![Internal Penetration Testing: The Definitive Guide [2023] Internal Penetration Testing: The Definitive Guide [2023]](/blog/images/internal-penetration-testing.webp)
As a growing organization, it’s important to take every precaution to protect your company’s assets and data.
While it’s easy to focus on external threats such as hackers and cyber-attacks, it’s also important to consider the potential vulnerabilities that may exist within your own organization. This is where internal penetration testing comes in.
Conducting internal penetration tests can help you understand the risks your business is facing and implement the necessary measures to reduce these risks.
In this guide, we’ll discuss the importance of internal penetration testing and how to go about conducting these tests in your organization.
Types of penetration testing
Penetration testing, also known as pen testing, is a method of evaluating the security of a computer system or network by simulating an attack by a malicious actor. There are two main types of penetration testing: internal and external.
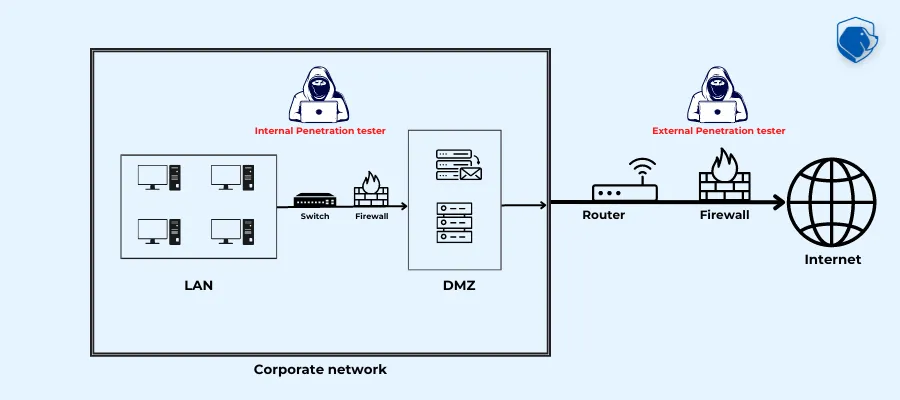
Internal penetration testing
Internal penetration testing simulates an attack from within an organization’s network.
The goal of this type of testing is to identify vulnerabilities that could be exploited by an attacker with access to the internal network, such as a current or former employee.
This type of testing can help organizations identify and address security weaknesses in areas such as network segmentation, access controls, and user privilege management.
External penetration testing
External penetration testing simulates an attack from outside an organization’s network.
This type of testing is designed to identify vulnerabilities that could be exploited by an attacker with no prior access to the network, such as a cyber-criminal.
This type of testing can help organizations identify and address security weaknesses in areas such as firewall and intrusion detection/prevention system configurations, web application security, and remote access protocols.
Why is internal penetration testing important?
Internal penetration testing is crucial for businesses of all sizes, as it helps to identify and address vulnerabilities within your own organization.
These vulnerabilities could be exploited by malicious insiders, such as disgruntled employees or contractors, or by external attackers who have gained access to your internal systems and networks.
Internal penetration testing can help to identify weaknesses in your security infrastructure, including:
Unsecured or weak passwords
Unpatched software or operating systems
Lack of access controls
Inadequate network segmentation
Misconfigured systems or devices
By identifying and addressing these vulnerabilities, you can prevent data breaches and protect your business’s sensitive information.
Also, it is helpful for you to meet compliance requirements, such as PCI DSS (Payment Card Industry Data Security Standard) or HIPAA (Health Insurance Portability and Accountability Act).
These standards require companies to demonstrate that they have taken appropriate measures to secure their systems and networks. Conducting internal penetration tests can help you to meet these requirements and avoid hefty fines and penalties.
How to conduct internal penetration testing
Conducting internal penetration testing requires careful planning and execution. Here are the steps to follow when conducting these tests in your organization:
1. Define your scope and objectives
Before you begin testing, it’s important to clearly define the scope and objectives of your testing.
This includes determining which systems and networks will be tested and what you hope to achieve with the testing.
2. Identify your testing team
It’s important to assemble a team of experienced professionals who are familiar with your systems and networks. This team should include a mix of IT staff, security professionals, and business stakeholders.
3. Create a testing plan
Your testing plan should outline the specific steps that will be taken during the testing process, including any tools or techniques that will be used.
This plan should also include a timeline for testing and a process for reporting and addressing any vulnerabilities that are identified.
4. Conduct the testing
During the testing process, the team will simulate cyber-attacks on your systems and networks to identify vulnerabilities.
It’s important to ensure that all testing is conducted in a controlled environment to minimize the risk of any damage to your systems.
5. Analyze and report on the results
After the testing is complete, the team should analyze the results and document any vulnerabilities that were identified.
This report should include recommendations for addressing these vulnerabilities and improving your overall security posture.
6. Implement security measures
Based on the findings of your internal penetration test, you should implement the necessary measures to address any vulnerabilities and improve your overall security posture.
This may include updating software and operating systems, strengthening passwords, implementing access controls, and improving network segmentation.
7. Monitor and reassess
It’s important to continuously monitor your systems and networks for vulnerabilities and to regularly reassess your security posture.
This may involve conducting additional internal penetration tests on a regular basis to ensure that your security measures are effective.
Benefits of internal penetration tests
Internal penetration testing is an important part of maintaining the security and integrity of your business. By simulating cyber-attacks and identifying vulnerabilities within your own organization, you can take the necessary measures to protect your company’s assets and data.
Internal penetration testing can provide several benefits for organizations, including:
Identification of vulnerabilities
Internal penetration testing allows organizations to identify and prioritize vulnerabilities within their internal network and systems. This can help organizations to better understand the risks they face and take appropriate steps to mitigate them.
Compliance
Many regulatory bodies require organizations to conduct regular penetration testing as part of their compliance requirements. Internal penetration testing can help organizations to meet these requirements and avoid penalties.
Improved incident response
Internal penetration testing can help organizations to identify and address vulnerabilities before they are exploited by a malicious actor. This can improve an organization’s incident response capabilities and reduce the impact of a successful attack.
Employee awareness
Internal penetration testing can raise awareness among employees about the importance of information security and the types of threats that organizations face. This can help to create a culture of security within an organization.
Cost-effective
Internal penetration testing is more cost-effective than external testing, as the tester already has access to the internal network and can move around without any restrictions.
Better understanding of internal network
Internal penetration testing allows organizations to have a better understanding of their internal network, and the flow of data within it. This can help organizations to identify and address any issues related to data flow, and ensure data is being transmitted securely.
Beagle Security for internal penetration testing
In addition to conducting manual internal penetration tests, it can also be beneficial to consider implementing automated penetration testing. Beagle Security can assist you with this by offering a variety of solutions to fit your demands for automated pen tests.
Beagle Security Cosmog allows you to run security tests for applications in your internal network without having to expose them on the internet.
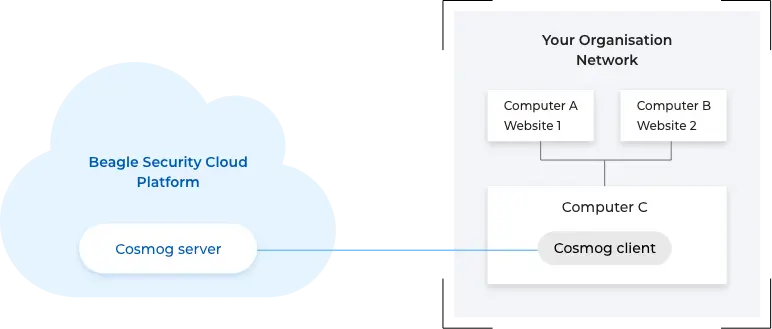
The Cosmog client installed in your internal network connects with the Cosmog server to establish a secure link between the Beagle Security Cloud Platform and your organization’s private network.
A single installation is enough to run tests for all the applications in your internal network. If required, you have the option to set up different profiles, each responsible for a separate internal network or location.
Automated testing allows you to regularly scan your systems and networks for vulnerabilities and can be more cost-effective and efficient than manual testing. It can also help to ensure that all your assets are tested on a regular basis.
By conducting internal penetration tests and implementing automated testing, you can keep your business secure and meet compliance requirements.


![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)