
What are software compliance standards?
Software compliance standards are guidelines, regulations, and best practices that ensure software is developed, used, and maintained in accordance with legal, regulatory, and industry-specific requirements.
These standards are designed to protect data integrity, enhance security, ensure privacy, and maintain the overall quality and reliability of software systems.
Regulatory compliance involves ensuring that a business adheres to all applicable laws, regulations, guidelines, and specifications pertinent to its operations.
This process ensures that a business operates within legal boundaries and takes necessary measures to meet all relevant regulatory requirements. Compliance is essential for businesses to maintain their licenses and stay in good standing with regulatory authorities.
Why is software compliance important?
IT compliance is crucial for safeguarding the privacy and security of customers, clients, employees, and companies, thereby enhancing customer trust in a business.
By adhering to stringent digital security and privacy standards, businesses can make customers feel more secure using their services, potentially attracting new users through positive word-of-mouth.
Customers and clients expect their sensitive information, such as social security numbers, medical records, and bank account details to be protected.
Meeting compliance standards indicates that a company is fulfilling legal requirements, thereby minimizing the risk of legal penalties, fines, or the loss of business opportunities in regions with specific compliance regulations.
What are the common software compliance standards?
Understanding common software compliance standards is a crucial step in deciding which ones apply for your organization.
We will further explore the key software compliance standards that organizations need to be aware of.
Each standard has its unique requirements and focuses on different aspects of software security and data protection.
By familiarizing yourself with these standards, you can better understand the necessary measures to implement within your organization to achieve compliance, mitigate risks, and foster a secure environment for your users.
Let’s delve into the most prevalent software compliance standards that every software provider should be aware of.
1. GDPR
General Data Protection Regulation (GDPR) is enforced by the European Union (EU) to protect the digital information of European citizens.
Any business, including those outside the EU, that collects data related to EU citizens must comply with GDPR standards. This includes companies and individual sellers from the United States who offer goods or services or monitor the behaviour of EU residents.
A key GDPR regulation is obtaining user consent to collect their data. Businesses must inform users when their data is being managed and give them the option to decline. If a user declines, the company must delete any gathered data.
2. ISO 27001
ISO/IEC 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability.
The standard is published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
ISO 270001 provides a structured approach to protecting sensitive information which supports the development of robust processes to ensure business continuity in the face of disruptions.
This standard is for organizations seeking to protect their information assets and maintain a high level of information security management.
3. SOC 2 Type 2
SOC 2 Type 2 is a report that provides detailed information and assurances about the controls at a service organization relevant to security, availability, processing integrity, confidentiality, and privacy.
Developed by the American Institute of CPAs (AICPA), SOC 2 Type 2 is part of the Service Organization Control (SOC) reporting framework and specifically addresses the effectiveness of the controls over a defined period (typically six months to a year).
This standard demonstrates to customers and stakeholders that the organization maintains high standards for security and operational effectiveness. It identifies potential risks and ensures controls are in place to mitigate them.
4. FedRAMP
The Federal Risk and Authorization Management Program (FedRAMP) is a US government-wide program that standardizes the security assessment, authorization, and continuous monitoring of cloud products and services.
FedRAMP was established to ensure that cloud service providers (CSPs) meet stringent security requirements when offering cloud computing solutions to federal agencies.
FedRAMP leverages security baselines established by the National Institute of Standards and Technology (NIST), including NIST SP 800-53, to define rigorous security controls that CSPs must implement and adhere to.
FedRAMP facilitates the adoption of cloud services by promoting interoperability and compatibility between federal agencies and CSPs.
It provides transparency and visibility into the security posture of cloud services through the FedRAMP Marketplace, where authorized CSPs are listed.
5. PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) governs the security of financial card data, such as debit and credit card numbers.
Any business that conducts online transactions involving the storage, transmission, and management of financial information must comply with PCI DSS. Meeting these standards helps businesses build transparency and trust with clients conducting online transactions.
When customers know a company complies with PCI DSS, they are likely to feel more secure using the online services. Businesses often develop robust systems to host and protect customer financial information to meet PCI DSS standards.
6. HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) ensures the security of patient health records in the healthcare industry.
It applies to all entities that handle, access, or transfer medical records, including clinics, hospitals, pharmacies, and insurance companies. HIPAA compliance involves:
Maintaining privacy regulations that restrict sharing medical information without patient consent.
Securing electronic files through administrative, physical, and technical measures to prevent unauthorized access.
Installing notification systems to alert businesses and patients in case of security breaches.
7. FISMA
The Federal Information Security Management Act (FISMA) applies to federal agencies and mandates the implementation of information security plans to safeguard sensitive information.
Federal agencies must develop data protection plans and use various security software and systems, while also verifying third-party vendors.
FISMA compliance varies based on the agency’s role, with national security agencies requiring higher standards than others, such as the U.S. Department of Housing and Urban Development. Businesses working with federal agencies may also need to be aware of FISMA regulations.
Which software compliance standard is right for you?
With the multitude of regulations and software compliance standards in existence, it can feel overwhelming to determine which ones apply to your business. Fortunately, there is a simple three-step process you can follow to identify the relevant regulations for your organization:
1. Consider your industry
Some regulations, such as HIPAA or FERPA (Family Educational Rights and Privacy Act), primarily impact specific industries. Research all regulations that specifically apply to your industry and ensure compliance with them.
For example:
In the healthcare industry, organizations handling sensitive patient information are subject to various security compliance requirements to ensure the confidentiality, integrity, and availability of healthcare data
HIPAA privacy rule: Protects the privacy of individually identifiable health information
HIPAA security rule: Establishes national standards for the security of electronic protected health information (ePHI), requiring safeguards to ensure its confidentiality, integrity, and availability.
HIPAA breach notification rule: Requires covered entities to notify affected individuals, the Secretary of Health and Human Services, and, in some cases, the media, of breaches of unsecured PHI.
Adhering to these specific security compliance standards is crucial for healthcare organizations to protect patient information, maintain regulatory compliance, and mitigate the risk of breaches and penalties.
2. Consider your clientele
Even if no industry-specific regulations affect your company, you will likely need to comply with regulations related to your customer base or employee data.
Research compliance standards for any countries where you operate, employ, or sell. Examine what customer data you store and investigate policies related to that type of data.
3. Consider the size of your business
Your business size can influence the standards you must meet. You may face different requirements than a publicly traded enterprise or a small business.
Reevaluate compliance standards as your business grows to ensure continued compliance considering any structural changes.
Once you have determined which regulations apply to your business, conduct a comprehensive cybersecurity assessment. This assessment will help you evaluate how well you currently meet all applicable regulatory requirements and identify areas needing changes or improvements.
Meeting software compliance standards
Meeting major regulatory requirements for your business and industry can be challenging.
The good news is that with a thorough understanding of the current IT compliance standards relevant to your business, you have the foundation needed to set your team up for success.
However, maintaining compliance requires more than just knowledge of existing regulations and their applicability to your business. You need a solution designed to help businesses like yours consistently meet those standards.
1. Compliance framework identification
Identifying the compliance framework involves recognizing the specific regulations, standards, and guidelines. It involves selecting frameworks such as SOC 2, ISO 27001, or HIPAA, providing a structured set of controls and criteria to ensure data security and regulatory alignment.
This step requires a thorough understanding of the following:
Industry-specific requirements
Regional laws (such as GDPR and HIPAA)
Sector-specific mandates (like PCI-DSS for payment processing)
2. Compliance readiness
Conducting a compliance readiness review entails evaluating the current policies, procedures, and technical measures to verify their alignment with selected compliance frameworks.
This assessment involves scrutinizing documentation, security protocols, data handling practices, and employee training.
The objective is to pinpoint any disparities between the present state and the mandated compliance standards.
3. Compliance strategy
Designing a compliance strategy involves developing a plan and outlining a roadmap to fulfil regulatory requirements while aligning with business objectives.
This strategy defines the necessary steps for achieving and maintaining compliance, considering factors like data security, privacy, and risk mitigation.
The process typically starts with comprehending the precise compliance requirements dictated by industry standards and regional regulations.
It entails establishing clear objectives, assigning responsibilities, setting implementation timelines, and ensuring a structured approach to attaining and preserving compliance.
4. Deployment
Upon formulating the compliance strategy, the deployment of aligned measures involves executing the outlined plans.
This includes implementing the required controls, protocols, and technological solutions to align with the compliance strategy effectively.
This process encompasses various actions, including updating software and integrating security measures such as encryption and access controls. It also involves conducting regular audits.
5. Compliance evaluation
Conducting a compliance preparedness evaluation involves assessing its readiness to meet regulatory standards and requirements. This evaluation starts with an internal review, examining existing policies, procedures, and technical measures.
The objective is to identify gaps between the current compliance status and the desired regulatory standards. Any deficiencies found are documented, and corrective actions are planned to align with compliance frameworks.
How Beagle Security can help you achieve software compliance standards
Beagle Security is an AI penetration testing platform that helps you uncover vulnerabilities in your web applications & APIs, providing contextual reports on how to fix them.
Penetration testing is a key step in meeting compliance requirements, often mentioned as a necessary measure in various software compliance standards.
With the Beagle Security platform, once a penetration test is completed, you can download compliance mapped penetration test reports against HIPAA, GDPR and PCI DSS standards.
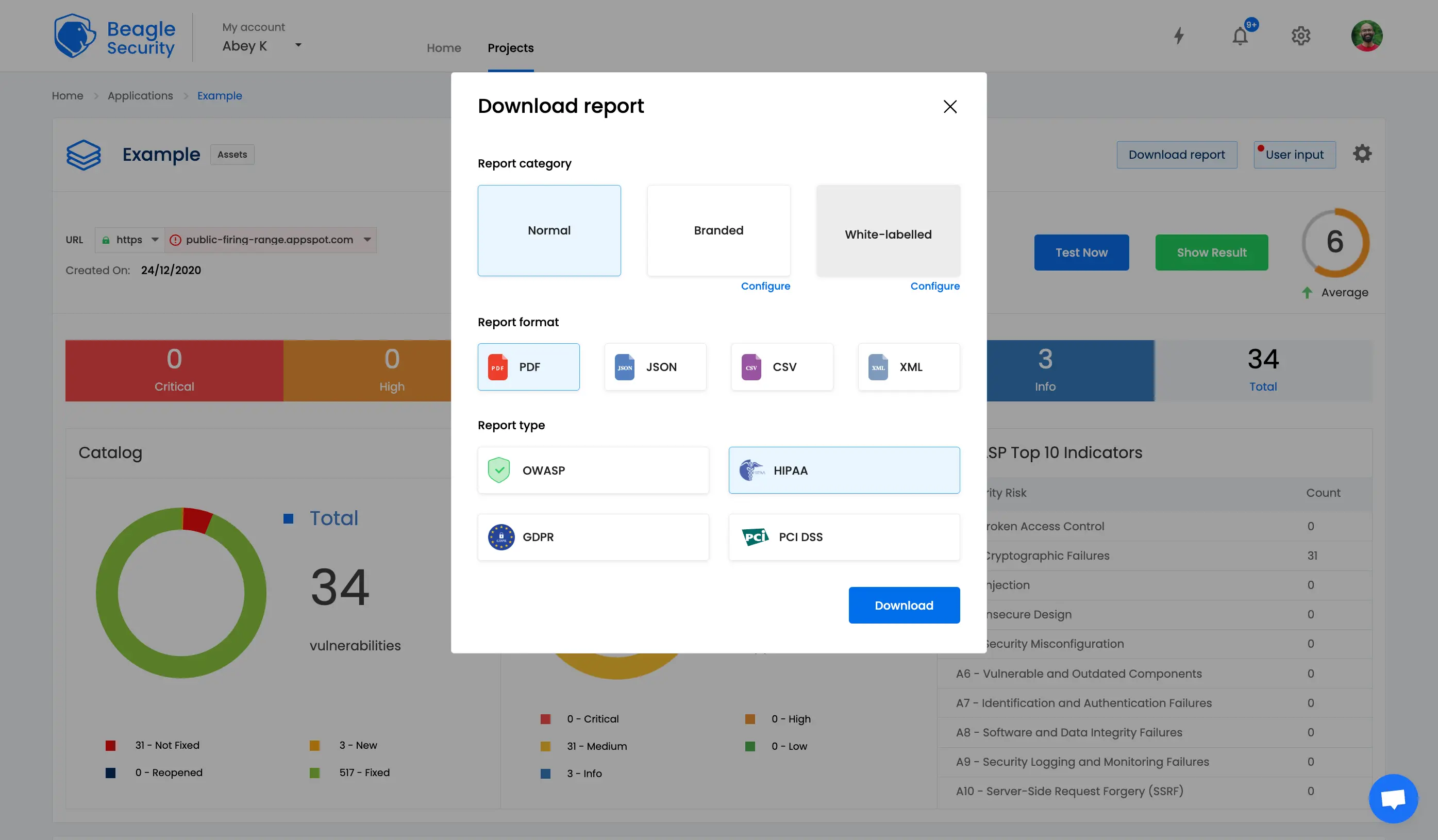
These reports include a compliance summary table that gives you insights into the compliance checks you have passed and failed. For any failed checks, you can see detailed vulnerability findings along with remediation and occurrence details.
There’s also an OWASP report that can be used for your ISO 27001 and SOC 2 compliance needs. Both these compliance standards only require a penetration test to be completed, without any specific compliance mapping involved.
By leveraging Beagle Security, you can streamline your path to achieving and maintaining software compliance standards.
With comprehensive reporting and actionable insights, Beagle Security ensures that your applications are secure and compliant with industry requirements. Take the proactive step towards securing your software today with Beagle Security.
![Best tools for SOC 2 compliance penetration testing [2025] Best tools for SOC 2 compliance penetration testing [2025]](/blog/images/blog-banner-two-cover.webp)

![Best tools for HIPAA penetration testing [2025] Best tools for HIPAA penetration testing [2025]](/blog/images/blog-banner-one-cover.webp)



