![Top 20 cybersecurity consulting firms [2025] Top 20 cybersecurity consulting firms [2025]](/blog/images/blog-banner-two.webp)
The rise of cyber threats over the past decade has transformed cybersecurity from a technical support function into a core business priority. Organizations today operate across distributed cloud environments, remote work setups, interconnected applications, and third-party digital ecosystems. This expansion of the attack surface has created both new opportunities and new risks. As a result, cybersecurity consulting firms have become essential partners in helping companies understand their security posture, reduce vulnerabilities, and defend against evolving cyber attacks. By offering specialized expertise, strategic advisory, and hands-on threat mitigation, these firms play a critical role in safeguarding business continuity and trust.
According to multiple industry studies, the average cost of a data breach in 2025 ranges between 4.5 and 6 million USD, factoring in financial losses, operational disruption, and long-term reputational damage. Regulatory compliance mandates such as GDPR, CCPA, HIPAA, PCI DSS, NIS2, and sector-specific cyber standards have further increased the pressure on businesses to maintain strong security hygiene. At the same time, consumer trust is increasingly determined by how responsibly organizations manage and protect sensitive information. These trends continue to reinforce the value of cybersecurity consulting as both a defensive and strategic investment for organizations of all sizes.
What are cybersecurity consulting services?
Cybersecurity consulting services involve expert guidance, assessment, implementation, and ongoing support to help organizations secure their technology infrastructure, applications, data, and operational practices. Consulting firms work with companies to identify vulnerabilities, strengthen cyber defenses, design security strategies, and respond to incidents. These services may include penetration testing, security architecture design, cloud security assessment, identity and access management, threat detection, compliance advisory, and managed security operations.
These are some of the companies worth checking out.
Cybersecurity consulting firms to know
1. Beagle Security
Specialization: AppSec as a Service, AI-powered penetration testing, continuous security testing, developer-centric remediation
Beagle Security is a modern cybersecurity company that delivers application security as an ongoing service rather than through periodic consulting engagements. Its platform uses Agentic AI automated penetration testing to identify vulnerabilities in web applications and APIs, enabling development teams to discover and resolve weaknesses early in the development lifecycle. This approach supports continuous security assurance, making it well-suited for organizations adopting DevSecOps practices and releasing software frequently.
Beagle Security provides capabilities for business logic testing, authenticated application testing, and real-time vulnerability verification. The platform integrates with CI/CD pipelines such as GitHub Actions, GitLab CI, and Jenkins, allowing security testing to automatically trigger as part of development workflows. It also offers compliance reporting for frameworks such as SOC 2, PCI DSS, ISO 27001, and HIPAA, along with actionable remediation guidance tailored for engineering teams.
Beagle Security stands out for enabling teams to run penetration testing continuously without requiring lengthy consulting cycles or scheduling engagements. The platform is especially popular among SaaS companies, fintechs, and API-driven businesses that require rapid, scalable security validation.
Ratings and reviews:
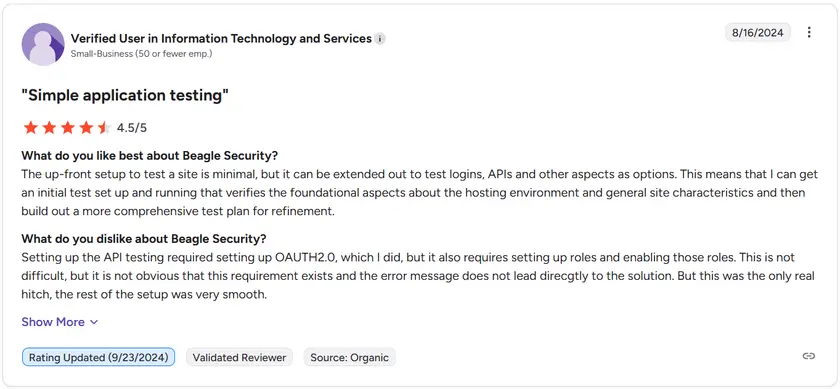
Beagle Security maintains a 4.7 out of 5 rating on G2, with customers highlighting the platform’s accuracy, ease of setup, and developer-friendly remediation experience. Users consistently praise its continuous testing approach as an effective alternative to traditional consulting-driven penetration testing.
2. Deloitte
Specialization: Cyber risk advisory, identity security, cloud security, managed SOC
Deloitte is one of the global leaders in cybersecurity advisory and consulting, working with some of the world’s largest enterprises and government organizations. The firm delivers end-to-end services across strategy, implementation, threat detection, and incident response. Deloitte’s cybersecurity practice helps organizations modernize their defenses, adopt zero trust frameworks, secure cloud architectures, and improve governance and compliance programs.
The company also operates large-scale security operations centers that monitor and respond to cyber threats in real time. Its consulting approach blends business strategy with deep technical expertise, allowing clients to align security initiatives with broader organizational goals.
Ratings and reviews:
Deloitte maintains a strong reputation with a 4.1 out of 5 rating, based on its global cybersecurity consulting performance. The firm is known for aligning enterprise cybersecurity strategy with regulatory compliance and business transformation. Clients particularly value Deloitte’s ability to support large-scale programs across cloud migration, identity governance, and risk management.
3. PwC
Specialization: Cyber strategy consulting, data protection, governance, digital trust
PwC provides cybersecurity consulting services that help organizations understand cyber risks and build long-term security resilience. Its cybersecurity practice focuses heavily on governance, compliance, privacy frameworks, security architecture, and security awareness cultural programs. PwC works with enterprises across finance, healthcare, manufacturing, critical infrastructure, and public sector environments.
The firm emphasizes risk-based security planning, helping organizations prioritize actions that align with regulatory requirements, operational needs, and organizational maturity. PwC’s global network and cross-industry expertise make it a strong partner for organizations navigating complex compliance landscapes.
Ratings and reviews:
PwC holds an overall 4.2 out of 5 rating, reflecting customer confidence in its strategic cybersecurity guidance. The company is frequently recognized for its structured frameworks and ability to help organizations meet compliance and audit expectations. Clients note PwC’s advisory strength in governance, cyber maturity assessments, and large transformation programs.
4. EY
Specialization: Cybersecurity strategy, identity management, risk consulting, threat exposure analysis
EY helps organizations assess cyber risks, define long-term security strategies, and implement controls that reduce exposure. Its consulting teams focus on identity and access management, data privacy, operational technology security, and threat intelligence. EY works with large enterprises and government agencies that require mature risk governance and compliance assurance.
The firm’s cybersecurity framework emphasizes resilience and business continuity, helping clients prepare for breach scenarios and recover efficiently. EY is also recognized for its thought leadership in emerging cybersecurity policy and risk management practices.
Ratings and reviews:
EY has earned a consistent 4.2 out of 5 user rating for its cybersecurity consulting and advisory practices. Reviews highlight the firm’s expertise in identity management, risk frameworks, and secure digital transformation. Enterprises particularly appreciate EY’s ability to integrate cybersecurity with continuity planning and enterprise resilience initiatives.
EY is highly rated for executive-level cybersecurity advisory and organizational cyber risk assessments. Clients appreciate its expertise in aligning cybersecurity programs with business priorities and compliance standards.
5. KPMG
Specialization: Incident response, risk management, cyber governance, cloud security assurance
KPMG provides cybersecurity consulting focused on helping organizations identify risks, secure cloud environments, and improve governance frameworks. The firm offers incident response services to support organizations during active breaches, including forensic analysis and containment efforts. KPMG also collaborates with enterprises undergoing major digital transformation, helping secure cloud adoption and data migration initiatives.
The firm’s structured approach enables clients to mature their cybersecurity capabilities and strengthen internal processes for sustained resilience. Its consulting teams are known for strong regulatory and compliance knowledge, particularly in financial and government sectors.
Ratings and reviews:
KPMG carries a steady 4.2 out of 5 customer rating across its cybersecurity and risk advisory services. Many organizations note KPMG’s governance-focused approach and strength in regulated sectors like BFSI and government. Clients also point out the firm’s structured methodology in conducting audits, assessments, and compliance-driven engagements.
6. IBM
Specialization: Security architecture engineering, threat intelligence, managed detection and response
IBM operates one of the most extensive cybersecurity consulting and managed services businesses globally. IBM Security provides strategic advisory, implementation, and 24/7 managed threat detection. Its services are powered by QRadar SIEM, IBM X-Force threat intelligence, and a global network of security operations centers.
Clients work with IBM to design secure cloud and hybrid architectures, deploy zero trust controls, automate security workflows, and enhance detection and response readiness. IBM’s scale and research-backed threat intelligence allow it to support large and highly complex environments.
Ratings and reviews:
IBM Cybersecurity Consulting is rated 4.0 out of 5, supported by feedback on its global threat intelligence from IBM X-Force and managed SOC capabilities. Clients value IBM’s ability to handle complex enterprise environments involving hybrid cloud and legacy systems. The combination of advisory and hands-on security operations is cited as a notable advantage.
7. Accenture
Specialization: End-to-end security transformation, managed security, cloud security consulting
Accenture provides large-scale cybersecurity consulting services with a focus on digital transformation and cloud-first environments. The company offers threat detection, vulnerability assessment, identity management, and cloud security design. It also manages global SOC operations for organizations needing fully outsourced security operations.
Accenture works closely with hyperscale cloud providers and major enterprise platforms, enabling clients to modernize infrastructure while maintaining strong security controls. The firm is also active in security automation and AI-driven defense programs.
Ratings and reviews:
Accenture receives a 4.2 out of 5 rating for its end-to-end cybersecurity transformation services. Clients highlight Accenture’s scale, industry-specific security frameworks, and strong cloud security capabilities. Its integration with infrastructure modernization programs is frequently mentioned as a differentiator.
8. Wipro
Specialization: Managed security services, cloud security, SOC operations, digital identity
Wipro is one of India’s largest cybersecurity service providers, supporting global enterprises with security operations management, cloud security consulting, and identity and access management. The company delivers managed SOC services, threat monitoring, and incident response across hybrid cloud environments.
Wipro works heavily with enterprises undergoing modernization and migration to cloud-native systems. Its cybersecurity practice emphasizes automation and threat analytics to improve defense efficiency.
Ratings and reviews:
Wipro’s cybersecurity practice holds a 4.1 out of 5 customer rating, reflecting its established presence in managed security services. Enterprises appreciate Wipro’s global delivery operations, incident response support, and identity access management services. Customers also mention the benefit of Wipro’s long-term engagement flexibility.
9. TCS
Specialization: Enterprise cybersecurity consulting, cloud security, identity services, risk governance
Tata Consultancy Services offers comprehensive cybersecurity consulting and managed security services to large enterprises across sectors. TCS supports organizations in designing secure architectures, transitioning to cloud environments, strengthening endpoint security, and improving resilience to advanced threats.
The firm’s cybersecurity consulting practice integrates with its broader digital transformation services, allowing customers to embed security throughout modernization efforts. TCS also operates global security operations and threat research centers.
Ratings and reviews:
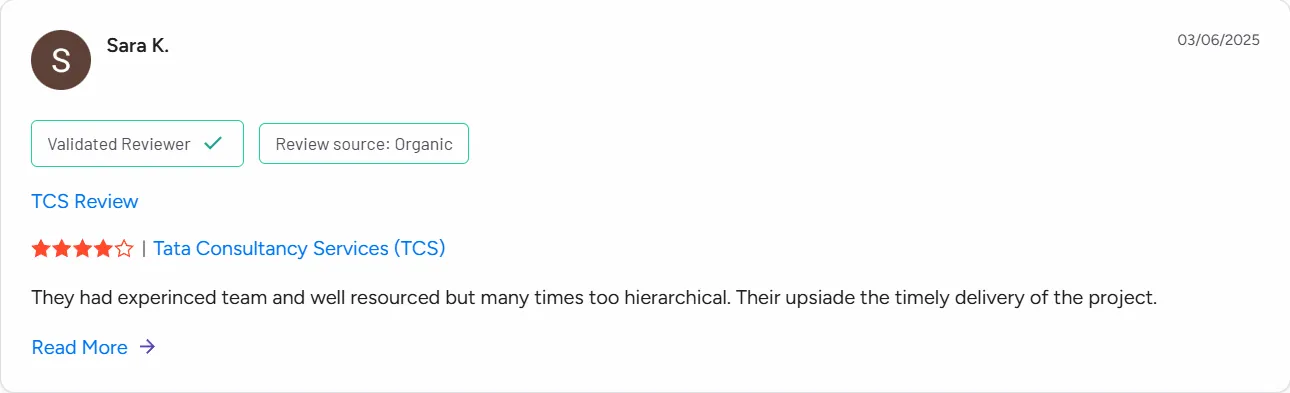
TCS maintains a 4.3 out of 5 user rating for its enterprise cybersecurity solutions. Many clients value its global service delivery model and ability to support multi-year cybersecurity improvement programs. TCS is recognized for identity services, cloud security controls, and governance implementations across industries.
10. Capgemini
Specialization: Cyber defense consulting, cloud and application security, digital identity, managed SOC
Capgemini delivers cybersecurity services focused on helping organizations modernize defenses while supporting business transformation. Its consulting services include cloud security design, application security assessments, identity governance, and managed threat monitoring. Capgemini works extensively with organizations shifting legacy systems to cloud environments.
The firm emphasizes a structured approach to improving cyber maturity, with security frameworks integrated into operations, development, and governance processes.
Ratings and reviews:
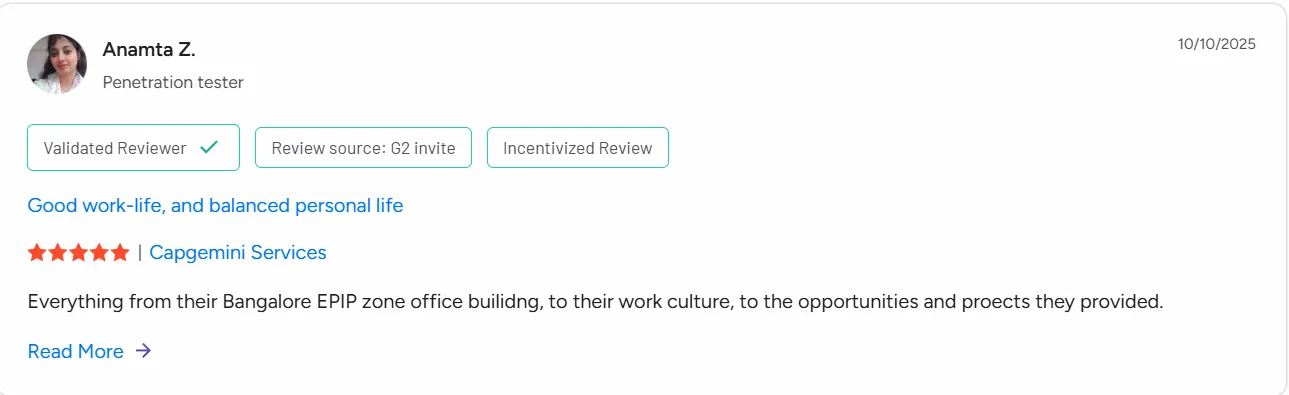
Capgemini is rated 4.0 out of 5 for its cybersecurity consulting and managed security offerings. Customers highlight its cloud security capabilities and digital identity frameworks. Capgemini is also noted for supporting enterprise-wide transformation and cross-region security operations.
11. Infosys
Specialization: Cloud and application security, cyber defense center operations, digital identity
Infosys provides cybersecurity consulting and managed security services to global enterprises, supporting modernization, zero trust adoption, and continuous security monitoring. The firm’s services include cloud workload security, vulnerability management, DevSecOps advisory, and identity management programs.
Infosys operates cyber defense and threat monitoring centers to help organizations maintain real-time security visibility. Its consulting approach blends automation with industry-specific security design.
Ratings and reviews:
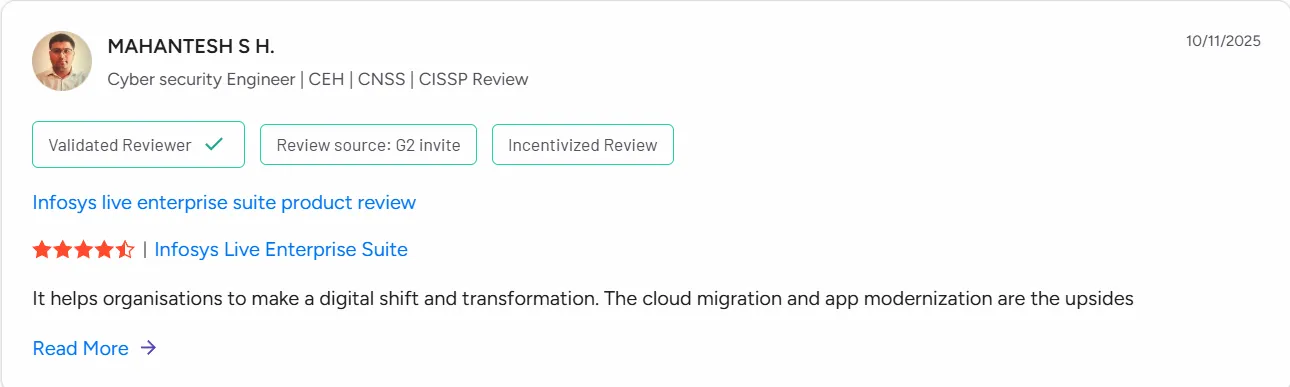
Infosys holds a solid 3.8 out of 5 user rating across cybersecurity consulting engagements. Clients frequently emphasize its delivery scale, particularly for cloud security and identity modernization. Infosys is also recognized for supporting highly regulated global businesses with compliance-aligned security transformation.
12. Optiv
Specialization: Security architecture, penetration testing, managed detection, cyber risk assessment
Optiv is a cybersecurity consulting firm that helps organizations design and improve security architecture, implement threat detection programs, and conduct penetration testing and risk assessments. The company works with mid-market and enterprise organizations seeking structured, hands-on cybersecurity improvement.
Optiv is known for combining vendor-neutral advisory with technical implementation services, helping organizations align tools and controls to actual security outcomes.
Ratings and reviews: Optiv is well-reviewed for its technical expertise and vendor-agnostic approach. Customers note strong support in designing scalable cybersecurity programs.
13. Kroll
Specialization: Incident response, digital forensics, threat intelligence, risk management
Kroll specializes in incident response and cyber investigations, helping organizations respond to and recover from breaches. The company provides digital forensics, ransomware response, breach assessment, threat attribution, and crisis advisory. Kroll is known for responding to high-profile cyber attacks across industries.
Kroll also provides proactive cyber risk assessment and threat intelligence services, helping clients prepare for emerging threats and improve resilience. Its global response teams are available around the clock.
Ratings and reviews:

Kroll is rated 3.8 out of 5, based on its excellence in incident response, forensics, and breach investigation. Clients appreciate Kroll’s speed of engagement during security incidents and its ability to coordinate legal, regulatory, and technical remediation efforts.
14. NetSPI
Specialization: Enterprise penetration testing, attack surface management, red team operations
NetSPI provides offensive security consulting services to large enterprises and government organizations. It specializes in manual penetration testing, adversary simulation, cloud security assessment, and attack surface management. NetSPI’s approach emphasizes deep, human-led testing of complex environments.
NetSPI also provides continuous penetration testing services for organizations that require ongoing security assurance beyond periodic engagements.
Ratings and reviews:
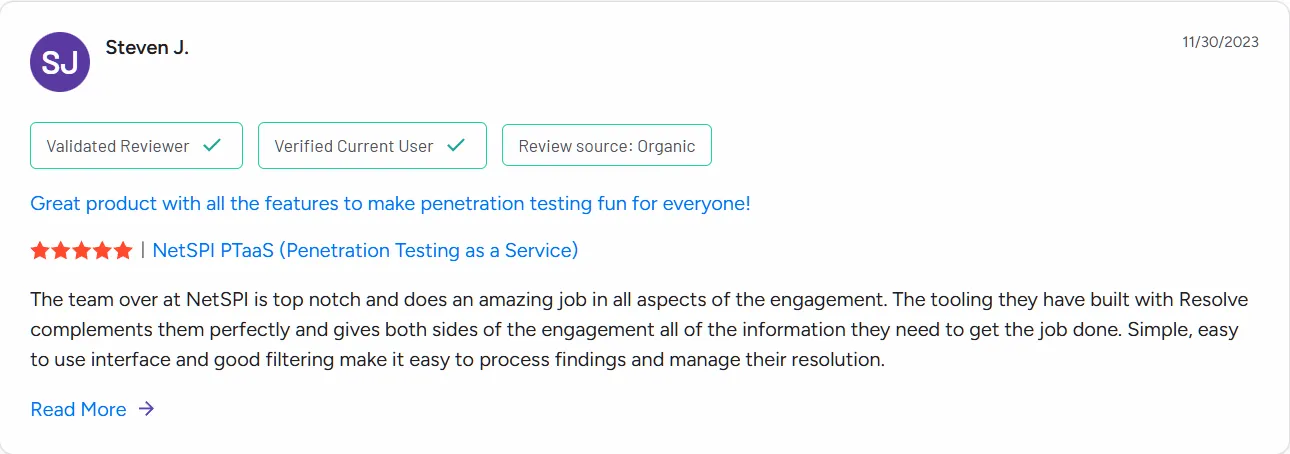
NetSPI holds a 4.9 out of 5 user rating, driven by its reputation for deep penetration testing expertise. Organizations value NetSPI’s ability to simulate real-world attacker behavior and provide actionable remediation guidance. Continuous testing and red-team services are frequently cited strengths.
15. Bishop Fox
Specialization: Offensive security, red team exercises, advanced penetration testing
Bishop Fox is a well-regarded offensive security firm known for conducting deep security testing of applications, networks, and cloud environments. The company specializes in red team exercises and adversary emulation, helping organizations understand how attackers might penetrate their environment. Bishop Fox is known for its research-driven methodologies and ability to uncover complex vulnerabilities.
The firm works with Fortune 500 companies, technology providers, and government organizations that require expert-level testing and exploit analysis. Bishop Fox’s work often informs future cyber defense strategies and detection improvements.
Ratings and reviews: Bishop Fox receives strong reviews for technical depth and expertise. Customers emphasize the firm’s ability to uncover sophisticated vulnerabilities and provide highly detailed remediation guidance.
16. Atos
Specialization: Managed security operations, cyber defense consulting, cloud security services
Atos is a major global cybersecurity service provider offering cloud security consulting, identity management, managed detection and response, and security operations outsourcing. The firm operates multiple security operations centers worldwide that support continuous threat monitoring for enterprise environments. Atos also works with organizations undergoing large-scale digital modernization initiatives.
Its consulting services help organizations build resilient architectures and implement unified security frameworks across cloud and hybrid systems. Atos also has a strong presence in critical infrastructure and public sector security programs.
Ratings and reviews:
Atos holds a 1.5 out of 5 client rating in cybersecurity consulting and managed SOC services. Organizations appreciate Atos’s global scale and cloud-native security transformation capabilities. Its focus on secure digital infrastructure modernization is often highlighted.
17. Aujas
Specialization: Cyber transformation consulting, identity and access management, DevSecOps security
Aujas is an India-based cybersecurity consulting firm that helps organizations strengthen security architecture, manage digital identity programs, and embed security into software development lifecycle workflows. Its services include risk assessment, DevSecOps consulting, IAM implementation, and security operations setup.
Aujas works with enterprises across banking, telecom, insurance, and technology sectors. It is recognized for its structured consulting methodology and strong identity governance expertise.
Ratings and reviews: Aujas receives positive feedback for its advisory-led consulting approach and IAM implementation experience. Customers value its domain knowledge and security program rollout support.
18. Secureworks
Specialization: Managed detection and response, endpoint security, threat intelligence, security consulting
Secureworks provides cybersecurity consulting and threat detection services to enterprises globally. The company operates managed security services that monitor, analyze, and respond to security events. It also provides incident response services and cyber risk consulting to help organizations assess and improve their defenses.
Secureworks leverages its proprietary threat analytics platform and research center to stay ahead of emerging threats. It works across industries including finance, retail, manufacturing, and healthcare.
Ratings and reviews:
Secureworks receives a 4.6 out of 5 user rating for its managed detection and response offerings. Customers note the strength of its threat intelligence and incident response readiness. Its ability to provide continuous monitoring across distributed environments is commonly mentioned.
19. Cognizant
Specialization: Cloud security, identity governance, managed security services, cyber advisory
Cognizant offers cybersecurity consulting services that support cloud adoption, application modernization, and identity governance improvement. Its cybersecurity practice provides advisory services, architecture design, SOC management, and incident response support. Cognizant works with enterprises undergoing digital transformation, helping secure both legacy and cloud-native environments.
The firm emphasizes zero trust adoption, identity lifecycle governance, and security automation for operational efficiency.
Ratings and reviews:
Cognizant is rated 4.2 out of 5 for enterprise security transformation and managed security services. Clients highlight its global delivery capability and alignment with large-scale cloud modernization projects. Cognizant’s experience across enterprise identity and application security is also noted.
20. Tech Mahindra
Specialization: Enterprise security consulting, cloud and network security, SOC services, compliance advisory
Tech Mahindra delivers cybersecurity consulting and managed security services for enterprises across telecom, healthcare, manufacturing, and financial sectors. Its services include cloud security design, network defense, risk management, compliance advisory, and managed SOC operations. The firm supports organizations undergoing IT modernization and infrastructure scaling.
Tech Mahindra focuses on aligning cybersecurity maturity improvements with organizational digital transformation goals.
Ratings and reviews:
Tech Mahindra holds a 4.8 out of 5 user rating for consulting, SOC services, and security engineering. Customers mention its strong telecom security expertise and cross-industry digital security support. Its role in securing large digital transformation programs is frequently acknowledged.
Conclusion
Cybersecurity consulting continues to play a central role in helping organizations strengthen their defenses and adapt to a rapidly evolving threat landscape. As businesses expand into cloud-native environments, rely more heavily on distributed applications, and face increasing regulatory expectations, the need for expert guidance and structured security strategy becomes even more essential. The firms in this list offer a wide range of capabilities, from strategic advisory and compliance guidance to technical penetration testing and managed security operations, making it possible for organizations to find the support that matches their maturity level and risk profile.
While traditional consulting firms continue to provide foundational governance and enterprise-scale security leadership, new-age platforms like Beagle Security demonstrate how continuous, automation-driven security testing can accelerate protection in modern development environments. Choosing the right cybersecurity consulting partner comes down to a clear understanding of business needs, operational priorities, and the pace at which security improvements must be delivered. For organizations looking to build resilience in 2025 and beyond, partnering with the right security experts is one of the most impactful investments they can make.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)