Application security testing is crucial to make sure your application is free of flaws and dangers, to minimize the attack surface, and to guard against online threats. Organizations today are under growing pressure to release secure, high-performing applications without slowing innovation, and this demands the right testing strategy that utilizes both efficiency and thoroughness.
Two of the most widely used approaches for AppSec are Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST). Both play critical roles in identifying vulnerabilities but they operate at different stages of development and uncover distinct types of risks.
This guide explores the difference between DAST vs SAST, their individual strengths, and how you can combine them to achieve comprehensive application security.
What is DAST (Dynamic Application Security Testing)?
Dynamic Application Security Testing (DAST) is a method of testing applications from the outside in. Often referred to as black-box testing, DAST evaluates a running application the same way an attacker would.
The goal of DAST is to identify and report on security issues that could be exploited by an attacker, so that they can be fixed before the application is deployed.
Instead of reviewing code, DAST interacts with the live application, sending various requests and inputs to identify security flaws that appear during runtime. This helps uncover real-world vulnerabilities like SQL injection, cross-site scripting (XSS), authentication weaknesses, and server misconfigurations.
DAST tools don’t require access to source code, which makes them ideal for testing compiled applications, APIs, or systems developed using multiple programming languages.
When to use DAST
You should use DAST when you need to understand how your application performs under real-world attack scenarios. Common use cases include:
Pre-deployment testing: Before releasing an application, DAST helps validate that it’s secure from an external attacker’s perspective.
Continuous monitoring in CI/CD pipelines: Many organizations integrate DAST into automated workflows to detect runtime vulnerabilities early and continuously.
Third-party component testing: When working with externally built apps or APIs, DAST helps identify vulnerabilities even without code access.
Regulatory compliance checks: DAST scans support frameworks like SOC 2, HIPAA, and ISO 27001, which require proof of security testing.
Benefits of using DAST
DAST delivers several important advantages that make it a cornerstone of modern AppSec programs:
Real-world simulation: DAST tests the application’s behavior during actual execution, revealing vulnerabilities attackers can exploit in production.
Language-independent: Since it tests compiled applications, DAST works with any language or framework.
Comprehensive coverage: It identifies configuration issues, authentication weaknesses, and server misconfigurations that code analysis might miss.
Actionable results: DAST provides clear, reproducible vulnerabilities that security teams can validate and fix quickly.
Supports CI/CD integration: Automated DAST scans fit seamlessly into continuous delivery pipelines, offering ongoing visibility into application security posture.
What is SAST (Static Application Security Testing)?
Static Application Security Testing (SAST), on the other hand, works from the inside out. Also known as white-box testing, SAST analyzes the application’s source code, bytecode, or binaries before the application runs.
SAST examines the structure and logic of your codebase to detect vulnerabilities such as hardcoded secrets, buffer overflows, input validation errors, and insecure dependencies ,all before the software is deployed.
The goal of SAST is to identify and report on security issues that could be exploited by an attacker, so that they can be fixed before the application is deployed.
This makes static application security testing an essential part of the “shift-left” security movement, embedding security early in the software development lifecycle (SDLC).
When to use SAST
SAST is most effective during the development and build stages of your software lifecycle. You should use SAST when:
Building secure-by-design applications: SAST helps developers catch vulnerabilities early in the coding phase, reducing downstream risk.
Reviewing large or legacy codebases: It provides deep insights into security issues hidden in complex or old source code.
Training developers: SAST reports help engineers understand recurring security flaws in their coding patterns.
Implementing shift-left security: Integrating SAST into IDEs or CI/CD pipelines enables early, automated security feedback before release.
Benefits of SAST
SAST offers a different but equally important layer of protection within your application security testing program:
Early vulnerability detection: Identify and fix coding flaws before they become exploitable vulnerabilities.
Reduced remediation costs: Fixing vulnerabilities in development is significantly cheaper than in production.
Developer empowerment: Integrating SAST tools directly into the developer workflow helps reinforce secure coding practices.
Compliance assurance: SAST supports secure coding requirements under standards like OWASP, NIST, and ISO 27034.
Custom rule sets: Teams can tailor SAST rules to match their organization’s security policies and programming environments.
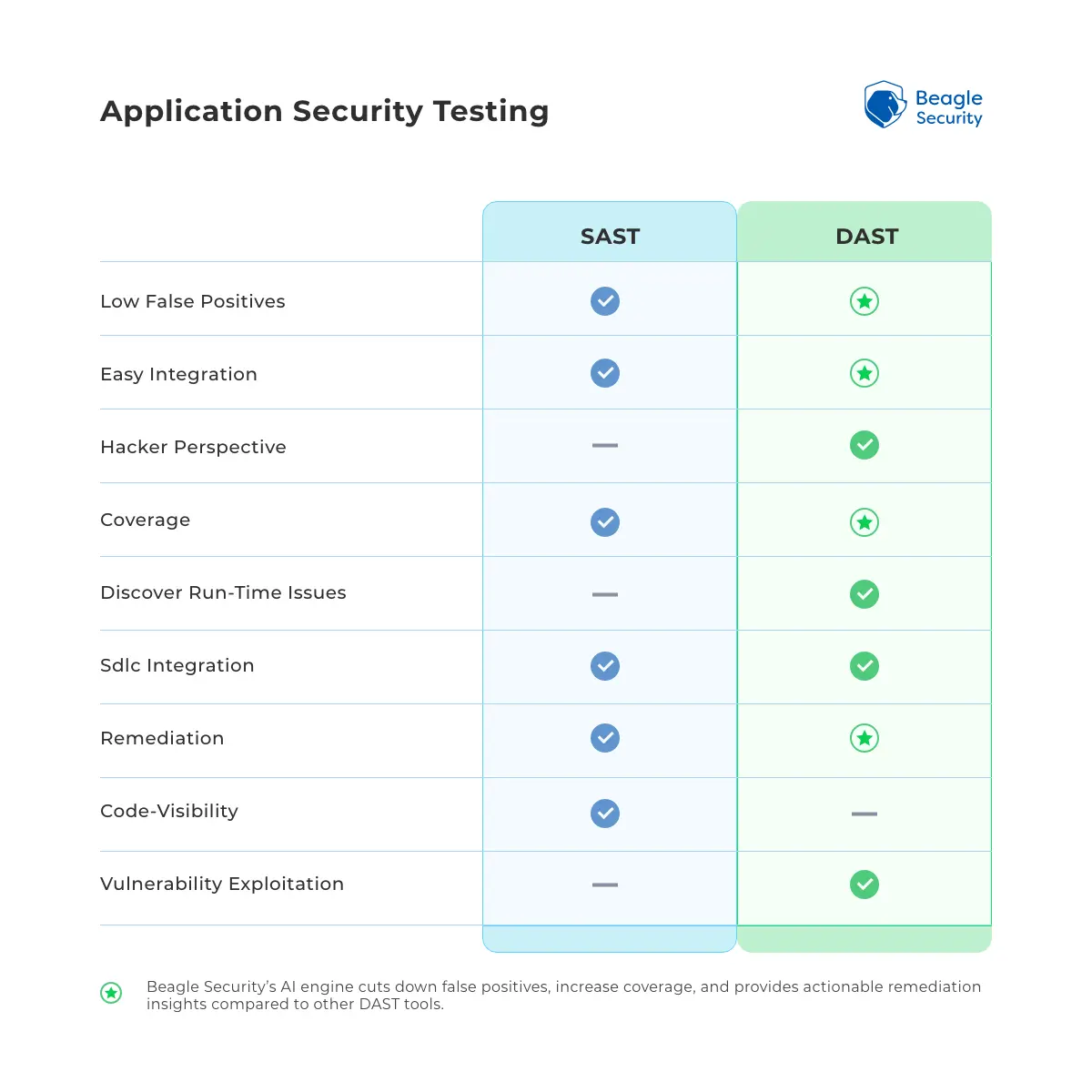
DAST vs SAST: What’s the difference?
While both DAST and SAST aim to secure applications, their approaches and coverage differ significantly. Understanding these differences helps teams decide when and how to use each.
| Criteria | SAST (Static application security testing) | DAST (Dynamic application security testing) |
|---|---|---|
| Testing type | White-box (internal) | Black-box (external) |
| Stage of use | Pre-build / development | Post-build / runtime |
| Focus area | Identifies flaws in code logic or structure | Detects vulnerabilities during execution |
| Access needed | Requires full code access | No access to source code |
| Common findings | Code-level errors, insecure logic, hardcoded credentials | Injection flaws, misconfigurations, auth issues |
| Ideal for | Developers and code reviewers | Security and QA teams |
| Coverage | Examines the entire application, including the source code and the compiled binary, which provides a more comprehensive view of potential vulnerabilities. | Focuses on testing the application's external facing interfaces such as web services, web pages, and APIs. |
| Output type | Detailed code analysis reports | Exploitable runtime vulnerabilities |
In essence:
SAST secures the code before it’s deployed.
DAST secures the application after it’s running.
DAST or SAST: Which one is right for you?
Choosing between DAST vs SAST is about when and how to use each, and it depends on your organization’s priorities, development practices, and compliance needs.
1. Development process
SAST can be a preferable option if your firm uses a classic Waterfall development method because it is frequently carried out during the development process.
DAST can be a preferable option if your company uses an Agile development method because it is frequently carried out after the software has been deployed.
2. Security maturity level
SAST can be a strong choice for organizations with a mature security program and a well-defined software development life cycle (SDLC). It integrates seamlessly with development tools allowing developers to receive real-time security feedback as they write and commit code.
In contrast, DAST typically operates later in the development process, testing running applications from the outside. While it’s not as tightly integrated into developer workflows as SAST, modern DAST tools are increasingly offering CI/CD integrations to support DevSecOps practices.
3. Resources
Due to the need to simulate actual application attacks and execute the program in a test environment, DAST uses more resources than SAST.
SAST uses fewer resources because it analyses an application’s source code or binaries without running it.
4. Compliance
If your organization is subject to specific security regulations, such as PCI DSS or HIPAA, both SAST and DAST can help you comply with these regulations.
5. Risk level
Both SAST and DAST can be required to ensure the security of the application if it handles sensitive data and is a high-risk application for your company.
Basically, choose SAST if you:
Want to implement shift-left security early in your SDLC.
Have access to the source code and aim to reduce technical debt.
Want to empower developers to write secure code proactively.
And choose DAST if you:
Need to validate how your application behaves under attack in production.
Work with multiple third-party components or legacy systems without source code access.
Are focused on compliance or penetration testing-style assessments.
For most organizations, the best approach is a combination of both. SAST helps you build secure software; DAST ensures it remains secure in the real world.
How to combine DAST and SAST for full application security
Modern AppSec programs are moving toward a unified testing model **that integrates DAST and SAST into the same pipeline to cover the entire application lifecycle.
Here’s how to do it effectively:
Integrate SAST early in the SDLC
Embed SAST tools directly into IDEs and CI pipelines so developers can fix issues as they code.
Automate DAST scans in later stages
Run DAST after builds and before deployment to catch runtime vulnerabilities.
Establish unified reporting
Correlate results from SAST and DAST for a consolidated vulnerability view, reducing false positives and streamlining remediation.
Adopt DevSecOps practices
Encourage collaboration between developers, QA, and security teams to maintain security ownership across all phases.
Prioritize vulnerabilities
The vulnerabilities discovered by DAST and SAST should be prioritized depending on risk, and the highest priority vulnerabilities should be fixed first.
Leverage AI-based testing tools
Modern solutions use AI to prioritize critical vulnerabilities, simulate attack patterns, and continuously monitor application security.
Continuously monitor
Continuously monitor your application for new vulnerabilities, and re-run DAST and SAST scans as necessary.
Train your developers
To help them build more secure code, train your developers how to identify and address the flaws that DAST and SAST have found.
By combining both static application security testing and dynamic application security testing, organizations can ensure coverage from the first line of code to the final runtime environment, minimizing risk while maintaining speed and innovation.
Final thoughts
Both DAST and SAST are essential pillars of a robust application security testing strategy.
SAST empowers developers to build secure-by-design applications.
DAST ensures those applications stay resilient once deployed.
If your goal is to build trust, protect user data, and stay ahead of evolving threats, it’s time to think beyond one approach. Adopt a layered AppSec strategy that integrates DAST and SAST into your CI/CD workflows, and automate wherever possible.
In addition, incorporating a platform like Beagle Security into your pipeline can help you continuously run dynamic application security tests, identify vulnerabilities in real-time, and ensure your applications remain resilient throughout the development lifecycle. Check out our advanced 14-day trial or the interactive demo to see if we’re the right fit for your application.
FAQ
What is DAST in security testing?
Dynamic Application Security Testing (DAST) is a black-box security testing method that scans web applications in real-time to detect vulnerabilities like SQL injection and XSS without accessing source code, helping organizations strengthen their runtime application security posture.
What is SAST and why is it important?
Static Application Security Testing (SAST) analyzes source code and binaries early in the SDLC to find security flaws before deployment, making it essential for DevSecOps teams to build secure, compliant, and high-quality software.
What’s the main difference between DAST and SAST?
The key difference is that SAST tests code from the inside (static analysis), while DAST tests the running application (dynamic analysis).
Together, they offer a complete view of potential security risks across the software lifecycle.
Can DAST and SAST be used together?
Yes. Combining DAST and SAST gives comprehensive vulnerability coverage, helping global enterprises and startups alike detect both code-level flaws and real-world attack surfaces, leading to stronger DevSecOps pipelines.
Which is better for DevSecOps: DAST or SAST?
Neither alone. SAST secures code early, while DAST validates security in production. For DevSecOps success, especially in fast-scaling SaaS or enterprise environments, integrating both ensures continuous and holistic security assurance.