Cyber safety for businesses has grown increasingly crucial as more people worldwide work remotely. Virtually all business enterprises, regardless of size, are subject to cybersecurity concerns because of the ongoing growth in cybercrime.
This constant threat necessitates a system that provides consistent and reliable security testing.
Penetration testing has been acknowledged as an absolute necessity by most security leaders to analyse an organisation’s defences. But pen tests can only provide a snapshot of this defence.
A continuous evaluation of the organisation’s security cannot be obtained.
This is where continuous penetration testing comes in.
What Is continuous penetration testing?
Continuous penetration testing involves regular vulnerability assessments and constant monitoring of software assets.
A constantly evolving and varying cyberspace means that attackers are constantly changing how they approach exploiting new vulnerabilities. Therefore, regular assessments must be undertaken in response to changes in a network or the threat landscape.
This form of testing can simulate more realistic, real-world-like conditions.
Regular updates to your applications also suggest that new vulnerabilities may arise in its security posture. Therefore, it is necessary to identify them before they start creating problems. Continuous pentesting can help with this.
The first step of continuous testing is a full penetration test from which a baseline is obtained. This baseline helps to identify vulnerabilities that currently exist with the application. Continuous monitoring is then combined with demand-based testing to provide consistent and reliable security testing.
Benefits of continuous penetration testing
Easier on the wallet: Addressing security issues consistently means that time spent on unplanned work can be cut down drastically, thus improving efficiency and being cost-effective.
Be in trend: The fast-changing cyber-scape means that it is best to be aware and protected against the latest trends of attacks and attackers. Continuous penetration testing helps with exactly this by keeping you aware of vulnerabilities and preventing them from causing problems later.
Know your armour strength: Consistent analysis of vulnerabilities means that you have live knowledge of your armour strength i.e., how secure you are. This in turn improves your adaptability to face issues that may arise.
Best of both worlds: Continuous testing supplies all the advantages of automated security tools while also having the meticulous detailing of manual penetration testing.
Effectively address regulatory compliance requirements: Organizations are under pressure to adhere to a myriad of information security-related compliance rules, and pentesting is usually necessary.
Implementing continuous penetration testing
Continuous penetration testing often begins with a baseline penetration test of your application to obtain the first report. This is similar to normal penetration testing.
An automated security monitoring system keeps track of new assets and other changes that may arise.
This is combined with on-demand manual penetration testing depending on factors such as changes to the environment that may have introduced new vulnerabilities or risks. The time-frequency for these tests is based on user requirements.
All of this is combined with the CI/CD pipeline to initiate tests whenever new code is updated or a change is made to the application.
So, what’s the best way to start securing your applications through continuous penetration testing?
Well, that’s where a solution like Beagle Security comes into picture.
Beagle Security facilitates your continuous penetration testing needs in two ways:
1. Integrating continuous penetration testing into your CI/CD pipeline
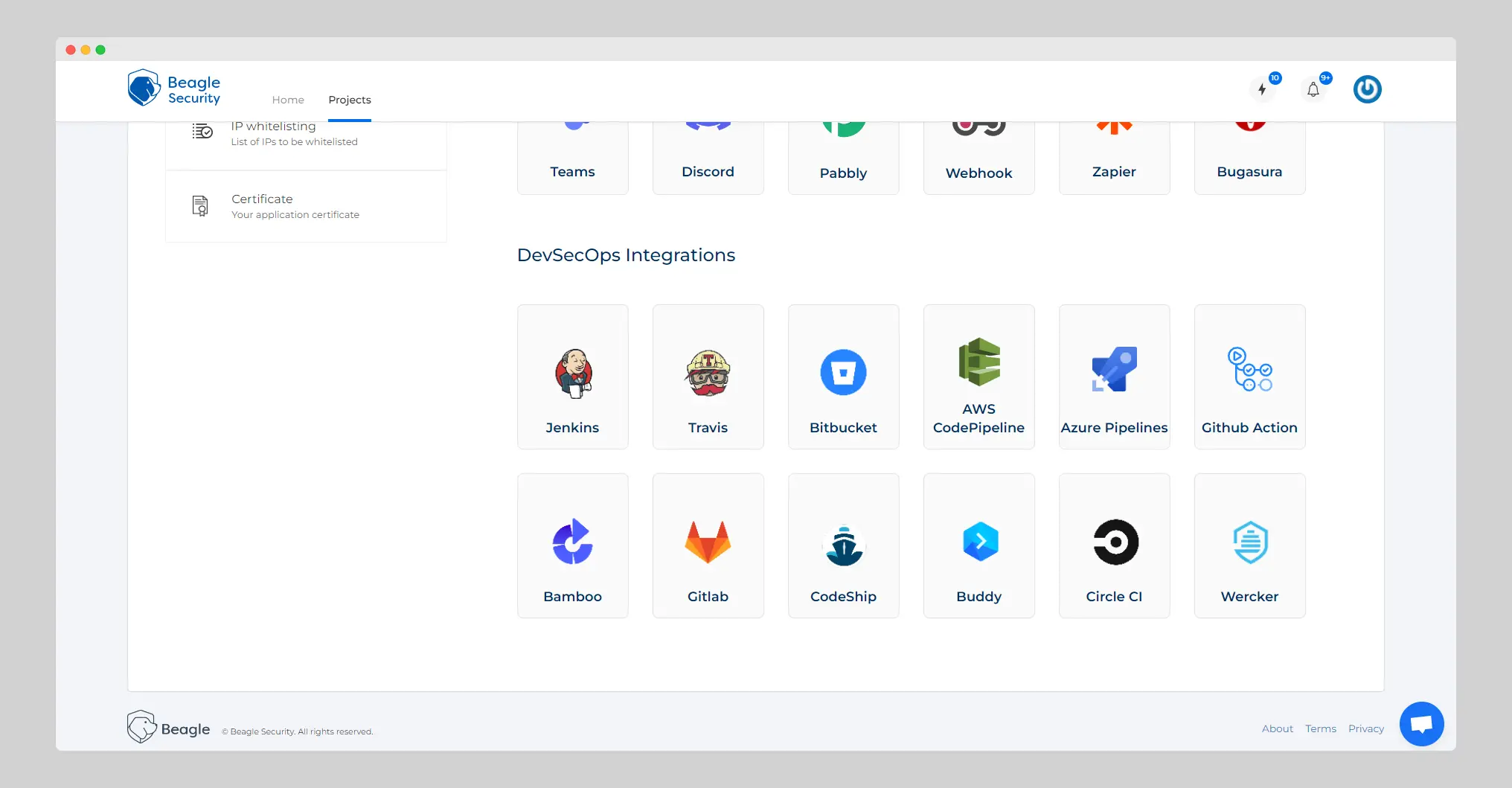
Beagle Security gives you the capability to integrate security testing into your CI/CD pipeline.
Beagle Security can help you turn your DevOps process into DevSecOps, allowing developers to easily understand the potential risk to their applications and decide the measures that need to be implemented.
This allows you to find security issues earlier in your development lifecycle and improve your operations. Integrating pentest tools into your CI/CD pipeline makes vulnerability assessment an organic aspect of the development cycle.
Check out all the integration opportunities we provide to make your life easier here.
2. Schedule continuous penetration tests on a recurring basis
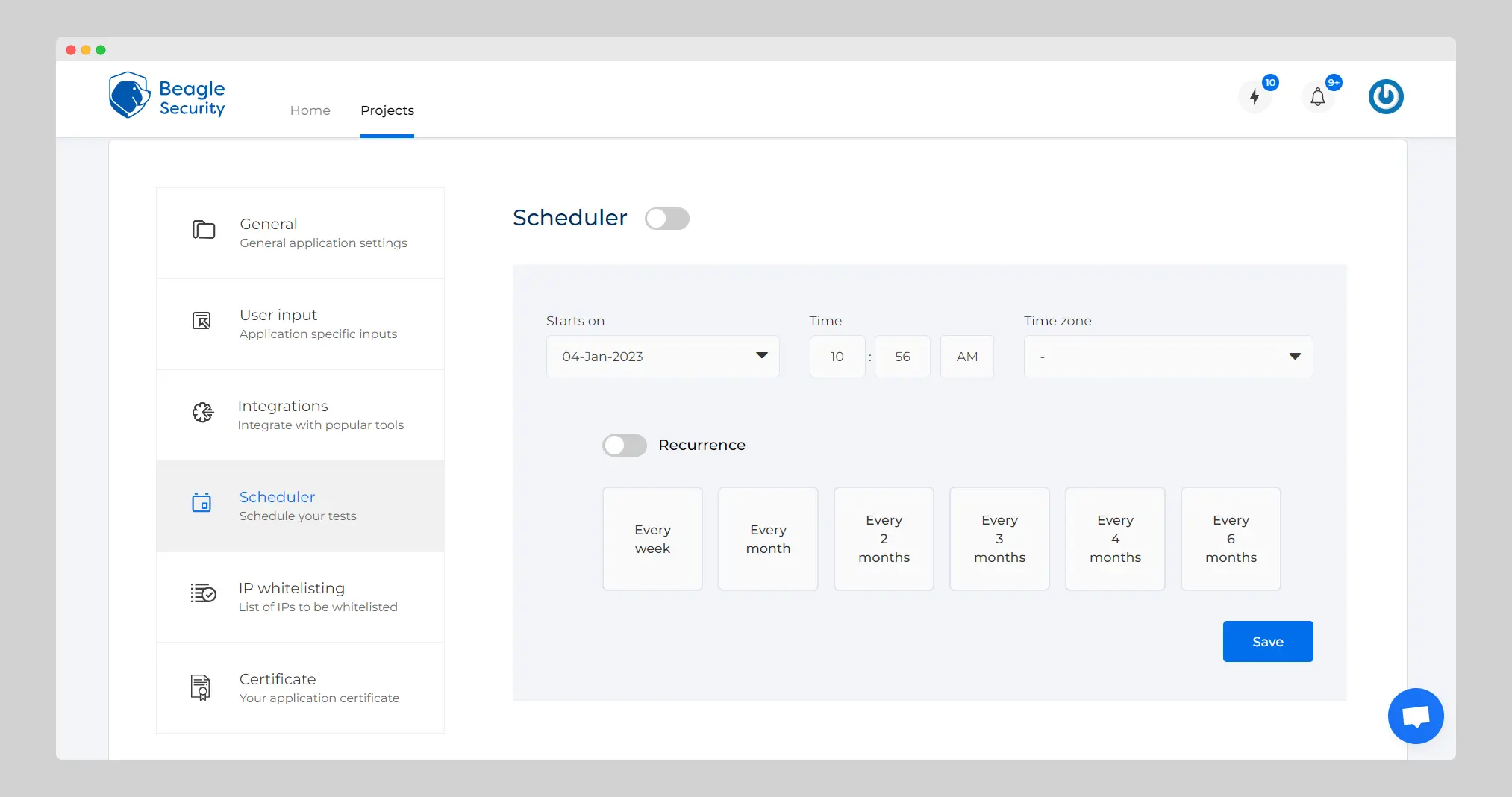
Scheduling your tests gives you better efficiency and a lot less stress. Scheduling tests w.r.t changes made to the application ensures that possible new vulnerabilities are found and delt with before they can cause damage.
The Scheduler is one such feature in Beagle Security’s arsenal that will help you obtain the best results from a penetration test.
It provides you the ability to schedule tests according to your requirements with a time gap as low as a test a week to bi-yearly tests.
The ability to choose the time and time-zone also allows you to schedule the tests during times when your servers are less busy, improving the overall efficiency of the test.
Beagle Security’s continuous penetration testing service amalgamates two crucial factors in security testing: the meticulous nature of manual penetration testing with the help of a human-like automation AI engine.
This helps create the perfect mixture to meet your security testing requirements when it comes to continuous penetration testing.
It is necessary to understand that the word ‘continuous’ here does not imply that there is a constant evaluation hourly or even daily.
Such a mode of testing would not be practical or cost-efficient.
Continuous pentesting leverages the use of automated security monitoring tools along with decisively scheduled or on-demand penetration tests to provide optimal security to your applications.