
What is vulnerability scanning?
A vulnerability scan identifies and reports any weaknesses in your firewalls, software, web applications, servers, and other devices connected to your corporate IT systems. It is an essential component of a company’s vulnerability management program and overall security posture.
Vulnerability scans come in two types: internal and external. Internal scans aim to find vulnerabilities within your company’s internal networks and IT assets.
In contrast, external scans are conducted on your company’s network perimeter, which connects to the outside world. Essentially, an external scan checks the locks on your house’s entrance doors and windows, while an internal scan checks the locks on the doors of individual rooms.
To conduct these assessments, companies use a vulnerability scanner, an automated security scanning tool that identifies known vulnerabilities.
It’s important to note that a vulnerability assessment will not detect zero-day vulnerabilities, which are vulnerabilities unknown to the software or hardware vendor.
Limitations of vulnerability scanning
Vulnerability scanning, while a critical component of a robust security posture, does have several limitations:
1. False positives and negatives
False positives: The scanner may incorrectly identify a vulnerability that does not exist, leading to unnecessary remediation efforts.
False negatives: The scanner might miss actual vulnerabilities, providing a false sense of security.
2. Zero-day vulnerabilities
Vulnerability scanners cannot detect zero-day vulnerabilities, which are unknown to the software or hardware vendor.
3. Configuration issues
Scanners may not detect vulnerabilities arising from complex configurations or specific settings within an environment.
4. Limited context
Vulnerability scans often lack the context needed to understand the criticality of vulnerabilities in relation to the specific business environment and the potential impact.
5. Performance impact
Scanning can consume significant network and system resources, potentially impacting performance during the scanning process.
6. Frequency of scans
If scans are not performed regularly, new vulnerabilities that emerge between scans may go undetected.
7. Authentication and access
Scanners may have limited access to all areas of the network or systems, leading to incomplete assessments. Lack of proper authentication can also hinder the effectiveness of scans.
8. Complex environments
In highly complex or large-scale environments, vulnerability scans may not cover every device, application, or network segment comprehensively.
9. Static nature
Scanners may not adapt well to dynamic environments where systems and applications are frequently updated or changed.
10. Remediation efforts
Identifying vulnerabilities is only part of the solution; effective remediation requires time, resources, and prioritization, which can be challenging to manage.
Understanding these limitations is crucial for integrating vulnerability scanning effectively within a broader security strategy that includes other measures such as penetration testing, threat intelligence, and continuous monitoring.
What is penetration testing?
A penetration test is performed by a team of penetration testers, or ethical hackers, to identify and test entry points within an organization’s security environment. The goal is to expose potential vulnerabilities and exploit weaknesses.
Penetration testing, often referred to as “pen testing,” simulates a cyber-attack to assess how easily cybercriminals could exploit vulnerabilities and infiltrate the organization’s internal networks.
As a result, pen testing is generally more effective at exposing and managing an organization’s overall cybersecurity risk than a vulnerability assessment.
What is the main difference between vulnerability scanning and penetration testing?
| Aspect | Penetration testing | Vulnerability scanning |
|---|---|---|
| Usage scenario | Provides a thorough security evaluation by simulating real-world attacks to uncover existing and potential vulnerabilities. This approach not only identifies issues but also demonstrates how they can be exploited. | Identifies known vulnerabilities within systems and applications, helping to maintain a baseline level of security. However, it does not replicate the full complexity of an actual attack. |
| Method | Combines automated tools with expert manual testing, leveraging the creativity and experience of ethical hackers to find weaknesses that automated scanning tools might miss. | Primarily relies on automated tools that scan systems against a database of known vulnerabilities, which may leave gaps where new or complex vulnerabilities exist. |
| Recurrence | Recommended quarterly or after significant changes to ensure ongoing security resilience. Regular testing can adapt to evolving threats. | Typically conducted annually, particularly for compliance purposes. More frequent scans may be done internally, but these are often less rigorous. |
| False positives | Minimized through expert validation, ensuring that only real, exploitable vulnerabilities are reported. This leads to actionable insights without the noise of false positives. | While automated scans are efficient, they can miss nuances, leading to false positives and possibly overlooking sophisticated vulnerabilities requiring manual verification. |
| Coverage | Offers comprehensive coverage across all infrastructure components, including those not easily detected by scanners. Customizable based on the specific needs and risk profile of the organization. | Coverage is typically limited to known vulnerabilities within the database of the scanning tools, which may not fully address emerging threats or complex attack vectors. |
Vulnerability scanning vs penetration testing: Which is better?
Choosing between vulnerability scanning and penetration testing depends on your organization’s specific needs and security objectives:
For regular monitoring: Vulnerability scanning is better for ongoing, regular monitoring of your security posture. It helps in quickly identifying and addressing known vulnerabilities across a wide range of assets.
For deep analysis: Penetration testing is better for a deep, thorough analysis of your security defenses. It provides a realistic assessment of your risk exposure by simulating actual attack scenarios.
Optimal approach: Both vulnerability scanning and penetration testing are essential components of a robust cybersecurity strategy. Combining them ensures continuous monitoring and regular in-depth assessments, providing comprehensive protection against potential threats.
How does Beagle Security help with penetration testing?
Beagle Security is an automated AI penetration testing platform that helps you identify vulnerabilities in your web applications & APIs. The platform uses an AI engine to mimic the actions of a real hacker to understand how deep your web applications or APIs can be compromised.
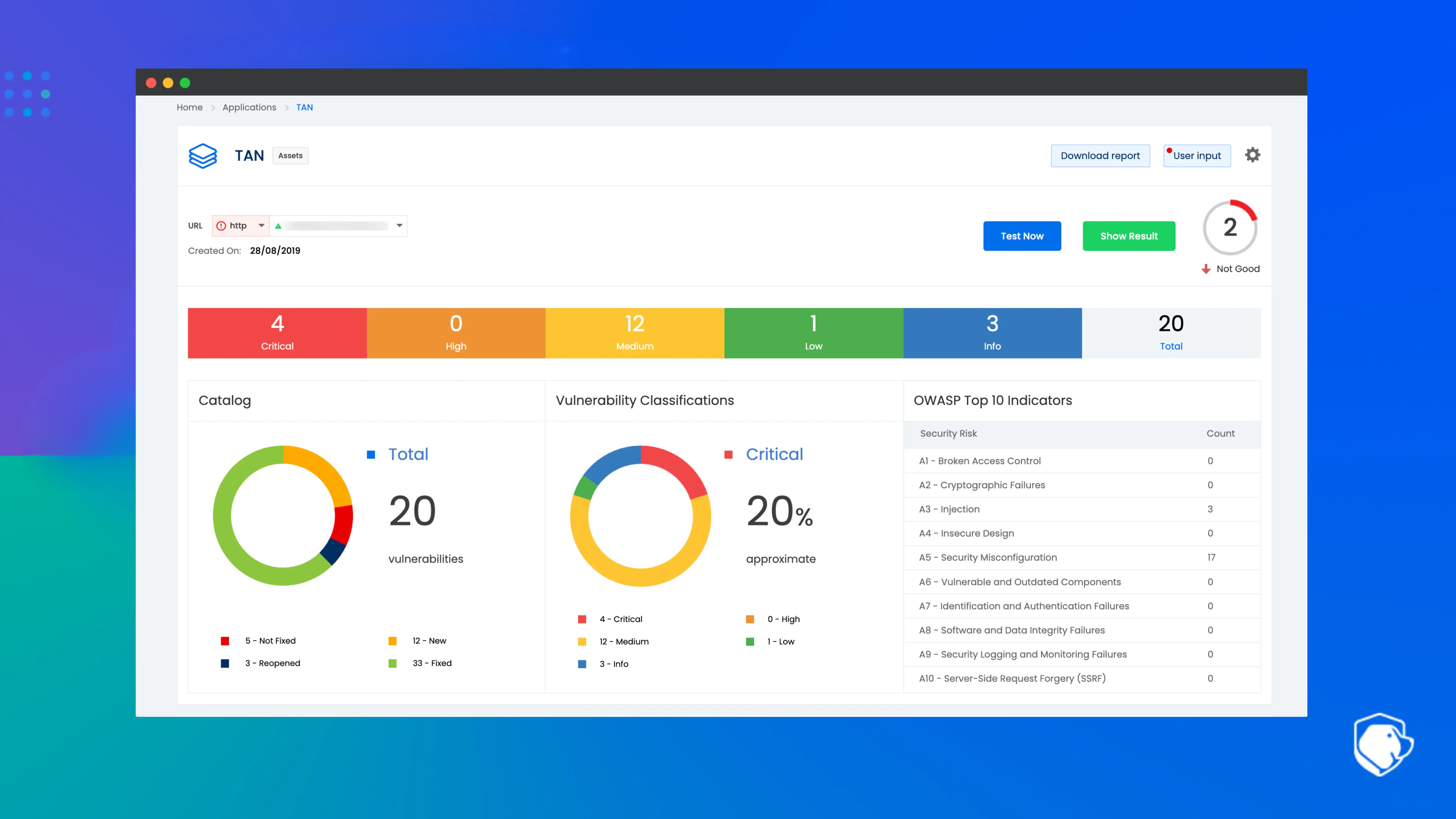
Comprehensive coverage
The platform’s automated penetration testing provides extensive coverage across your web applications and APIs. Beagle Security’s auto asset discovery feature identifies all associated subdomains, ensuring no critical areas are overlooked.
Additionally, flexible scheduling options allow for systematic testing that aligns with your security strategy.
Contextual fix recommendations
The platform provides detailed, developer-centric reports that offer actionable insights. These reports include precise remediation steps tailored to your tech stack, helping teams quickly address vulnerabilities
CI/CD integrations
The Beagle Security platform seamlessly integrates into your CI/CD pipeline, enabling continuous security assessments with every deployment.
This continuous testing approach ensures that your applications remain secure as they evolve, keeping pace with the dynamic nature of software development.
Compliance reports
The platform also aids in meeting regulatory requirements by providing comprehensive penetration test reports that align with industry standards such as PCI DSS, HIPAA, and GDPR. You also get OWASP reports that can be used for your SOC 2 and ISO compliance needs.
These reports help organizations demonstrate their commitment to security and compliance, reducing the burden of regulatory audits.
Wrapping up
In conclusion, both vulnerability scanning and penetration testing are crucial for maintaining robust security, but they serve different purposes.
Vulnerability scanning provides a broad, automated assessment of potential security weaknesses, offering a regular check-up on known issues.
Penetration testing, however, dives deeper by simulating real-world attacks to uncover and validate vulnerabilities, assessing their potential impact and providing detailed insights for remediation.
Together, these approaches complement each other, enabling organizations to proactively identify and address security risks, ultimately strengthening their defense against cyber threats.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)