
Cybersecurity has become one of the most defining risk factors in modern mergers and acquisitions. With most businesses operating on cloud-native infrastructure, relying on SaaS ecosystems, and processing sensitive customer data, security posture has a direct impact on valuation, post-deal liabilities, and integration strategy. As a result, cybersecurity due diligence is now essential for private equity firms, corporate development teams, and financial decision-makers seeking to acquire or invest with confidence.
For investment analysts, CFOs, and M&A teams operating under tight timelines, the challenge is twofold: uncover meaningful security risks early enough to influence negotiations, and distinguish between remediable gaps and fundamental weaknesses that threaten deal viability. This guide provides a strategic yet practical framework for conducting M&A cybersecurity due diligence, focusing on application security maturity, operational readiness, and red flags that materially affect deal outcomes.
What is cybersecurity due diligence?
Cybersecurity due diligence is the process of evaluating an acquisition target’s security posture, vulnerabilities, and operational risk exposure during an M&A transaction. It determines whether the target’s current controls, processes, and technologies are strong enough to prevent breaches, support regulatory requirements, and sustain business operations post-acquisition. In essence, it ensures that undiscovered security weaknesses do not become inherited financial liabilities.
The value of M&A cybersecurity due diligence
Before entering an acquisition, investors need clarity on how secure, resilient, and compliant the target truly is. Effective M&A cybersecurity due diligence helps deal teams uncover hidden risks, validate technical maturity, and ensure the business can scale safely under new ownership. Cybersecurity evaluation is now a critical pillar of modern M&A strategy because it:
Protects deal value: Uncovers hidden vulnerabilities, past breaches, or unresolved technical debt that could translate into high remediation costs or post-deal instability.
Quantifies security maturity: Helps investors understand whether the target’s engineering and security practices can support long-term product reliability and customer trust.
Reduces regulatory exposure: Validates whether the organization actually meets compliance obligations (SOC 2, ISO 27001, GDPR, HIPAA) and identifies gaps that could lead to penalties.
Prevents reputational risk: Identifies potential breach vectors such as exposed APIs, weak authentication, or poor cloud hygiene before they impact the acquiring brand.
Strengthens negotiation leverage: Provides objective, evidence-backed risk scoring that supports price adjustments or conditional remediation terms.
Ensures safe integration: Confirms that the target’s technology can be integrated into the acquiring company without introducing systemic security risks or unpredictable costs.
Key areas examined in a cybersecurity due diligence assessment
A thorough cybersecurity due diligence assessment focuses on the systems, processes, and controls that determine the target’s overall security resilience. This helps deal teams quickly identify strong areas, weak links, and issues that may require further investigation. Key areas include:
Application & API security: Analysis of DAST/SAST results, exposed endpoints, authentication design, and the overall maturity of secure development processes.
Cloud & infrastructure configuration: Evaluation of IAM roles, logging coverage, network segmentation, and misconfigurations that may expose assets to public access.
Identity & access management: Review of MFA enforcement, access governance, privilege allocation, and potential presence of shared or orphaned accounts.
Data protection: Verification of encryption standards, data handling practices, retention policies, and the reliability of backup and recovery procedures.
Incident response maturity: Assessment of breach history, historical remediation practices, and the presence of repeatable, well-governed incident workflows.
Vendor & supply chain risk: Review of third-party APIs, SaaS dependencies, and outsourced services that could introduce vulnerabilities.
Compliance status: Validation of the target’s alignment with frameworks like SOC 2, ISO 27001, GDPR, and HIPAA, not just certifications, but actual operational controls.
Network & endpoint hygiene: Insights into patch cadence, device security hardening, and the presence of outdated or unsupported systems.
Structure of a cybersecurity due diligence process
A well-structured cybersecurity due diligence process gives deal teams the ability to quantify risk, understand true security maturity, and make confident go/no-go decisions under tight timelines. This includes:
Document review: Collecting and examining security policies, architecture diagrams, compliance documentation, and prior security assessments to establish baseline posture.
Stakeholder interviews: Speaking with engineering, DevOps, and security leaders to validate documented processes and uncover operational gaps.
Historical incident analysis: Reviewing breach disclosures, audit logs, past incidents, and remediation timelines to identify patterns or unresolved issues.
Access & identity review: Assessing authentication mechanisms, privilege management, and enforcement of least-privilege access across systems and environments.
Vulnerability testing & penetration testing: Conducting automated scans and real-world exploit testing to validate severity, exploitability, and business impact of risks.
Cloud & architecture evaluation: Analyzing cloud accounts, infrastructure design, data flows, and integrations to identify systemic weaknesses or misconfigurations.
Business impact mapping: Translating technical findings into financial terms by estimating remediation cost, operational disruption, and potential regulatory exposure.
Risk-ranked reporting: Producing a concise, executive-ready report that outlines critical risks, acceptable gaps, and issues that may warrant renegotiation or conditional commitments.
Cybersecurity due diligence checklist
Below is a structured, M&A-ready checklist designed to help deal teams evaluate the security maturity of acquisition targets quickly and objectively.
| Assessment area | What to verify | Red flags | Why it matters |
|---|---|---|---|
| Application security | Automated DAST/SAST results, API security, authentication mechanisms | Critical CVEs, exposed APIs, weak authentication | Impacts customer data safety and product reliability |
| Cloud security | IAM roles, policies, logging, misconfiguration scans | Open ports, unrestricted IAM permissions, missing logs | Cloud misconfigurations are the leading cause of modern breaches |
| Infrastructure & network | Segmentation, firewall rules, patch cadence | Legacy tech, flat networks, unsupported OS | Increases likelihood of lateral movement and ransomware risk |
| Data protection | Encryption, key management, backups | Unencrypted sensitive data, weak key storage | Directly tied to compliance and breach impact severity |
| Identity & access management | MFA, RBAC, service account governance | Shared accounts, missing MFA, privilege sprawl | Primary vector for account takeover and internal misuse |
| Incident response | IR plan, detection tooling, historical incident logs | Lack of procedures, poor visibility, unresolved incidents | Suggests hidden liabilities and unpreparedness |
| Vendor risk | Third-party assessments, API dependencies | High-risk vendors, no vendor reviews | Expands attack surface and compliance burden |
| Compliance & governance | SOC 2, ISO 27001, GDPR, HIPAA posture | Unverifiable certifications or major controls gaps | Affects customer trust and market eligibility |
| DevSecOps & SDLC | CI/CD security, code review, secrets management | Hardcoded secrets, no security controls in pipeline | Signifies operational immaturity and long-term remediation cost |
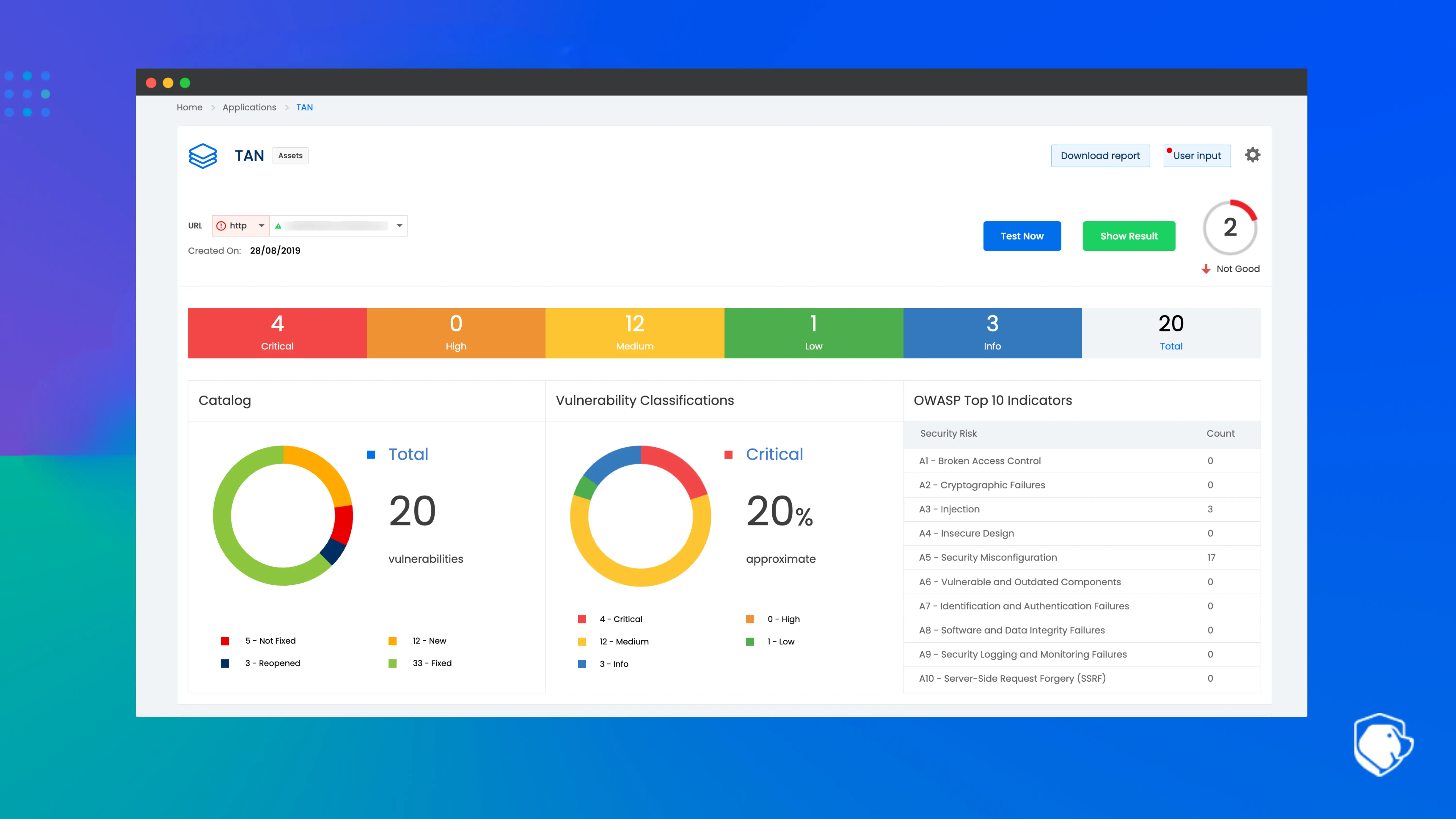
Using the Beagle Security platform for cybersecurity due diligence
Beagle Security provides a fast, objective, third-party view of an acquisition target’s application and API security posture, critical for cybersecurity due diligence processes. Through automated penetration testing and continuous DAST, Beagle Security helps M&A teams validate vulnerabilities, identify real-world risk exposure, and assess how mature the target’s security practices truly are. This independent analysis strengthens negotiation positions and helps quantify remediation effort without requiring internal system access.
Final thoughts
Cybersecurity due diligence is undeniably inseparable from financial, operational, and legal diligence. Security lapses directly influence valuation, integration complexity, and long-term business resilience. For private equity partners, investment analysts, CFOs, and corporate development teams, the ability to identify unacceptable risk can determine whether a deal becomes a strategic win or a costly liability.
A structured approach to M&A cybersecurity due diligence allows deal teams to distinguish between manageable gaps and fundamental weaknesses. Combined with independent assessment tools like Beagle Security, investors can verify claims, uncover hidden risks, and make data-driven decisions even under compressed transaction timelines. Ultimately, cybersecurity due diligence protects not just the deal, but the future value of the combined organization.
With Beagle Security, teams gain an objective, third-party view of an acquisition target’s true application and API security posture. This helps them validate risk early, strengthen negotiation positions, and accelerate confident decision-making. Check out our 14 day advanced trial or the interactive demo to see if we’re the right fit for you.
FAQ
What is a red flag during cybersecurity due diligence?
A red flag is any critical vulnerability, misconfiguration, or undisclosed incident, such as exposed APIs, unpatched CVEs, weak access controls, or hidden breach history, that introduces immediate financial or operational risk.
How long does cybersecurity due diligence take?
Typically 30–90 days, depending on organizational complexity and documentation availability.
How do you evaluate a company’s breach history?
Request incident logs for the past 3–5 years, RCAs, regulatory notifications, impact analysis, and evidence of security improvements.
Which compliance records should be requested pre-deal?
ISO 27001, SOC 2, PCI DSS, GDPR documentation, HIPAA records, DPAs, RoPA, pentest reports, vulnerability scans, and evidence of third-party risk management.
Why is regulatory documentation important during M&A?
It reveals hidden liabilities, potential fines, unresolved compliance gaps, and the real maturity of the security program.



![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)