There is an increasing number of companies across all verticals building applications with a core focus on API infrastructure. The increasing adoption of the cloud is becoming one of the key drivers for the increase in usage of APIs.
But as development teams choose for shipping new releases without proper security checks, APIs often get compromised because of known vulnerabilities.
According to a recent Gartner report, “By 2022, API abuses will be the most frequent attack vector resulting in data breaches for enterprise web applications.”
API security testing is the process of checking for security weaknesses or vulnerabilities in your APIs and remediating any potential issues.
Why is API security testing important?
Companies use APIs to connect web services and transfer data between them. It has become an integral part of modern mobile and web applications, both internal and customer-facing.
These applications may also exchange a high volume of valuable data like PII (personally identifiable information) and sensitive medical or financial information thereby making it a very appealing target to hackers.
APIs are one of the easiest access points for a hacker to exploit and there have been a number of high profile companies that were at the receiving end of hacker attacks due to insecure API endpoints.
Thus, proper and timely security testing of APIs is very important to make sure that no sensitive information is being exposed.
Top security issues in APIs
The latest API security Top 10 published by OWASP includes:
Broken Object Level Authorization
APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface Level Access Control issue. Object level authorization checks should be considered in every function that accesses a data source using an input from the user.
Broken User Authentication
Attackers often compromise authentication tokens or implementation flaws to assume other user’s identities temporarily or permanently due to incorrect implementation of authentication mechanisms. Compromising a system’s ability to identify the client/user, compromises API security overall.
Excessive Data Exposure
Looking forward to generic implementations, developers tend to expose all object properties without considering their individual sensitivity, relying on clients to perform the data filtering before displaying it to the user.
Lack of Resources & Rate Limiting
In most cases, APIs do not impose any restrictions on the size or number of resources that can be requested by the client/user. This can impact the API server performance, leading to Denial of Service (DoS), and also leave the door open to authentication flaws such as brute force.
Broken Function Level Authorization
Complex access control policies with different hierarchies, groups, and roles, and an unclear separation between administrative and regular functions, tend to lead to authorization flaws. Attackers can gain access to other users’ resources and/or administrative functions by exploiting these issues.
Mass Assignment
Binding client provided data (e.g., JSON) to data models, without proper filtering of properties based on an allowlist, usually leads to Mass Assignment. Either guessing objects properties, exploring other API endpoints, reading the documentation, or providing additional object properties in request payloads, allows attackers to modify object properties they are not supposed to.
Security Misconfiguration
Security misconfiguration is commonly a result of unsecure default configurations, incomplete or ad-hoc configurations, open cloud storage, misconfigured HTTP headers, unnecessary HTTP methods, permissive Cross-Origin resource sharing (CORS), and verbose error messages containing sensitive information.
Injection
Injection flaws, such as SQL, NoSQL, Command Injection, etc., occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s malicious data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Improper Assets Management
APIs tend to expose more endpoints than traditional web applications. This makes proper and updated documentation highly important. Proper hosts and deployed API versions inventory also play an important role in mitigating issues such as deprecated API versions and exposed debug endpoints.
Insufficient Logging & Monitoring
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems to tamper with, extract, or destroy data. Most breach studies demonstrate the time to detect a breach is over 200 days. Most often this is detected by external parties rather than internal processes or monitoring.
Best practices for API security
When it comes to ensuring API security, you need proper policies for authentication and authorization.
Some of the most common ways by which you can ensure API security include:
Access control: Authenticating API traffic using OAuth and JWT allows you to set access control rules to specific API resources.
Encryption: Encrypting data using TLS is a standard practice for API security. This would require users to provide a signature to decrypt and modify the data. It can help mitigate the risk of MITM attacks.
Vulnerability assessment: Doing automated penetration tests on your APIs can allow you to identify vulnerabilities at the right time and remediate them accordingly.
Quotas and throttling for APIs: Having quotas for how often an API can be called and tracking its usage over time can help you prevent abuse. Additionally, the throttling of APIs can mitigate the chances of DoS attacks.
Using an API gateway: An API gateway allows you to keep track of all API calls and do necessary monitoring to understand how the API utilization happens.
Why choose Beagle Security for API security testing
Understanding the innumerable ways in which a hacker could compromise your APIs is a difficult mission. You need to think and act like a hacker.
Handling this manually might not be the best use of your time and resources. This is where Beagle Security’s API security testing feature can help you.

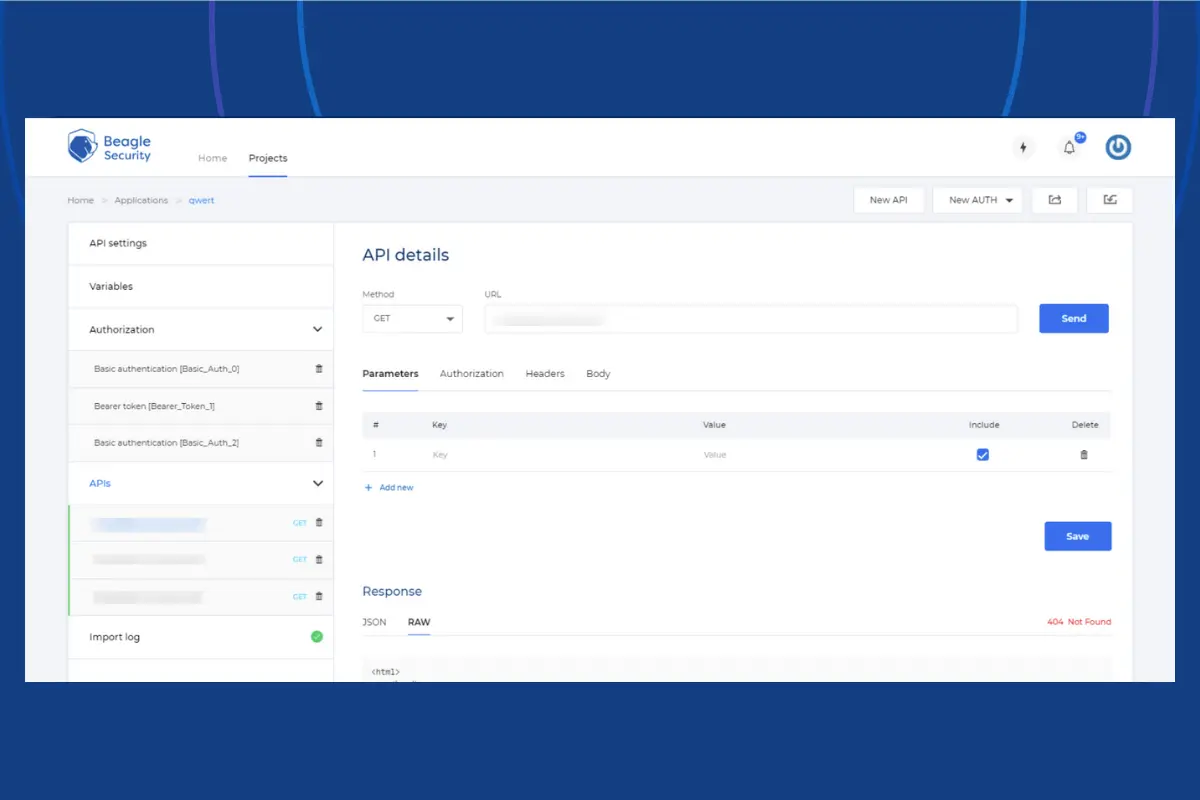
To get started, you just have to enter your API URL, import your APIs from Postman and configure the authorization details and variables. Once that’s done, you’re ready to start the automated security test.
Beagle Security follows a human-like automation process, i.e, mimicking the action of a skilled human pentester to identify the vulnerabilities in your APIs. You’re then provided with detailed recommendations on how you can remediate the issues.
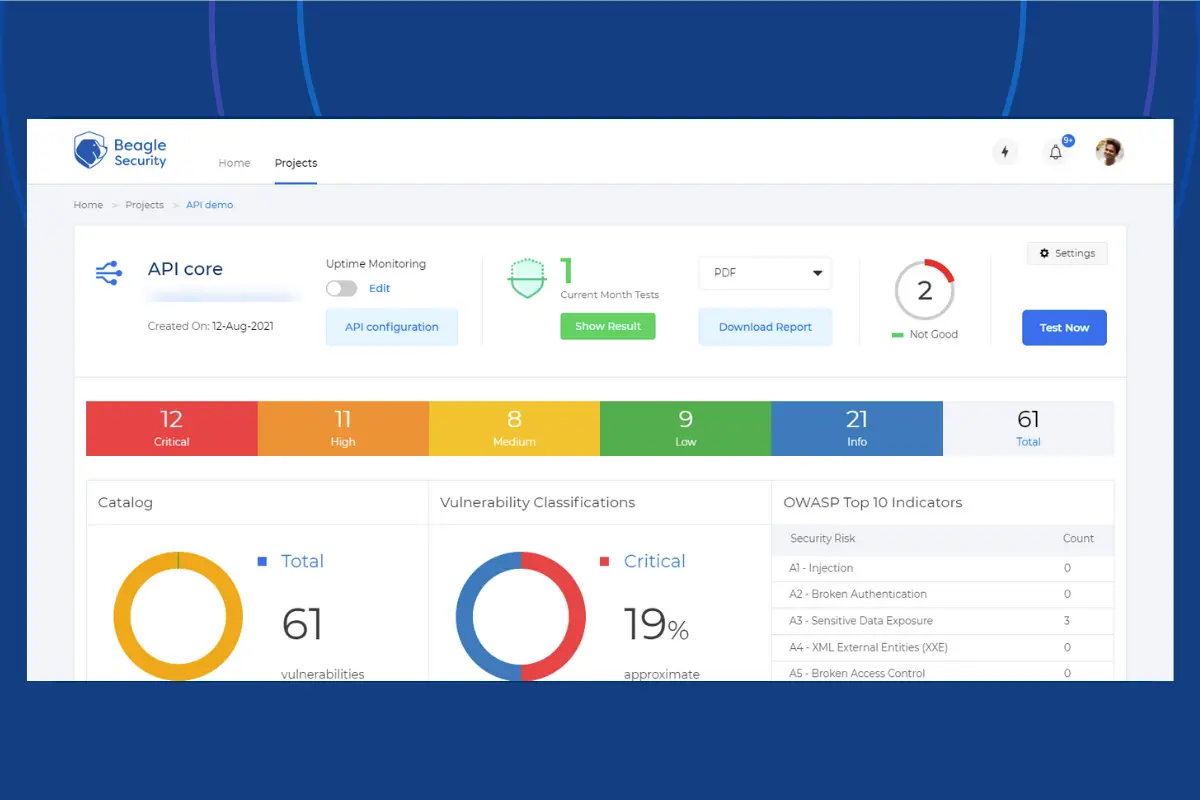
With reporting based on OWASP & SANS security standards, you get complete visibility into the potential attach surface of your APIs.
We also have a dedicated team of security engineers constantly updating our vulnerability database so that your apps are always protected from the latest vulnerabilities.
API security testing is an integral part of the SDLC and with Beagle Security, you can ensure that your APIs are free of any critical vulnerabilities. Try it out today!



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)