
Cyber threats seem to be everywhere in this digital era. Viruses, malware, ransomware, trojans, phishing and a lot more make a never ending list of cyber threats. But one of the most prevalent threats out there that often gets overlooked is manipulator-in-the-middle (previously referred to as ‘man-in-the-middle’) attack.
While using the internet, we expect our communications to be confidential and not to be changed or tampered while in transit. When you are submitting some sensitive data to a web application, you rely on the assumption that:
everything you have entered is valid,
all the data reaches the server in its correct form, and
third parties cannot see, intercept or change your data.
But the fact is that a man-in-the-middle (MITM) attack breaks either one of the last two assumptions or both.
If the connections you make to websites and online services are not secure, you could be vulnerable to security risks such as phishing, fraud, impersonation, malware, and many others.
The Beginning and The Present
Intercepting and altering communication has happened for centuries, and the advent of the internet and further development has made it easier than ever for criminals to inject their interests into private transmissions.
During the late-16th century, letters related to an assasination plot against Queen Elizabeth I of England by Mary Stauart and her fellow conspirators were intercepted, decoded and modified by a cryptography expert named Thomas Phelippes. This happens to be one of the earliest MITM attacks on record.
In 2018, Russian spies attempted a MITM attack on the headquarters of the Organisation for the Prohibition of Chemical Weapons (OPCW).
In 2019, the national government of Kazakhstan attempted to introduce an internet surveillance system. The goal of the State security officials was to protect Kazakh users from hacker attacks, online fraud and other kinds of cyber threats. The certificate allowed users’ traffic to be intercepted by the government, circumventing encryption used by email and messaging applications.
Recently, the personal data of more than 12,000 Indian blood donors were on offer on the clear web for free. It was found by risk monitoring firm CloudSEK.
The leak might have been possible because of an unsecured HTTP site that was intercepted by third parties or an exposed database or cloud storage bucket, or even a phishing campaign that succeeded in accessing system admin credentials.
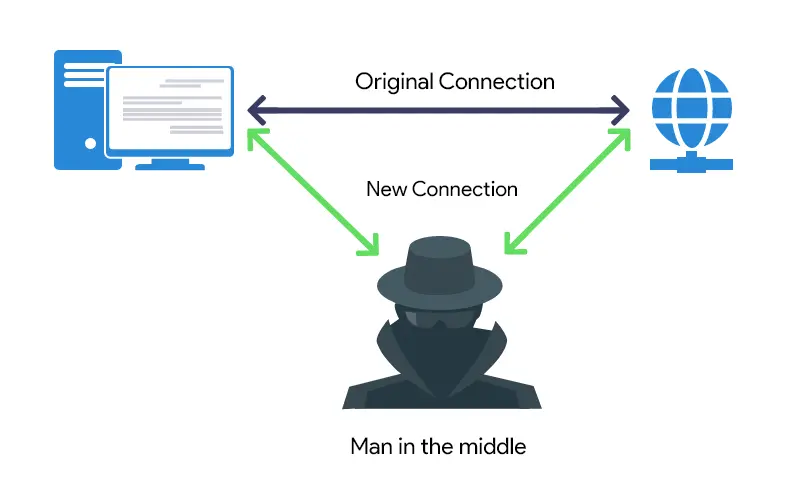
MITM attacks usually take two forms:
The first is where an adversary may want to read the content of a message which is often said to be an attack on confidentiality.
The second would involve the adversary changing the content of the message or otherwise modifying the communication which is said to be an attack on integrity.
Man-in-the-middle attacks involve the physical proximity to the intended target or it involves a malicious software or malware. For example, the client or user receives a mail which includes a link to a bank site, from the “man-in-the-middle“ or the attacker which appears to be a legitimate one.
When you click on the link and log in, you are actually passing your credentials and data to the attacker. And this type of attack includes phishing also.
Types of Man-in-the-Middle Attacks
A MITM attack is essentially an eavesdropping situation in which a third party or an adversary secretly inserts itself into a two-party conversation to gather or alter information. MITM attacks can affect any communication exchange, including device-to-device communication and connected objects (IoT).
Generally, man-in-the-middle attacks can be categorized into two:
Active session attack
During an active session attack, the attacker stops the original client from communicating with the server and then replaces himself within the session.
From this point onwards, the attacker will be communicating with the server and he will be able to do anything that a normal user can do. He could tamper the data or collect sensitive information that may have a potential impact later.
Passive session attack
In a passive session attack, the attacker monitors the data flowing across the network without interrupting the actual communication. The intruder eavesdrops the communication but does not modify the message stream in any way. He could collect all the data passing through the network which may cause an active attack later.
Techniques Used in Man-in-the-Middle Attacks
Some of the common man-in-the-middle attack techniques used are:
Rogue Access Point
A rogue access point is a device that is operating on the network without the authorization of an administrator, posing a security threat. They are set up to trick computers that automatically connect to Wi-Fi by posing as legitimate public networks. These rogue networks often monitor traffic and steal sensitive information.
The attacker could use this rogue access point as a public Wi-Fi of a coffee shop to control and intercept every communication passing through that network.
Address Resolution Protocol (ARP) Spoofing
ARP is a communication protocol used to find out the MAC address of a particular device whose IP address is known. If a device wants to communicate with another device on the network, then the sending device uses ARP to find the MAC address of the device that it wants to communicate with.
And these ARP packets can be forged to connect with a device as a legitimate one which is referred to as ARP spoofing.
This allows the attacker to intercept, modify, and drop the incoming messages.
MITM by ARP spoofing is done by exploiting two security issues. The first security issue is that each ARP request or response is trusted. As every request and response is trusted, you can just tell any device that’s on your network that you’re the router and that allows further communication.
The second one is that the clients can accept responses even if they didn’t send a request. Ultimately, you can respond to them as you are the router and could connect with them without the device sending any request.
Domain Name System (DNS) Spoofing
Domain Name System (DNS) spoofing is a technique that tricks a user to a bogus website rather than the real one the user intends to visit. The website will appear to be the real one and you may think you’re visiting a safe, trusted website when you’re actually interacting with a fraudster. The attacker’s goal is to divert traffic from the real site or capture user login credentials and other data.
DNS spoofing is done by replacing the IP addresses stored in the DNS server with the ones under the control of the attacker.So, whenever a user tries to access a particular website, they get directed to the malicious website placed by the attacker in the spoofed DNS server.
Email Hijacking
Email hijacking happens when attackers compromise and gain access to a user’s email account and watch communications to and from the account.
When an opportunity arrives, for instance, if the user is exchanging funds or any other data with another party, the attacker takes advantage of the situation by attempting to intercept the funds and transfer it to their own accounts.
Attackers can also use the email to take over other online accounts tied to the email account.
Internet Control Message Protocol (ICMP) redirection
ICMP is used by network devices, like routers, to communicate with the source of a data packet about transmission issues. For example, it might report to the host that a requested service is not available or that a host or router could not be reached.
In order to establish a successful MITM attack, the attacker looks for the network hosts that are down. When these hosts are pinged by other nodes in the network, the attacker will respond to them by sending a successful ping message.
And in this way, the attacker can forge ICMP-redirect packets in order to redirect traffic to himself which eventually results in gathering all data passing through it.
Dynamic Host Configuration Protocol (DHCP) spoofing
DHCP dynamically assigns IP addresses. In DHCP spoofing, an attacker’s computer is issued as a DHCP server and sends forged DHCP acknowledgments to any connecting nodes.
The attacker can supply its own IP address for the default gateway address or DNS server in forged DHCP requests hence executing a man-in-the-middle attack.
SSL stripping
SSL/TLS is a secure cryptographic protocol used to communicate sensitive information. The protocol’s security is established by creating an encrypted connection between two parties.
When a user enters a domain name or when an unsecured HTTP request is sent, the server responds via HTTP and then redirects the user to HTTPS.
The user then sends a secure HTTPS request, and the secure session is initiated. In order to strip the SSL, the attacker intervenes in this redirection of HTTP to HTTPS and allocates himself between the server and client. While the victim and attacker will be in an unsecured connection, the attacker maintains an HTTPS connection with the server.
How to Prevent Man-in-the-Middle Attacks
MITM attacks can be detected or prevented by two means: authentication and tamper detection.
Authentication
Authentication provides a degree of certainty that a given message has come from a valid source. A public key infrastructure, such as TLS, can harden Transmission Control Protocol (TCP) against MITM attacks.
Implementing multi-factor authentication, pre-shared key authentication or certificate-based authentication makes it difficult for attackers who intercept messages to decrypt them, or construct fake messages for communicating with others.
Tamper Detection
Tamper detection checks whether a message has been altered or not and ensures that the data is safe from corruption. This checks the integrity of the message by comparing the equivalent hash of the message sent by one user to the other one which can also be encrypted.
Best Practices to Stay Safe from Man-in-the-Middle Attacks
It is rarely possible for those affected to recognize whether a man-in-the-middle attack has occurred or not. But, MITM attacks can be avoided by following some best practices.
For Individuals
Make sure that you always access websites through an SSL/TLS secure connection.
Verify that a website’s SSL certificate is active and issued by a trusted certificate authority.
Avoid using freely accessible VPNs or proxy servers.
Always use the latest version of your web browser and make sure that your operating system is up to date. Mozilla has added an HTTPS-Only Mode to the latest Firefox browser release in a bid to protect users from unencrypted web connections.
Think twice before connecting to free wireless hotspots in public locations such as coffee shops, hotels or airports. If you see something odd, notify the network owner.
Even if you are using public Wi-Fi hotspots, don’t enter any sensitive data like account credentials and try to avoid downloads and online payments.
Remember to not ignore Bluetooth. A recent “BLURtooth” flaw allows attackers within wireless range to bypass authentication keys and open the door to a man-in-the-middle attack utilizing the issues in the pairing process for Bluetooth 4.0 through 5.0 implementations. Users with Bluetooth-capable devices should install any available updates from device and operating system manufacturers.
Use complex passwords, update them frequently, and use separate passwords for each application. Refrain from reusing old passwords.
Do not click on links in emails from unknown senders that might lead you to a malicious site. Even if email links from unknown senders look legitimate, observe thoroughly before using those links. It may lead you to become the victim of phishing.
For organizations
Employees should not be allowed to use public networks for any confidential work. And it will be good if separate networks are used for internal work, employees, outsiders, etc.
Implement virtual private networks (VPNs) to establish secure connections from your business to online applications. And ensure that employees securely connect to your internal private network from remote locations. VPNs and HTTPS both send a scrambled form of your data across the network.
Even if attackers intercept it, they won’t be able to derive original data from it. Use the latest version of high-security web browsers such as Chrome, Internet Explorer, Firefox, or Safari and enforce the use of HTTPS.
Secure your email using SSL/TLS to protect messages in transit, and consider using PGP/GPG encryption to protect them at rest as well.
Implement multi-factor authentication, firewalls and intrusion detection system (IDS) to monitor your network. You’ll be alerted about unusual or malicious traffic flow.
For website operators
Protect your customer data by securing websites with secure mechanisms for customer logins using an up to date SSL certificate from a reliable certificate authority.
Additional securing mechanisms like multi-factor authentication should be implemented.
Inform your customers that you never ask about login data or any other data through emails and avoid hyperlinks in customer emails.
And most importantly, always ensure that your website is free of security threats by regular auditing and testing it.



