAST platforms.
3. Checkmarx DAST
Checkmarx DAST sits within the Checkmarx One platform, which unifies SAST, DAST, SCA, and IaC scanning. The tool emphasizes developer workflows and unified security under a single platform. Teams that want one vendor for full AppSec program governance often choose Checkmarx.
Checkmarx DAST is strong in organizations practicing shift-left security. It encourages early detection through CI pipeline integration rather than post-deployment scanning. Licensing can be expensive, making it better suited for larger environments.
Key features:
Unified AppSec platform with SAST, DAST, and SCA
CI/CD focused scanning controls
Policy-driven governance for enterprise environments
Consistent developer reporting across tools
Pricing:
Custom enterprise pricing
Usually licensed as part of Checkmarx One platform bundles
Ratings and reviews:
G2 rating averages around 4.2 out of 5. Reviewers praise integrated workflows and platform management. Some note that setup and configuration require dedicated AppSec engineering support.
4. Tenable WAS
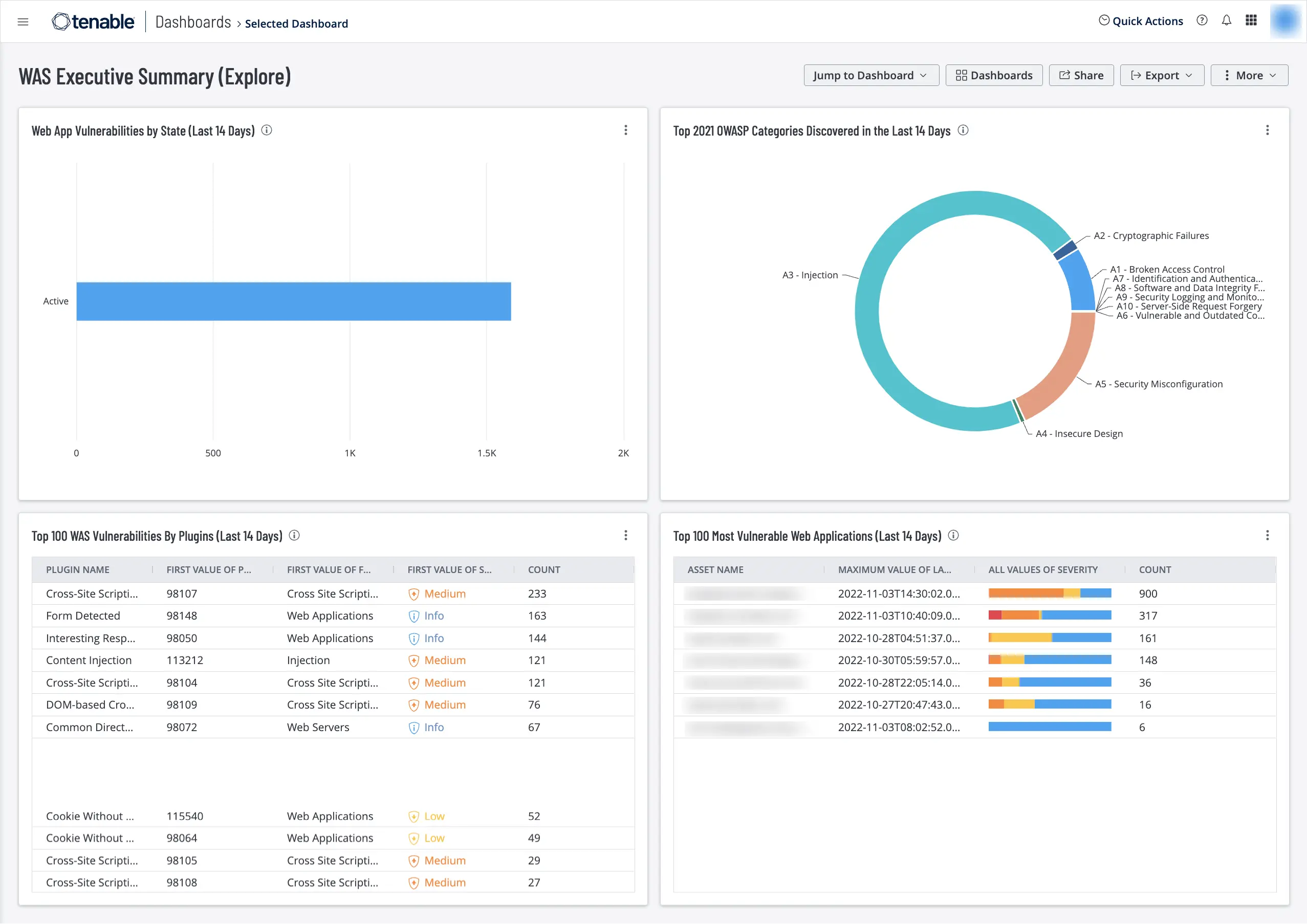
Tenable WAS focuses on risk-based web application scanning supported by Tenable’s Vulnerability Priority Rating system. Organizations already using Tenable for network and cloud vulnerability management often add WAS for unified reporting.
This tool is well suited for environments that prioritize centralized vulnerability visibility across assets.
Key features:
Risk-based vulnerability scoring
Unified reporting with Tenable.io
Automated web application scanning
Asset inventory and exposure tracking
Pricing:
Pricing starts at $7,434 per year for 5 FQDNs
Additional targets priced per domain
Ratings and reviews:
G2 rating is around 4.5 out of 5. Customers appreciate consolidated risk dashboards. Some mention limited modern application coverage compared to dedicated DAST platforms.
5. Qualys WAS
Qualys WAS extends Qualys’ vulnerability management platform into web application scanning. It is typically used by organizations already invested in the Qualys ecosystem. The platform offers strong scanning automation but may require security teams to interpret and triage findings for developers.
Key features:
Integration with Qualys VMDR
Automated scanning workflows
Policy-driven reporting
Cloud-based asset inventory and dashboards
Pricing:
- Custom pricing per application or asset tier
Ratings and reviews:
Qualys WAS holds a 4.5 out of 5 rating on G2. Reviewers highlight reliable scanning and reporting. Developer usability is sometimes cited as an area for improvement.
6. Invicti
Invicti provides proof-based scanning that verifies vulnerabilities through safe exploitation techniques. This reduces false positives and helps security teams prioritize confirmed issues. The platform is suited for organizations that want validated findings before assigning developer remediation work.
Invicti is positioned for mid-sized to large enterprises managing multiple web applications and requiring strong vulnerability accuracy.
Key features:
Proof-based vulnerability verification
Wide scanning coverage across frameworks
Workflow automation and ticketing integration
Support for on-prem or cloud deployments
Pricing:
Custom pricing based on application portfolio size
Enterprise contracts typically required
Ratings and reviews:
Invicti is rated around 4.7 out of 5 on G2. Users value the accuracy of confirmed findings. Some note that pricing can be high for smaller organizations.
7. Burp Suite Professional
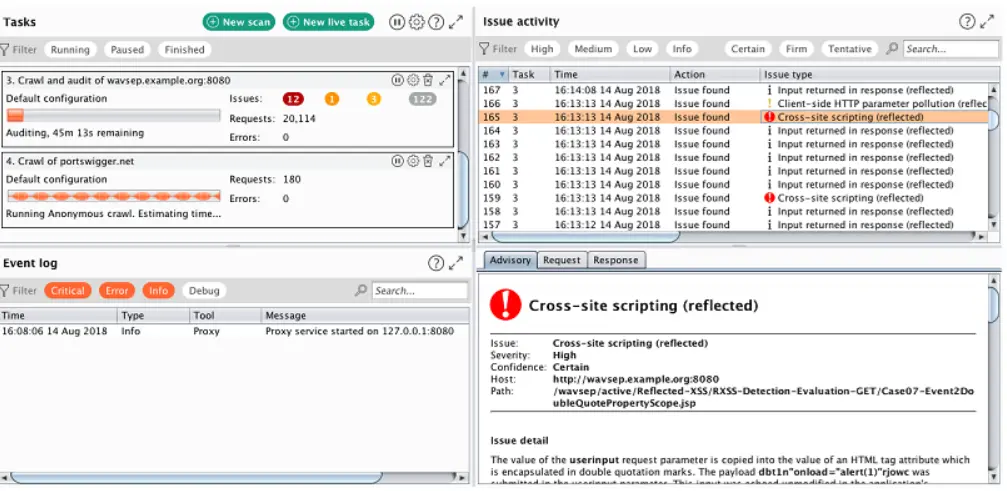
Burp Suite Professional is the standard toolkit for manual web application penetration testing. It offers full control to security testers and provides advanced capabilities to dig into complex vulnerabilities. The tool is ideal for hands-on security research.
Key features:
Manual scanning and testing tools
Extensibility with plugins
Interception proxy and request manipulation
Repeatable testing frameworks
Pricing:
- Free community edition available
- $475 per user per year
Ratings and reviews:
Burp Suite holds a 4.8 out of 5 rating on G2. Reviewers emphasize flexibility and depth. It requires human expertise and is not intended as a continuous automated scanning solution.
8. Rapid7 InsightAppSec
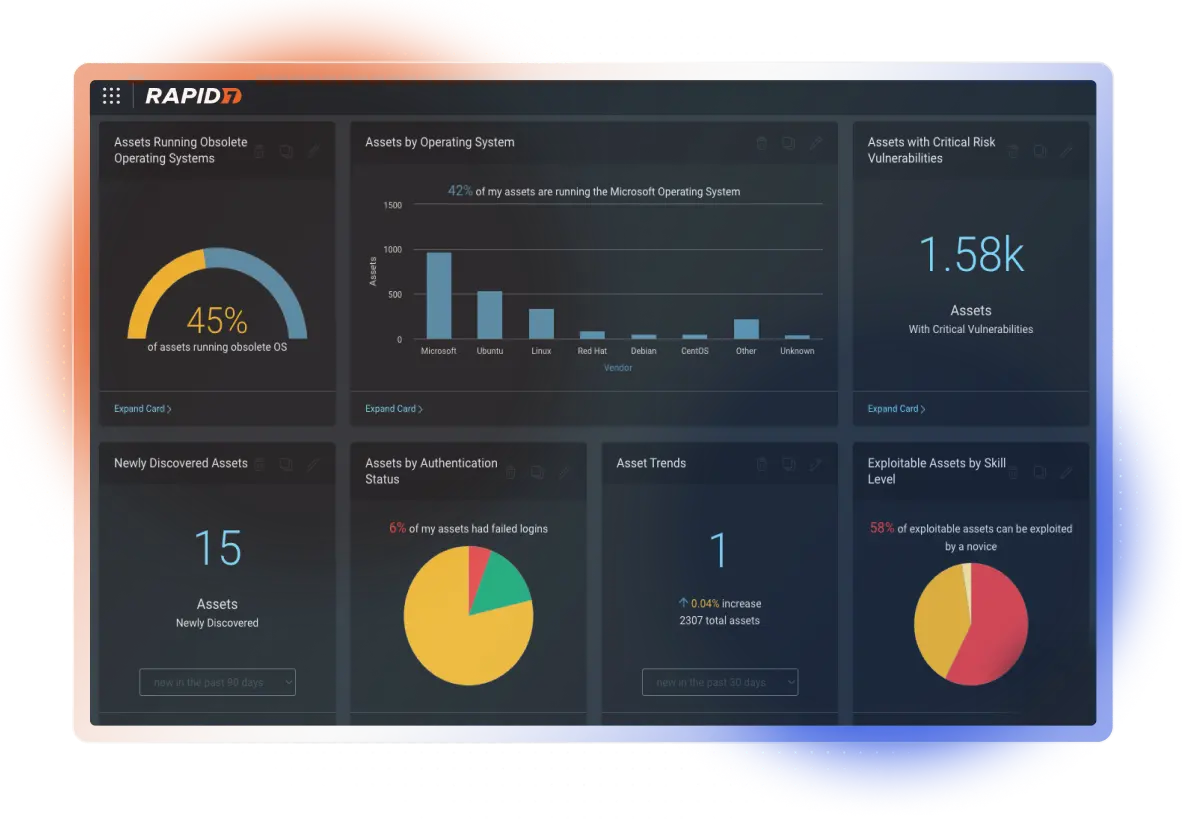
Rapid7 InsightAppSec integrates into the Rapid7 Insight cloud platform, providing scanning and remediation workflows alongside detection and response capabilities. The platform emphasizes policy automation and reporting.
Key features:
Integration with Rapid7 Insight IDR and SIEM
Automated scanning and dashboards
Attack replay features for validation
CI/CD support
Pricing:
- Starts at around $175 per application per month
Ratings and reviews:
G2 rating averages 4.3 out of 5. Users value platform consolidation benefits. Some note that scanning coverage can vary depending on application complexity.
9. Acunetix
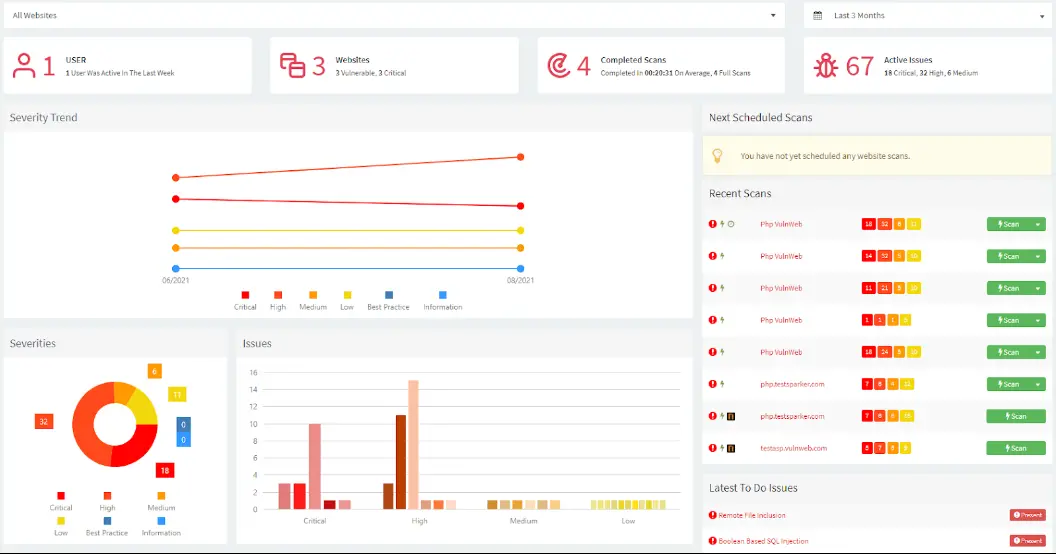
Acunetix has been a recognized DAST tool for many years, offering strong vulnerability detection and stable crawling capabilities. It is commonly used in traditional enterprise security setups and consulting environments.
Key features:
Advanced crawler for dynamic web applications
Coverage including OWASP Top 10 and known CVEs
Support for authenticated and unauthenticated scans
Hybrid deployment options
Pricing:
Custom pricing based on number of targets
Typical entry pricing starts around $4,500 per year
Ratings and reviews:
Acunetix maintains a 4.1 out of 5 on G2. Reviewers highlight scanning reliability but mention that modern microservices and API-heavy applications sometimes require additional configuration.
10. Snyk DAST
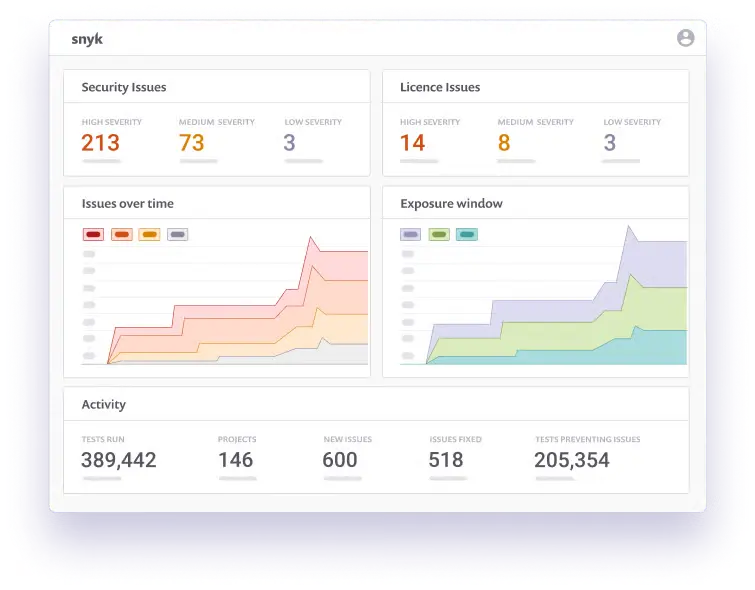
Snyk DAST extends the Snyk security ecosystem to dynamic testing. It integrates closely with developer workflows and centralizes reporting with Snyk SAST and SCA findings. The focus is on enabling engineers to fix issues early.
Key features:
Developer-first workflows
Unified platform reporting with Snyk tools
Git repository and CI pipeline integration
Policy governance and access controls
Pricing:
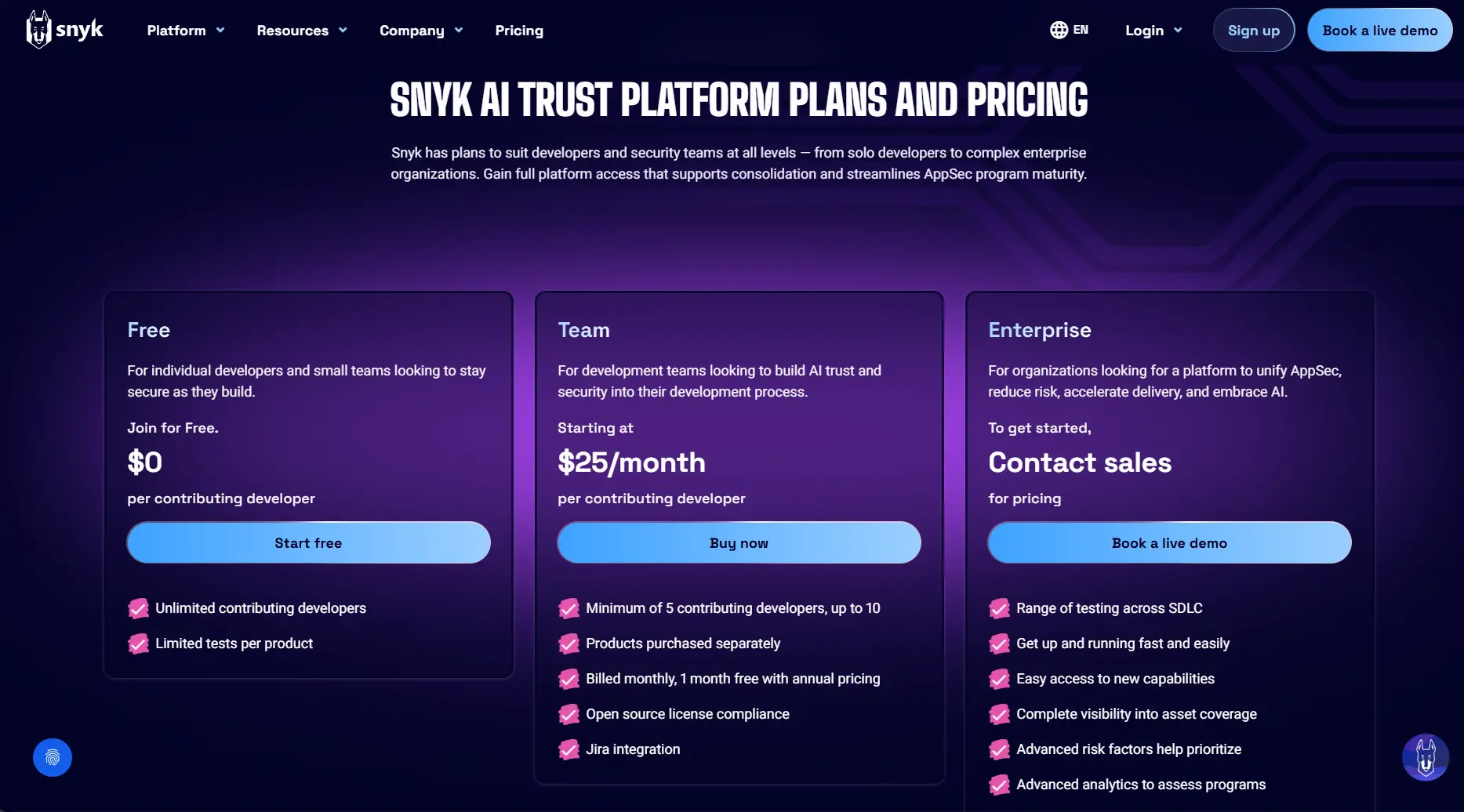
- Free Tier available
- Team Plan: $25/month per contributing developer
- Enterprise: Custom quote
Ratings and reviews:
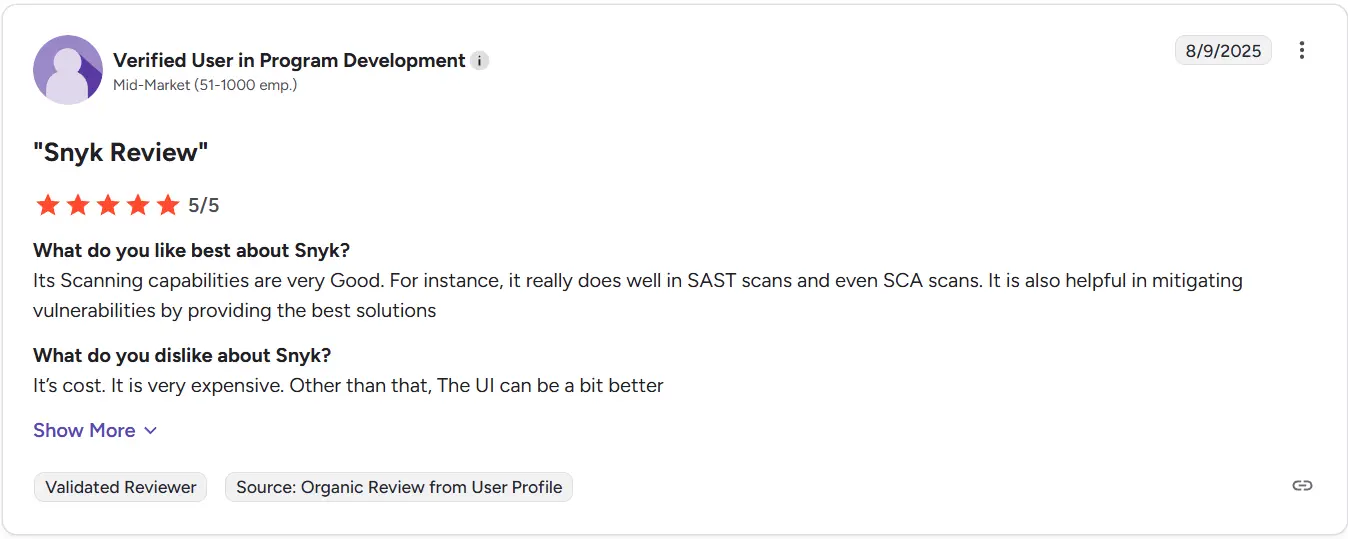
Snyk has an average rating of 4.6 out of 5 on G2. Users appreciate tight integration with development workflows. Some indicate that DAST scanning depth is still evolving compared to older DAST tools.
Conclusion
Choosing the right AppCheck alternative depends on your application portfolio size, team structure, and security maturity. AppCheck’s unlimited scanning model is powerful for organizations with large portfolios that are actively scanning many applications on a frequent basis. However, teams with smaller portfolios often see better ROI from usage-based or per-application pricing models.
Beagle Security stands out for cost efficiency and developer usability, especially for teams that want continuous testing integrated into CI/CD workflows. Enterprise organizations with strong governance needs may prefer Veracode or Checkmarx. Security engineering and manual testing teams may rely on Burp Suite for deeper control.
The right tool supports your development speed and scales with your environment. Understanding how you test, how often you test, and who consumes the results is key to selecting the best fit.
FAQ
What makes AppCheck different from other DAST tools?
AppCheck provides unlimited scans and unlimited users under one license, which is not common among DAST vendors. This makes it valuable for organizations with frequent scanning needs across many applications. Other tools typically charge per application, per target, or based on usage volume.
Is unlimited scanning always cost effective?
Unlimited scanning provides predictable spend and can be cost efficient for large portfolios. However, many organizations do not actually scan every application frequently enough to benefit. Usage-based pricing or per-application pricing can be more cost aligned for smaller portfolios.
Can automated DAST replace manual penetration testing?
Automated DAST tools detect common vulnerabilities efficiently and support continuous validation. Manual testing is still needed for advanced logic flaws, chained attack paths, and creative exploitation. Many organizations use both approaches together.
Which tools are best for developer-first environments?
Beagle Security and Snyk DAST are preferred in development-led environments. They integrate with CI/CD systems and produce remediation guidance written for engineers rather than security teams.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)