
For modern teams building SaaS applications, SOC 2 penetration testing plays a crucial role in maintaining compliance, protecting customer data, and proving that security isn’t just a checkbox.
Whether you’re a security engineer implementing SOC 2–aligned testing workflows or an engineering manager evaluating DAST tools for your CI/CD pipeline, this guide walks you through what SOC 2 penetration testing is, why it matters, and how long it takes to get it right.
What is SOC 2 penetration testing?
At its core, SOC 2 penetration testing is a structured security assessment designed to uncover vulnerabilities in your systems, applications, and processes that could impact your compliance with the SOC 2 Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 2 compliance is governed by the American Institute of CPAs (AICPA) and focuses on how an organization manages customer data. While the SOC 2 audit itself doesn’t mandate a penetration test, auditors and customers increasingly expect one as part of your evidence of continuous security assurance.
SOC 2 penetration testing focuses on two types of SOC 2 compliance: Type I and Type II.
Key differences between SOC 2 Type I and Type II
While both SOC 2 Type I and Type II reports assess how an organization manages customer data, they differ in scope and depth.
| Criteria | SOC 2 Type I | SOC 2 Type II |
|---|---|---|
| Primary Focus | Evaluates whether controls are designed correctly at a specific point in time. | Evaluates whether controls are operating effectively over a period of time. |
| Assessment Period | Single date or snapshot | Typically covers 3–12 months of continuous operation |
| Goal | Confirms initial compliance readiness and control setup. | Confirms sustained control performance and reliability. |
| Evidence Collected | Documentation, screenshots, and interviews proving control design. | Audit evidence, activity logs, and testing results proving ongoing control operation. |
| Audit Effort & Duration | Faster, usually 4–12 weeks. | Longer, typically 4–12 months, including observation and testing. |
| Audit Outcome | Provides assurance on design effectiveness at one point in time. | Provides assurance on both design and operational effectiveness over time. |
| Customer Perception | Demonstrates compliance intent and early security maturity. | Demonstrates proven, ongoing compliance. |
In essence, Type I is a snapshot of your security setup, while Type II is a continuous validation of how well those controls perform in practice.
Organizations pursuing long-term trust and enterprise readiness typically aim for SOC 2 Type II, as it provides stronger assurance to customers, partners, and auditors.
What is the purpose of an SOC 2 penetration test?
The purpose of a SOC 2 test is to verify that an organization’s systems and processes effectively protect customer data in line with the AICPA’s Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. In other words, it confirms that your company not only has security controls in place but that they work as intended to safeguard sensitive information.
For SaaS providers, cloud platforms, and other service-based businesses, a SOC 2 test demonstrates operational reliability and compliance maturity. Auditors evaluate whether your access controls, encryption methods, monitoring tools, and data-handling procedures meet strict standards that enterprise clients and regulators expect.
A SOC 2 test serves three critical purposes:
Assurance: It provides independent validation that your organization maintains a secure environment and protects customer data from breaches or unauthorized access.
Trust: It builds confidence with customers, investors, and partners. This is essential during procurement, due diligence, and renewal cycles.
Compliance readiness: It helps your teams identify control gaps, prioritize remediation, and maintain continuous compliance throughout the year.
How long does a SOC 2 pentest take?
The duration of a SOC 2 penetration test depends on several variables including scope, complexity, and testing approach. Generally, organizations can expect:
| Organization type | SOC 2 Type I duration | SOC 2 Type II duration | Notes |
|---|---|---|---|
| Startup / Early-stage SaaS | 4–6 weeks | 4–6 months | Limited systems and smaller scope make audits faster. |
| Mid-size SaaS (50–200 employees) | 6–10 weeks | 6–9 months | Moderate scope; often includes multiple trust criteria. |
| Enterprise / Multi-region org | 10–12 weeks | 9–12 months | Broader infrastructure, multiple cloud environments, complex controls. |
For continuous compliance and DevSecOps alignment, organizations often adopt this testing rhythm:
Quarterly automated penetration tests integrated into build pipelines.
Annual independent SOC 2 penetration testing to validate automated findings and satisfy auditor requirements.
On-demand targeted tests for major releases, new APIs, or infrastructure changes.
How to use Beagle Security for your SOC 2 penetration testing
Leveraging an automated penetration testing platform like Beagle Security can greatly minimize both the time and costs associated with penetration testing. Here’s how you can approach it:
Getting started
Add a new application: Choose Add Application, then pick the kind of target you want to test. It can be a traditional website, a RESTful API, or a GraphQL endpoint.
Enter application information: Provide a clear name and the full URL that will act as the main testing target for your AI-driven penetration test. You can also indicate the application’s priority and adjust access settings (e.g., public vs. restricted) to reflect how testers should reach the asset.
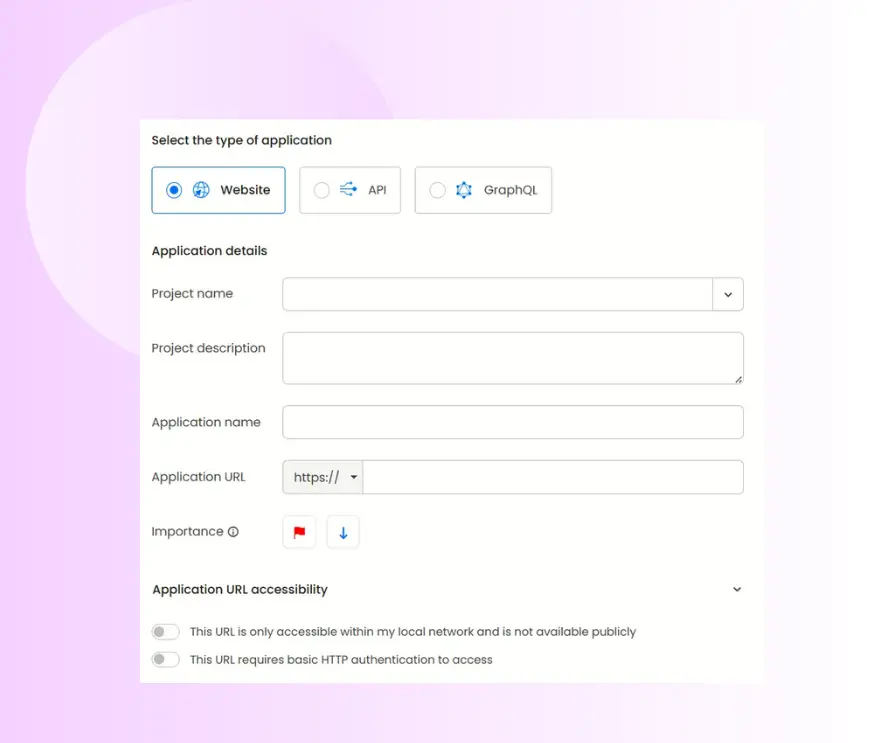
Deciding between black box and grey box penetration testing selection
When designing a SOC 2 penetration test, one of the earliest decisions is determining how much information your tester will have about the target environment. This defines whether you’ll take a black box or grey box testing approach.
Black box testing simulates an external attacker with no prior knowledge of your systems. It’s ideal for assessing perimeter security, network exposure, and your organization’s ability to detect and respond to real-world attacks.
Grey box testing, on the other hand, provides testers with limited internal details such as valid credentials, API documentation, or architectural context. This enables deeper inspection of internal logic, user roles, and post-authentication attack surfaces that are vital to SOC 2’s Security and Availability Trust Criteria.
For initial external SOC 2 assessments, many organizations start with a black box test. In Beagle Security, this can be initiated directly after registering your application.
Simply click Start Test to launch a scan that evaluates your publicly accessible systems from an outsider’s perspective, without privileged access.
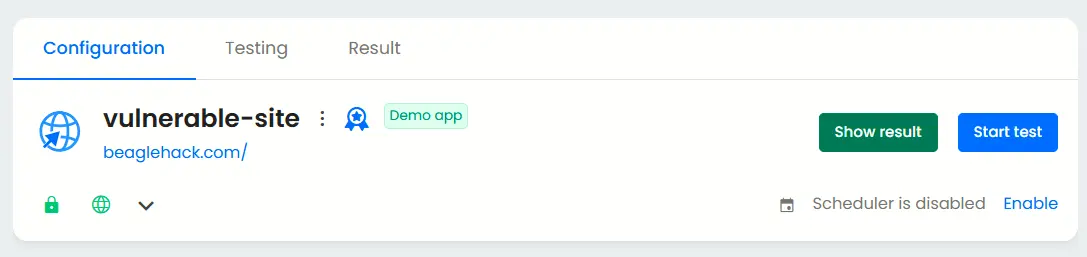
Additional configurations for grey box penetration test
Once you’re ready to go beyond surface-level testing, grey box testing helps validate how securely your application behaves under authenticated and real-world conditions.
Authenticated testing
Enable “authenticated testing” at the bottom of basic tab and provide test credentials. This lets the AI-driven modules evaluate post-login functionality, user roles, and internal workflows, essential for SOC 2 evaluations involving access control and least privilege enforcement.
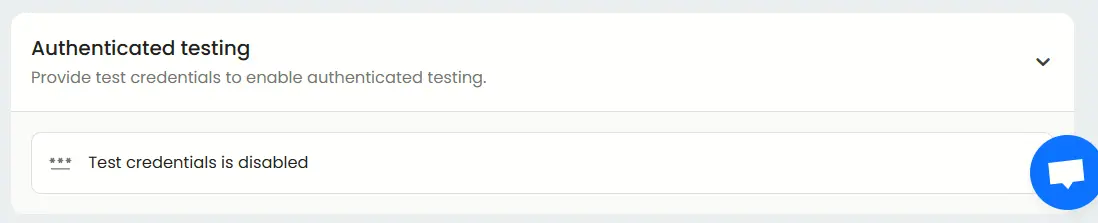
You can configure multiple credential types, including:
Traditional username-password logins
Signup-based flows
Third-party SSO (e.g., Google, Azure AD)
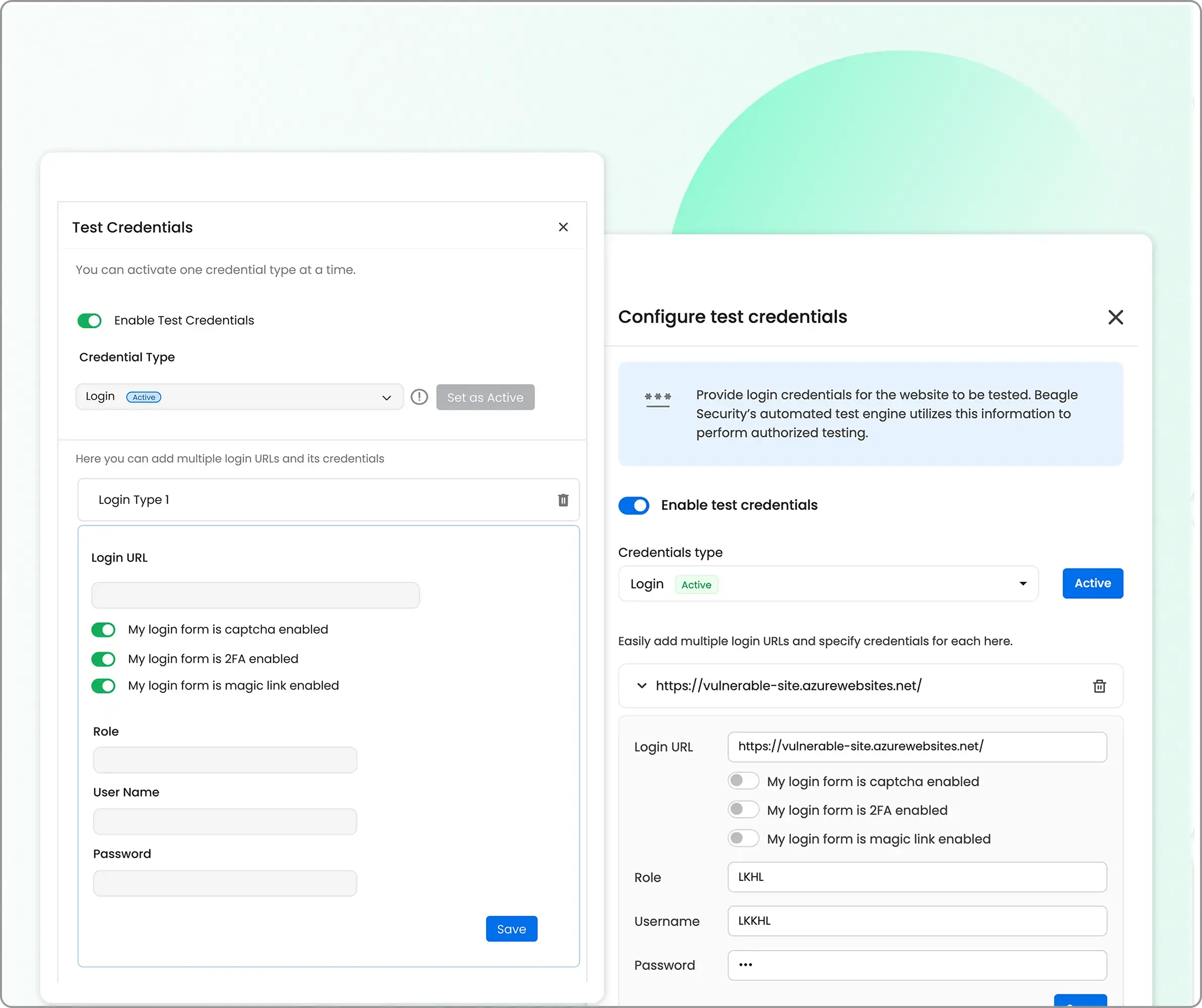
The recommended login is the “recorded login” option which can be set up by Beagle Security’s chrome extension.
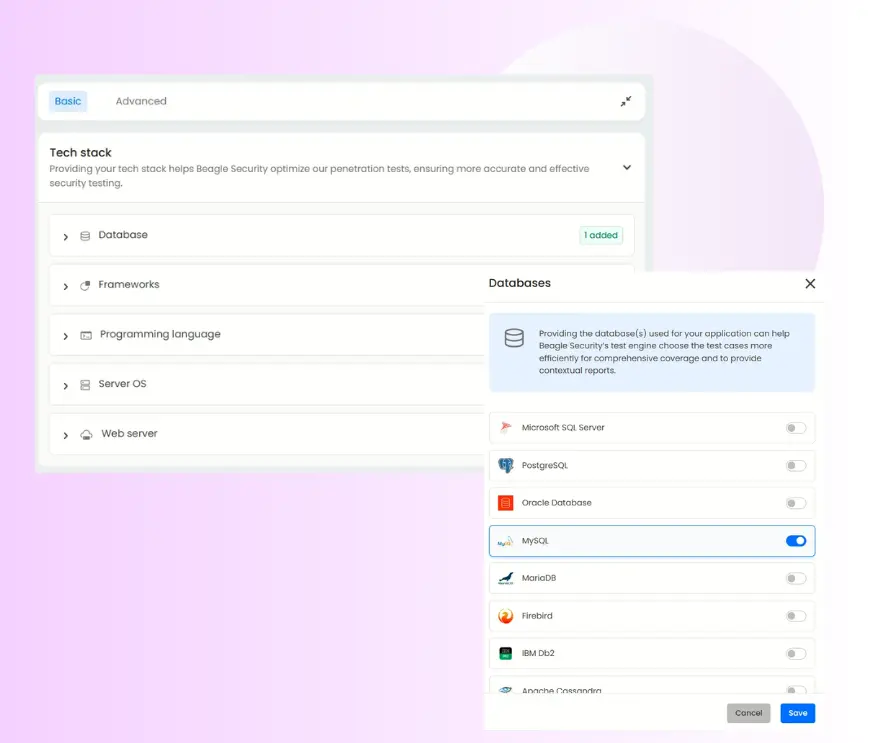
Tech stack configuration
Under the Basic tab, Beagle Security allows you to define your application’s tech stack such as frameworks (React, Django, Laravel), server types, and databases.
By doing so, Beagle automatically fine-tunes the pentesting process to match your specific environment, enabling better coverage of stack-specific vulnerabilities like XSS and deserialization flaws.
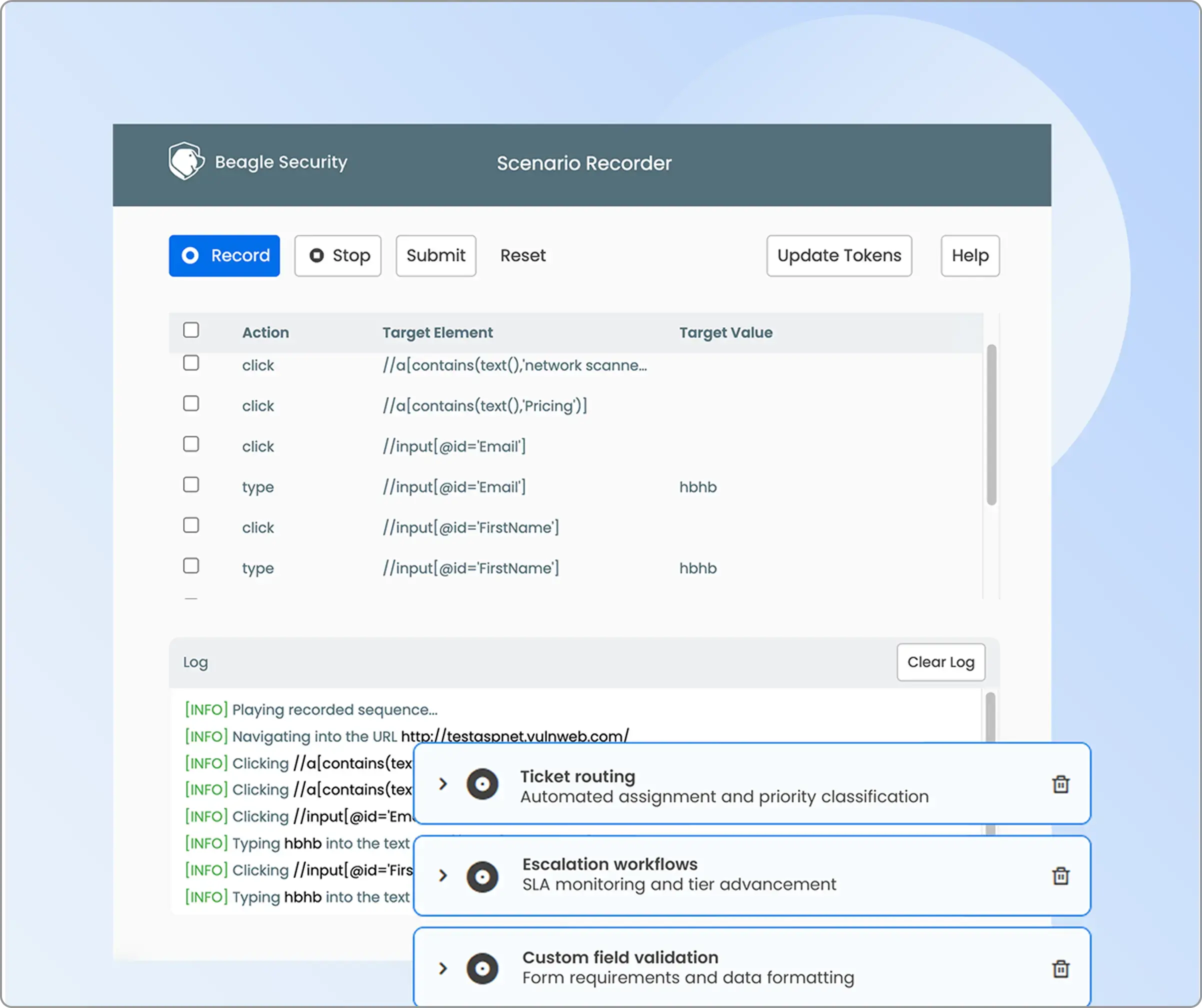
Business logic recording
In complex SaaS and fintech platforms, security risks often hide within custom workflows and multi-step user transactions. Beagle’s Business Logic Recording feature, available under the Advanced tab, enables you to capture these unique processes using its browser plugin.
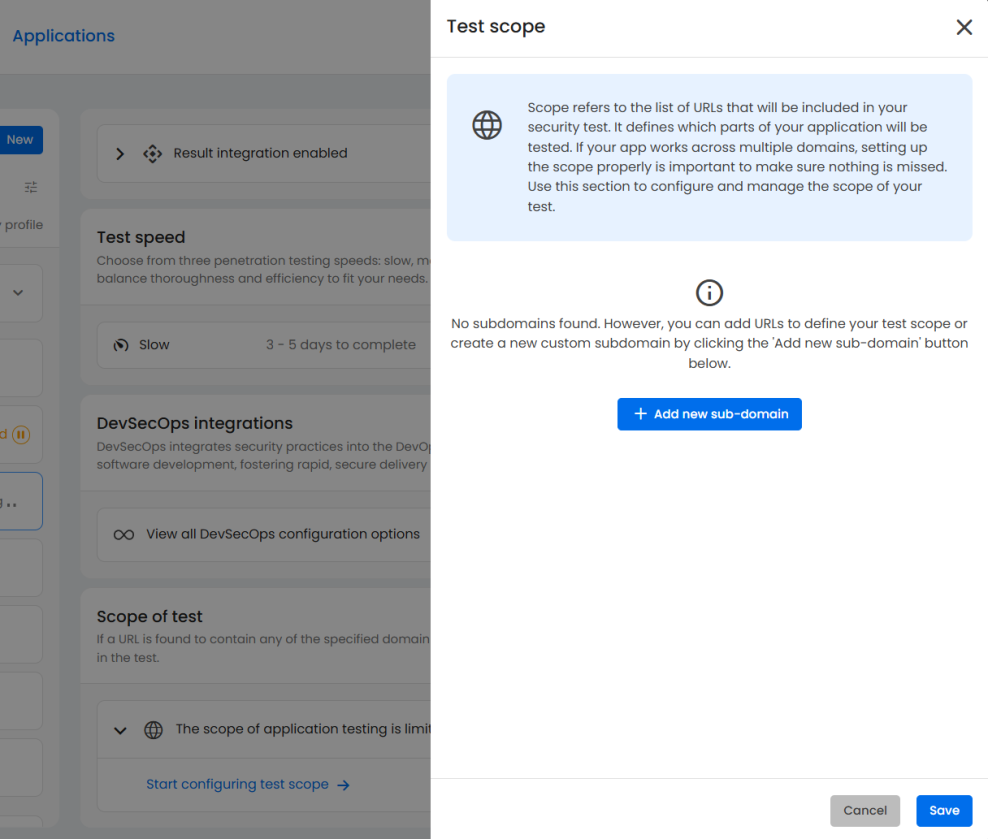
Pentesting scope
A well-defined pentesting scope ensures full coverage without unnecessary noise. The scope determines which URLs, domains, or subdomains are included in your testing.
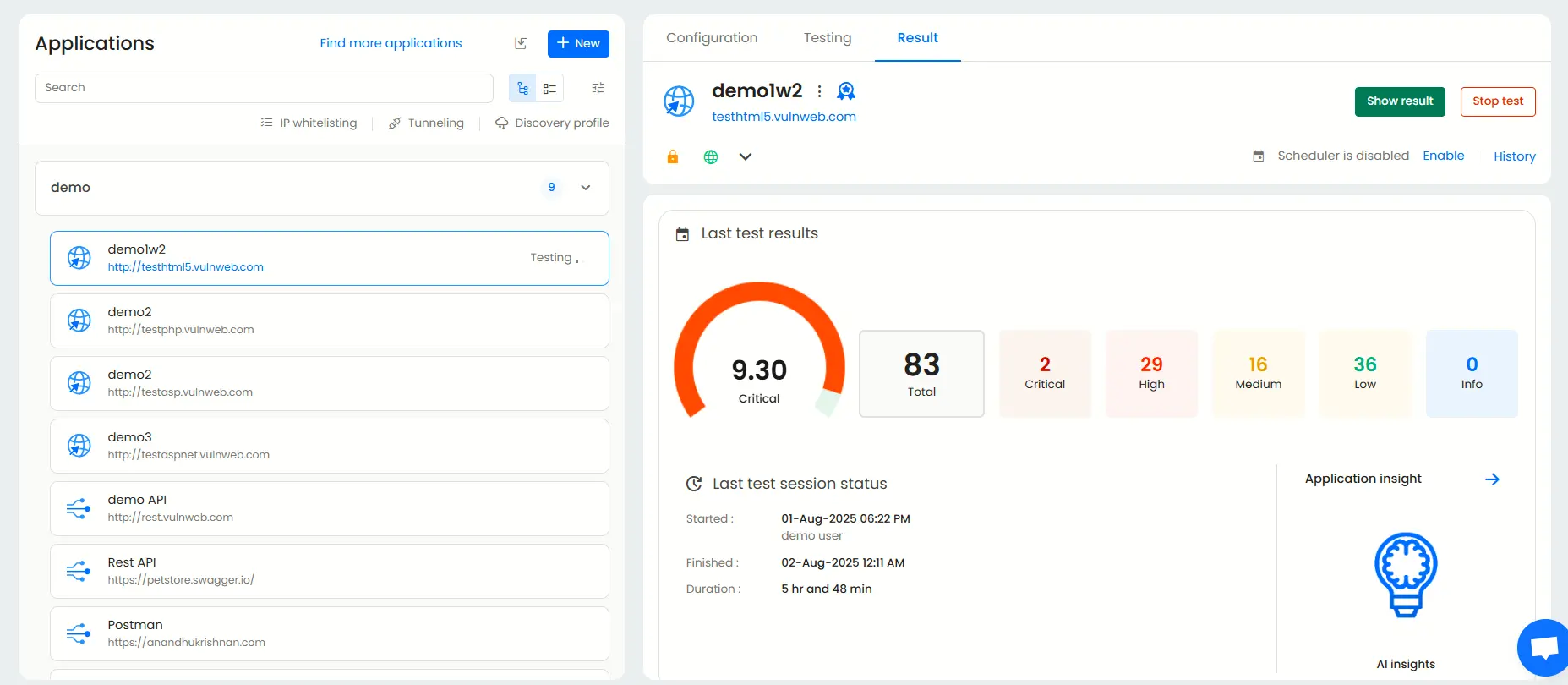
Viewing the penetration test results and reports
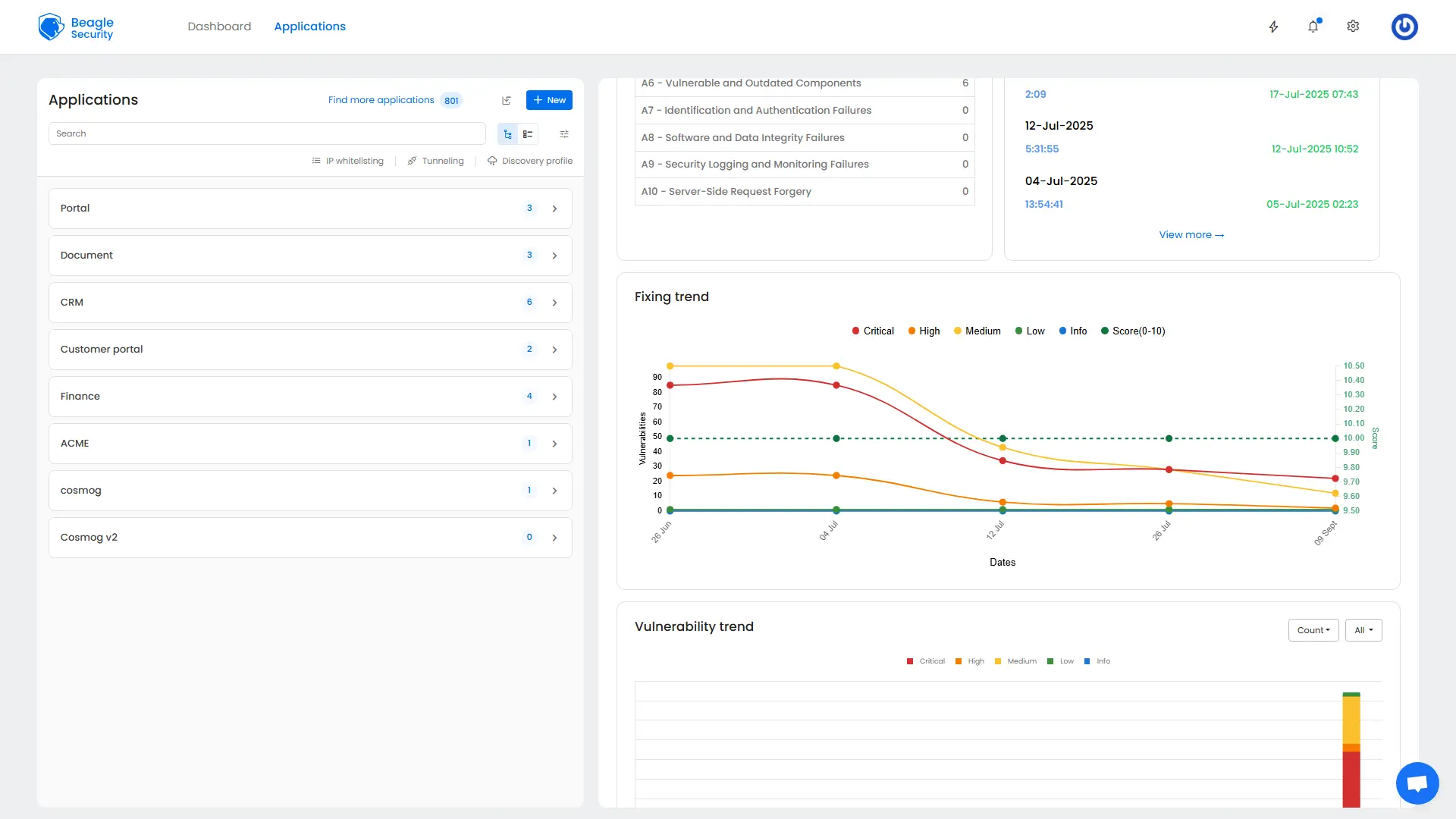
Application dashboard
The Application Dashboard gives you a high-level summary of each application, displaying last test results, vulnerability counts, and prioritized remediation tasks. This is ideal for security engineers managing multiple projects.
Open vulnerabilities by severity
Quickly assess how many critical, high, medium, and low issues remain unresolved using this widget.
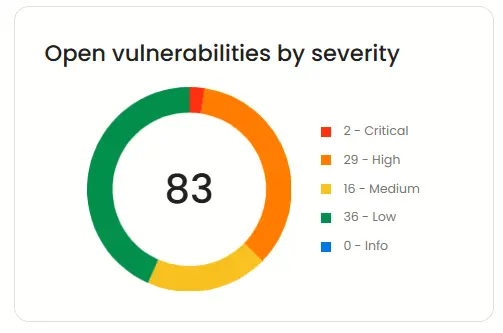
Open vulnerabilities by age
Track how long vulnerabilities have existed, supporting SOC 2’s requirements for timely remediation.
OWASP top 10 indicators
The OWASP Top 10 is a standard that represents a broad consensus of the ten most critical security risks to web applications. Identify vulnerabilities aligned with the OWASP Top 10, helping maintain alignment with SOC 2 Security Trust Criteria.

Fixing trend
View the rate and severity of vulnerabilities you’ve resolved over time, crucial for demonstrating continuous improvement.
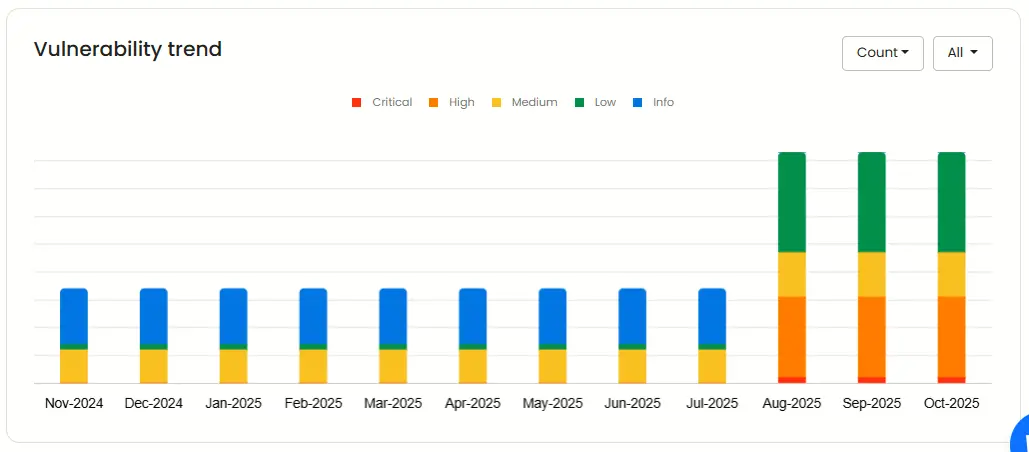
Vulnerability trend
Analyze vulnerability frequency over the past year to measure the impact of your DevSecOps maturity.
Result dashboard
The result dashboard is unique to each application and shows you the overview. Keep track of how many vulnerabilities are present, the severity of each one, and the date and time of your previous scans.
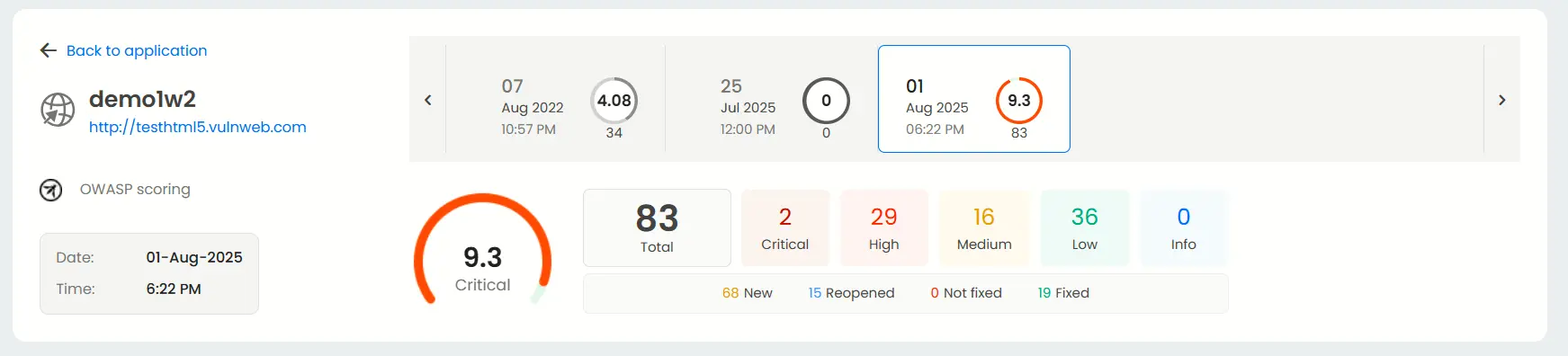
Mapping with ISO27001, OWASP & OWASP Top 10
Beyond SOC 2, Beagle Security allows you to map your penetration test findings to other leading frameworks such as ISO 27001, HIPAA, and PCI DSS.
This is particularly useful for globally distributed teams or SaaS companies targeting international compliance certifications.
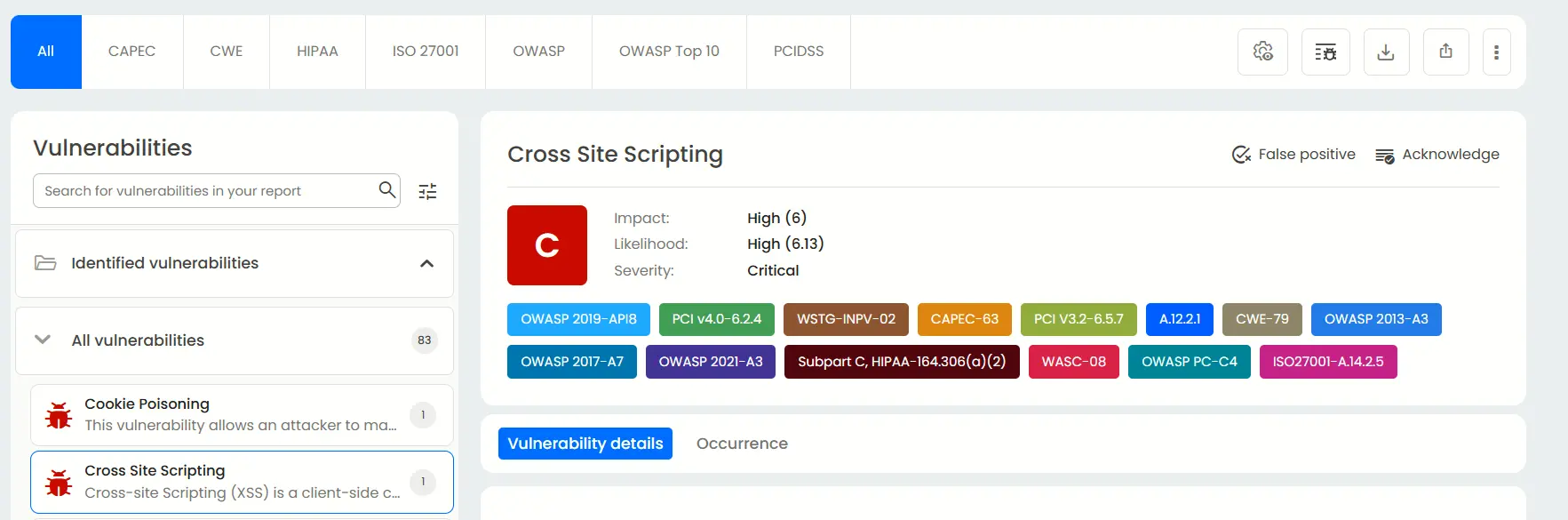
Detailed findings, fix recommendations & occurrence details
For every identified issue, Beagle Security provides:
A technical description of the vulnerability
Detailed remediation guidance with code-level suggestions
Historical occurrence details and verification tracking
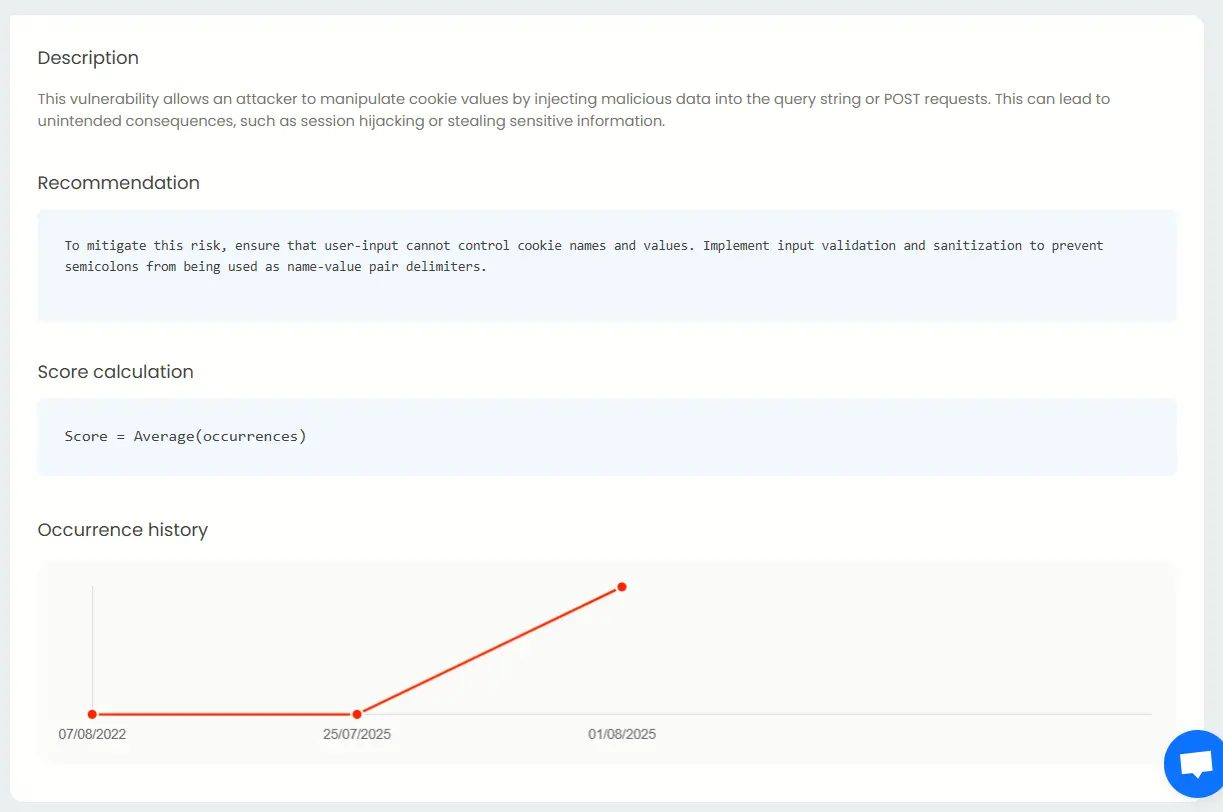
OWASP reports
While the OWASP Top 10 highlights the most common vulnerabilities, Beagle Security’s extended OWASP Report goes further by documenting all detected OWASP-aligned issues, regardless of frequency.
This gives security teams a complete view of their web application risk landscape, ensuring compliance not just with SOC 2 but also with broader AppSec best practices

Final thoughts
As compliance expectations rise, SOC 2 penetration testing has become a cornerstone of modern application and infrastructure security. By adopting a SOC 2 penetration testing methodology that balances automation with expert validation, you can:
Strengthen your control effectiveness.
Shorten audit preparation time.
Build trust with customers and stakeholders.
Take the guesswork out of compliance and turn your SOC 2 testing into a strategic advantage with Beagle Security. Try out our 14 day free advanced trial or check out the interactive demo to see if we’re the right fit for you.
FAQ
What is the SOC 2 testing framework?
The SOC 2 testing framework evaluates how effectively an organization safeguards customer data using the Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy, based on AICPA standards.
What is the cost for an SOC 2 penetration test?
The cost of an SOC 2 penetration test typically ranges from $5,000 to $25,000, depending on factors like company size, system complexity, and compliance scope.
An automated pentesting software such as Beagle Security, however, can significantly reduce the costs involved. Our plans start from $119, providing a much cheaper and faster alternative to manual SOC 2 testing.
What’s the difference between PTES and SOC 2?
PTES (Penetration Testing Execution Standard) outlines a technical approach for ethical hacking, while SOC 2 is a compliance framework focused on verifying an organization’s security controls and data protection processes.
Is SOC 2 compliance mandatory?
SOC 2 compliance isn’t legally mandated, but it shows that you take data security seriously and should be implemented if possible.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)