![Top cybersecurity companies in India [2025] Top cybersecurity companies in India [2025]](/blog/images/blog-banner-two.webp)
India’s cybersecurity ecosystem has experienced rapid growth over the past decade, driven by nationwide digital transformation, cloud adoption, and the increasing sophistication of cyber threats. As more organizations migrate to cloud infrastructures, adopt SaaS applications, and expand digital service delivery, cybersecurity has become deeply tied to business resilience and continuity. Government initiatives like Digital India and the National Cyber Security Policy have helped accelerate both awareness and investment, positioning cybersecurity as a national priority. India has evolved into not just a consumer of cybersecurity solutions but a global producer of advanced security technologies.
The Indian cybersecurity industry has transformed from primarily service-driven models to innovation-led, product-first approaches. Companies across the country are developing modern solutions in application security, cloud security, threat intelligence, identity management, and data protection. Artificial intelligence, automation, and zero-trust architecture are at the heart of this shift, enabling organizations to move from reactive defense to proactive, continuous security. Many Indian cybersecurity firms are now globally recognized, serving Fortune 500 companies and government institutions across multiple continents.
However, for CISOs and IT leaders, selecting the right cybersecurity partners remains a complex challenge. The market is crowded, and not all solutions provide the depth, scale, or integration required for enterprise security programs. Indian organizations often require solutions tailored to local regulatory expectations, sector-specific compliance needs, and unique business models. The right cybersecurity partner must combine technological strength with practical implementation experience, strong customer support, and long-term reliability.
This guide highlights ten leading cybersecurity companies in India in 2025. These companies were selected based on industry impact, customer outcomes, innovation maturity, India-market relevance, and global competitiveness. The list spans application security, cloud security, threat intelligence, identity and access management, and data protection. Each profile below provides an overview of capabilities, key features, limitations, pricing clarity, and ratings or user sentiment to help enterprise teams make informed decisions.
Top cybersecurity companies in India [2025]
1. Beagle Security
Website: https://beaglesecurity.com
Category: AI-powered application security testing (Agentic AI Pentesting)
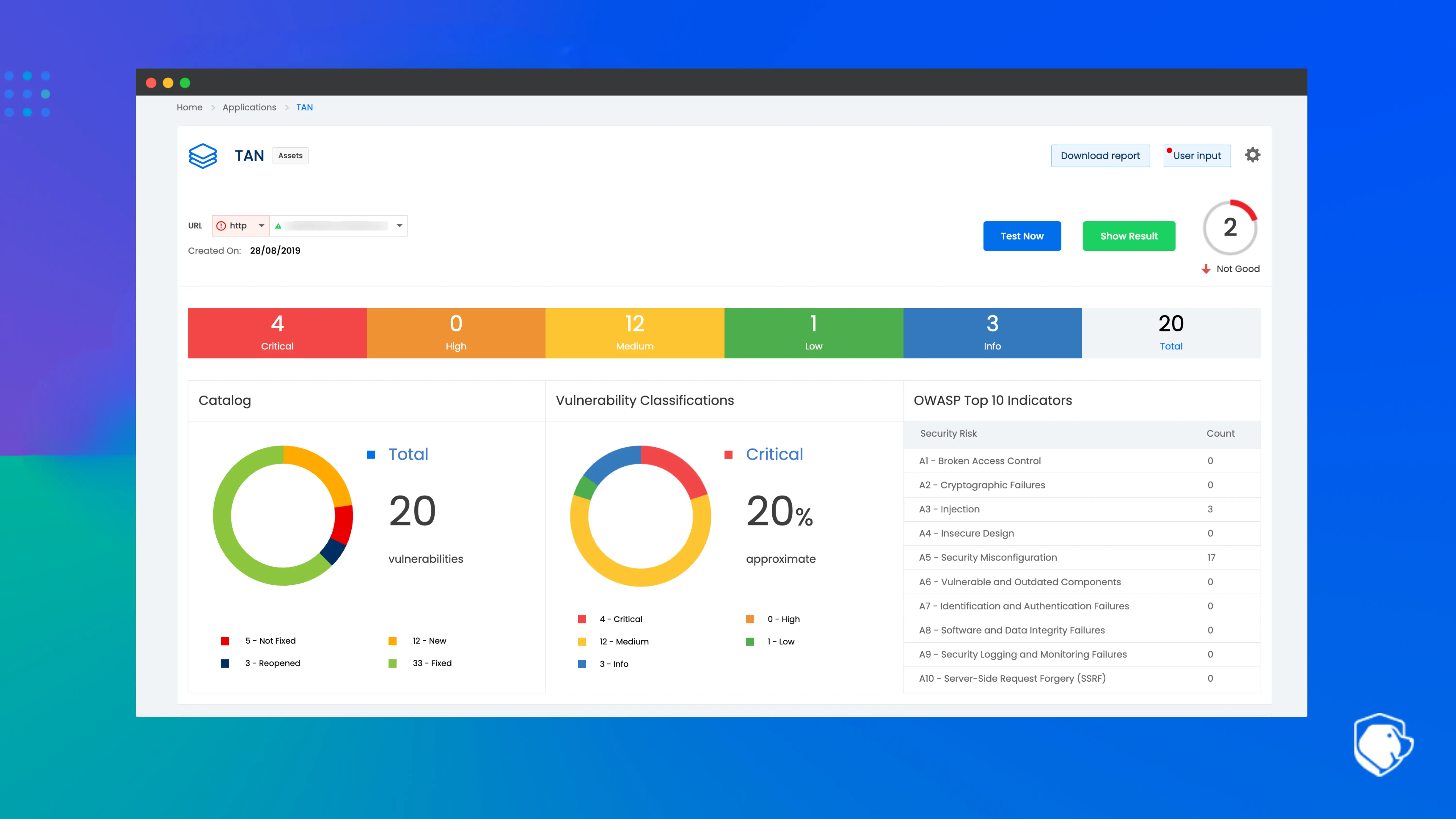
Beagle Security is one of India’s leading innovators in application security, providing AI-powered automated penetration testing for web applications and APIs. Designed for modern DevSecOps teams, Beagle Security conducts real-time attack simulations to uncover security flaws before attackers can exploit them. The platform is tailored for organizations transitioning to digital-first architectures, where application and API-layer security is critical. Beagle Security is used by startups, mid-market firms, and enterprises across fintech, SaaS, healthcare, education, and retail sectors. Its workflow-friendly design allows development teams to integrate security testing into CI/CD pipelines without slowing product releases.
The platform emphasizes continuous security, enabling organizations to detect vulnerabilities as applications evolve. Unlike traditional manual pentesting, Beagle Security’s agentic AI engine automatically identifies logic flaws, API misconfigurations, authentication weaknesses, and OWASP Top 10 risks. The system adapts to the unique architecture of each application, making it effective for microservices, serverless deployments, and multi-environment pipelines. Enterprise teams benefit from clear remediation guidance mapped directly to code and infrastructure context, improving collaboration between engineering and security functions.
Key features
AI-powered attack simulation: Uses adaptive learning to identify complex vulnerabilities in real-world conditions.
Business logic workflow testing: Models multi-step interactions to detect issues like broken access control, privilege escalation, and workflow abuse.
API-first security: Deep testing for REST, GraphQL, and microservices-based API ecosystems that are widely used in cloud-native apps.
CI/CD integration: Connects with GitHub, GitLab, Bitbucket, Jenkins, Azure DevOps, and cloud deployment pipelines for shift-left security workflows.
Continuous pentesting: Runs automated testing at defined intervals or after deployments to maintain the application security posture over time.
Validated vulnerability reporting: Eliminates false positives by confirming exploitability before reporting issues.
Compliance-ready audit reports: Generates reports aligned to ISO 27001, SOC 2, PCI DSS, HIPAA, and GDPR standards.
Developer-centric remediation guidance: Provides practical fix instructions mapped to code languages, frameworks, and configurations.
Limitations
Learning curve: Teams new to automated pentesting may require onboarding to interpret results effectively.
Focused scope: The platform specializes in application and API security and is not designed to replace infrastructure or cloud posture security tools.
Best value with workflows: Maximum benefit is achieved when integrated with CI/CD automation rather than used only for one-time tests.
Pricing
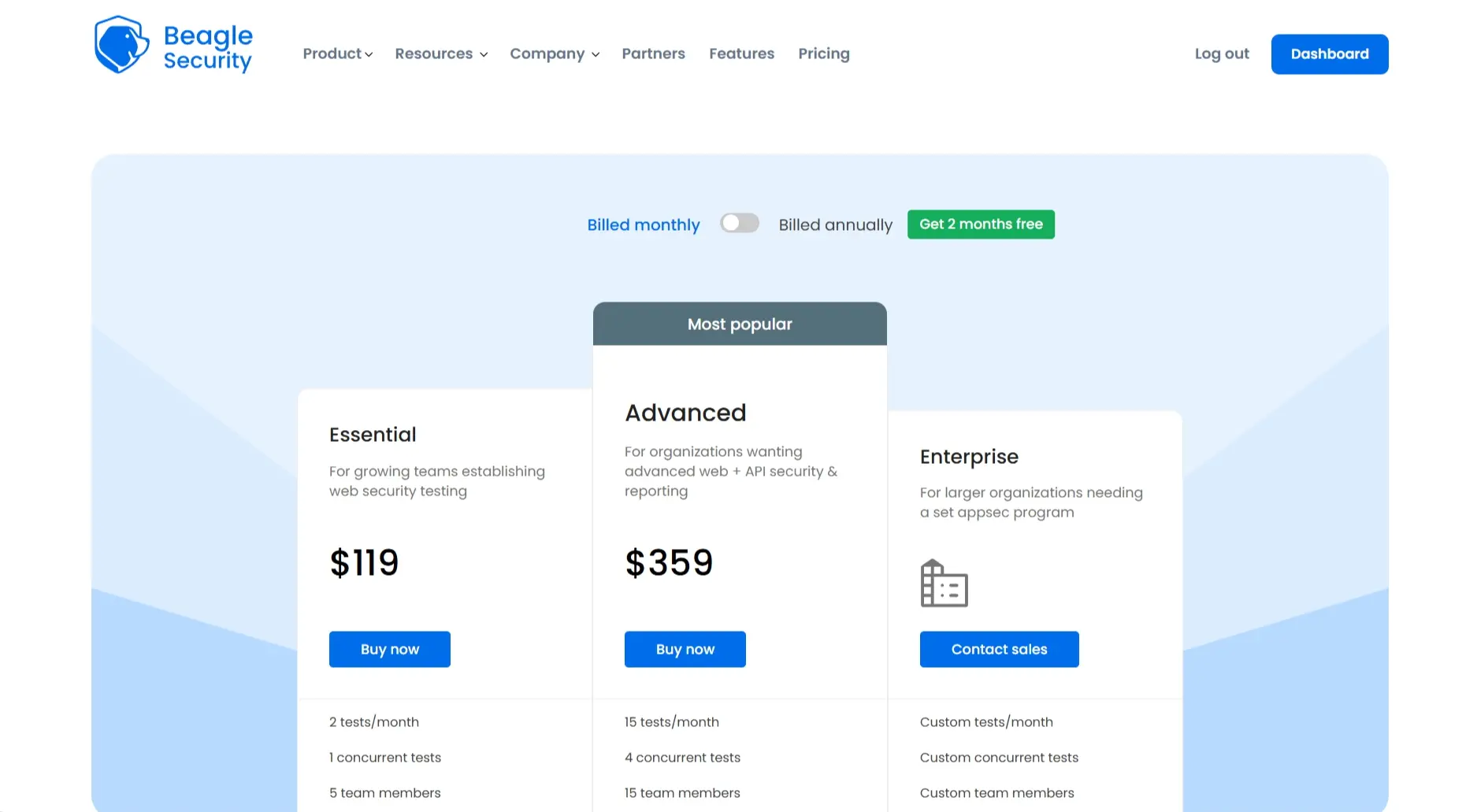
Starting price: ₹9,900 per month
Enterprise: Custom pricing available for large environments
Free trial: 14 days available
Ratings and reviews
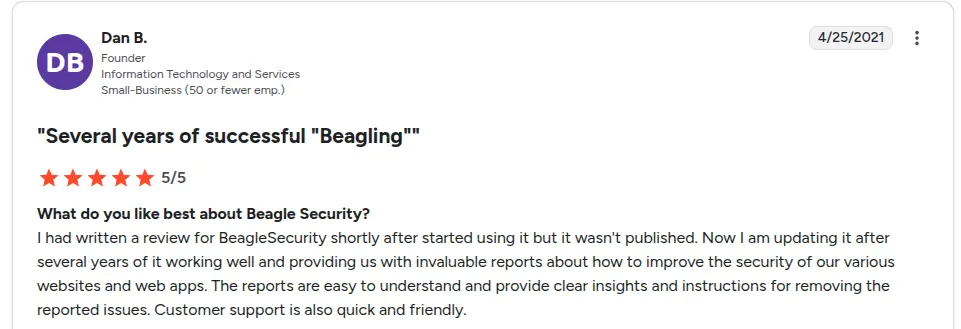
Beagle Security holds a strong rating of 4.7 on G2 from verified users. Customers consistently highlight the platform’s accuracy in vulnerability detection and the practicality of its developer-focused remediation guidance. Many reviews also emphasize its seamless CI/CD workflow integration, making it suitable for organizations scaling product delivery without compromising on security.
2. Endor Labs
Website: https://endorlabs.com
Category: Software supply chain security and dependency analysis
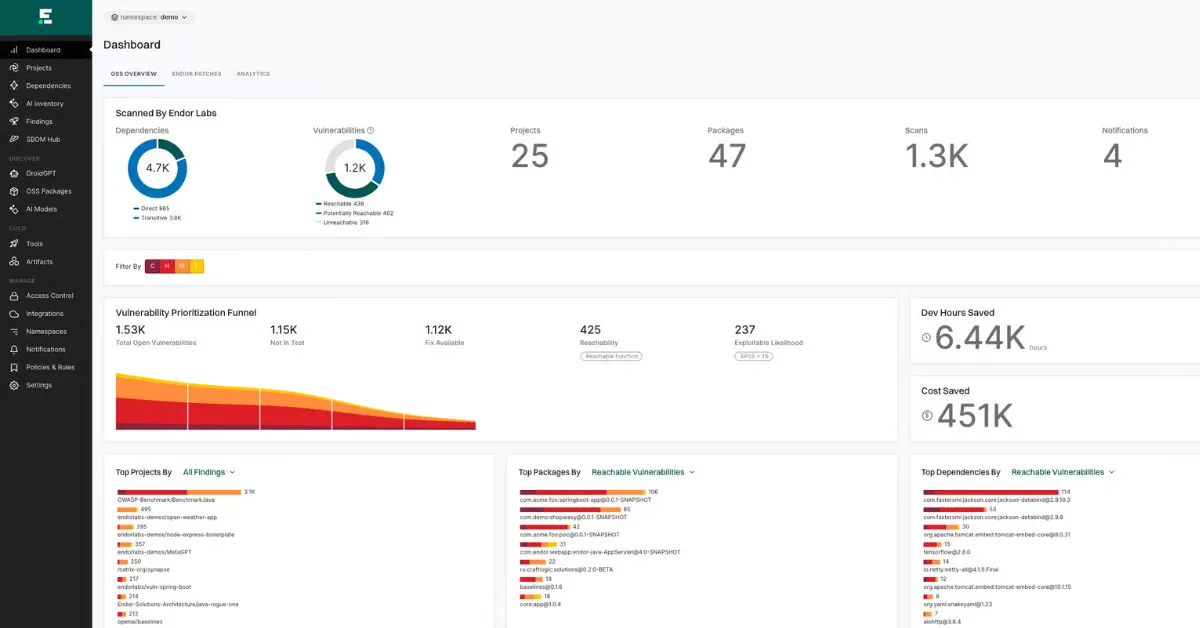
Endor Labs focuses on securing the software supply chain by analyzing and monitoring open-source dependencies used within applications. With modern applications heavily reliant on third-party code, Endor Labs helps development and security teams identify vulnerable libraries, dependency risks, version trustworthiness, and transitive dependency weaknesses. The platform is designed to reduce noise in vulnerability reporting and provide meaningful prioritization.
Key features
Dependency risk intelligence: Evaluates open-source libraries based on security maturity, community activity, and real-world exploit likelihood.
SBOM generation: Creates software bill of materials for compliance and supply chain visibility.
Vulnerability prioritization: Filters irrelevant CVEs and highlights issues that pose real exploit risk.
Policy-based governance: Ensures only approved packages and versions enter the development workflow.
Limitations
Best suited for organizations with mature DevSecOps pipelines.
Requires alignment between security and development teams for full impact.
Some advanced capabilities require enterprise-tier licensing.
Pricing
Custom pricing based on project size and development workflows.
Ratings and reviews
Endor Labs holds a G2 rating of 4.2. Users note strong supply chain visibility and practical guidance in dependency governance. Some mention that initial configuration and policy fine-tuning require dedicated onboarding time.
3. Traceable AI
Website: https://traceable.ai
Category: API security and attack surface defense
Traceable AI provides deep visibility into API behavior to prevent API-based attacks. The platform leverages runtime analysis and machine learning to profile API traffic, detect anomalies, and block malicious interactions. This is particularly valuable in microservices and distributed cloud environments, where APIs form the backbone of communication layers.
Key features
API discovery and attack surface mapping
Behavioral anomaly detection for API traffic
Protection against credential abuse, data exfiltration, and privilege misuse
Compliance reporting and API usage audit trails
Limitations
Requires traffic routing or deployment connectors.
High-volume environments may need tuning to avoid alert fatigue.
Strongest results are seen in complex distributed systems.
Pricing
Quote-based enterprise pricing.
Ratings and reviews
Traceable AI has a 4.7 rating on G2. Customers consistently highlight its ability to detect sophisticated API abuse patterns and appreciate its advanced traffic intelligence. Some users note that the initial setup may require architectural coordination for maximum coverage.
4. Indusface
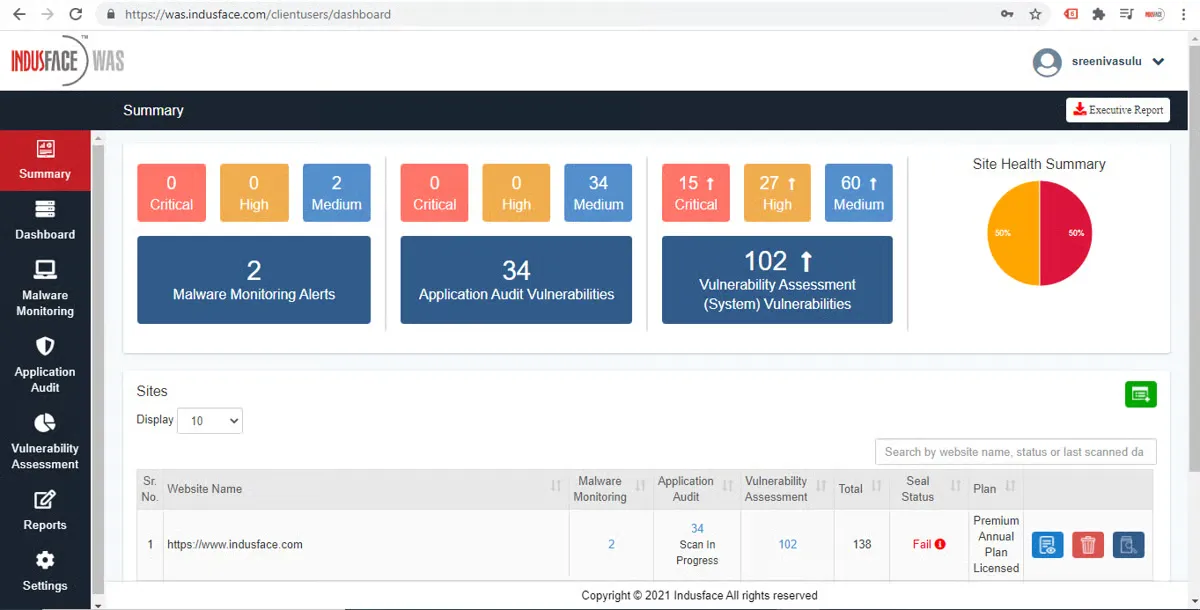
Website: https://www.indusface.com
Category: Managed web application and bot protection
Indusface provides application and website protection through a combination of web application firewall (WAF), bot management, DDoS protection, and continuous security monitoring. It is recognized for its managed model, making it suitable for organizations seeking hands-on support.
Key features
Fully managed WAF tuned by security experts
Bot detection and behavioral traffic controls
Malware scanning and website monitoring
Real-time mitigation support and risk dashboards
Limitations
Managed model may reduce customization flexibility for some engineering teams.
Best suited for web workloads vs complex distributed services.
Pricing
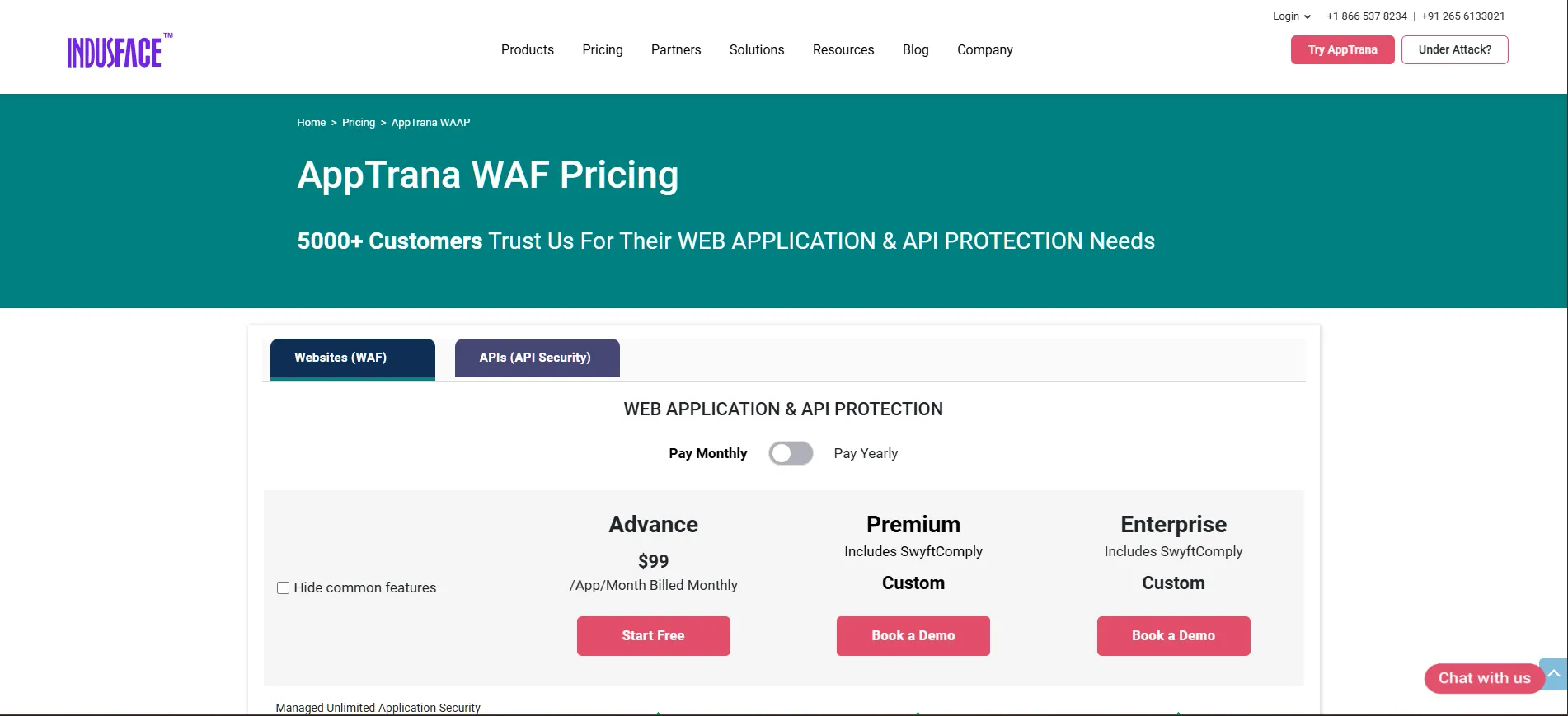
Advance: $99/month
Premium: Custom pricing
Enterprise: Custom pricing
Ratings and reviews
Indusface maintains positive sentiment among Indian enterprises, particularly for hands-on support and incident response assistance. Customers value the peace of mind offered by the managed service approach.
5. Netskope
Website: https://www.netskope.com
Category: Secure access service edge (SASE) and cloud security
Netskope helps organizations secure cloud access, SaaS applications, and remote user traffic through identity-aware gateways and real-time data control. Its solutions are widely adopted in enterprises transitioning to hybrid work and cloud-first IT models.
Key features
Real-time inspection of cloud app activity
Zero trust network access (ZTNA)
Data loss prevention policies across cloud and web usage
Unified network and security policy framework
Limitations
Configuration complexity can grow in multi-cloud environments.
Licensing may scale significantly based on user volume.
Pricing
Subscription pricing based on users and services enabled.
Ratings and reviews
Netskope is well-regarded for its strong security cloud capabilities and user experience. Enterprise teams appreciate its unified control plane for remote access and data safety.
6. Cyble
Website: https://cyble.com
Category: Threat intelligence and cyber risk observability
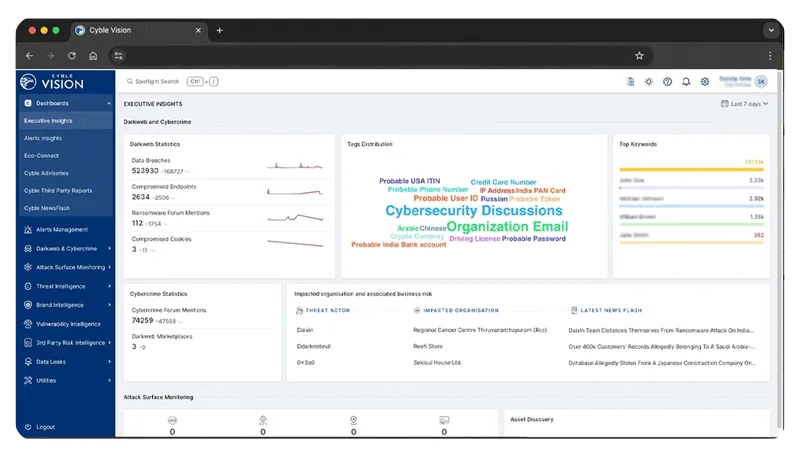
Cyble specializes in dark web monitoring, threat intelligence, ransomware tracking, and digital risk identification. It helps organizations detect leaked credentials, brand impersonation risks, exposed data, and targeted threat campaigns.
Key features
Automated dark web monitoring
Threat actor profiling and alerting
Brand and identity protection
Ransomware intelligence and predictive breach indicators
Limitations
Requires strong security operations maturity to act on intelligence.
Some organizations may need SOC or MSSP support for response workflows.
Pricing
Custom pricing based on monitored digital assets.
Ratings and reviews
Cyble holds a 4.7 rating on G2. Users highlight its extensive dark web visibility and intelligence depth. Some reviews point out that the maximum value depends on having clear incident response workflows in place.
7. Cohesity
Website: https://www.cohesity.com
Category: Data security, backup, and ransomware recovery

Cohesity provides data backup, recovery, and ransomware resilience for cloud and on-premise environments. It helps enterprises reduce the blast radius of data breaches by ensuring fast and secure recovery.
Key features
Immutable backup storage
Rapid ransomware recovery workflows
Multi-cloud data management
Compliance and audit trail tracking
Limitations
Enterprise-focused pricing
Deployment planning required for hybrid infrastructures
Pricing
Quote-based based on storage and environment scale.
Ratings and reviews

Cohesity holds a 4.4 rating on G2. Customers frequently highlight fast data restoration and encryption strength. Some note that configuration and scaling may require specialist involvement for large environments.
8. Cyware
Website: https://cyware.com
Category: Threat intelligence sharing and SOC collaboration
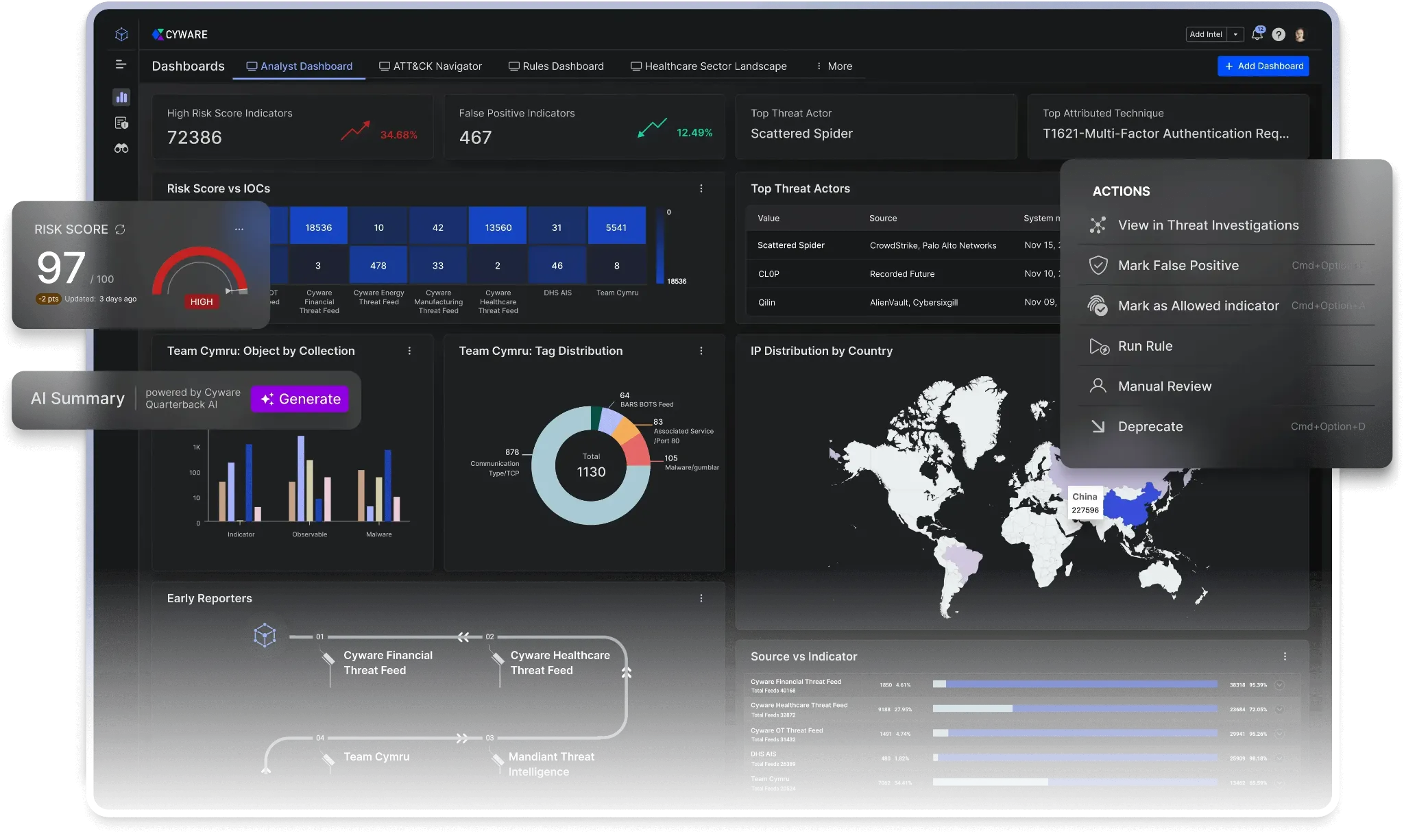
Cyware enables organizations to build advanced security collaboration environments through automated threat intelligence sharing and coordinated security response workflows. Its platform is designed for enterprises that operate distributed SOC teams, MSSPs, and government or sector collaboration groups that require unified situational awareness. Cyware supports analyst teams with intelligence normalization, correlation, and automation playbooks that reduce manual triage. It is widely used in sectors that require real-time intelligence dissemination, including banking, telecom, and energy.
Key features
Threat intelligence fusion: Collects, correlates, and enriches intelligence from multiple feeds to improve detection decisions.
Security orchestration and automation: Allows security teams to automate playbooks for incident response, phishing triage, and malware investigation.
Cross-team collaboration hubs: Enables secure intelligence sharing between internal SOC teams and external industry peers.
Case management workflows: Consolidates investigation artifacts and analyst notes into unified security cases.
Flexible deployment models: Supports on-premise, hybrid, and multi-cloud environments.
Limitations
Requires mature SOC processes to leverage automation effectively.
Initial setup and playbook design may require skilled security engineers.
Works best in organizations with structured incident response frameworks already in place.
Pricing
Custom pricing based on deployment complexity and SOC scale.
Ratings and reviews
Cyware does not have a widely referenced G2 rating. However, enterprise security teams consistently recognize Cyware for enabling collaborative threat intelligence programs and improving analyst efficiency. Many users highlight that the platform significantly enhances visibility and communication across distributed SOC environments.
9. Cequence Security
Website: https://cequence.ai
Category: API security and bot defense
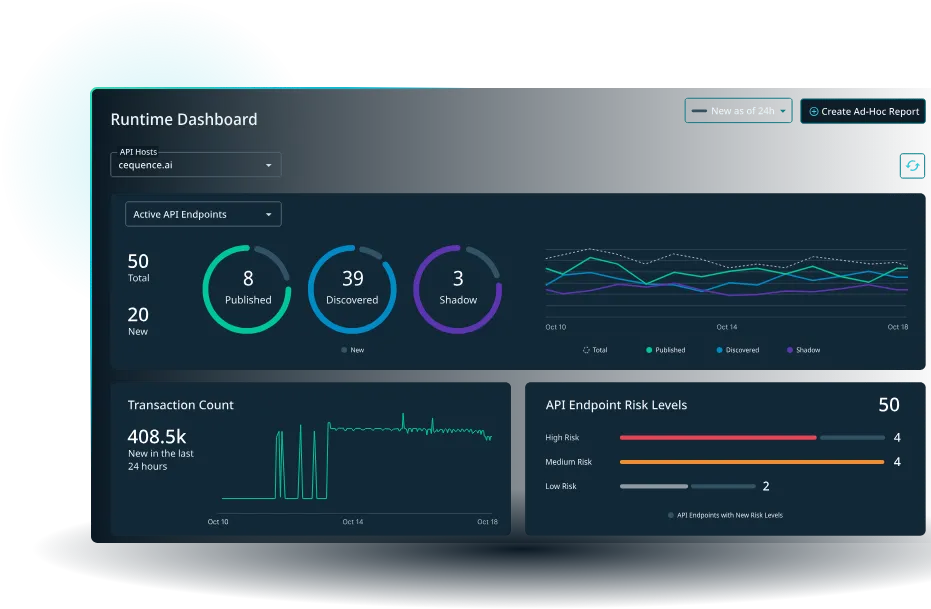
Cequence Security provides a holistic API security platform designed to detect and block bot attacks, API abuse, credential stuffing, and account takeover attempts. It is particularly effective for digital-first enterprises that rely heavily on public and private APIs to enable customer interactions and service delivery. Cequence analyzes real-time API traffic to differentiate legitimate user behavior from automated or malicious activity.
Key features
API attack surface discovery: Automatically identifies exposed APIs and evaluates associated risk.
Bot detection and mitigation: Uses behavioral analysis to prevent automated attacks such as credential stuffing and inventory scraping.
Risk scoring engine: Prioritizes threats based on impact and exploit likelihood.
Application-layer protection: Blocks malicious requests without impacting user experience.
Flexible policy engine: Allows security teams to tune enforcement based on risk tolerance.
Limitations
Complex application environments may require tuning to minimize false positives.
Deep analytics and threat modeling work best with ongoing monitoring.
Requires alignment between application engineering and security operations teams.
Pricing
Quote-based enterprise pricing tailored to application footprint and traffic volume.
Ratings and reviews
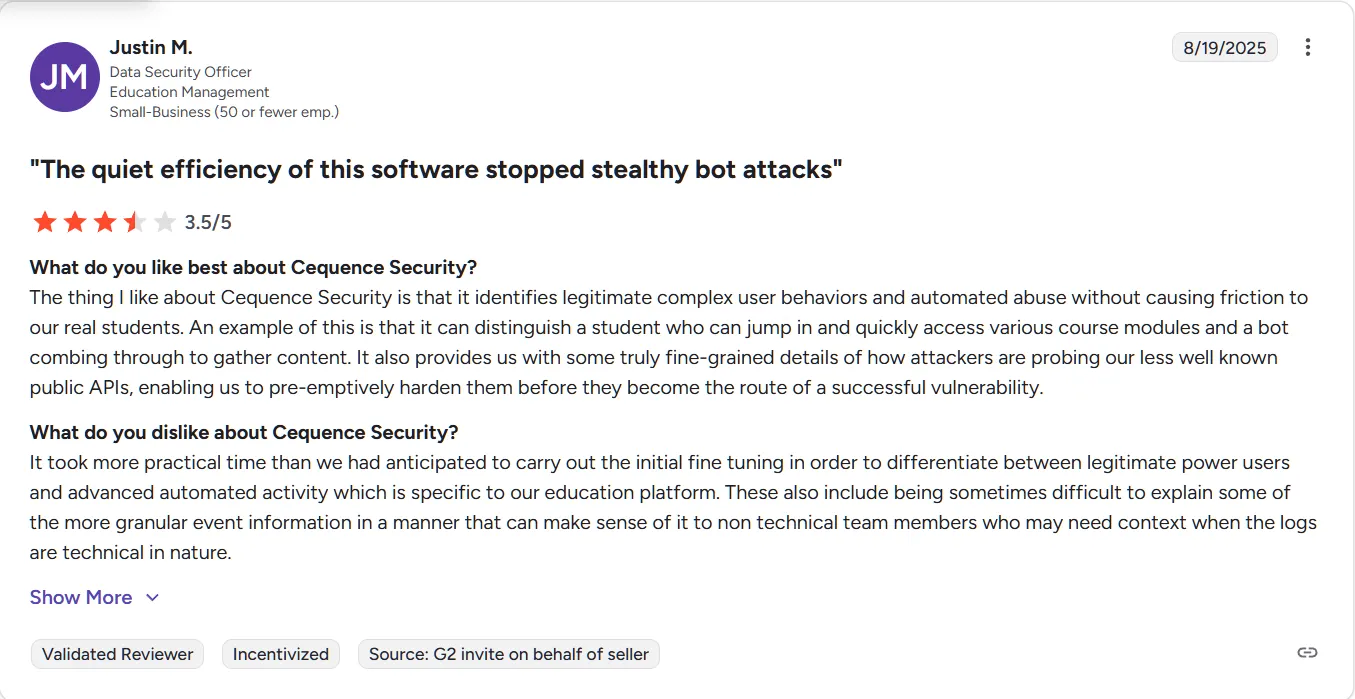
Cequence Security holds a G2 rating of 4.6. Users consistently highlight its strength in preventing bot-driven abuse and API-based attacks at scale. Many reviews note that Cequence is especially effective in industries where fraud prevention and transaction integrity are critical. Some customers mention that policy tuning and deployment planning are important to achieve optimal detection accuracy.
10. Ping Identity
Website: https://pingidentity.com
Category: Identity and access management (IAM)
Ping Identity delivers enterprise-grade identity security solutions, including single sign-on, multi-factor authentication, and identity governance. The platform is built for organizations with complex hybrid or multi-cloud identity environments where consistent access control and secure authentication are essential. Ping Identity supports passwordless authentication, federated identity, and integration with SaaS and on-premise applications.
Key features
Single sign-on across cloud and on-premise apps: Ensures seamless user access with centralized identity management.
Passwordless and adaptive authentication: Reduces credential risks and improves user experience.
Identity federation: Allows secure access across partner ecosystems and distributed business units.
Zero trust access policies: Enforces contextual access decisions based on user behavior and device posture.
Compliance and audit controls: Aligns with regulated industry requirements such as BFSI and healthcare.
Limitations
Complex enterprise identity environments may require advanced architecture planning.
Licensing can increase with large-scale user bases.
Some features require specialized IAM expertise to configure effectively.
Pricing
Custom enterprise pricing based on identity volume and deployment architecture.
Ratings and reviews
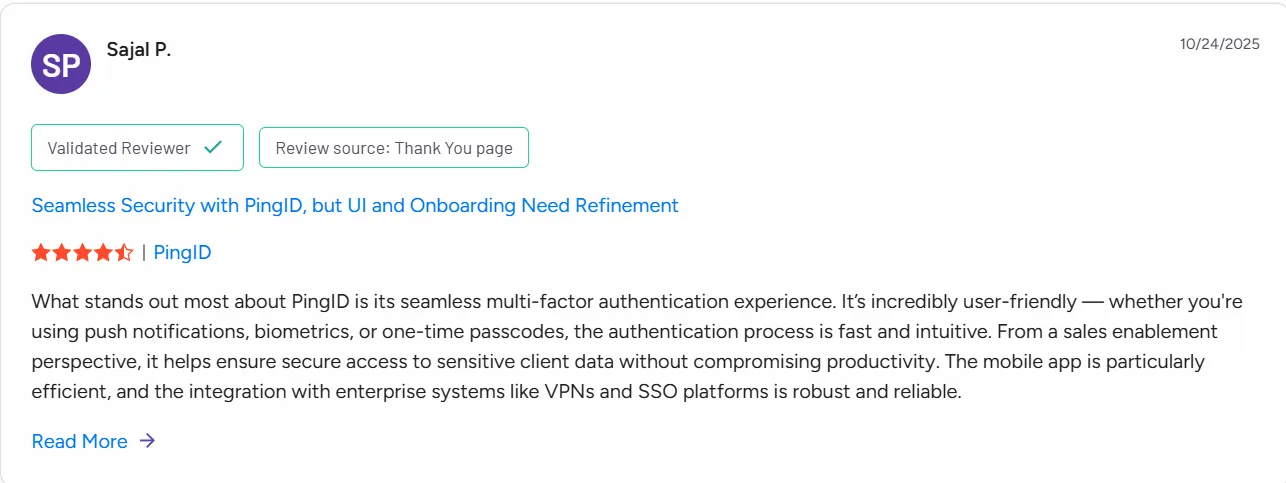
Ping Identity holds a G2 rating of 4.4. Users value its strong authentication capabilities and flexibility in hybrid cloud environments. Reviews frequently mention robust security controls and identity orchestration, while some note that setup complexity can increase in highly customized identity workflows.
Quick reference grouping
Application security: Beagle Security, Cequence Security, Traceable AI, Indusface
Cloud security and access: Netskope
Software supply chain security: Endor Labs
Threat intelligence and monitoring: Cyble, Cyware
Data protection and resilience: Cohesity
Identity and access management: Ping Identity
This grouping allows decision makers to identify companies aligned to their current security priorities.
Final thoughts
India has emerged as a significant force in global cybersecurity, with companies delivering solutions that rival and often surpass international competitors. The organizations highlighted in this list represent the best of Indian innovation and capability across application security, cloud protection, data defense, threat intelligence, and identity security. They enable enterprises to strengthen their security posture while aligning with regional regulations, operational requirements, and business needs.
Choosing the right cybersecurity partner depends on organizational priorities, digital maturity, architecture, and risk tolerance. Some organizations may require deep application testing, while others may focus on cloud infrastructure, identity governance, or ransomware recovery. It is essential for security leaders to evaluate both capability fit and integration compatibility with existing technology stacks.
As the cybersecurity landscape continues to evolve, proactive security approaches, AI-assisted detection, and continuous testing will define resilient enterprise defenses. Application security remains especially critical, as web-based applications and APIs form the primary gateway to digital services.
Beagle Security provides a globally trusted platform for AI-powered application and API penetration testing, helping Indian organizations secure their digital products without slowing development velocity.
Ready to enhance your application security?
Start a 14-day free trial of Beagle Security or schedule a call to get started with the Beagle Security platform.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)