What is Social Engineering?
Social engineering refers to the act of taking advantage of psychological manipulation to influence people to perform specific actions or share confidential information. Social engineering attacks are often used by bad actors for fraudulent purposes or financial gains.
It usually unfolds as a series of steps that a person takes against their best interests without even realising it.
For example, a social engineering attacker can pose as an IT support employee at an organisation and easily trick an employee into giving his password.
The human instinct of trust helps an attacker to manipulate a user’s behaviour. It is essential to know who to trust because if you’re not vigilant, you can always be one step away from sharing confidential information to a cybercriminal posing as someone you know.
Common Types of Social Engineering Attack Techniques
Anybody with an understanding of human psychology can use it to their advantage to influence the cognitive biases people exhibit. There’s a lot of red flags we hardly notice.
Let’s take a look at some of the most commonly performed social engineering attack techniques.
Phishing
Phishing remains to be the most common social engineering tactic in use. It occurs when an attacker disguises as a trusted entity or individual and obtains sensitive information.
Phishing scams usually unfold through emails, and text messages creating a sense of urgency or fear in victims.
The goal is to trick a recipient to click a specific link or download an attachment that can lead to the revealing of a person’s sensitive information.
Nearly a third of all breaches that happened in the past year involved phishing. Attackers are also exploiting users with phishing campaigns related to the Covid-19 pandemic.
The earliest attempts of phishing attacks started in the 1980s and by the 2000s it started growing in numbers year after year.
Phishing Attack Example
The primary aim of a phishing campaign is to lure a victim into taking the bait. In the case of an email, this starts with the email subject line.
Some classic phishing emails have stood the test of time and still succeed in making people take action.
For example, online service providers notify users with an email when they detect unusual activity on their user’s accounts. Attackers have made similar email copies that look legitimate and are capable of making someone take action if they weren’t paying close attention.
Consider this fake Microsoft security notice which looks almost identical to an actual alert from Microsoft concerning “unusual sign-in activity”.
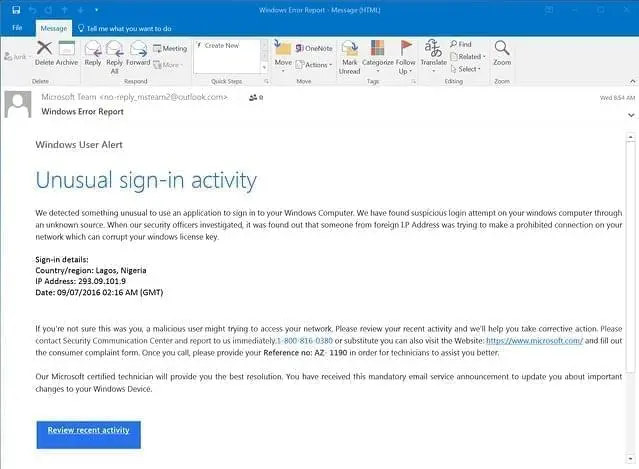
Now this email looks incredibly realistic because it includes links to the Microsoft website. Ironically, they have also mentioned that a malicious user might be trying to access the user’s network.
But the real lure here is that they have not included any malicious link in the email body.
Instead, they ask a user to call on an official looking toll-free number. This is easy to spoof. Attackers just buy an 800 number and route the calls wherever they want.
If a user calls, a ‘technician’ will assist them and ask to install remote access and troubleshooting software. They will, in turn, find some security issues and sell a software program to clean up the problem ending up with a person’s credit card number.
Pretexting
Pretexting is a social engineering tactic in which an attacker uses a convincing story as a pretext to gain the trust of an individual.
In pretexting, the attacker’s motive is to gain information by either acting as someone in authority or as a colleague looking to help. It can either involve an attempt to impersonate people or create a whole new identity and weave a story around that fictional character.
A solid pretext is an essential part of building trust with a person and making someone comfortable to disclose information they normally would not.
The main difference between phishing and pretexting is that fear and urgency are usually used for phishing attacks whereas the foundation of pretexting is building trust with a victim and getting the necessary information from them.
It all comes down to being prepared to answer all the questions that a victim might put forward and not allowing them to get suspicious.
Pretexting Example
Stanley Mark Rifkin pulled off one of the biggest bank heists in American history using pretexting techniques. He walked away from the Security Pacific National Bank with $10.2 million without touching a single dollar or holding anyone at gunpoint.
Rifkin worked for a company under contract to develop a backup system for the Security Pacific National Bank wire transfer room. While on the job, he learned of the wire transfer procedures and discovered that the wire transfers were authorized with a numerical code that changed daily.
It used to be posted in a secure room that only “authorized personnel” had access to.
In the autumn of 1978, he visited the Security Pacific National Bank, where bank employees recognized him as a contract worker. He made his way towards the bank’s wire transfer room and managed to talk his way into the room where the bank’s secret code of the day was posted.
He memorised the code easily and walked away without leaving any room for suspicion.
He rang up the bank transfer room later and impersonated as Mike Hensen, an employee of the bank’s international division. He then ordered a transfer of $10.2 million wired to the Irving Trust Company in New York and provided the secret code numbers to authorize the transaction.
Nothing about the transfer appeared to be out of the ordinary and Rifkin walked away with $10.2 million.
The bank never knew about the scam until FBI agents informed them of the robbery later on and Rifkin got caught while attempting other ambitious things with all the money.
Rifkin pulled off a well thought out plan with a solid pretext.
He built a good storyline with the things that were familiar to him to carry out one of the largest bank thefts in US history.
Quid Pro Quo Attack
A quid pro quo attack is a type of attack that promises a benefit in exchange for information. It is a variant of baiting that promises a victim a service or benefit based on the execution of a specific action.
One of the most common scenarios involves fraudsters calling random numbers at a company and offering IT assistance. Eventually, they will find someone with a legitimate problem and offer to help them solve it.
During the process, the attacker will have the user type commands that give the attacker remote access or allows him to launch malware. Giveaways or offers to be part of research studies might expose you to a similar attack.
Quid Pro Quo Attack Example
Psychologists at the University of Luxembourg did a large-scale study to investigate how people can be manipulated to share their passwords with complete strangers in return for small gifts.
When we receive something nice from someone we automatically feel the need to return the favour. This universal principle of reciprocity is precisely what psychologists tried to exploit to encourage people to divulge their passwords.
Researchers asked random passers-by about their attitude towards computer security. They found out that giving a small gift increased the likelihood of participants sharing their password. When a bar of chocolate was given beforehand, a total of 43.5% of respondents shared their passwords with the interviewer.
The willingness to divulge passwords increased further when the chocolate was offered immediately before the participants were asked to disclose their passwords.
The study showed how easy it is to manipulate people with a simple act of reciprocity.
Watering Hole Attack
A watering hole is a targeted attack that works by identifying websites that users within a targeted organisation or an entire sector visit and infecting them with malware.
Attackers capitalise on the trust users have in specific websites they regularly visit. It involves careful planning to gather information about websites that the targets often visit and finding vulnerabilities in them.
This will allow an attacker to inject code that may infect a visitor’s system with malware. The end goal of a watering hole attack is to infect a user’s computer and gain access to a particular organisation’s network.
As with targeted website attacks, the malware may be delivered and installed without the target even realising it, also known as a ‘drive-by’ attack. Users don’t need to click on any links or download any files to their computer.
Given the trust a victim has in a watering hole website, the malicious file could also be something a user downloads consciously without realising what it contains.
The malware will usually be a Remote Access Trojan (RAT) that allows an attacker to gain remote access to a victim’s system.
Watering Hole Attack Example
The International Civil Aviation Organization (ICAO) was a victim of a large scale watering hole attack back in 2016. Attackers compromised two servers at the ICAO as well as accounts of the mail servers, domain admin and system admin.
The attack left not just the ICAO vulnerable but also all its partners worldwide.
Hackers had access to the passwords of more than 2000 ICAO system users and could read, send or delete emails from any user.
It turned out that the attackers had set up a chain of watering holes leading to the string of breaches that happened.
Tailgating
In a tailgating attack, an attacker simply follows an authorised person trying to seek entry to a restricted area. This is often done by following a person who has legitimate access.
A tailgating or piggybacking attack can either be electronic or physical. It is probably one of the simplest forms of social engineering techniques. It is as simple as convincing an authorised person that you’ve forgotten or lost the appropriate identity token.
Tailgating Attack Example
Tailgating attacks came into attention when a series of weaknesses were exposed in airport security. Officials from the US Federal Aviation Administration (FAA) repeatedly breached security measures at major airports.
In fact, they penetrated secure areas at major US airports more often than they failed. Investigators made 173 attempts to breach airport security between November 1998 and April 1999 and they came out successful in 117 cases - a whooping 68% success rate.
Following airport and airline staff through controlled areas happened to be the easiest route to get through, and it uncovered the state of airport security in the US.
How to Stay Protected from Social Engineering Attacks
Human instincts of curiosity and fear allow an attacker to exploit and draw victims into a cleverly set bait easily. Thinking twice before allowing someone to manipulate you is a skill we need to spend more time mastering.
This comes in handy, especially in a social engineering perspective.
When it comes to most things, we don’t get the bigger picture until we have first-hand experience. Being a victim of a social engineering attack is no different. We like to think we would never be tricked or scammed.
There are many things we can as an individual keep in mind to reduce the risk of being a victim to social engineering frauds.
In addition, organisations also need to take up the responsibility of educating their employees about the right countermeasures to protect themselves.
Keep the following in mind to stay protected from social engineering attacks:
Avoid giving out personal information to strangers via email, phone or text message and avoid clicking on attachments from unknown senders.
Use different passwords for different accounts. In the event of a compromise, you don’t want to make things easier for an attacker.
Consider using multifactor authentication for your personal accounts and also at the workplace. You’ll be able to protect your account even in the event of a system compromise.
Some offers are too good to be true and remember that nothing good comes for free. Be aware of what’s at stake.
If a message or call from an unknown source conveys a sense of urgency to share sensitive information, take things slow and think before you act. The key is to be in control of your actions.
Always keep all software up to date. Don’t delay or skip a software update, particularly security patches.
Think twice before sharing certain aspects of your life online. While most social engineering attackers don’t engage the victim deeply, some go to the extent of finding all that’s available online about a specific person.
Use spam filters meticulously for your email client.
Train employees to identify potential social engineering tactics at the workplace and counter them accordingly.
Conclusion
Social engineering attackers are capable of making the best out of perfectly normal situations and manipulate people to divulge critical information.
Being aware of the ways we can be influenced psychologically, and taking necessary precautions can go a long way in helping us stay safe in this digital realm.













