
What is DAST?
Dynamic Application Security Testing (DAST) is an essential component of a robust cybersecurity strategy, offering a unique and comprehensive approach to identifying vulnerabilities in running applications.
Unlike Static Application Security Testing (SAST), which focuses on analyzing the source code, DAST operates by evaluating an application in its fully deployed and operational state.
This allows DAST to simulate real-world attack scenarios, providing a perspective that mimics the actions of a potential attacker.
One of the primary advantages of DAST is its ability to uncover vulnerabilities that arise from runtime behaviors, configuration errors, and environment-specific vulnerabilities.
By interacting with the application in its live environment, DAST can detect flaws such as SQL injection, cross-site scripting (XSS), and other web application vulnerabilities that could be exploited if left unaddressed.
DAST’s proactive nature is another significant benefit. By continuously testing applications throughout the development and deployment lifecycle, DAST ensures that vulnerabilities are identified and remediated promptly, reducing the window of opportunity for malicious actors.
Moreover, DAST complements other testing methodologies, such as SAST and Interactive Application Security Testing (IAST), to provide a more comprehensive security posture.
Why do you need DAST?
A DAST tool is essential for several reasons:
Real-world simulation: DAST tools simulate real-world attacks on applications by interacting with them just like a potential hacker would. This approach helps uncover vulnerabilities that may not be detectable through other testing methods like SAST.
Comprehensive coverage: DAST tools provide broad coverage by testing the entire application stack, including front-end interfaces, APIs, and backend services. This comprehensive testing helps ensure that all potential entry points for attacks are evaluated.
Scalability and automation: DAST tools are often scalable and can be automated to run regular tests throughout the development lifecycle and after deployment. This scalability ensures that applications remain secure as they evolve and scale.
Compliance requirements: Many regulatory frameworks and industry standards require regular security testing. Organizations can effectively navigate compliance by using a DAST tool.
Risk mitigation: By identifying and remediating vulnerabilities early in the development process or before they are exploited by attackers, DAST tools help mitigate the risk of security breaches, data leaks, and potential financial and reputational damage.
Integration with DevOps practices: DAST tools can be integrated into DevOps pipelines, allowing for continuous testing and rapid feedback on security vulnerabilities. This integration supports agile development practices without compromising on security.
It complements other testing methodologies, supports regulatory compliance, and helps mitigate risks associated with cyber threats.
Now, let’s delver deeper and look at the 4 best DAST tools available in the market today.
4 best DAST tools in 2024
1. Beagle Security
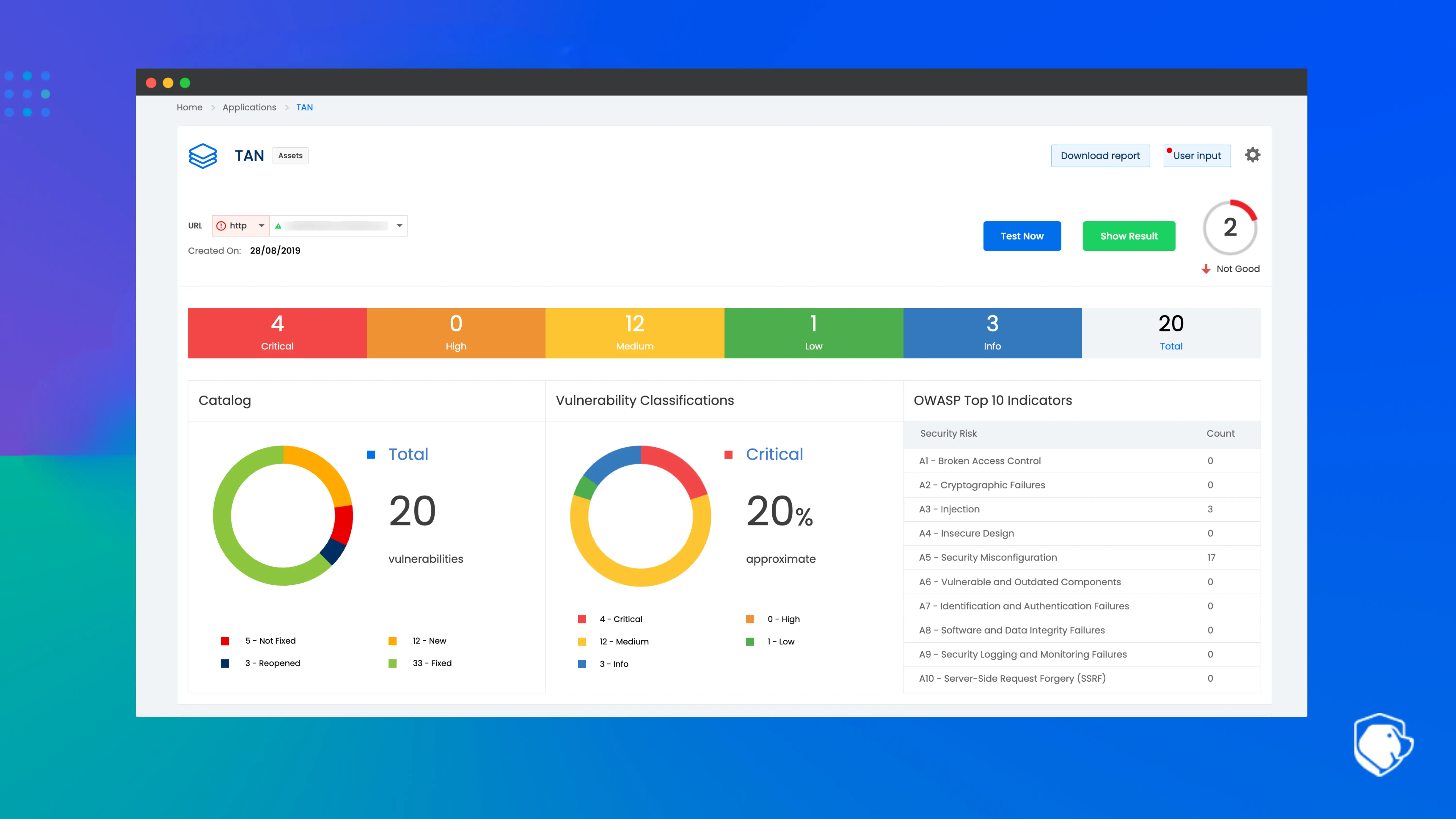
Beagle Security is an automated penetration testing platform designed to identify vulnerabilities in web applications and APIs, offering practical insights to help you address them.
Leveraging an AI core, Beagle Security overcomes the limitations of traditional SaaS vulnerability scanners. It can manage complex login processes like 2FA, magic link, and business logic, ensuring a precise and consistent examination of an application’s security posture.
By providing the tech stack information of your application—such as programming language, database, and framework—you receive contextual reports with tailored recommendations that developers can easily implement. These recommendations come with proof of exploitation and a detailed timeline of vulnerability findings.
Beagle Security also assists in meeting compliance requirements for standards such as GDPR, HIPAA, and PCI DSS. This not only reduces the risk of penalties and reputational damage but also fosters trust with customers and partners.
Key features of Beagle Security
Coverage beyond OWASP Top 10 & CWE Top 25
Tailored LLM based recommendations to address security issues
Asset discovery
Security test complex web apps with login
Compliance reports - GDPR, HIPAA & PCI DSS
OWASP report for ISO & SOC 2 compliance
Test scheduling
DevSecOps integrations
Role-based access controls
SSO
Beagle Security pricing
Beagle Security pricing plans start at $99/month, billed annually. A 10-day free trial is available.
You can also check out an interactive demo or book a personalized demo of the Beagle Security platform.
2. Invicti
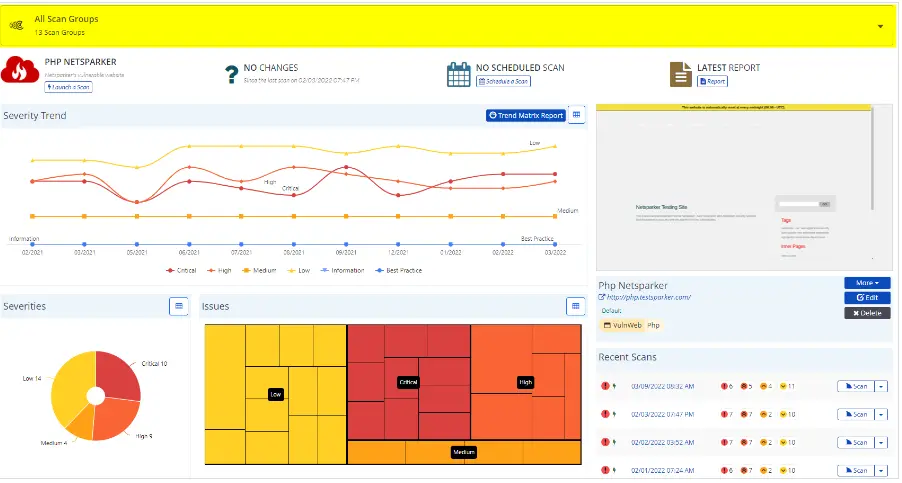
Invicti is a web application security testing platform designed to help organizations identify and remediate vulnerabilities in their web applications and APIs.
It offers automated security testing tools that enable continuous security assessment throughout the development lifecycle.
It supports various authentication mechanisms to ensure comprehensive scanning.
Invicti integrates with popular development and DevOps tools. The platform provides customizable reporting features to help organizations meet regulatory and compliance requirements.
Key features of Invicti
Automated scanning
Integration with development tools
Compliance reporting
User-friendly interface
Invicti pricing
Contact Invicti. No free trial is available.
3. ZAP
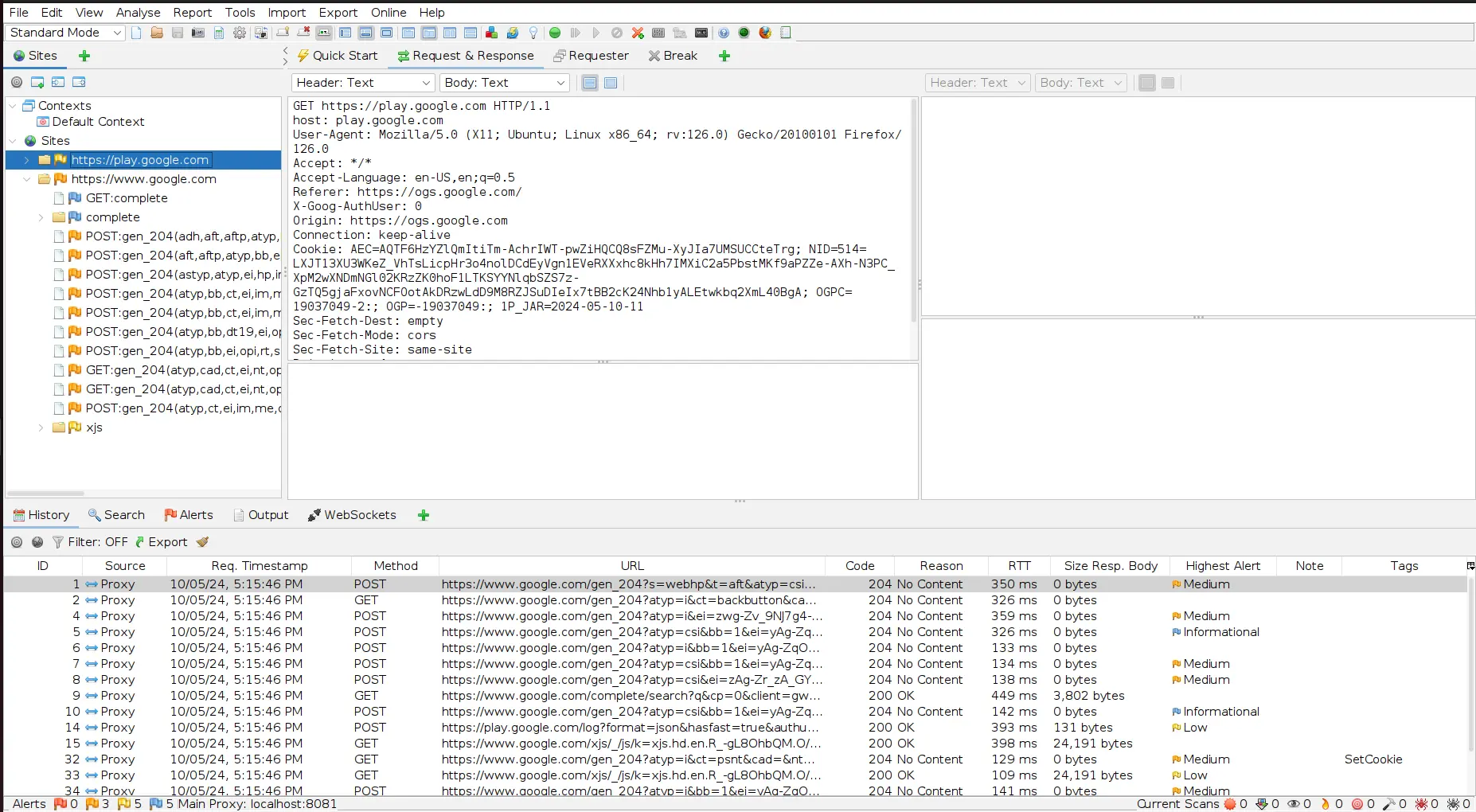
ZAP is an open-source web application security scanner designed to help developers identify security vulnerabilities in their web applications. Acting as a proxy server between the user’s browser and the web application, ZAP allows users to intercept and modify HTTP and HTTPS requests and responses.
ZAP passively monitors traffic and alerts users to potential vulnerabilities without actively sending requests to the application.
ZAP supports various authentication methods and can handle authenticated sessions. However, it requires time to set up, has a learning curve, and does not support advanced login mechanisms.
Key features of ZAP
Active and passive vulnerability scans
Different authentication methods
API integrations
Scan policy
ZAP pricing
ZAP is a free and open-source tool.
4. Burp Suite
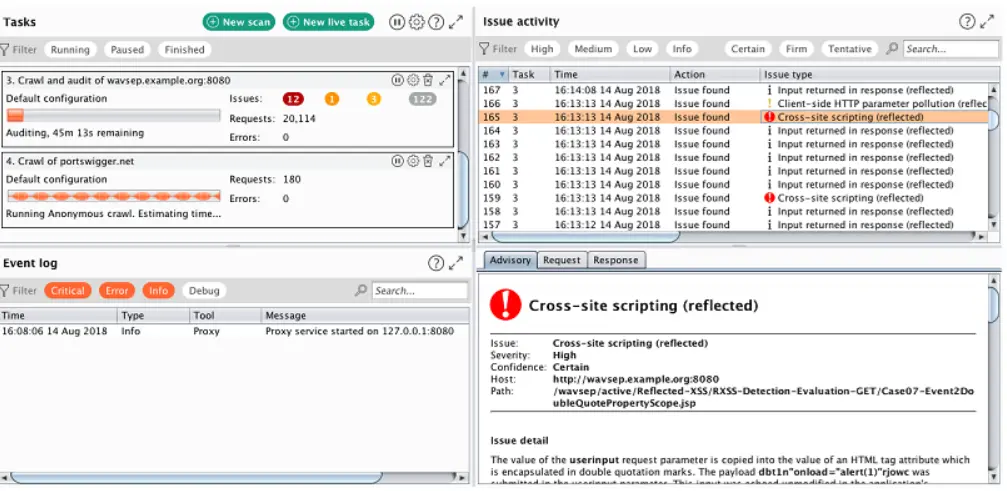
Burp Suite is a dynamic application security testing (DAST) tool designed to help security professionals and developers identify and remediate vulnerabilities in web applications. It offers a comprehensive set of features for security testing, making it a popular choice among penetration testers and security analysts.
While Burp Suite is a powerful DAST tool, it does come with a learning curve and may require significant manual effort to achieve optimal results.
Key features of Burp Suite
Proxy server
Automated crawling and scanning
Detailed reporting
Burp Suite pricing
Pricing for Burp Suite Professional plan starts from $ 449/user/year. Dastardly from Burp Suite is a free, lightweight DAST scanner for your CI/CD pipeline that checks for 7 security issues.
Wrapping up
Choosing the right DAST tool in 2024 depends on your organization’s specific requirements.
Each of the 4 best DAST tools we’ve explored offers distinct advantages.
The optimal choice will depend on several factors, including the size of your company, the specific nature and complexity of your applications, the maturity and scope of your application security practices, and the degree of integration required with your existing workflows and tools.
Additionally, these tools often include features for handling various authentication mechanisms and maintaining authenticated sessions, ensuring thorough security assessments.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)