As a software engineer, ensuring the security of your web application is obviously one of the top priorities.
But did you know, there are some non-obvious factors that are commonly overlooked in the software security testing process?
In this article, we’ll introduce you to some aspects that can help you maintain robust security practices and how a bug tracker can help you achieve this seamlessly.
The cost(s) of overlooking systematic security practices
A 2022 data breach report by IBM found that companies spent an average of $4 million per data breach and this number has been growing 10% year over year.
In fact, the global spend on cybersecurity amounted to a whopping $71 billion in 2021. These numbers may seem like hard, cold stats but there are several real-life examples to learn from.
A few years ago, the founder & CEO of Bugasura.io, Pradeep Soundararajan, used a vulnerability in 7Zip to bypass a McAfee Intrushield while testing for a cloud based OS.
Had this vulnerability been discovered by a hacker, the company would have lost their next round of funding!
Much like the OS, you could save millions of dollars in security costs by including the below non-obvious practices that are frequently ignored.
How a bug tracker can be integral to your web application’s security
When it comes to development, the biggest non-obvious security threat is attention to detail and ignoring an issue.
Any uncovered vulnerability needs to be tracked to closure. Ignoring warnings or low level vulnerabilities is what leads hackers to look for a bigger door.
The next big non-obvious problem is - how do you close the issue fast.
This is where a bug tracker can make or break the deal for you. When picking a bug tracker for security testing check for these pointers below:
Capture the issue holistically
People are lazy to detail. This is where security bugs enjoy a larger life span.
Detailing is important. Setting a template of reporting a security bug is different from that of a functional bug.
A tracker that enables different templates is critical to making this happen.
During a security test, testers may identify vulnerabilities or insecure authentication mechanisms. These vulnerabilities can be tracked and prioritized using a bug tracking tool, and steps can be taken to fix them.
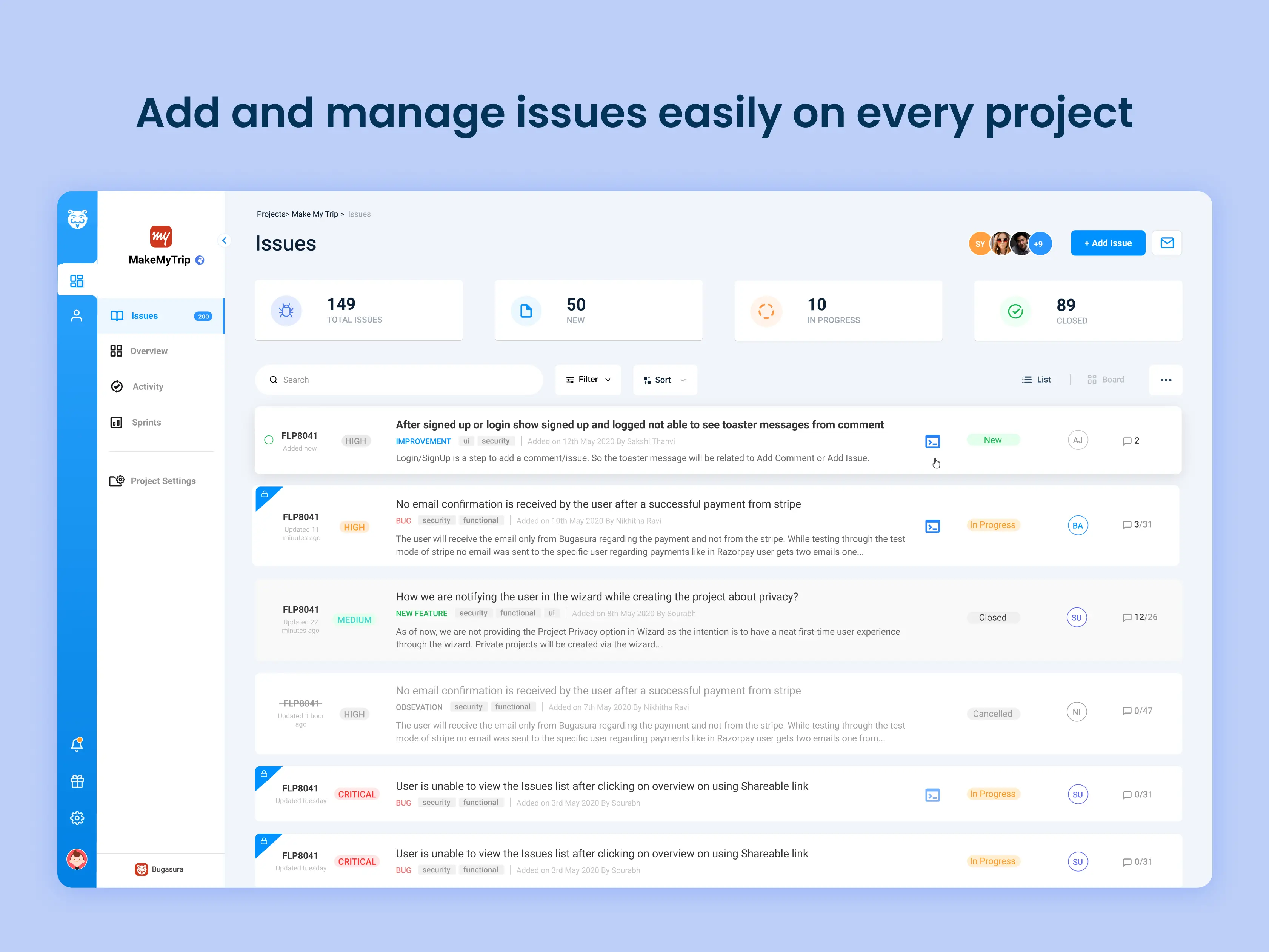
Adding and managing issues on Bugasura is extremely simple and effective.
A clean UI, robust filter mechanisms and customisable issue fields allow you to capture security bugs visually and contextually.
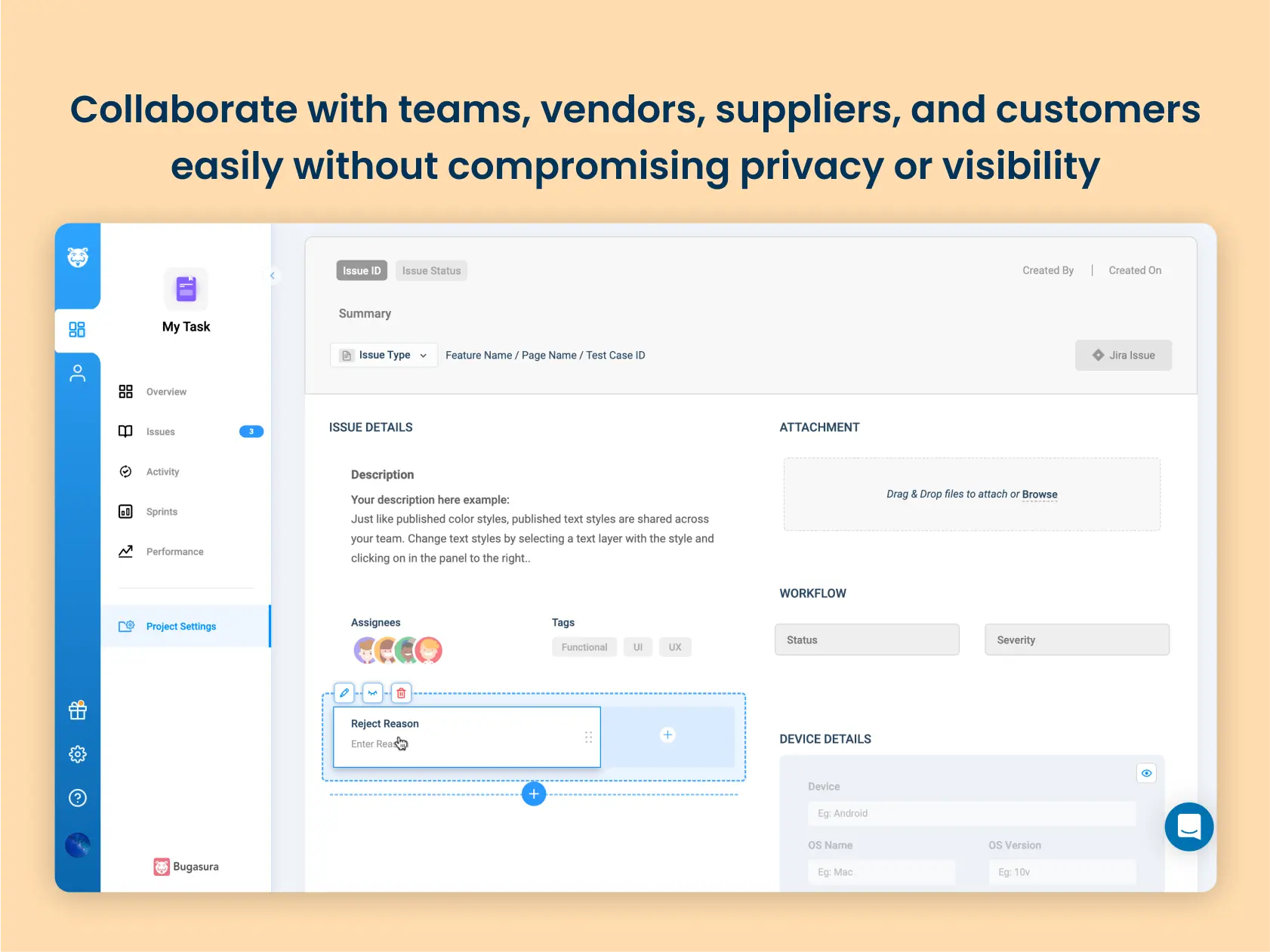
Bring stakeholders together
Many times, there are external stakeholders in an organization, yet internal and external members must collaborate to discover and resolve problems.
A bug tracking tool can be used to collaborate and coordinate efforts, ensuring that all potential security issues are thoroughly addressed.
There are several teams that may be involved in security testing, depending on the size and structure of the organization.
Involving multiple teams in security testing can help ensure that a wide range of perspectives and expertise are brought to bear on identifying and addressing vulnerabilities.
With the Bugasura public tracker, even your customers or bug bounty hunters can report issues to your team directly.
Document evidence and investigation on the same thread
Losing sight of the progress is also how security bugs enjoy a long life span giving the opportunity for hackers to take advantage.
When one hacker knows a vulnerability, they share it among other hackers to also take advantage. A tracker that makes it complex for people to track evidence is bad for closing such bugs.
To fix a security issue, it is important to have detailed documentation of the issue, including steps to reproduce it. A modern bug tracker like Bugasura can be used to document these issues and provide a clear record of the steps taken to resolve them.
Here are some good practices for documenting security issues in a bug tracker:
Use a clear and descriptive title: The title should briefly and accurately describe the issue, so that anyone reviewing the bug tracker will have a clear understanding of the problem.
Provide a detailed description of the issue: This should include information about the affected system or application, the specific vulnerability that was identified, and any steps that have been taken to reproduce the issue.
Include relevant information: This can include details such as the version of the system or application that is affected, the type of vulnerability (e.g., SQL injection, XSS), and any relevant log files or error messages.
Assign the issue to the appropriate team or individual: It is important to ensure that the issue is assigned to the team or individual who is responsible for addressing it.
Set the appropriate priority level: The priority level should be set based on the severity of the issue and the potential impact on the organization or its customers.
Close it fast: Security bugs can’t be kept open for long. Every minute is risk multiplied. A tracker that enables fast closure is what an org should pursue. Bugasura is built to help you achieve this. When integrated with Beagle Security, you can not only capture and document vulnerabilities but also provide context and information in a simple manner to close the issue faster.
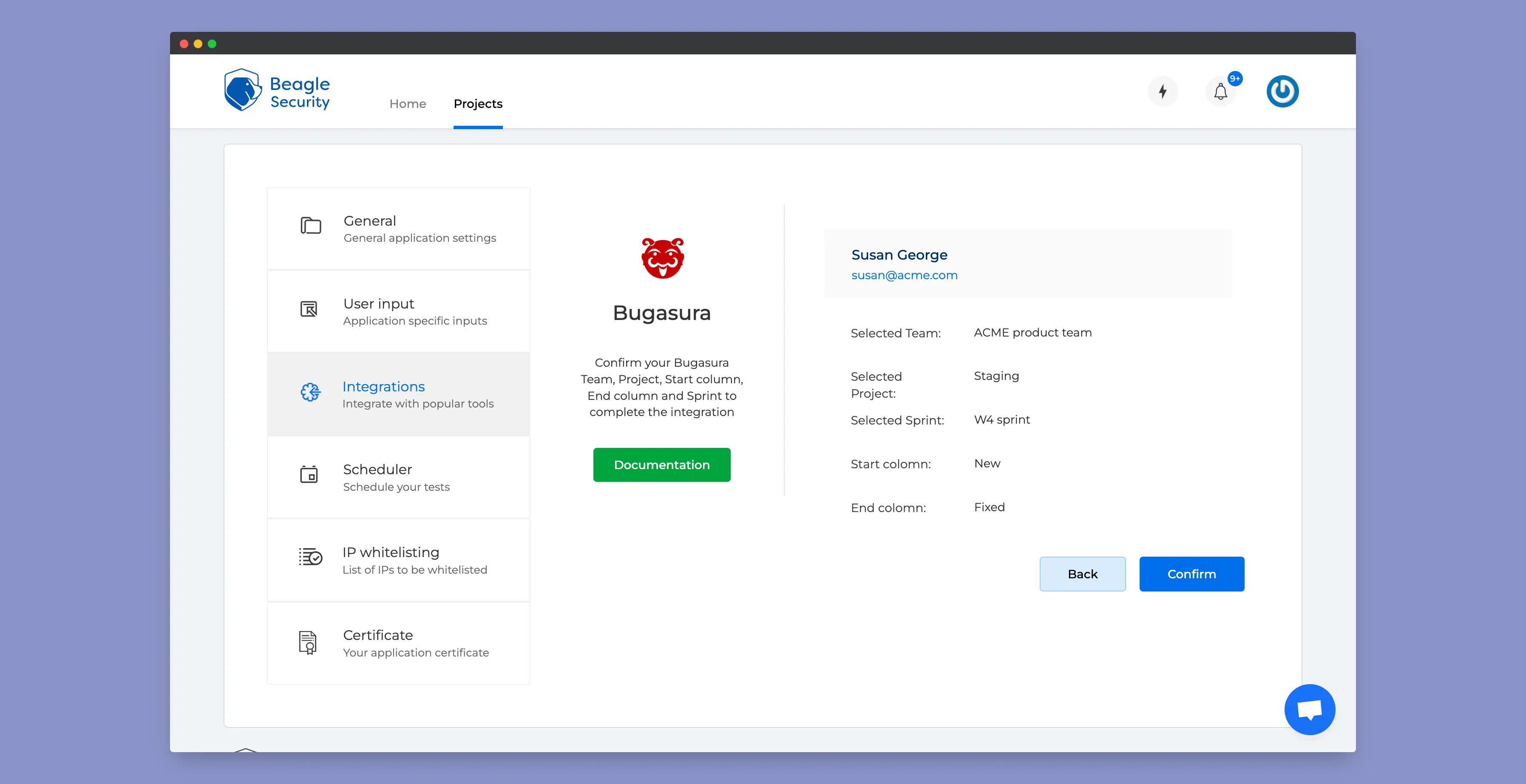
Are you serious about your security practices?
This integration was built to help you save money and build safer software for your customers. If you are serious about your software security practices, explore the integration and discover the value it offers. You can read more about the integration here.
Want to learn more about the latest trends that will shape application security in 2023?
We will be going LIVE with Rejah Rehim, co-founder of Beagle Security and Pradeep Soundararajan, Founder CEO of Bugasura.io soon. Stay tuned and do make sure to follow Beagle Security on LinkedIn for more updates on that.
Happy security cost savings to you!