
Investing in penetration testing is no longer optional, it’s a business necessity. However for many decision-makers, understanding what goes into a penetration testing quote can feel like navigating a maze of technical terms, methodologies, and pricing structures.
Whether you’re a CTO evaluating vendors, a compliance manager preparing for an audit, or a business owner concerned about data breaches, understanding how a penetration testing quote is structured can help you make smarter, more cost-effective security decisions.
This guide breaks down every element of a quote: What it includes, what influences the cost, and how to evaluate proposals to ensure you’re getting real value from your investment.
What is a penetration testing quote?
A penetration testing quote is a detailed proposal that outlines the scope, methodology, deliverables, timelines, and cost associated with conducting a penetration test. Essentially, it’s the blueprint of how your chosen vendor plans to simulate real-world cyberattacks on your systems to uncover vulnerabilities before attackers do.
A well-structured quote helps you understand:
What systems will be tested: web applications, servers, APIs, networks
What type of testing will be performed: black box, grey box, or white box
How deep the assessment will go: from surface-level scanning to in-depth exploitation
Deliverables: Vulnerability reports, risk ratings, and remediation guidance
Timelines for execution, reporting, and retesting
A good penetration testing quote isn’t just about the numbers, it’s about clarity, transparency, and alignment with your organization’s security and compliance goals.
Key components of a penetration testing quote
A clear, comprehensive penetration testing quote protects both buyer and vendor and speeds procurement decisions.
While different vendors may format their quotes differently, most comprehensive penetration testing quotes include a mixture of the following sections:
1. Executive summary
One-paragraph overview of the engagement purpose, high-level objectives, and what the client will receive.
Quick statement of value: security posture improvements, compliance alignment, risk reduction.
2. Scope of work
Assets & targets: domains, IP ranges, web apps, APIs, cloud accounts, internal networks, mobile apps, OT, etc. (explicitly list IPs/URLs).
In-scope vs out-of-scope: clearly enumerate exclusions to avoid surprises.
Authentication: unauthenticated vs authenticated (provide test accounts/credentials).
User roles & environments: staging vs production, admin roles to test.
Data sensitivity considerations (PII, PCI, PHI) and special handling instructions.
3. Objectives & success criteria
What types of vulnerabilities or attack paths the test aims to find (e.g., RCE, auth bypass, privilege escalation).
Acceptance criteria: what constitutes a valid finding and how severity is scored.
4. Rules of engagement (RoE)
Allowed testing windows and blackout dates.
Rate limits, DoS testing policy, and escalation contacts for accidental outages.
Safe-testing measures and rollback procedures.
Authorization statement signed by the client (proof of permission).
5. Methodology & testing approach
Testing types: external network, internal network, web application, API, mobile, cloud, social engineering, red team.
Standards referenced: OWASP, NIST, PTES, OSSTMM (if vendor uses them).
6. Deliverables
Primary report: executive summary, detailed findings, technical reproduction steps, risk rating, remediation steps, affected assets list.
Supplemental deliverables: vulnerability spreadsheet/CSV, prioritized remediation roadmap, remediation code snippets, threat models.
Executive presentation: slide deck for leadership (often optional/premium).
Retest report: verification of fixes (scope/price for retest should be stated).
7. Timeline & milestones
Proposal validity period.
Start date (or availability window).
Estimated engagement duration (testing phase) and time to deliver final report.
Milestones: kickoff, interim updates, delivery, retest.
8. Pricing & fee structure
Clear breakdown: flat fee, hourly rate, per-asset pricing, vs tiered packages.
What’s included vs add-ons (social engineering, red team, code review, retest).
Payment terms: deposit, milestone payments, refunds/credits for cancellations.
9. Assumptions & constraints
Test relies on provided credentials, network access, or client resources.
Limitations that could affect findings (e.g., feature flagged code, 3rd-party services).
Performance impacts and any monitoring / logging considerations.
10. Risk classification & severity scoring
Which vulnerability scoring system is used (CVSS, custom rating) and what each severity means for the client.
Prioritization guidance: quick wins vs high-impact issues.
11. Remediation support & retesting
Availability of remediation guidance, code examples, and consulting hours.
Retest policy: included retest window or charged separately; how many retests permitted.
12. Legal, confidentiality & compliance
NDA and confidentiality commitments.
Data handling, storage and retention periods for test data and evidence.
Regulatory compliance implications (HIPAA, PCI-DSS, SOC2, GDPR) and how results may be mapped to those controls.
13. Liability, insurance & indemnity
Limitation of liability clause and any caps.
Proof of professional indemnity / cyber insurance if applicable.
Vendor responsibilities in case of an incident caused by testing.
Key factors that influence penetration testing cost
While two quotes may look similar on the surface, several key factors can significantly affect the overall cost of a penetration testing quote.
1. Scope and number of assets
The scope defines exactly what will be tested. This section typically lists:
The number of web applications, servers, or IP addresses in scope
Specific environments (production, staging, or internal)
Exclusions or limitations (e.g., third-party systems)
The broader the scope, the more detailed and resource-intensive the engagement becomes, directly affecting the cost and timeline.
2. Type of penetration testing
Each testing type comes with its own pricing model and complexity level:
Black box penetration testing: The tester has no prior knowledge of the system, simulating an external attacker. Requires more time for reconnaissance.
Grey box penetration testing: Limited access credentials provided. Balances efficiency and depth.
White box penetration testing: Full system access and source code provided. Most comprehensive and time-intensive.
Your penetration testing quote should clearly state which approach is used, as this significantly impacts pricing.
3. Testing depth
A quick vulnerability scan and an in-depth manual penetration test are vastly different in scope and value.
Automated scans cost less and can be conducted on a regular basis.
Manual assessments by ethical hackers yield deep findings but can be costly and slow.
The quote should specify how much manual testing is included and how vulnerabilities are validated.
4. Compliance requirements
If your organization needs to comply with standards like ISO 27001, SOC 2, HIPAA, or PCI DSS, the penetration testing quote must reflect additional reporting and evidence requirements. Compliance-aligned tests require stricter documentation and validation, which can raise costs but are crucial for passing audits.
5. Engagement model (one-time vs regular)
Many organizations now prefer ongoing or subscription-based testing over one-time engagements.
One-time tests identify vulnerabilities at a point in time.
Continuous testing (monthly or quarterly) ensures sustained protection against evolving threats.
Regular engagements often come with discounted pricing per test and deliver stronger long-term security outcomes.
Common mistakes to avoid when evaluating a penetration testing quote
Understanding a penetration testing quote is one thing, evaluating it wisely is another. Avoiding common pitfalls can save both money and reputation.
1. Choosing vendors purely on price
Opting for the cheapest quote can lead to incomplete assessments or low-quality reports.
A quote that seems “too good to be true” often excludes critical deliverables like manual testing or remediation validation. Always prioritize depth and expertise over cost alone.
2. Ignoring retest or remediation validation
The goal of penetration testing isn’t just to find vulnerabilities, it’s to ensure they’re fixed effectively.
A comprehensive penetration testing quote should include retesting to confirm whether remediation steps were successful. Without it, you risk remaining vulnerable even after mitigation efforts.
3. Overlooking cloud or third-party integrations
Modern applications often depend on cloud platforms or third-party APIs. Ignoring these integrations in the testing scope can leave major blind spots.
Make sure your quote specifies whether cloud infrastructure, APIs, or integrations are included in scope.
4. Not aligning testing scope with compliance goals
If your goal is to meet specific compliance requirements, the test must be aligned with those frameworks.
For instance, a PCI DSS audit requires testing payment systems and encryption practices. If your penetration testing quote doesn’t align with such compliance targets, you may end up repeating tests later.
Penetration testing with Beagle Security
Choosing the right partner for penetration testing can make the difference between a surface-level report and true resilience.
Beagle Security is an AI-powered penetration testing platform that combines advanced automation with actionable security insights, all delivered through an intuitive and user-friendly interface.
Setup for black box penetration testing
Define the scope
Specify your URL, IP, or web application for testing.

Configure testing parameters
Choose testing depth, duration, and objectives.
Beagle Security then simulates real-world hacker behavior with zero prior knowledge of the system, delivering results that reflect your actual exposure to external threats.
This approach gives organizations clear visibility into their true security posture and highlights weaknesses that could be exploited by attackers.
Setup for grey box penetration testing
Providing limited credentials or session details allows testers to simulate insider-level access during security assessments. Beagle Security securely manages these authentication workflows and user permissions, enabling safe and controlled testing.
With authenticated access, the scope expands to include deeper application areas, uncovering vulnerabilities and misconfigurations that traditional unauthenticated scans often miss.
This balanced approach combines the realism of black box testing with the contextual depth of internal assessments, offering comprehensive risk coverage.
Key platform features
Business logic recorder
Captures multi-step workflows such as login, checkout, or data submission processes, enabling business logic testing beyond simple endpoint scanning.
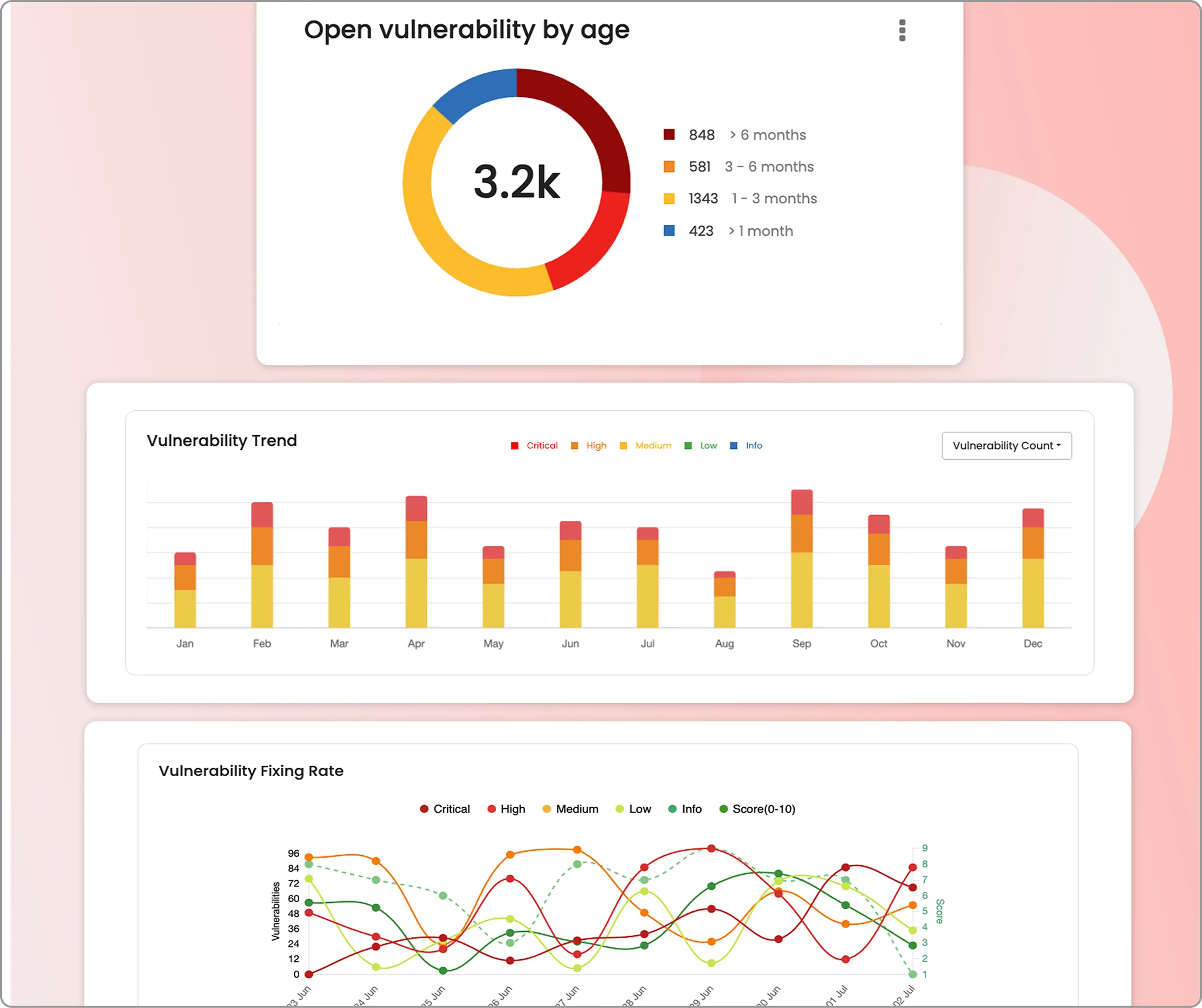
Real-time results dashboards
Monitor penetration testing progress, view executive summaries for leadership, and access technical reports for engineers all within a single interface.
Compliance-ready reports
Automatically map findings to frameworks like OWASP Top 10, PCI DSS, SOC 2, and HIPAA. This ensures your penetration testing results are audit-ready and aligned with industry standards.
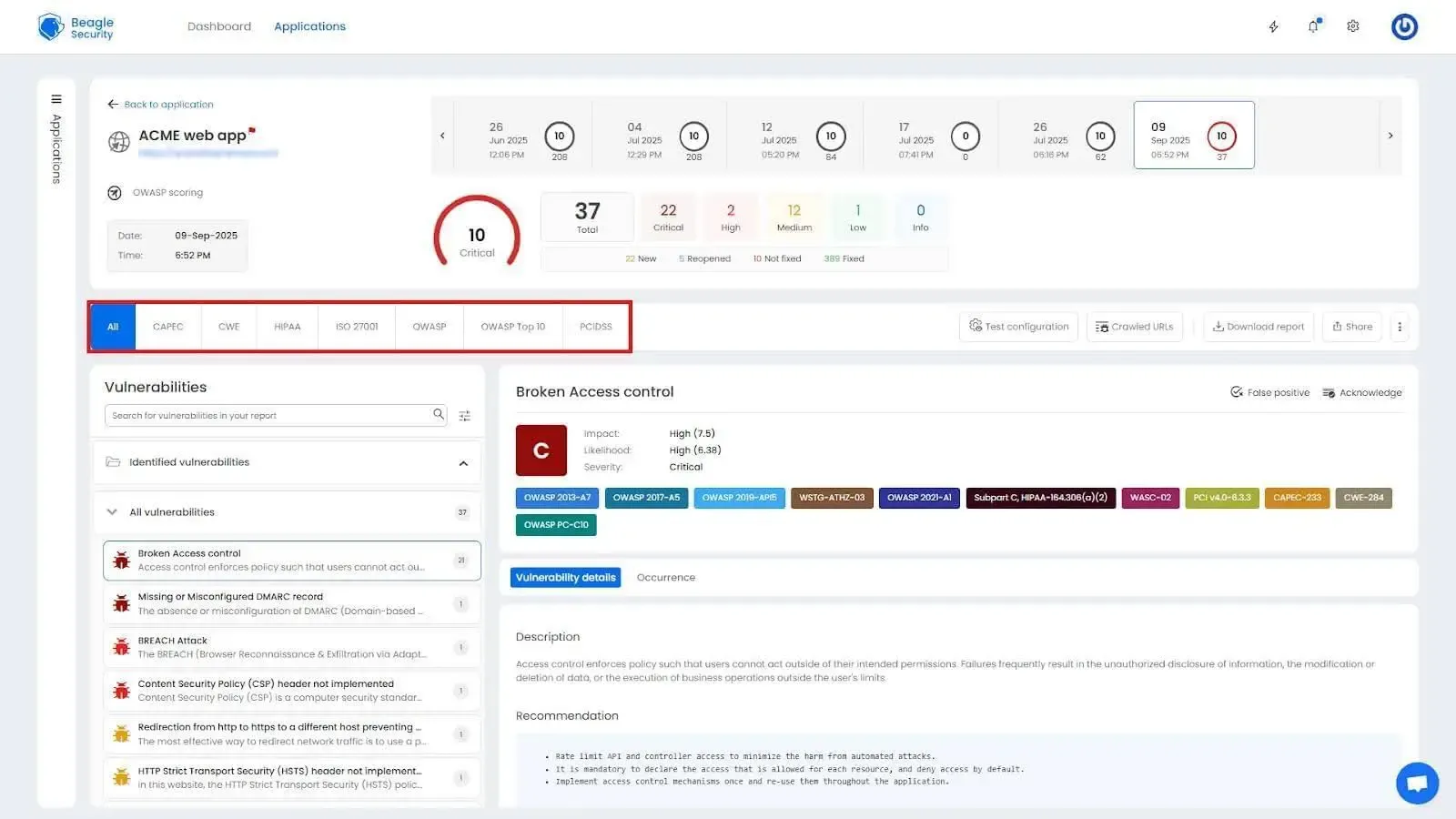
Collaboration and integration tools
Assign vulnerabilities, track remediation status, and integrate results into CI/CD pipelines for faster fixes and DevSecOps automation.
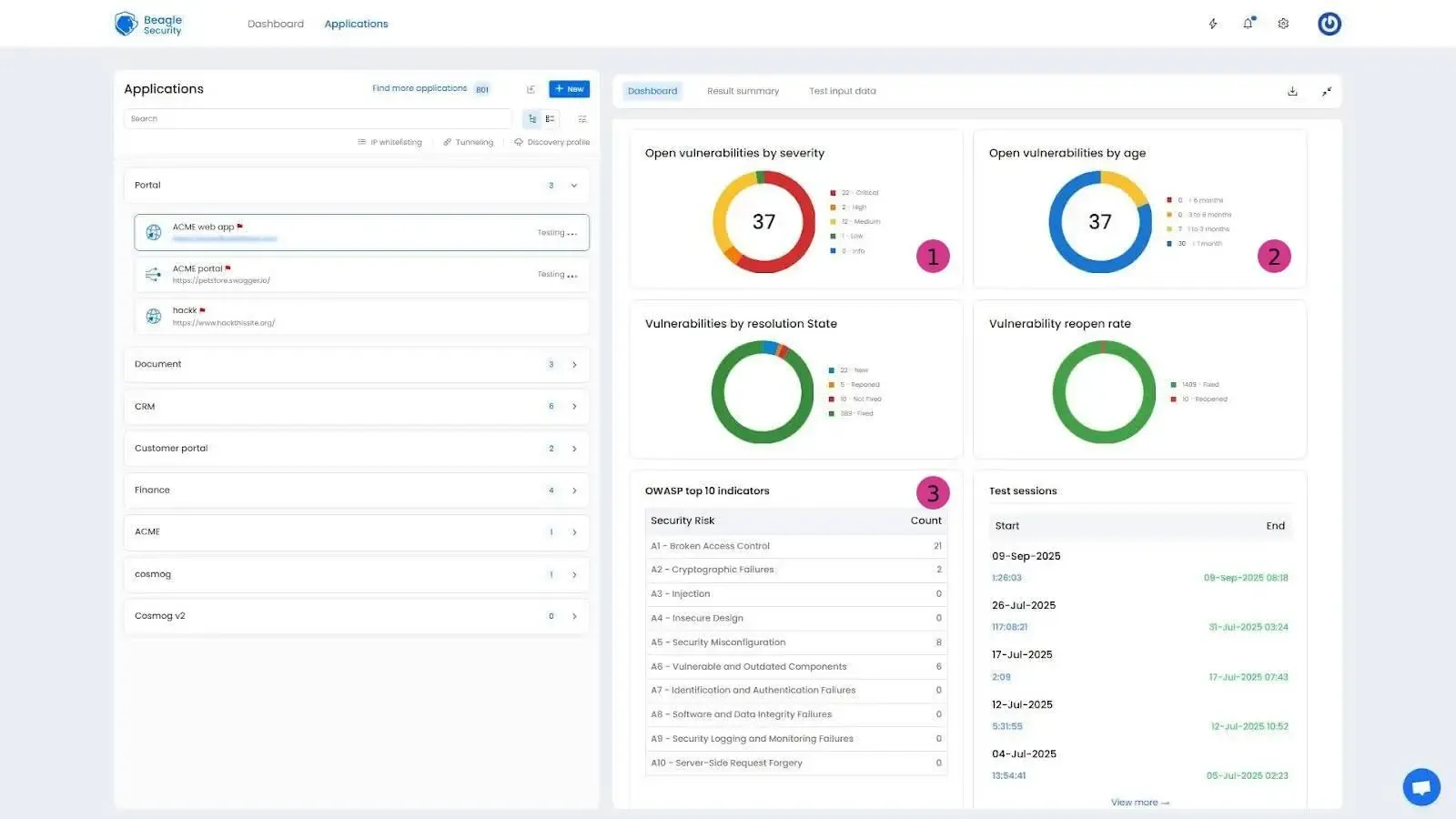
Whether you’re evaluating a penetration testing quote for a single application or planning an ongoing security program, Beagle Security offers the flexibility, depth, and compliance assurance your business needs to stay protected against evolving threats. We also offer a plan starting from $119 that can meet all your pentesting quote needs.
Final thoughts
Understanding penetration testing quotes helps you evaluate vendors objectively, align testing efforts with compliance and business goals, and ensure that every dollar spent drives measurable risk reduction.
When reviewing quotes, always ask:
Does the scope cover all critical assets?
Is manual testing included?
Are remediation and retesting part of the package?
Does the methodology align with recognized standards?
By asking the right questions and partnering with a trusted provider like Beagle Security, you can move beyond checkbox testing toward continuous, intelligence-driven protection.
When you request a penetration testing quote from Beagle Security, you get a transparent breakdown of scope, methodology and cost, empowering you to make data-driven decisions without hidden surprises. Check out our 14-day advanced free trial to see if we’re the right fit for you.
FAQ
1. How much should a penetration test cost?
A penetration test typically costs between $3,000 and $50,000+, depending on scope, complexity, and testing methodology.
2. Do penetration testing quotes vary based on methodology?
Yes. Costs differ based on whether the test is black box, grey box, or white box, as each requires different access levels and effort.
3. Is an internal penetration testing quote different from an external one?
Yes, internal tests usually cost more because they involve on-site or VPN access and deeper network analysis compared to external tests.
4. Why is my vulnerability assessment quote much cheaper than a penetration testing quote?
A vulnerability assessment only scans for issues, while a penetration test actively exploits and validates them, providing more in-depth insights.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)