The healthcare industry faces an unprecedented cybersecurity crisis.
Healthcare data breaches are costing organizations an average of $10.93 million per incident. This is nearly three times the global average. Thus protecting ‘electronic protected health information’ (ePHI) has never been more critical.
The Department of Health and Human Services (HHS) has introduced sweeping changes to HIPAA vulnerability scan requirements in 2025 that will fundamentally reshape how healthcare organizations approach cybersecurity.
The proposed HIPAA Security Rule updates, published in the Federal Register on January 6, 2025, represent the most significant changes to healthcare cybersecurity requirements in over two decades.
This landmark update introduces a new requirement for risk assessment in healthcare: all covered entities and business associates must conduct penetration testing of their electronic information systems at least once every 12 months.
These changes respond directly to 2024 being “the worst-ever year in terms of breached healthcare records,” with 276,775,457 records breached as of March 2025.
Why are HIPAA vulnerability scans important?
Healthcare organizations have become prime targets for cybercriminals. Despite a subtle drop in year-over-year cyberattacks (less than 2%), the number of records breached has soared by 64.1%, affecting eight in every ten U.S. citizens.
HIPAA vulnerability scans serve as your first line of defense against these threats. Unlike traditional security assessments that provide a snapshot in time, vulnerability scans continuously monitor your systems for weaknesses that could be exploited by attackers.
The healthcare sector’s unique challenges make vulnerability scanning particularly crucial:
Legacy system dependencies: Many healthcare organizations rely on medical devices and systems that weren’t designed with modern cybersecurity principles, often containing embedded vulnerabilities.
Interconnected ecosystems: Modern healthcare environments involve complex networks of connected devices, from IoT medical equipment to third-party applications. Each connection point represents a potential vulnerability.
High-value data: Medical records contain personally identifiable information, financial data, and health information. This makes them valuable on the dark web and attractive to state-sponsored actors.
Regulatory compliance: Beyond protecting patient data, vulnerability scans help demonstrate due diligence to regulators and can significantly reduce penalties in the event of a breach.
What are the HIPAA vulnerability scan requirements in 2025?
The 2025 HIPAA Security Rule updates introduce specific, mandatory HIPAA risk assessment requirements that represent a significant departure from previous guidelines.
Mandatory testing requirements
Penetration testing: All covered entities and business associates must conduct penetration testing at least once every 12 months by “qualified person(s)” with appropriate knowledge of generally accepted cybersecurity principles.
Vulnerability scanning: Vulnerability scanning must be conducted at least every six months, doubling the frequency compared to previous recommendations.
Risk-based adjustments: Testing must be conducted every 12 months “or in accordance with the healthcare entity’s risk analysis, whichever is soonest,” meaning high-risk organizations may need more frequent testing.
Comprehensive scope requirements
The updated HIPAA log requirements extend beyond traditional IT infrastructure to include:
Network infrastructure: All systems that process, store, or transmit ePHI
Web applications: Custom healthcare applications, patient portals, and EHR systems
API security: FHIR APIs and health information exchanges require specialized API security testing
Cloud environments: Cloud configurations, storage systems, and hybrid infrastructure
Medical devices: Connected medical devices, including IoT sensors, infusion pumps, and diagnostic equipment
Documentation and reporting standards
The new HIPAA security assessments’ requirements mandate comprehensive documentation of all vulnerability scanning activities, including:
Detailed scope definitions for each scan
Methodologies used for vulnerability identification
Risk ratings and prioritization criteria
Remediation timelines and responsible parties
Validation testing results
Exception handling procedures
Additional compliance requirements
Beyond testing, the proposed updates introduce the following additional HIPAA compliance assessment requirements:
Multi-factor authentication: Mandatory implementation of MFA for accessing ePHI systems.
Encryption standards: Required encryption for ePHI both at rest and in transit.
Documentation requirements
Written technology asset inventory
Network mapping of systems and assets impacting ePHI
Documented audit procedures every 12 months
Written risk management plan with yearly reviews
Recovery procedures: Systems and data must be recoverable within 72 hours of a loss.
Drawbacks of HIPAA vulnerability scans
While HIPAA vulnerability scanning is essential for compliance, traditional approaches have significant limitations:
Point-in-time limitations: Traditional vulnerability scans provide a snapshot at a specific moment, potentially missing critical vulnerabilities that emerge between assessment periods.
False positive burden: Conventional vulnerability scanners often generate high volumes of false positives, with security teams spending an estimated 30-40% of their time investigating alerts that don’t represent genuine risks.
Limited context understanding: Traditional scans often lack the context needed to understand how vulnerabilities might be exploited in real-world attack scenarios.
Compliance gaps: Many organizations perform vulnerability scans to check a compliance box rather than genuinely improve their security posture.
| Aspect | Traditional vulnerability scanning | Continuous penetration testing |
|---|---|---|
| Frequency | Quarterly/annual | On a recurring schedule (weekly or monthly) |
| Threat detection | Known vulnerabilities only | Emerging threats + zero-days |
| Context awareness | Limited | Full attack path analysis |
| Remediation speed | Weeks to months | Hours to days |
| Compliance coverage | Point-in-time compliance | Continuous compliance |
| Resource efficiency | High false positive rates | AI-driven prioritization |
| Cost effectiveness | High per-scan costs | Predictable subscription model |
Why continuous penetration testing should be part of your HIPAA compliance roadmap
The evolution from annual compliance assessments to continuous security validation represents a fundamental shift in healthcare cybersecurity approach.
The inadequacy of annual penetration testing
Annual penetration testing creates dangerous security gaps. A healthcare organization conducting its annual test in January might miss a zero-day vulnerability discovered in March, providing attackers with a nine-month window of opportunity.
Benefits of continuous penetration testing
Real-time threat detection: Continuous platforms identify vulnerabilities as they emerge, not months later during scheduled assessments.
Attack path analysis: Modern penetration testing maps complete attack paths, helping organizations understand how attackers might chain together multiple vulnerabilities.
Compliance automation: Continuous testing platforms automatically generate compliance reports, reducing administrative burden while ensuring ongoing HIPAA adherence.
Cost optimization: While upfront investment may seem higher, continuous testing typically reduces overall security costs by preventing breaches.
Real-world healthcare attack scenarios
Recent healthcare breaches demonstrate sophisticated attack patterns:
Advanced persistent threats: The Premera Blue Cross incident involved attackers maintaining undetected access for nine months, exfiltrating information from over 10.4 million individuals.
Supply-chain attacks: The 2023 MOVEit attack affected hundreds of healthcare organizations worldwide, exploiting a zero-day vulnerability that annual testing wouldn’t have detected.
Medical device exploitation: Connected medical devices often contain hardcoded credentials, unencrypted communications, and weak authentication mechanisms.
How the Beagle Security platform can help with your HIPAA penetration testing
Beagle Security offers a comprehensive automated AI-driven penetration testing platform specifically designed for healthcare organizations facing the 2025 HIPAA requirements.
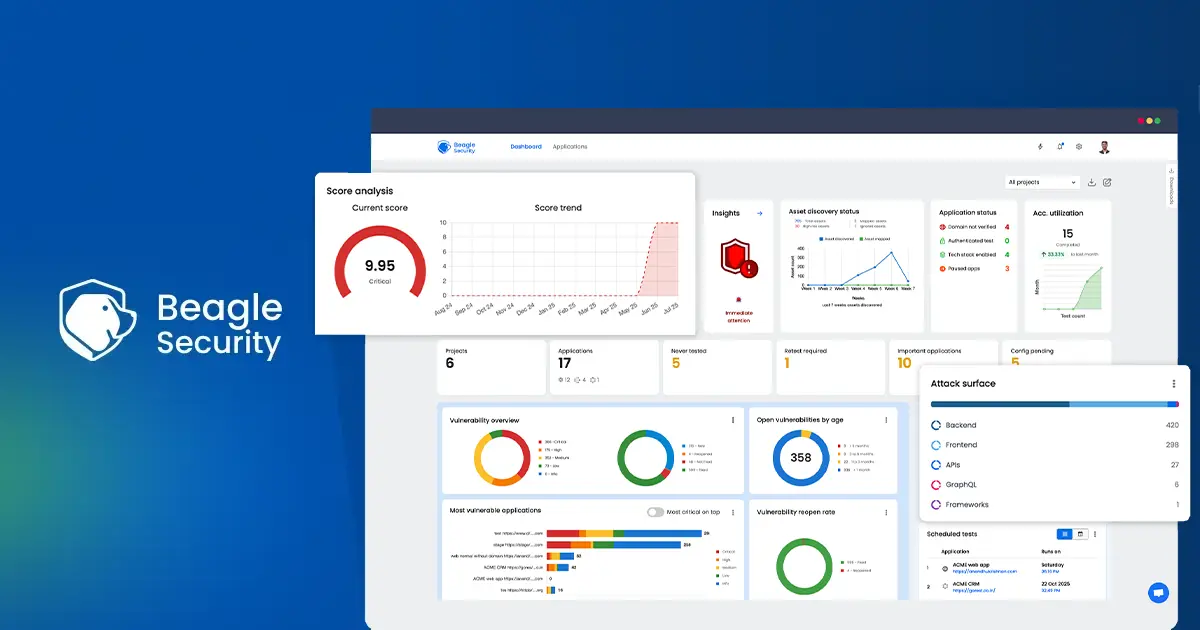
Web application penetration testing
Healthcare organizations rely heavily on web applications for patient portals, EHRs, and clinical management systems.
Traditional security scanners miss critical vulnerabilities because they can’t navigate these intricate workflows or understand the sensitive data flows involved.
Beagle Security’s web application penetration testing goes beyond surface-level scanning and includes:
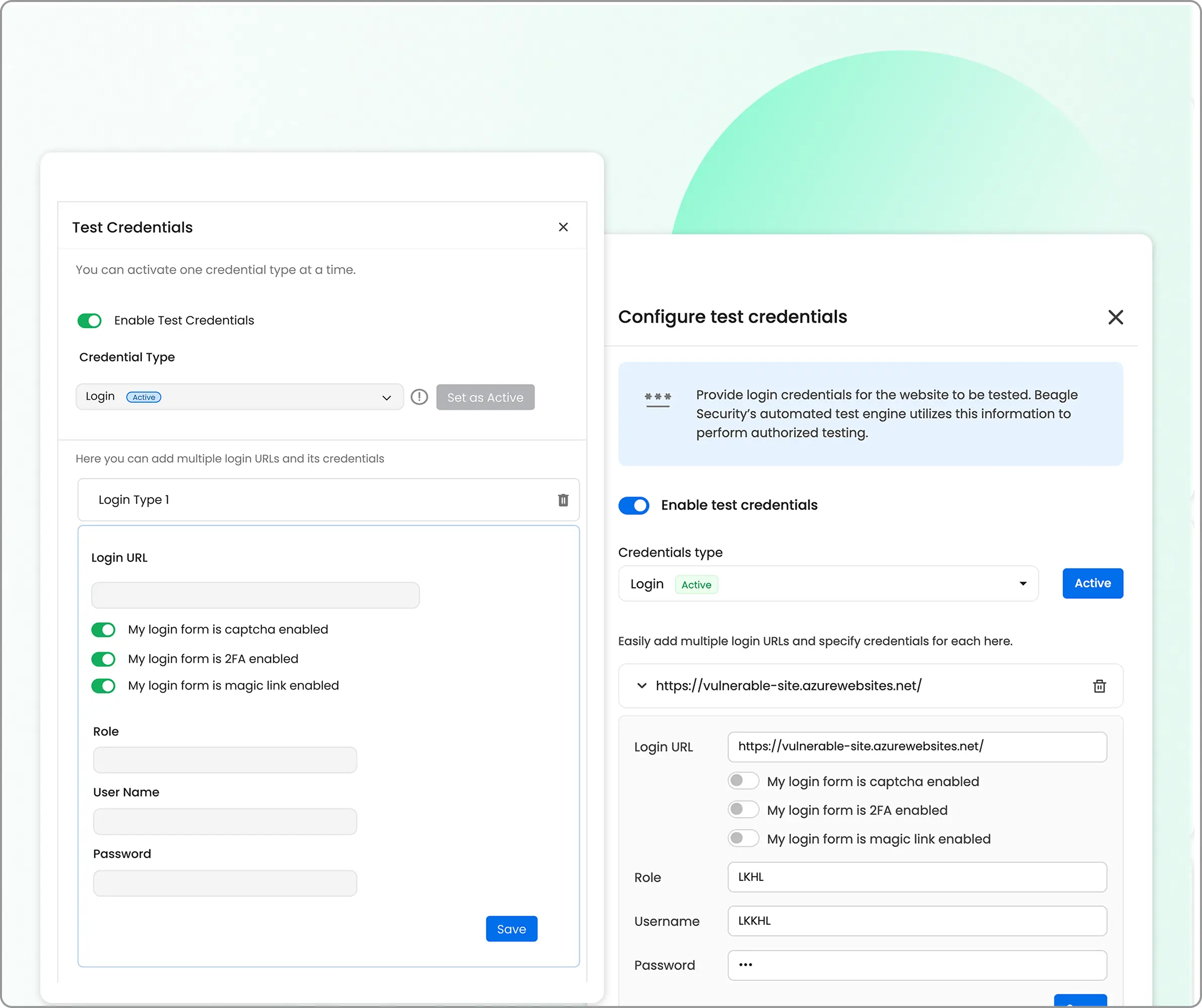
Authenticated testing
Most healthcare applications critical functionality behind a login.
Beagle Security’s AI engine doesn’t just test your login page, it gets inside your application and tests every page, form, and function that your patients and staff actually use. It then finds the vulnerabilities and includes it in the reports.
Cover complex business logic
Healthcare applications have some of the most complex business logic I’ve ever encountered.
Think about a typical patient scheduling workflow.
It might involve multiple steps and various user permissions.
With Beage Security’s business logic recorder, your team can simply record these complex workflows once, and the AI engine learns how to navigate and test them automatically. No more manual testing of every possible user journey, the platform handles it intelligently.
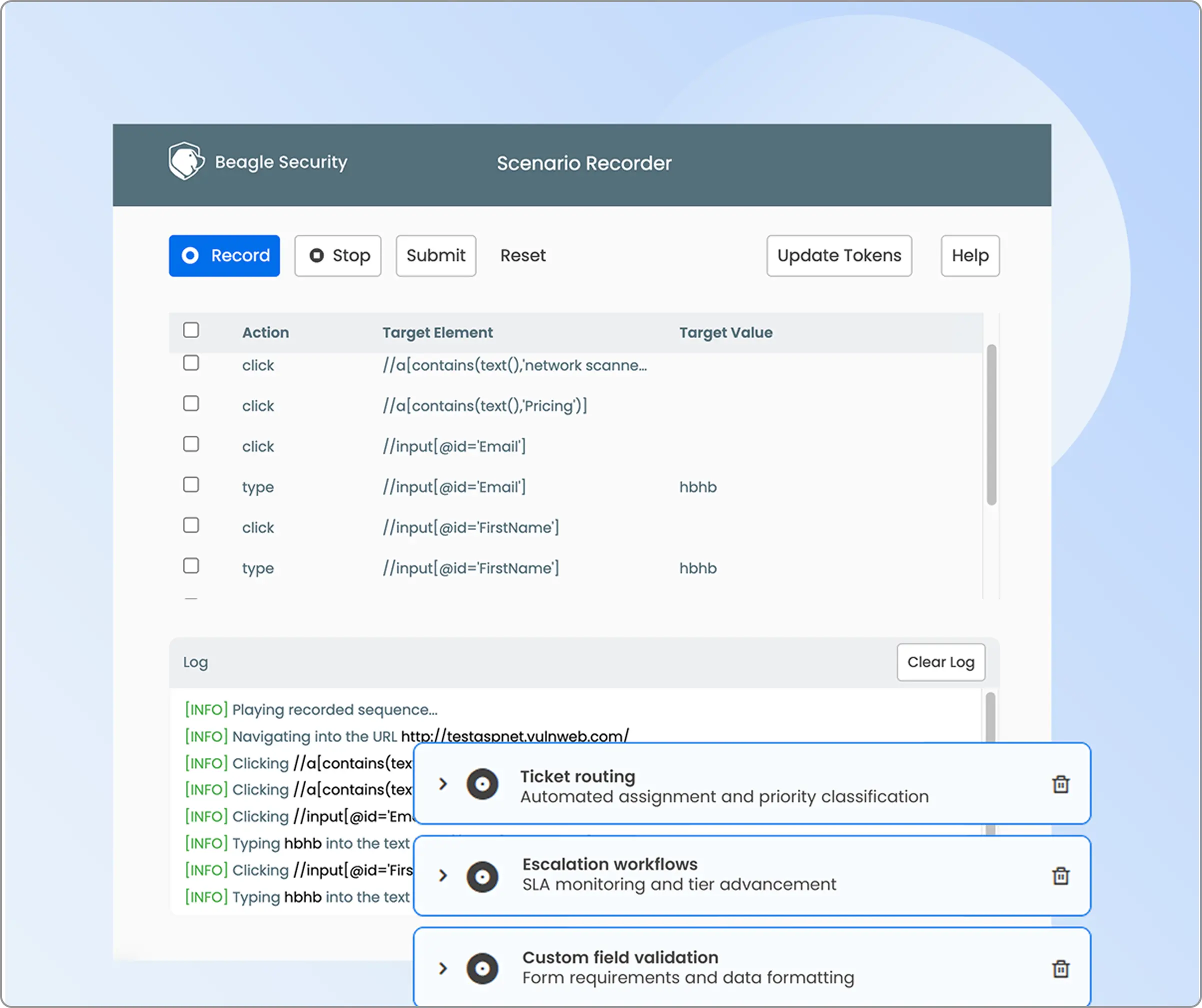
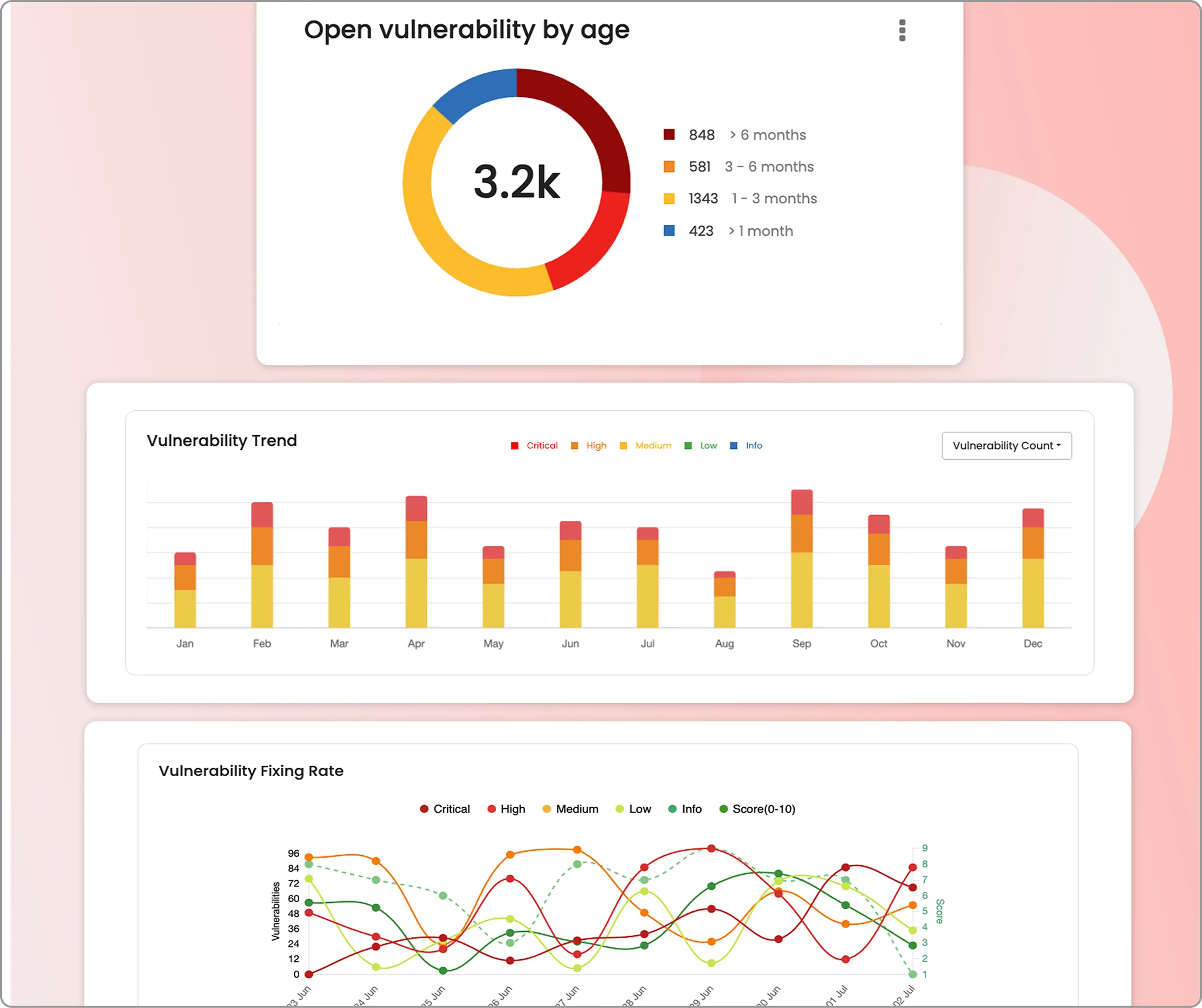
Actionable security dashboards
Detailed security dashboard with customizable widgets that can be tailored to the metrics and insights that matter for you.
API & GraphQL penetration testing
The healthcare industry’s API adoption creates new attack surfaces requiring specialized security testing. Beagle Security’s API & GraphQL penetration testing capabilities include:
Direct sync with Postman
direct Postman integration automatically syncs your API collections, so you don’t need to recreate your entire API inventory just for security testing.
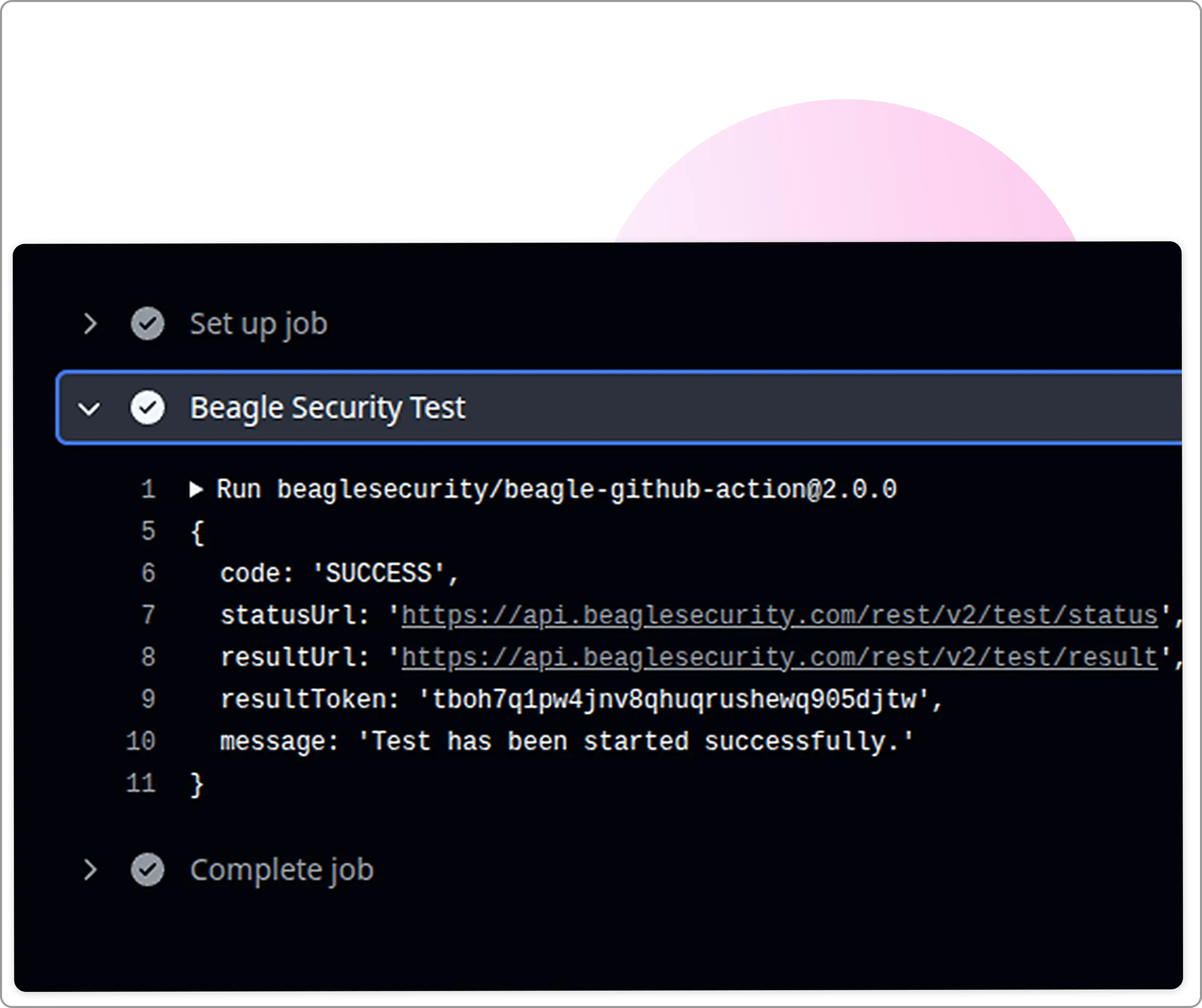
Automate pentesting in the CI/CD pipeline
Native CI/CD integrations let you automate penetration testing right in your development pipeline without creating bottlenecks.
Your team can catch vulnerabilities before they hit production, which is crucial when you’re dealing with patient data.
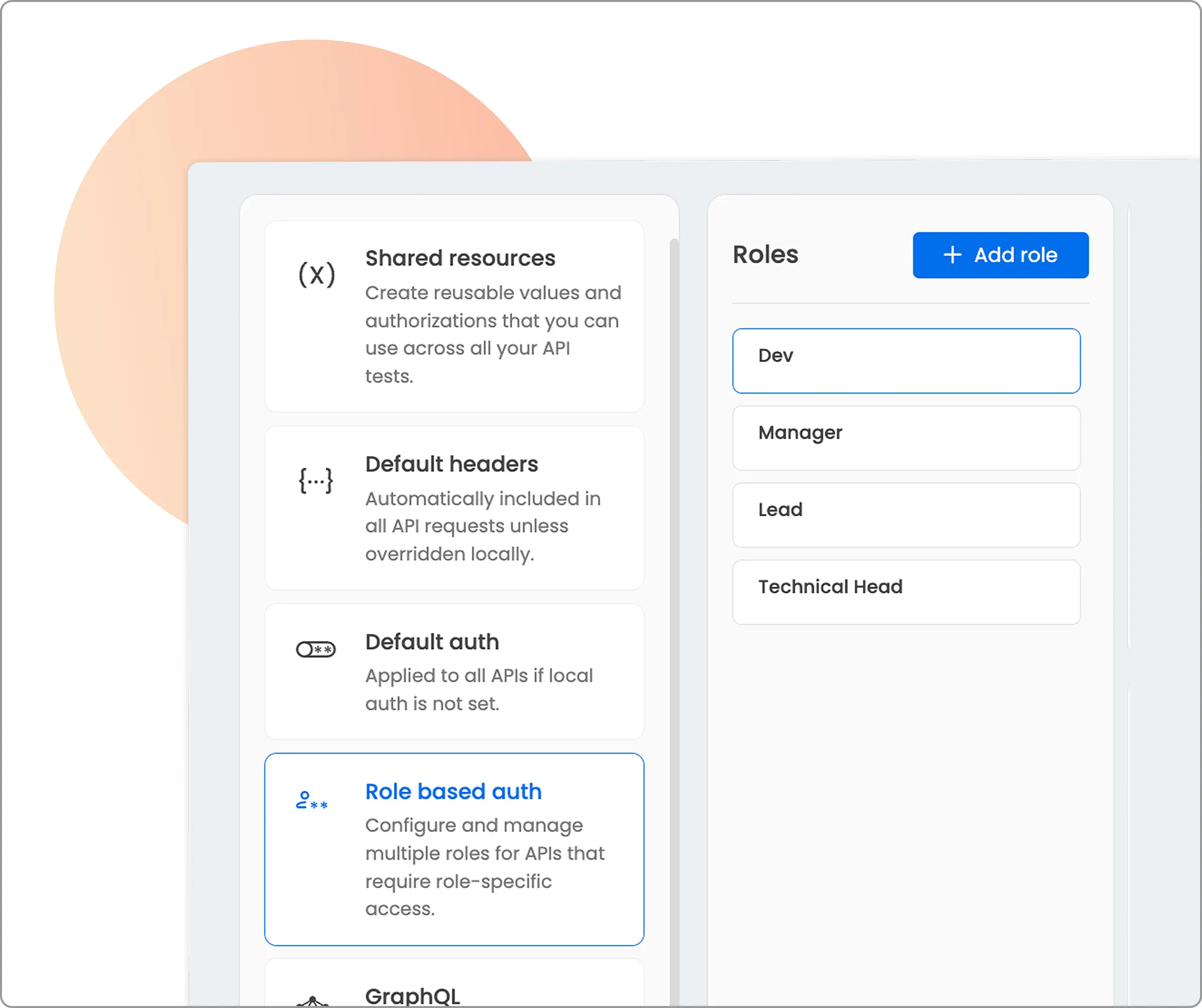
Role-based testing of APIs
Healthcare applications have some of the most complex authorization models out there. Doctors, nurses, administrators, patients, and insurance representatives all need different levels of access.
The Beagle Security platform tests these authorization boundaries with support for OAuth 2.0, Bearer tokens, and API keys, ensuring that a patient can’t access another patient’s records or that a nurse can’t perform admin functions.
Penetration test reports against HIPAA compliance
Beagle Security’s reporting capabilities address HIPAA compliance requirements including:
Compliance mapping
Detailed mapping of vulnerabilities to specific HIPAA Security Rule requirements
Risk prioritization
Vulnerability scoring considering specific risks to ePHI
Executive summaries
Board-ready executive summary section in reports communicating security posture to leadership
Remediation guidance
Detailed developer-friendly technical guidance with step-by-step recommendations
Wrapping up
The 2025 HIPAA vulnerability scan requirements and HIPAA logging represent a watershed moment for healthcare cybersecurity.
The requirement for vulnerability scanning every six months and penetration testing annually signals a fundamental shift from reactive to proactive security testing.
Healthcare organizations that embrace these changes will find themselves better positioned to protect patient data and maintain regulatory compliance.
This will help build trust with patients and partners. Success requires a comprehensive approach combining automated vulnerability scanning and continuous penetration testing.
The cost of compliance pales in comparison to the potential impact of a major data breach. Healthcare organizations that view these requirements as an opportunity to strengthen their security posture rather than merely a compliance burden will emerge as industry leaders.
FAQs
What are the requirements of the HIPAA security rule?
The HIPAA Security Rule requires covered entities to implement administrative, physical, and technical safeguards to protect ePHI. The 2025 updates mandate vulnerability scanning every six months, annual penetration testing, network segmentation, and enhanced documentation requirements.
What is required for software to be HIPAA-compliant?
HIPAA-compliant software must implement access controls, audit logging, data encryption, and secure authentication mechanisms. Under the 2025 updates, software systems must undergo regular vulnerability assessments and penetration testing.
What data needs to be HIPAA compliant?
All electronic protected health information (ePHI) must be HIPAA compliant, including patient medical records, billing information, insurance details, and any identifiable health information stored, processed, or transmitted electronically.
![Best tools for SOC 2 compliance penetration testing [2025] Best tools for SOC 2 compliance penetration testing [2025]](/blog/images/blog-banner-two-cover.webp)

![Best tools for HIPAA penetration testing [2025] Best tools for HIPAA penetration testing [2025]](/blog/images/blog-banner-one-cover.webp)