
As healthcare applications and APIs evolve to handle massive volumes of sensitive patient data, HIPAA penetration testing has become a cornerstone of modern healthcare cybersecurity. The Health Insurance Portability and Accountability Act (HIPAA) mandates strict safeguards around Protected Health Information (PHI), but compliance alone doesn’t guarantee security.
Whether you’re setting up your first automated HIPAA testing pipeline, configuring authenticated scans for a complex EMR system, or preparing for an external audit, this guide provides a practical roadmap. By the end, you’ll have a clear understanding of how to design, execute, and maintain an efficient HIPAA penetration testing process that enhances both compliance and resilience.
What is HIPAA penetration testing?
HIPAA penetration testing is the process of simulating cyberattacks on healthcare systems, applications, or data environments to assess their resilience against unauthorized access, data breaches, or compliance violations under the Health Insurance Portability and Accountability Act (HIPAA).
Unlike general web application testing, HIPAA penetration testing goes beyond identifying vulnerabilities. It ensures that Protected Health Information (PHI) is properly safeguarded in line with HIPAA’s Security Rule.
In practical terms, a HIPAA penetration test evaluates:
Application security controls (authentication, access control, data validation)
Infrastructure resilience (network segmentation, firewalls, endpoint security)
Data storage and transmission (encryption standards, TLS/SSL configuration)
User access management (least privilege, audit logging)
Third-party and API integrations handling PHI
When done correctly, HIPAA penetration testing provides both a technical and procedural validation of how well a healthcare organization can protect sensitive health data in real-world attack scenarios.
What is the purpose of a HIPAA penetration test?
The purpose of HIPAA penetration testing is not simply to find vulnerabilities, it’s to prove due diligence in protecting PHI and demonstrate compliance with regulatory expectations.
Here’s what a structured HIPAA penetration testing methodology achieves:
Identify security weaknesses across applications, APIs, and infrastructure handling PHI
Validate HIPAA Security Rule compliance, specifically around administrative, physical, and technical safeguards
Test incident response readiness by simulating data breach attempts
Measure remediation effectiveness after patches and configuration updates
Build audit-ready reports that show traceable, verifiable security posture improvements
For DevSecOps engineers and AppSec teams, integrating automated HIPAA penetration testing into CI/CD pipelines ensures that every release is tested for compliance gaps before deployment.
How long does a HIPAA pentest take?
The duration of a HIPAA penetration test depends on several factors, including the scope, complexity, and testing methodology used.
| Aspect | Automated HIPAA testing | Manual HIPAA penetration testing |
|---|---|---|
| Primary HIPAA objective | Continuous identification of technical vulnerabilities affecting ePHI | Validate real-world exploitability and support formal HIPAA risk analysis |
| Execution time (small HIPAA app) | Hours to a few days | 1–2 weeks |
| Execution time (enterprise healthcare environment) | Several days to ~2 weeks | 3–6 weeks (sometimes longer for hospitals, EHR integrations) |
| Frequency in HIPAA programs | Continuous or per release | Annual or after major system changes |
| Best use case | Ongoing security monitoring for systems handling ePHI | Compliance-driven assessments and assurance for leadership |
For organizations transitioning from manual to automated HIPAA testing, it’s advisable to start with a pilot run covering core assets, then gradually expand the scope as reporting, triage, and remediation workflows mature.
Phases of a HIPAA penetration test
Below are the key phases every covered entity or business associate should understand when preparing for a HIPAA-compliant security assessment.
1. Planning & scoping
In this phase, the pentesting team collaborates with your organization to define objectives, scope, and compliance requirements. This includes identifying critical systems that handle PHI, determining test boundaries, and ensuring testing aligns with HIPAA Security Rule safeguards.
2. Reconnaissance & information gathering
Testers collect intelligence about your network, applications, and infrastructure. This stage mimics how real attackers operate by mapping assets, discovering open ports, and profiling technologies to identify potential weak spots before exploitation.
3. Vulnerability identification
Using both automated tools and manual analysis, testers uncover security flaws such as misconfigurations, outdated software, weak authentication, and insecure APIs. At this stage, risk severity is correlated with potential impact on PHI confidentiality, integrity, and availability.
4. Exploitation
Once vulnerabilities are identified, ethical hackers attempt controlled exploitation to validate their real-world impact. The goal is to demonstrate how an attacker might gain unauthorized access to PHI or disrupt healthcare operations.
5. Post-exploitation & analysis
This phase involves assessing the depth of compromise and documenting findings. It helps determine lateral movement possibilities, privilege escalation risks, and data exposure levels relevant to HIPAA’s Administrative, Technical, and Physical Safeguards.
6. Reporting & remediation
The final report details each vulnerability, its HIPAA relevance, risk rating, and actionable remediation steps. A strong pentesting partner also conducts a remediation validation to ensure fixes are correctly implemented and compliance gaps are closed.
How to choose the right HIPAA pentesting partner
Choosing the right partner for HIPAA penetration testing is crucial not just for compliance, but for ensuring actionable insights that improve real-world security posture.
Here’s what to look for when evaluating a HIPAA pentesting partner:
1. Healthcare-focused expertise
Look for teams with a proven record in healthcare and familiarity with HIPAA, HITECH, and HITRUST frameworks. Domain knowledge ensures that findings are mapped to compliance requirements, not just CVSS scores.
2. Support for authenticated scans
Modern healthcare apps often use complex authentication (SSO, OAuth, JWT tokens). Your pentesting platform should support authenticated DAST to test real-user journeys and sensitive operations involving PHI.
3. Compliance-ready reporting
Ensure the vendor delivers HIPAA-aligned reports with evidence of technical safeguards, remediation guidance, and audit references. Reports should be exportable for internal compliance teams or third-party assessors.
4. Continuous testing capability
Static one-time assessments no longer suffice. Choose a partner that enables continuous or scheduled penetration testing within your CI/CD workflow, ensuring every release remains HIPAA-compliant.
How Beagle Security can help
Protecting Protected Health Information (PHI) isn’t just a compliance checkbox, it’s a critical responsibility for every healthcare organization and their technology partners. The challenge? Traditional penetration testing can be complex, time-consuming, and difficult to scale within fast-moving development environments.
That’s where Beagle Security comes in. Purpose-built for modern AppSec and DevSecOps teams, Beagle Security helps organizations simplify and continuously automate their HIPAA penetration testing lifecycle. From authenticated scans to compliance-ready reports, it provides everything needed to maintain HIPAA Security Rule adherence without slowing down innovation.
Here’s how Beagle Security fits seamlessly into healthcare security workflows:
1. Automated HIPAA-focused DAST
Beagle Security delivers automated Dynamic Application Security Testing (DAST) tailored for HIPAA compliance. It continuously scans your web applications, APIs, and patient portals for vulnerabilities that could expose PHI or disrupt healthcare operations.
Unlike generic scanners, Beagle Security’s testing engine maps findings directly to HIPAA Security Rule requirements ensuring every vulnerability is evaluated not just by technical risk, but by its potential compliance impact. This includes identifying insecure configurations, exposed data endpoints, weak encryption, and session management flaws commonly found in healthcare web systems.
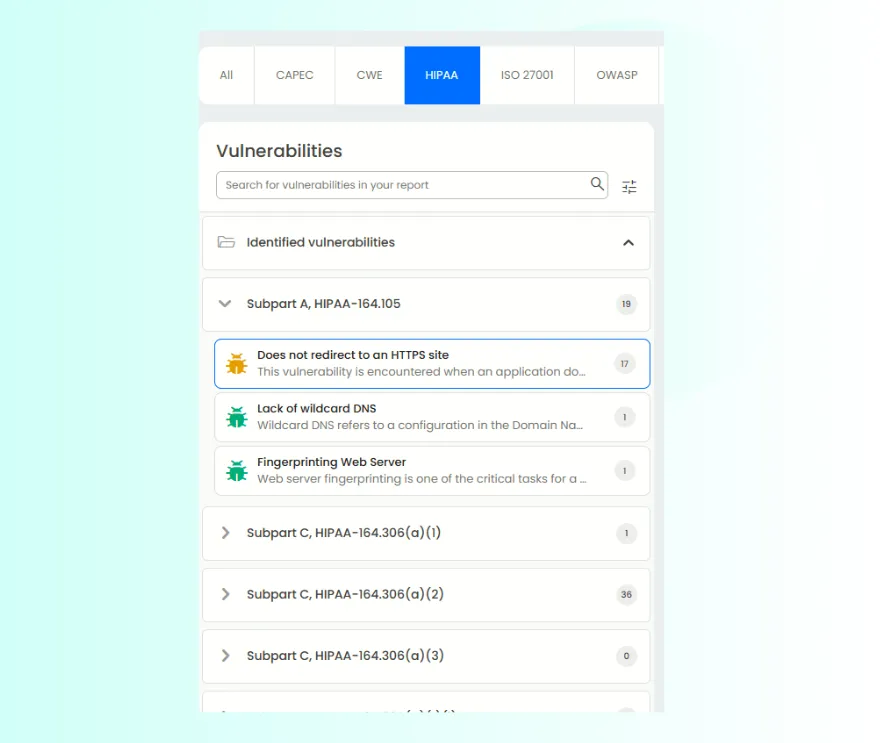
2. Authenticated testing for real-world scenarios
HIPAA applications are rarely public-facing; they’re protected by logins, tokens, and access controls. Beagle Security supports authenticated scans using session cookies, bearer tokens, or custom authentication flows, allowing realistic testing of user dashboards, Electronic Medical Record (EMR) systems, and patient engagement portals.
This ensures the assessment reflects how attackers might exploit internal vulnerabilities after gaining authorized access. It’s particularly valuable for testing features like medical data uploads, appointment management, or healthcare payment modules.
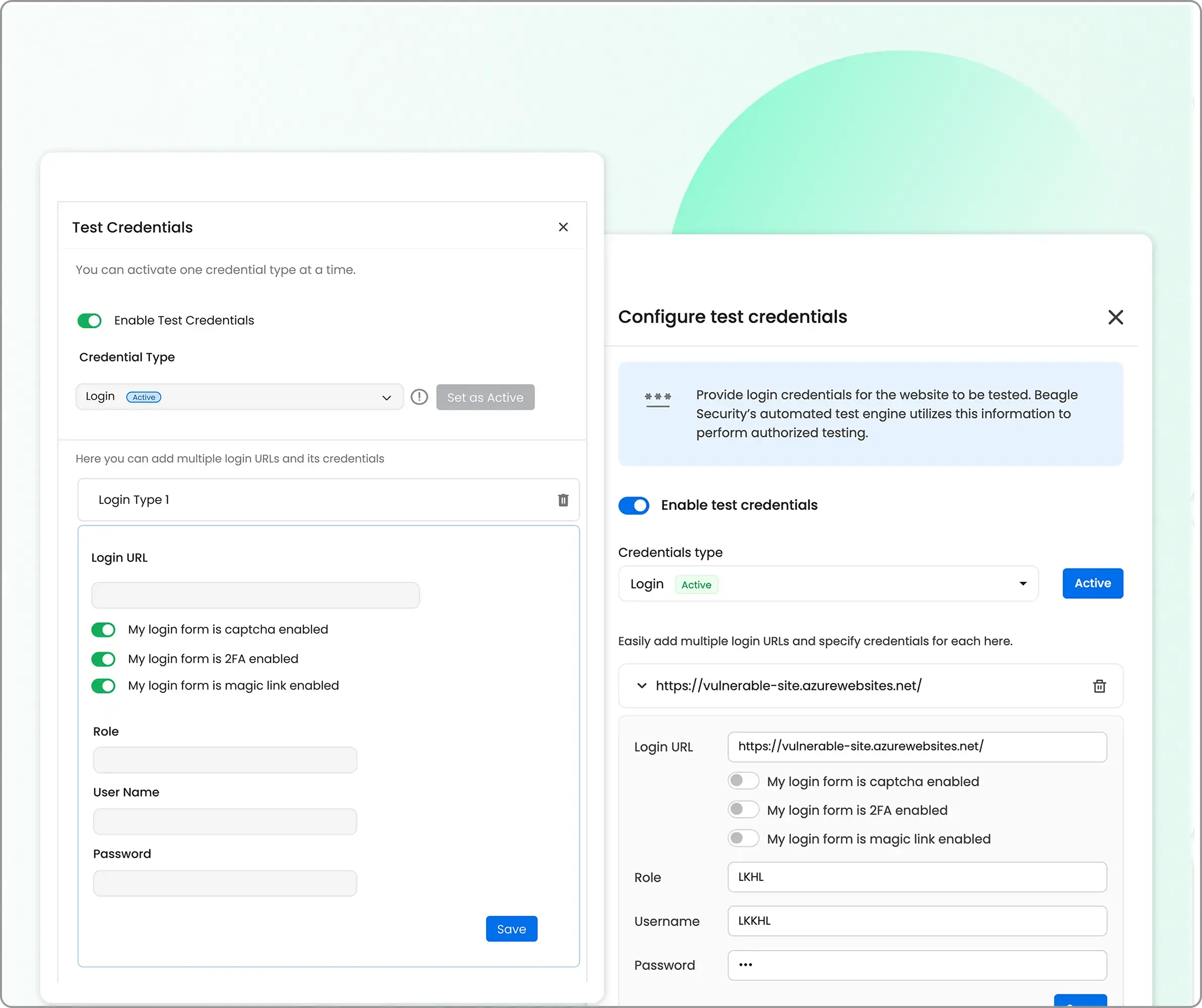
3. Seamless CI/CD Integration for DevSecOps
Modern healthcare applications are built for speed, so security needs to move just as fast. Beagle Security integrates natively with leading CI/CD platforms such as Jenkins, GitLab, and GitHub Actions, enabling automated penetration tests as part of your build and deployment pipelines.
This integration ensures that vulnerabilities are identified early before they reach production. Developers receive actionable, context-rich insights directly within their workflow, supporting a shift-left security approach that reduces remediation time and cost.
By embedding HIPAA penetration testing into CI/CD, Beagle Security helps healthcare DevOps teams maintain both agility and regulatory integrity.
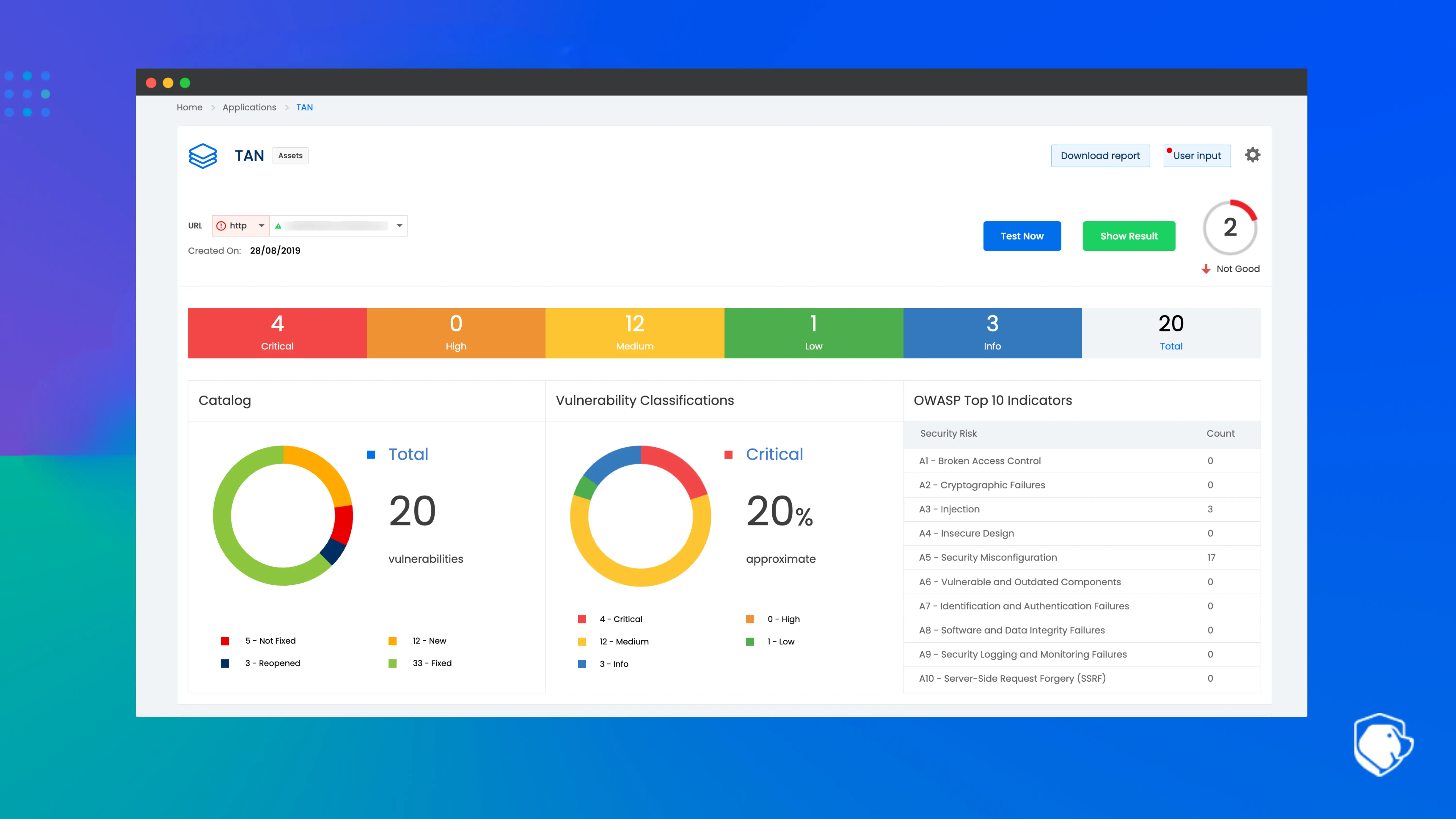
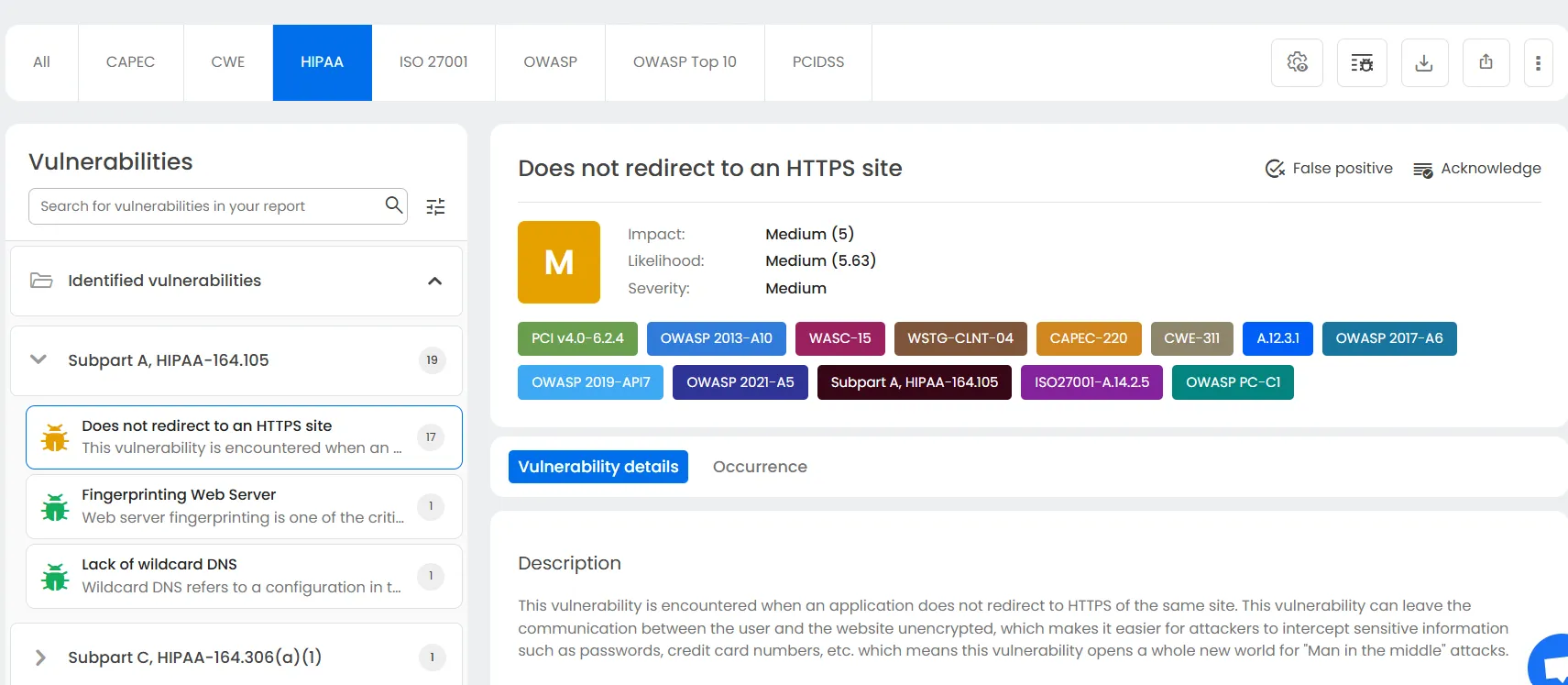
4. Compliance-ready reports and evidence packs
One of the biggest challenges in HIPAA compliance is proving that your applications are secure, not just assuming they are. Beagle Security makes this easy with audit-friendly, compliance-ready reports that map directly to HIPAA safeguards and control categories.
Each report includes:
A prioritized list of vulnerabilities with CVSS-based severity scores
Detailed remediation guidance
HIPAA safeguard mapping for every finding
Executive summaries for compliance teams and auditors
This makes Beagle Security an ideal solution for generating evidence packs during HIPAA or SOC 2 audits, showing clear proof of proactive risk management and continuous improvement.

5. Continuous vulnerability management
HIPAA compliance isn’t static, and neither are modern healthcare environments. Beagle Security enables continuous vulnerability monitoring and retesting across development sprints to ensure ongoing compliance.
Teams can schedule automated re-tests after patches, track remediation progress, and verify that vulnerabilities are resolved effectively. This continuous validation model turns HIPAA penetration testing from a once-a-year task into a living, adaptive security practice aligned with real-world development cycles.
6. Empowering healthcare security
By combining automation, contextual vulnerability insights, and HIPAA-specific compliance mapping, Beagle Security helps healthcare organizations and software vendors strengthen their security posture without slowing down delivery.
With Beagle Security, HIPAA penetration testing becomes continuous, verifiable, and developer-friendly, transforming compliance from a regulatory burden into a true competitive advantage
Final thoughts
HIPAA penetration testing is more than a regulatory checkbox, it’s a continuous security practice that validates your commitment to protecting patient data. As healthcare technology evolves, so must testing strategies.
For security engineers, AppSec teams, and DevSecOps professionals, integrating automated HIPAA penetration testing workflows ensures every deployment meets compliance standards without slowing innovation.
Platforms like Beagle Security make that journey practical and scalable helping teams shift from one-off audits to continuous, evidence-driven assurance of data protection. Check out our free 14-day advanced trial, or look into our interactive demo to see if we’re the right fit for you.
FAQ
What is the HIPAA testing framework?
It’s a structured methodology aligning penetration testing with HIPAA Security Rule safeguards covering administrative, technical, and physical protections for PHI.
What is the cost for a HIPAA penetration test?
Costs typically range from $5,000 to $25,000, depending on scope, environment complexity, and whether testing is automated or manual.
What’s the difference between PTES and HIPAA?
PTES defines a general penetration testing standard, while HIPAA mandates healthcare-specific safeguards for protecting PHI; HIPAA pentests apply PTES principles within that regulatory context.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)