Web applications play a key role in determining the success of a business. Many companies solely depend on web applications for their business, offering a SaaS product for other customers and also building web apps for internal use.
Yet it’s a fact that many companies don’t know how to keep track of their web application security and improve it.
Content management systems (CMS) like WordPress, Joomla and website builders have made it easy for everyone to create a website. Most of the website owners forget the fact that the attack surface of internet-facing web applications is much wider and that they need adequate security.
Whenever a customer or visitor is on your website you have to make sure that their data is safe.
If you fail to keep your customers’ data safe, you could be at the receiving end of a cyber attack which can lead to huge business loss and it can also get you sued. You have to keep in mind that no methods can guarantee your web application will be safe from attackers forever.
In this article, we’ll be looking into certain best practices that will help you improve web application security and prevent being an easy target for cyber attackers.
Choose a secure host
Even if your website has top of the line security it won’t do you any good if you are not using a secure host.
Do some research and choose a hosting company which has a good reputation and does not have much downtime issues. It is also recommended to check whether they meet your other unique requirements depending on your business needs.
Some of the key points to consider while choosing a hosting server is:
Does the web host offer a Secure File Transfer Protocol (SFTP)?
Is FTP used by Unknown User disabled?
Does it use a Rootkit Scanner?
Does it offer file backup to a remote server?
How well do they keep up to date on security upgrades?
Whether they provide technical support whenever necessary.
Know your web applications and prioritize them
It’s quite surprising that most organizations are still unaware of how many web applications they have or where they are hosted.
It is important to have a list of web applications including your organization’s and other third-party applications and prioritize it according to the amount of damage that could be done if something goes wrong.
Secure your login pages using SSL (HTTPS) encryption
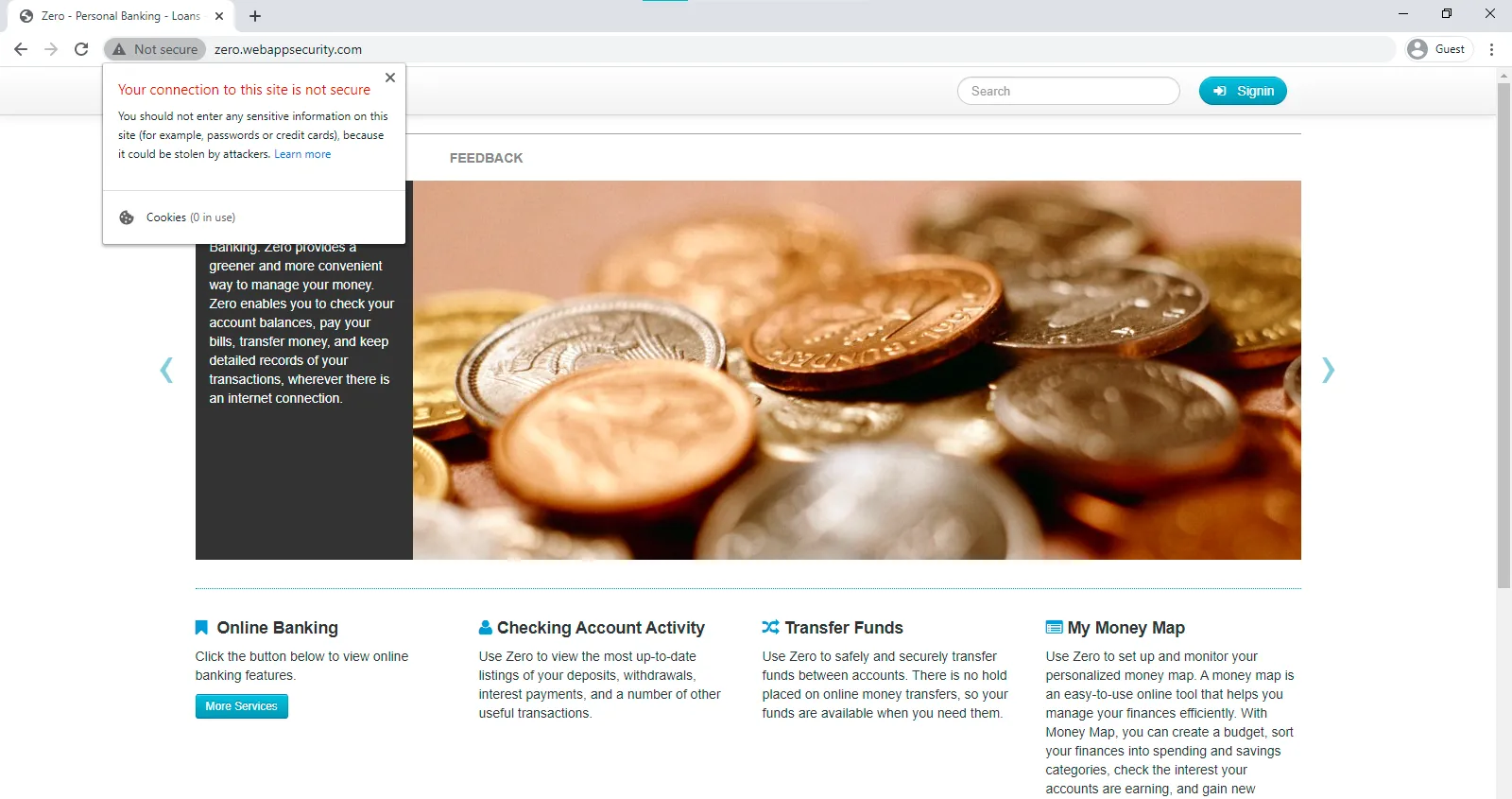
To keep your website safe, you need a URL with SSL (or even better TLS) encryption enabled.
HTTPS encrypts data sent from your browser to the web server and prevents a 3rd party from reading it while in transit. So, even if an attacker tries to intercept the data (manipulator-in-the-middle attacks), it will be useless.
If your website doesn’t have a valid SSL certificate, it is often flagged by most of the popular browsers as insecure. Browsers warn users not to send any personal, payment or password information in such cases.
Always sanitize and validate user input
Never trust any user input. This is a very common security mistake found on many websites.
If the user input data is not properly sanitized and validated, your website has a high risk of being targeted by attacks like XSS, SQL injection and other types of injection attacks. Sanitizing a user input may include the elimination of unwanted characters by removing, replacing, encoding, or escaping the characters.
Eg: <script>alert("XSS:);</script>
Html encoded <script>alert("XSS:);</script>
Validation is the process of ensuring that the user input data falls within the expected characters. You can create a whitelist or a blacklist to achieve this. In whitelisting, only the approved characters will be allowed and the rest of the characters will be rejected.
For example, if your website has a field for accepting phone numbers, you could whitelist numbers from 0 to 9. If the user tries to input any other character it won’t be accepted. On the contrary, in blacklisting, the list of defined characters will not be accepted as a valid input.
If possible, use whitelisting rather than blacklisting. When using a blacklist, you have to consider all the possible invalid options and if you miss something, you could expose your web application to hackers. This is why it’s much better to simply whitelist what is valid.
Have a good password policy
Whenever there is a talk about web application security, good passwords policies are always part of it.
Most companies nowadays have standard password policies to improve their online security. Even with these password policies, there are so many websites, databases, and programs, an admin or website owner has to keep password protected.
As a result, a lot of people end up using the same password in almost all places in order to remember their login information. But it’s a significant security mistake.
Nowadays, attackers use automated brute-forcing softwares to check whether sites are vulnerable. To protect against brute force, always use unique and complex passwords containing both uppercase, lowercase, numbers and special characters.
Use hard to guess passwords and also try not to use any personal information as passwords. If you try to keep a password in your memory, it is almost always an easy one. So, it is recommended to use a password manager for storing your passwords.
Also, if two-factor authentication (2FA) is available, always opt-in for it. Besides password, this will add an extra layer of security for your accounts.
Limit access rights and credentials
Whenever you think of giving access to your application, databases, etc, always follow the principle of least privilege (PoLP).
In simple terms, give users access only to data and tools they need to do their job. At first, you may feel comfortable giving high privileges to certain employees or your close friends thinking that they would use it with caution. Most of the time employees don’t think about website security when logging into the application or databases. This could pose a significant security risk to your application.
Make sure that a person has prior experience using your application before you give admin privileges to them. Check if they’re aware of how to avoid a security breach or a misconfiguration.
In most companies, employees are not permanent. If an employee leaves your company, you have to immediately revoke all the access given to that employee and also change the passwords if necessary. A best practice is to have a record of all employees with the privileges they have and what are the changes made by them.
Keep your website clean
Every database, application, or plugin on your website is another possible point of entry for hackers. You should delete any unwanted files or databases connected to your web application and close all unwanted open ports in your server that are no longer in use.
It is also important to keep your file structure organized to keep track of changes and make it easier to delete old files.
Ensure everything is up to date
It’s very important to keep all softwares, plugins and extensions you have up to date.
Attackers always keep an eye on the latest security vulnerabilities and know how to exploit them. If you don’t update regularly your company might become a likely target for attackers.
Always keep a note of every plugin or extensions you have and update whenever new versions are available. Be aware of the latest technologies and vulnerabilities found in the components you use by exploring different reputable web application security blogs.
Keep regular backups
Your web applications’ data is always at a constant risk. One of the best methods to keep your site safe is to have a good backup system in place.
Do not store your backups on the same server as your website is hosted on because if the server is under attack, the backups are also vulnerable. It is better to keep your backup on a home computer or hard drive. If possible find a climate-controlled off-site place to store your data and to protect it from hardware failures, attacks, and viruses.
Another best option is to backup your website in a cloud-based platform which makes storing data easy and allows access from anywhere.
It is recommended to use a solution where you can schedule your site backups automatically. Most of the content management systems have plugins or extensions that can automatically backup your website. Also, make sure your solution has a reliable recovery system too.
By doing this, you can restore files from any point to any other point you want to before a virus or ransomware wrecks havoc.
Make sure to tweak the default settings of your CMS
It is recommended not to run your CMS with default configurations. These configurations include default usernames/passwords, user permissions, login attempts etc.
Attackers use automated bots to scan websites. If your website is running using defaults usernames or passwords or with any misconfigured default settings, then your website will become a likely target.
For example, WordPress and other popular CMS platforms come with a default username “admin” and a password “password”.
The default login page of a WordPress website will be like example.com/wp-admin or example.com/wp-login.php. By default, WordPress doesn’t limit login attempts which could result in a brute force attack. Another overlooked security misconfiguration is specifying file permissions. Each file has three permissions which are represented by a number.
Read (4): View or read the file contents.
Write (2): Change the file contents.
Execute (1): Run the program file or script.
Other than these default file permissions there are also three user types.
Owner – Often, the creator of the file, but ownership can be changed. Only one user can be the owner at a time.
Group – Each file is assigned to a group. Users who are part of that specific group will gain access to the permissions of the group.
Public – Everyone else.
Assign file and user permission accordingly and never keep the default permissions as it is because at some point you may run into security issues.
Run security tests on your website for vulnerabilities
You should perform security checks and scans regularly if you want to stay on top and improve web application security.
It is recommended to perform a security scan at least once in a month and after each major changes, upgrades or downgrades you do to your website. You can use an automated penetration testing tool for this like the one we offer at Beagle Security.
Get professionals to “hack” your application
You should consider hiring professional hackers to try to penetrate your application if your business revolves around a web app that your company is selling or is using internally.
It’s very difficult to stay on top of web application security on your own. White-hat hackers can help you identify and fix the vulnerabilities present in your website before a real attacker finds and exploits it.
Also, instead of hiring professional hackers from a firm, you could organise a bug bounty program where you pay a reward to someone who finds a vulnerability in your web application.
Closing Thoughts
Nowadays companies mainly depend on web applications for their business.
Every website owner assumes that their website is safe and secure and forgets how exposed their applications are. Creating a website is very easy but keeping it secure is the difficult part.
It’s quite surprising how many options companies have for improving web application security but they hardly take the right measures.
Interested in using an automated web application penetration testing tool? Schedule a demo with us to know how Beagle Security can help you keep your web application secure.