Web application security assessment is the process of evaluating applications to identify risks and vulnerabilities and choosing the appropriate countermeasures to use.
With this, organizations are able to use security assessment methods to review their applications’ current security posture and decide what steps to take to protect their software from future vulnerabilities.
Four major steps for an effective security risk assessment
Identification: Identifying all the important technological infrastructure assets. After that, we determine what sensitive data these assets create, store, or transport.
Assessment: Implementing a method for assessing identified security threats to key assets and determining how to effectively and efficiently deploy time and resources to reduce risk following a thorough evaluation and assessment. The assessment strategy or methodology must be used to examine the relationship between assets, risks, vulnerabilities, and mitigating controls.
Mitigation: For each risk, we are required to define a mitigation strategy and set up security controls.
Prevention: Implementing tools and practices to prevent threats and vulnerabilities from affecting your company’s resources.
How to conduct an effective web application security assessment?
Following are some of the crucial components that make up an effective web application security assessment:
Well defined security policies
Web application security assessment alone does not guarantee applications to be secure. During each security audit, several granular vulnerabilities are discovered, none of which might not even require remediation.
This decision will be based on the well-defined and constantly evolving goals, objectives, and scope of security policies and processes.
Also, security policies and processes will define strategies, remediation procedures, incident response plans, patch management guidelines, and appropriate behavior.
Asset discovery and management
Application security asset management is the continuous, real-time identification of your organization’s IT assets and the potential security threats or loopholes that each one poses.
In the field of application security, you can’t secure something if you don’t know it exists. As a result, application security asset management has become an essential component of the foundation of cyber security operations in all types of businesses.
If an attacker uses a compromised resource to launch a broader attack, any device, resource, or service in your IT estate may be vulnerable to risks or vulnerabilities that result in a breach of the individual resource and your network as a whole.
Threat intelligence
Threat intelligence, also known as cyber threat intelligence, is data that helps an organization in understanding the threats focused towards it. This data is used to predict, prevent and identify cyber-threats attempting to exploit valuable resources.
Threat intelligence, when properly deployed, can assist in achieving the following goals:
Maintaining awareness of the most recurring threats, including weaknesses, targets, and bad actors.
Assisting you in becoming more proactive in the face of potential cyber security threats.
Keep executives, stakeholders, and users up to date on the current dangers and the potential consequences for the company.
Regular application scanning
Organizations require a web application scanning solution that can check for security flaws in web-based applications to prevent hackers from gaining unauthorized access to company information and data.
To prevent and detect breaches, organizations must regularly detect vulnerabilities, security gaps, weaknesses, defects, and other flaws in their applications, systems, third-party components, software, code, and other areas.
Pro Tip: The best step would be to let Beagle Security help you understand your security weaknesses and address them in the best possible way.
Penetration testing
Penetration testing, also known as a pen test, is a security exercise that employs a standardized testing process to expose an organization’s security flaws.
A penetration test can identify potential vulnerabilities in networks, applications, physical facilities, people, and other areas.
Penetration tests should be included in any organization’s security programme since they provide numerous advantages, including:
Detecting and eliminating vulnerabilities before they are exploited by cybercriminals.
Increasing cyber-resilience to ensure continuous business operations. Cyber attacks frequently result in the organization being rendered inoperable for an extended period of time.
Impact analysis
An impact analysis is performed by an organizational official to determine the extent to which changes to the information system have impacted the system’s security state.
Application security risk assessment
A security measure that can quantify the risk posed by applications is required to make decisions in security management and counter-attacks.
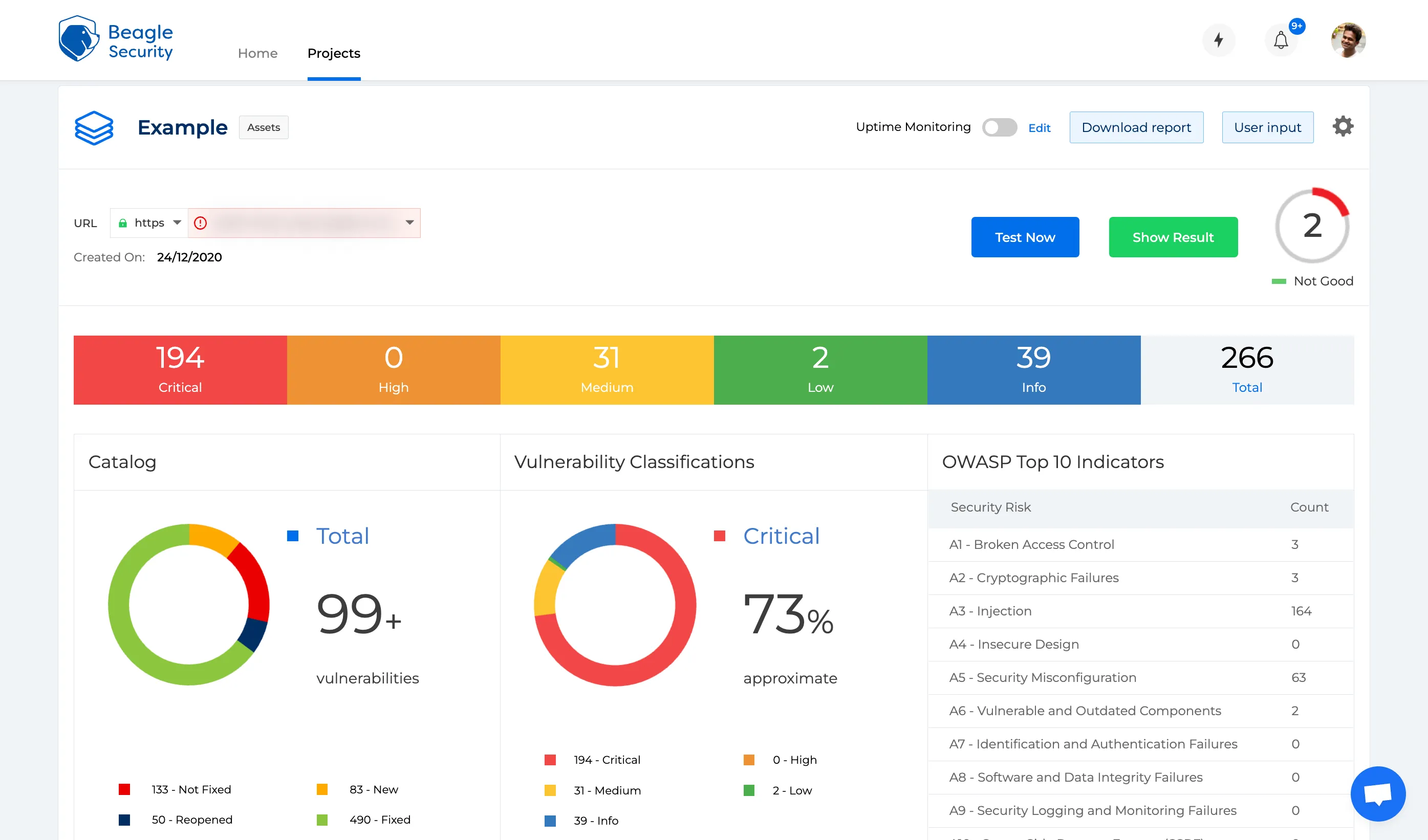
A security risk assessment identifies, evaluates, and implements critical application security controls. It also focuses on preventing application security flaws and vulnerabilities. An enterprise can view its application portfolio from the perspective of an attacker by conducting a risk assessment. It is an ongoing activity that should be done at least once a year.
An organization can use a comprehensive security evaluation to:
Identify the organization’s assets (e.g., network, servers, apps, data centers, tools, etc)
Create a risk profile for each asset
Understand what data these assets hold, send, and generate
Assess asset importance in terms of company operations. Prioritize assets for examination based on their risk ranking
Based on the assessment results, implement mitigation controls for each asset
Proper security recommendations
Another important aspect of a thorough web application security assessment is making security recommendations. To establish a strong security posture, businesses must re-strategize and redesign their security defenses after identifying current threats.
Result documentation
It is critical to keep track of the results of security assessments. A security assessment report takes a methodical and disciplined approach to documenting the assessor’s findings and recommendations for addressing any identified security control flaws.
Top management uses the precise information generated to make critical application security decisions such as budgets, policies, and procedures.
Closing thoughts
While applications are essential components of any technology-based organization, the underlying security flaws continue to be a major source of concern.
Security incidents are a major concern in today’s software-driven corporate world because they can harm a company’s reputation and revenue.
Continuous and effective security assessment provides a current and accurate picture of the threats and risks to which an organization is exposed.
If you’re confused or considering your options before diving into the depths of your web application’s security assessment, Beagle Security’s Free Website Security Assessment would be a good place to start.