The world of software development is constantly evolving, with speed and security now inextricably linked. Gone are the days when security was an afterthought, a final checkbox to be ticked before deployment.
A robust security posture needs to be built into every stage of the development lifecycle; the philosophy of DevSecOps.
With a landscape full of options, choosing the best platforms can be a daunting task. That’s why we’ve compiled a list of the top DevSecOps tools for 2025, providing a comprehensive guide to help you find the right fit for your team.
The best DevSecOps Tools of 2025
1. Beagle Security
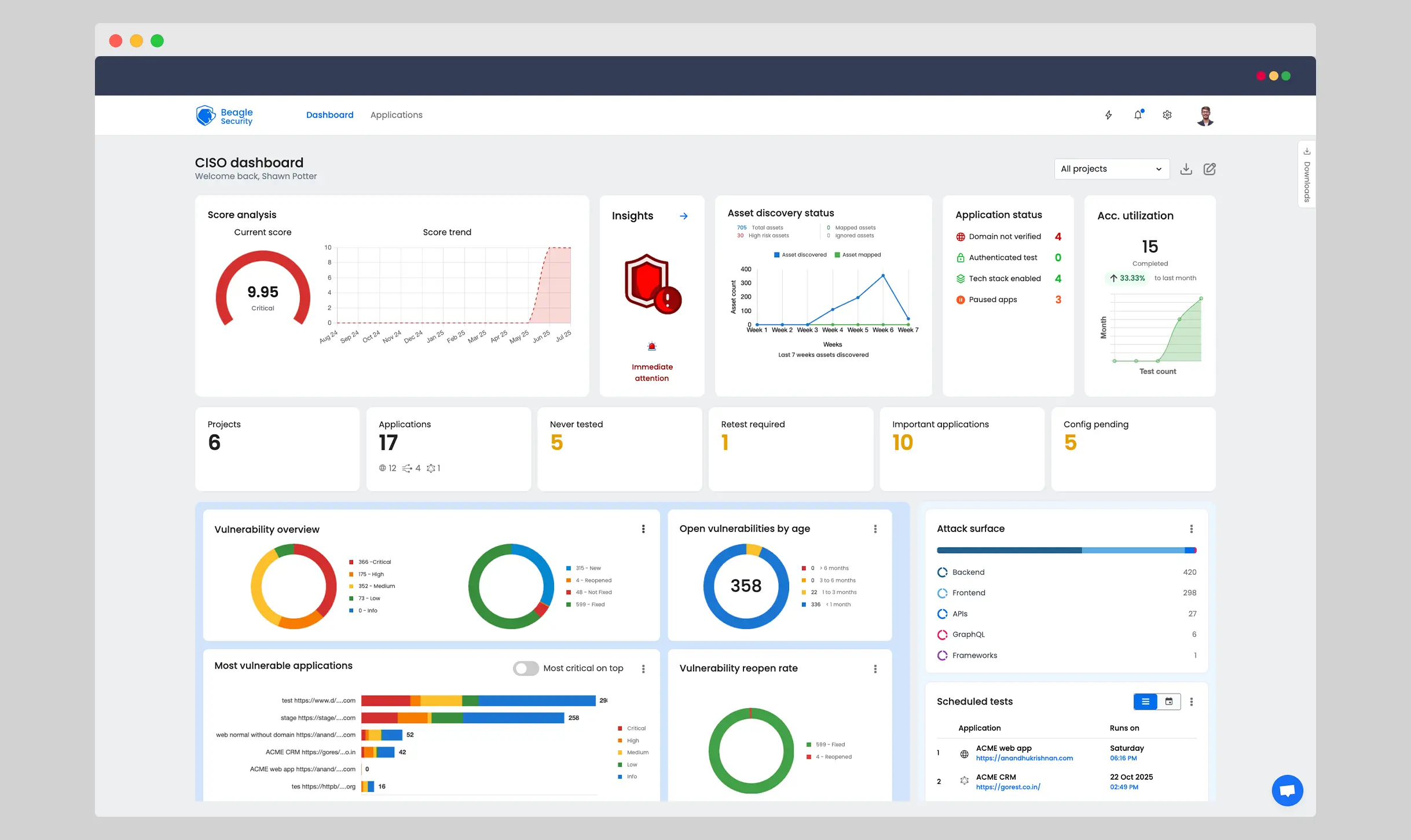
Beagle Security is a dynamic application security testing (DAST) platform designed to identify vulnerabilities in web applications, APIs, and GraphQL endpoints. Powered by AI-driven automated penetration testing, Beagle Security offers deep coverage with minimal false positives.
Its developer-friendly interface, CI/CD integrations, and detailed remediation guidance make it an excellent choice for DevSecOps teams aiming to embed security testing throughout the application lifecycle.
Key features:
AI-powered automated pen testing: Beagle Security’s core strength is its intelligent AI engine, which goes beyond standard scanning by learning from past penetration tests to uncover complex, business-logic vulnerabilities that are often missed by other tools.
Full-stack DAST: It provides comprehensive security testing for your entire application stack, including web applications, REST APIs, and GraphQL endpoints, ensuring no part of your digital footprint is left unexamined.
Developer-centric integrations: The platform integrates with popular tools like Jira, GitLab, and GitHub Actions, automatically pushing security findings to developers’ workflows as actionable tickets with clear remediation steps.
Actionable reports & compliance: Beagle Security provides contextual, developer-friendly reports that explain findings with step-by-step remediation guidance. It also generates reports mapped to major compliance standards, including OWASP Top 10, HIPAA, and PCI DSS.
User rating
Beagle Security has a rating of 4.7/5 from 87 reviews on G2. Users consistently praise Beagle Security for its ease of use, efficient setup, and the high quality of its actionable reports.
Pricing: Beagle Security offers a transparent, tiered pricing model:
Free trial: A 14-day free trial is available to test the platform’s capabilities.
Essential: A paid plan for growing teams, starting at $119 per month.
Advanced: A more comprehensive plan for organizations with advanced needs, starting at $359 per month.
Enterprise: A custom-priced plan for larger organizations with specific requirements for scale and support.
2. GitLab
Overview
GitLab is widely recognized as a comprehensive DevSecOps platform—an all-in-one environment for source code management, CI/CD pipelines, security, compliance, and governance, wrapped seamlessly in a single interface.
Key features
CI/CD integrations: Automate your build, test, and deployment pipelines end-to-end.
Issue tracking & project management: From backlog to milestone, GitLab covers planning and collaboration.
Scalable & flexible architecture: Fits small teams and enterprises alike.
Built-in security tooling: Includes SAST, DAST, dependency scanning, and secret detection natively integrated.
AI-native capabilities (GitLab Duo in 2025): Premium and Ultimate tiers now include AI tools like Code Suggestions and Chat in the IDE, enhancing developer productivity.
Pricing
Free tier: $0 per user/month; includes 400 compute minutes/month and is ideal for small teams or personal projects.
Premium and Ultimate plans above the free tier with custom pricing. Premium plan has 10,000 compute minute/month limit while Ultimate plan has a 50,000 compute minute/month limit.
Additional AI features can be added on to the Premium and Ultimate plans starting at $19.
User ratings
On G2, GitLab earns a solid 4.5/5, based on 846 reviews, and 4.6/5 on Capterra from 1198 reviews, reflecting overall strong satisfaction with its feature breadth and integrated experience.
3. Spacelift
As a robust infrastructure as code (IaC) management platform, Spacelift is purpose-built to help organizations automate and secure their cloud infrastructure. It acts as a powerful orchestration layer, centralizing control over multi-cloud environments and enabling a true DevSecOps approach to IaC. With native support for a wide range of tools, Spacelift allows teams to bring their existing workflows under a unified, policy-driven umbrella.
Key features
Multi-IaC orchestration: Create stacks that trigger on VCS changes and manage deployments across multiple IaC engines and cloud providers.
Policy as code: Employ Rego-based policies (via Open Policy Agent) to govern login, access, approvals, and resource creation.
Drift detection & contexts: Monitor infrastructure for configuration drift and reuse shared settings across stacks with contexts.
Credential-less cloud integrations: Securely manage dynamic, short-lived cloud credentials without hardcoding secrets.
Developer self-service & orchestration: Enable platform engineers to model complex micro-deployments with stack dependencies, reusable blueprints, and automated workflows SpaceliftSpacelift.
FinOps & cost estimation: Built-in cost estimation (through Infracost) helps teams forecast deployment costs before applying changes
Pricing
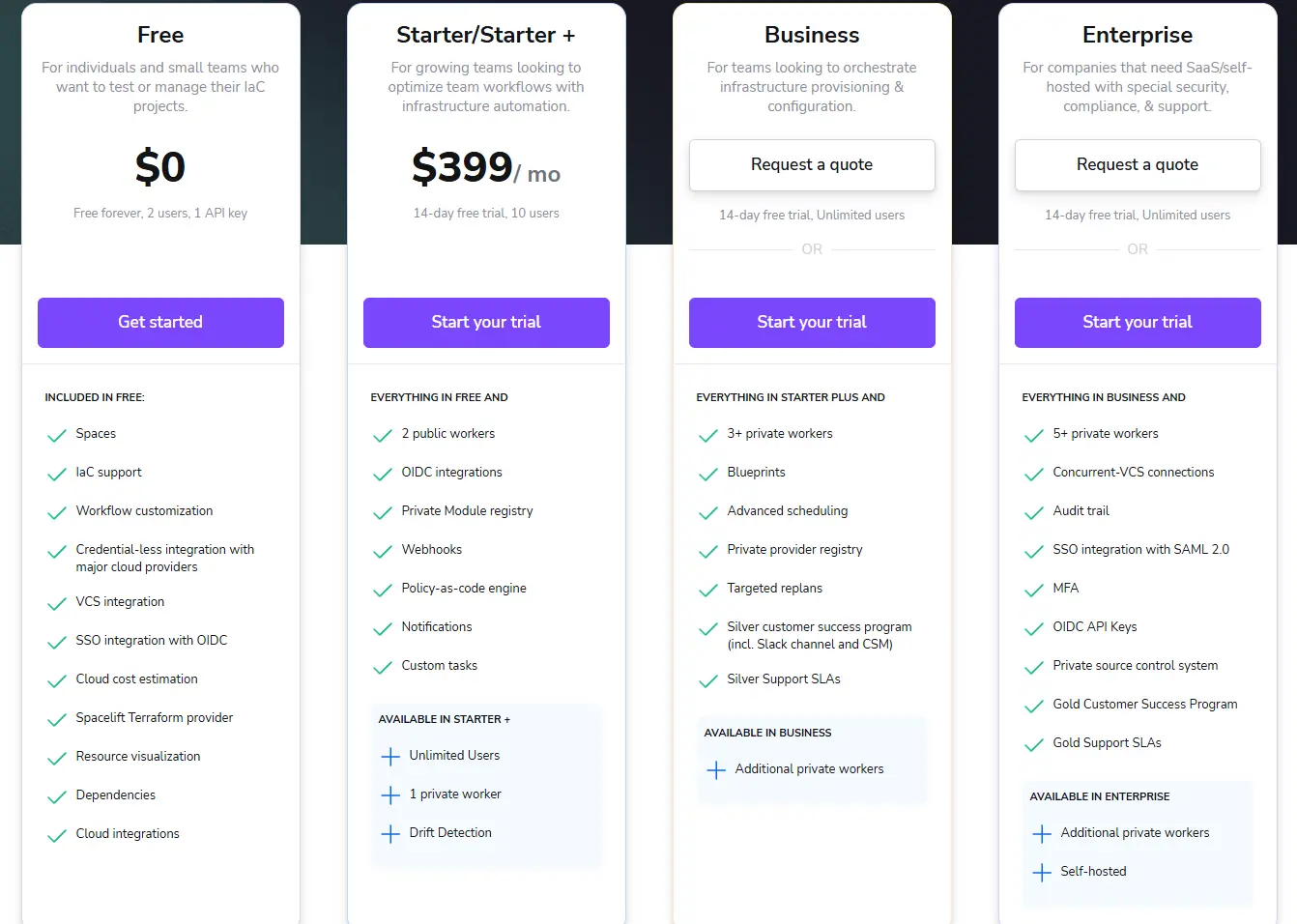
Spacelift offers a transparent pricing structure based on usage and features:
Free: A free-forever plan for individuals and small teams, including up to 2 users.
Starter/Starter+: A paid plan beginning at $399 per month for up to 10 users, with features like policy-as-code and private module registries.
Business & Enterprise: Custom-priced plans for larger organizations, offering additional private workers, advanced scheduling, and dedicated support.
4. Cloudflare
Cloudflare is a connectivity cloud company that provides a powerful platform of security and performance services at the network edge. For DevSecOps, Cloudflare is a critical “shift-right” tool that ensures applications are protected against external threats as soon as they are deployed. By acting as a reverse proxy, it provides a comprehensive suite of services that a dev team can integrate into their pipeline to secure their web assets and enhance performance from the first day of launch.
Key features:
Web Application Firewall (WAF): Cloudflare’s WAF protects applications from common web vulnerabilities and exploits, including SQL injection and cross-site scripting (XSS), by filtering malicious traffic before it reaches the origin server.
DDoS Protection: It offers robust, unmetered DDoS protection that automatically detects and mitigates attacks of any size or complexity, ensuring the application remains available and responsive.
Cloudflare Workers: This serverless platform allows developers to build and deploy code at the edge, reducing latency and providing a flexible environment for running security and performance logic.
Zero Trust Security: With products like Cloudflare Access, it helps implement a Zero Trust security model, securing access to internal applications and resources without relying on a traditional VPN.
API Gateway & Security: The platform provides tools to discover, manage, and protect APIs, safeguarding them from abuse and ensuring secure communication.
Pricing
Cloudflare’s pricing is designed to scale with your needs, from individuals to large enterprises:
Free: A generous plan that includes basic CDN, DDoS protection, and SSL for individuals and small projects.
Pro: Starting at $20 per month (billed annually), this plan adds advanced features like an enhanced WAF and bot management.
Business: Starting at $200 per month (billed annually), it offers more robust features, including an uptime SLA, advanced security analytics, and custom WAF rules.
Enterprise: A custom-priced plan with the highest level of security, performance, and dedicated support.
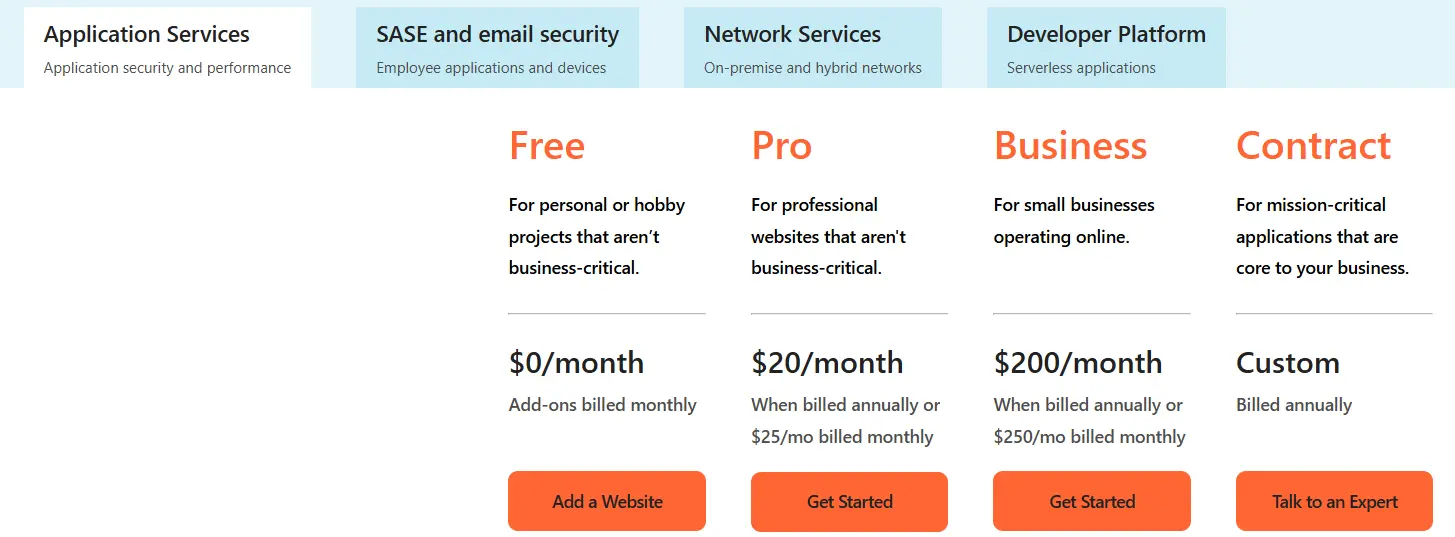
*The given pricing is for Cloudflare’s Application services. They provide more solutions with most having custom pricing.
User reviews
Cloudflare earns a 4.5/5 rating on G2 based on 555 user reviews and 4.7/5 rating on Capterra from 501 reviews.
5. Trivy
As an open-source, all-in-one security scanner, Trivy has become a favorite within the DevSecOps community for its simplicity and comprehensive capabilities. Designed to be fast and easy to integrate into continuous integration (CI) pipelines, it helps developers find vulnerabilities and misconfigurations in a wide range of targets early in the development process, embodying the “shift-left” security principle. Its versatility in scanning everything from container images to file systems makes it an essential part of a modern security workflow.
Key features:
Comprehensive scanning: Trivy can scan for vulnerabilities in various targets, including container images, file systems, Git repositories, and even single directories, making it a highly versatile tool.
Vulnerability detection: It identifies vulnerabilities in both operating system packages and application dependencies, using multiple security advisories to provide accurate and timely results.
IaC misconfiguration scanning: The tool automatically detects common misconfigurations in popular infrastructure as code files like Terraform, Kubernetes, and Docker, helping to prevent security flaws before they are deployed.
Secret detection: Trivy includes a robust feature to find secrets, such as API keys and passwords, that may have been accidentally committed to source code.
CI/CD integration: Its straightforward command-line interface and lightweight footprint make it a perfect fit for automated security checks within any CI/CD pipeline.
Pricing
Trivy is an open-source tool, so it is free to use. This makes it an incredibly cost-effective solution for teams of any size looking to integrate robust security practices without licensing fees.
User reviews:
Trivy has a rating of 4.3/5 on PeerSopt. As an open-source tool, Trivy does not have a traditional rating, but it is one of the most popular and highly-regarded scanners in the industry, with a large and active community on GitHub.
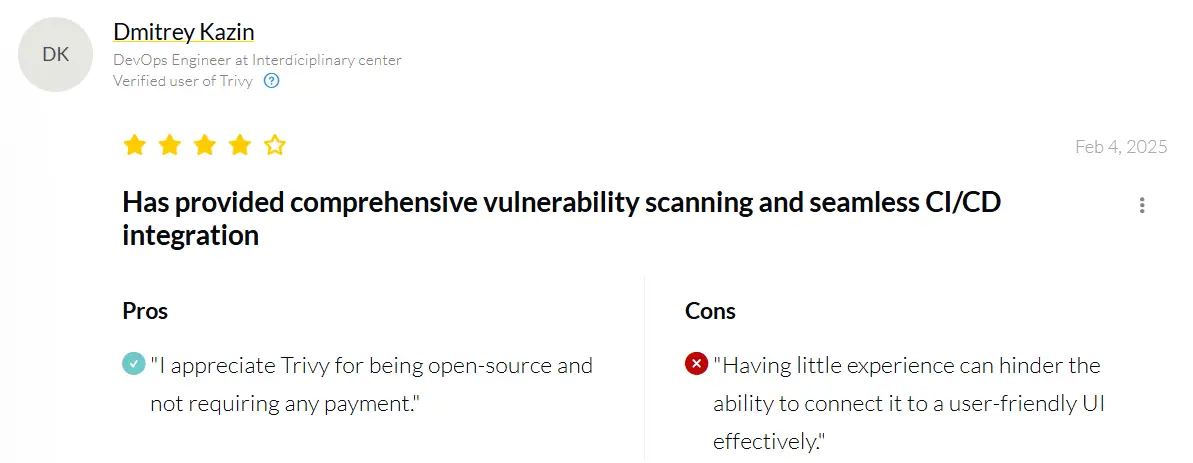
Source: PeerSpot
6. Semgrep
Semgrep is a powerful and flexible static analysis tool designed to help developers find security vulnerabilities, code quality issues, and misconfigurations early in the development lifecycle.
Supporting over 30 programming languages, Semgrep provides fast, lightweight scanning that integrates seamlessly with DevSecOps pipelines and developer workflows. Its customization capabilities allow organizations to enforce tailored security policies and coding standards, making it a popular choice for shift-left security in 2025.
Key features
Static Application Security Testing (SAST): Detects vulnerabilities and code smells across a broad range of languages and frameworks.
Customizable rules: Allows creation of custom security and quality rules using an easy-to-read syntax, making it adaptable to organization-specific policies.
CI/CD integration: Works smoothly with popular CI/CD pipelines like GitHub Actions, GitLab CI/CD, and Jenkins to automate security scans and enforce policies before deployment.
Secrets detection: Identifies hard-coded credentials, API keys, and tokens in code repositories to prevent accidental exposure.
Shift-left security: Provides instant feedback directly in IDEs and pull requests, enabling developers to fix issues early in the development process.
Developer-friendly: Lightweight, fast, and easily integrated with existing development environments, making adoption straightforward for engineering teams.
Pricing
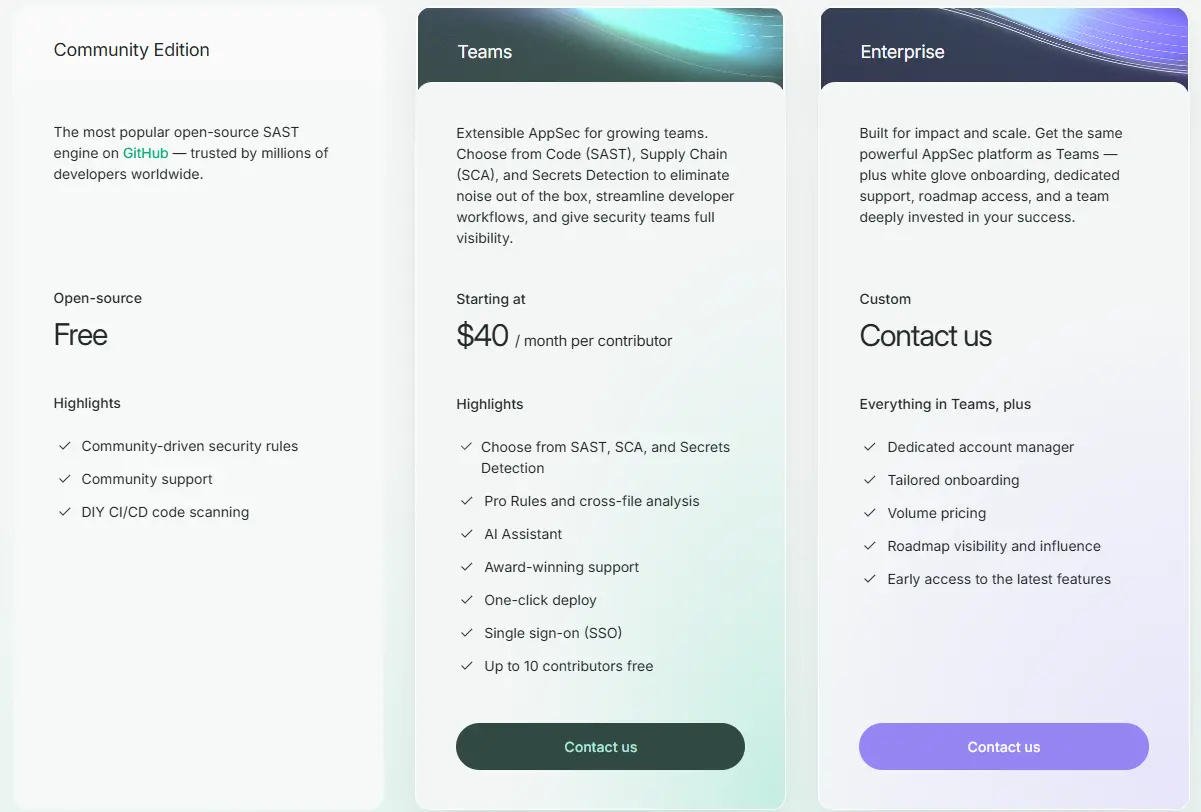
Semgrep operates on a freemium model that is highly accessible to all teams:
Open-source: The core Semgrep engine is completely free and open source through the Community plan, allowing anyone to use it for basic security scanning and custom rule creation.
Commercial tiers: For growing and enterprise teams, Semgrep offers paid tiers. These are Teams plan, with pricing starting at $40, and the Enterprise plan with custom pricing.
User review
Semgrep has a rating of 4.5/5 from 31 reviews on G2.
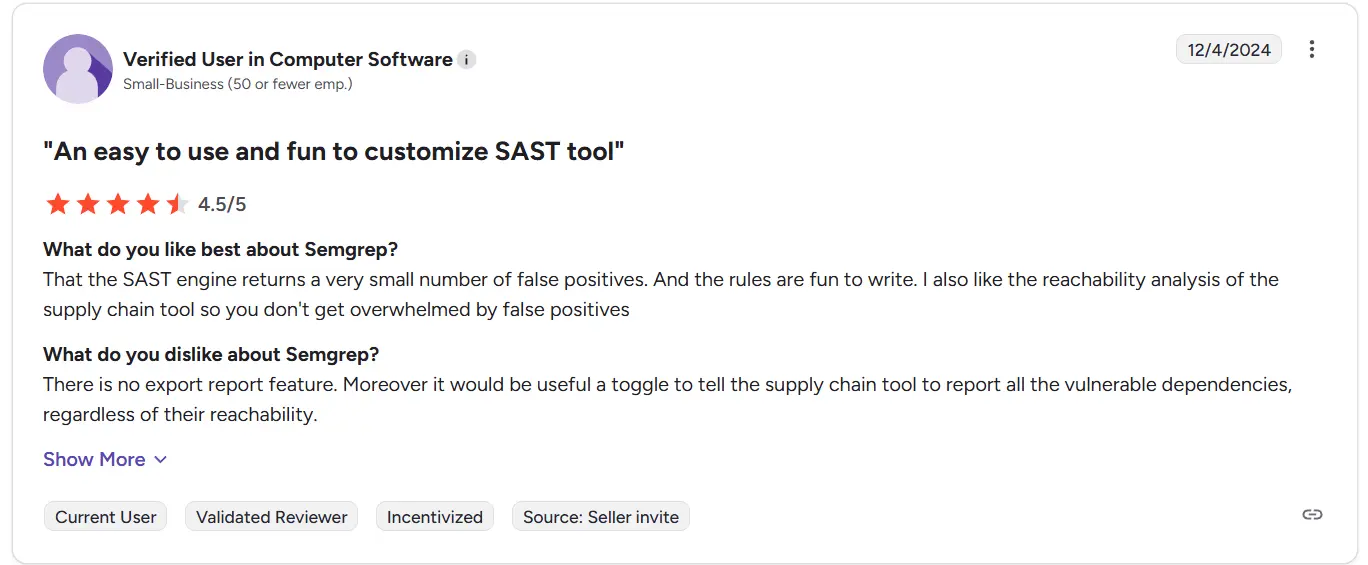
Source: G2
7. Grype
Grype is a free, open-source vulnerability scanner that has become a go-to tool for security-conscious development teams. Designed and maintained by Anchore, this lightweight tool specializes in finding vulnerabilities in container images and filesystems.
Its primary strength lies in its speed and its ability to be integrated directly into any continuous integration (CI) pipeline, giving developers immediate feedback on the security posture of their applications.
Grype is an essential “shift-left” tool that empowers teams to identify and address security issues before they ever reach production.
Key features:
Targeted scanning: Unlike some broader tools, Grype is highly specialized for scanning container images, local filesystems, and software bill of materials (SBOMs), providing precise and actionable results.
Extensive vulnerability database: It pulls vulnerability data from a wide variety of public and private sources, including the national vulnerability database (NVD), to ensure its scans are comprehensive and up to date.
Actionable reports: Grype produces detailed vulnerability reports that include severity levels and remediation steps, allowing developers to quickly understand and fix identified issues.
SBOM compatibility: Integrates with tools like Syft for Software Bill of Materials generation, enhancing transparency and supply chain security.
User reviews
As an open-source tool, Grype does not have a traditional rating, but its popularity and active development on GitHub make it one of the most trusted and widely adopted scanners in the DevOps community.
Pricing
Grype is a completely open-source and free tool. This makes it an ideal solution for teams looking to implement robust vulnerability scanning without incurring any costs.
8. Syft
Like Grype, Syft is an open-source CLI tool (and Go library) developed by Anchore. This tool is for generating Software Bills of Materials (SBOMs) from container images, filesystems, archives, and more.
By generating a complete inventory of every package and dependency within a container image or filesystem, Syft provides the critical visibility needed to manage vulnerabilities, ensure license compliance, and adhere to a growing number of security regulations. It works best when integrated directly into CI/CD pipelines, automatically creating an SBOM with every build.
Key features:
Software Bill of Materials (SBOM) Generation: Syft’s primary function is to generate a comprehensive and accurate SBOM that catalogs all the software components, including open-source libraries, frameworks, and their versions.
Broad source support: It can generate an SBOM from a wide variety of sources, including container images, local filesystems, archives, and git repositories, making it incredibly flexible for diverse development workflows.
Standards-based output: Syft outputs SBOMs in industry-standard formats like SPDX and CycloneDX, which enables easy consumption by other security tools and platforms for further analysis.
Open source & community driven: Regularly updated with new package ecosystem support and improvements based on community feedback.
Pricing
Syft is free and fully open-source. No pricing tiers or hidden paywalls; ideal for individuals and teams of any size.
Anchore provides enterprise-grade support and tooling that build on Syft and Grype under the Anchore Enterprise umbrella.
9. Terrascan
Terrascan is an open-source static code analyzer focused on Infrastructure as Code (IaC) security. It helps DevSecOps teams detect and fix security vulnerabilities and compliance violations in Terraform, CloudFormation, Kubernetes YAML, and other IaC templates before deployment.
Terrascan uses a policy-as-code engine that enforces security best practices and compliance requirements, making it an essential tool to prevent misconfigurations in cloud infrastructure in 2025.
Key features
IaC Security Scanning: Analyzes Terraform, CloudFormation, Kubernetes YAML, Helm charts, and more to identify misconfigurations and vulnerabilities early.
Policy-as-Code: Enables organizations to write, enforce, and automate custom policies using built-in compliance frameworks (CIS, GDPR, HIPAA, NIST) and custom rules.
Pre-deployment Security Checks: Integrates easily into CI/CD pipelines to run policies automatically before infrastructure is provisioned.
Detailed Reports: Provides clear, actionable results to guide remediation efforts and reduce misconfiguration risks.
Multi-Cloud Support: Works with resources on AWS, Azure, GCP, and Kubernetes clusters.
Open Source & Community-Driven: Frequently updated and improved by a strong open-source community.
Integration Ready: Compatible with GitHub Actions, GitLab CI, Jenkins, and other DevOps tools to embed security into existing workflows.
Pricing
Terrascan is fully open-source and available for free, making it accessible for organizations of all sizes.
User review
Terrascan, as an open-source tool, doesn’t have a formal G2 rating. However, it’s a widely respected and trusted tool within the DevOps community, with the added benefit of being developed and supported by Tenable, a prominent member in cybersecurity.
10. Open Policy Agent (OPA)
The Open Policy Agent, or OPA, is a powerful, open-source policy engine that has become a cornerstone of modern DevSecOps. As a graduated project of the cloud native computing foundation (CNCF), OPA allows you to define a single, unified set of policies as code and enforce them across your entire technology stack.
It’s a versatile tool that decouples policy decisions from application logic, enabling consistent security, governance, and compliance rules to be applied to microservices, Kubernetes, CI/CD pipelines, and more.
Key features:
Policy-as-code with Rego: OPA’s policies are written in Rego, a high-level declarative language designed for expressing rules over structured data. This makes it easy for teams to define and manage complex security policies that are readable and auditable.
Architectural flexibility: OPA is highly flexible and can be deployed in various ways, including as a sidecar container or a host-level daemon. This allows it to fit seamlessly into any architecture without requiring major refactoring of existing applications.
Centralized policy management: By centralizing policy logic in OPA, organizations can ensure consistency across a distributed environment. This simplifies the management, updating, and auditing of security and compliance rules.
Versatile use cases: The tool is incredibly general-purpose, with use cases that range from authorizing API requests and controlling Kubernetes admission to validating terraform plans and checking for container image signatures.
User reviews
OPA is a well-established and highly regarded tool in the community, with a large and active user base.
Pricing
OPA is an open-source tool and is free to use.
11. Ansible
Ansible is a powerful, open-source IT automation tool that has become an indispensable component of many modern DevSecOps strategies. While often thought of for its role in configuration management and application deployment, its true value in a security context lies in its ability to automate security tasks, enforce compliance, and ensure a consistent security posture across an entire infrastructure.
Key features:
Agentless & simple: Ansible’s agentless architecture makes it easy to get started without the overhead of installing agents on every machine. Its simple, human-readable playbooks make security automation accessible to a wide range of team members.
Security automation & compliance: It can automate a wide variety of security tasks, such as deploying security agents, managing firewall rules, enforcing access controls, and applying security patches across all servers, ensuring continuous compliance with internal and external policies.
Secret management: Ansible provides robust features for managing secrets, such as API keys and passwords, using integrations with tools like HashiCorp Vault, which helps prevent sensitive information from being exposed in plain text.
Idempotent workflows: Its idempotent nature means that playbooks can be run repeatedly without changing the state of the system if it is already compliant. This is critical for maintaining a secure and stable infrastructure.
User review
Ansible has a user rating of 4.6/5 from 371 reviews on G2.
Pricing
Ansible offers a highly flexible pricing model:
Open-source: The core Ansible tool is open-source and free to use, making it a powerful and accessible option for individuals and teams of all sizes.
Red Hat Ansible Automation Platform: For enterprises that require a more robust solution, Red Hat provides a commercial version that includes enterprise-grade features, certified content, and technical support. Price is only available as a custom quote.
12. Spectral
Part of Check Point’s CloudGuard system, Spectral is a cloud-native application security platform focusing on automated detection and prioritization of security risks. It serves all DevSecOps stakeholders by providing context-aware insights and automated remediation capabilities across code, configurations, and cloud environments, simplifying security workflows.
Key features
AI-Powered secret detection: Finds exposed keys, credentials, and sensitive data in codebases and logs.
CI/CD integration: Embeds security checks within pipelines for early vulnerability detection.
Software Composition Analysis (SCA): Monitors open-source components for vulnerabilities and license risks.
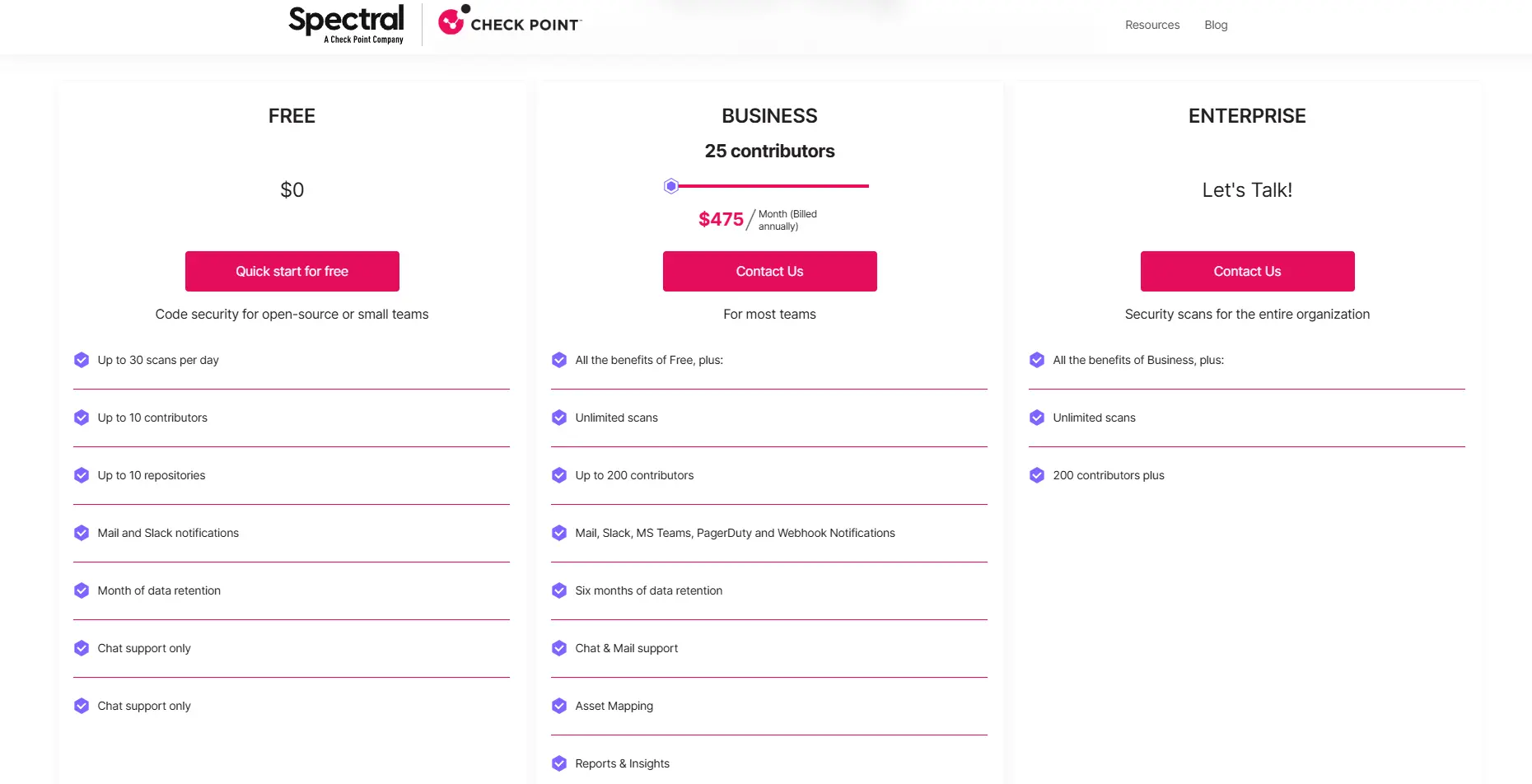
Pricing
Pricing for Spectral is available in 3 tiers:
Free plan
Business plan priced at $475/month for 25 contributors
Enterprise plan with custom pricing
13. Checkov
Checkov is an open-source, policy-as-code engine for securing Infrastructure as Code resources, developed by Bridgecrew. It scans Terraform, CloudFormation, Kubernetes, and Helm templates to detect security misconfigurations before deployment. Its cloud-resource-aware scanning leads to accurate detection and actionable remediation guidance for DevSecOps teams.
Key features
Comprehensive IaC security: Scans multiple IaC frameworks for vulnerabilities and misconfigurations.
Policy-as-code Enforcement: Supports predefined and custom policies for compliance frameworks like CIS, NIST, SOC 2.
Secrets detection: Finds hardcoded credentials in configurations.
CI/CD friendly: Easy integration with GitHub Actions, GitLab CI/CD, Jenkins, and Azure DevOps.
Compliance reporting: Detailed dashboards and reports to prioritize risk and track fixes.
Pricing
Checkov is fully open-source and free for all.
14. Calico
Calico is a cloud-native networking solution emphasizing security, widely used alongside Kubernetes and other container orchestration platforms. It enforces zero-trust network policies, microsegmentation, and encryption between services, enabling fine-grained access control and threat detection in distributed environments.
Key features
Zero-trust networking: Finely tune pod-to-pod communication through Kubernetes Network Policy and Calico’s extended rules.
WireGuard support for encrypted intra-cluster traffic.
Real-time anomaly detection and flow logging, aiding compliance and forensics
Pricing
Open-source: The core Calico open-source project is free to use and provides robust networking and network security capabilities.
Commercial tiers: Tigera, the company behind Calico, offers commercial products like Calico Cloud and Calico Enterprise. These paid versions provide additional features like centralized management, real-time threat detection, and dedicated support for enterprise environments.
15. Cosign
Cosign is an open-source, command-line tool that has become a cornerstone of modern software supply chain security. As a core component of the broader Sigstore project, Cosign is designed to simplify the process of cryptographically signing and verifying container images and other software artifacts.
Its primary function in a DevSecOps workflow is to ensure the integrity and authenticity of software from the build process all the way to deployment, providing critical assurance that a container has not been tampered with.
Key features
Container image signing: Provides cryptographic signatures for container images to prove authenticity.
Keyless signing: Uses OpenID Connect (OIDC) to streamline signing without manual key management.
Supply chain security: Verifies image provenance and prevents tampering during deployment.
CI/CD pipeline integration: Works with GitHub Actions, GitLab, and Kubernetes admission controllers.
Artifact and SBOM signing: Extends signing to Software Bill of Materials and software binaries for comprehensive supply chain trust.
Pricing
Cosign is a completely open-source and free tool. Its development is supported by major companies, and it is a public-good utility for improving software supply chain security.
Key takeaways
The right toolset empowers development teams to automate security, enforce compliance, and ship applications with confidence. From CI/CD platforms like GitLab and Spacelift, to security-focused solutions like Trivy, Checkov, and OPA, each tool addresses a different piece of the DevSecOps puzzle.
However, while most tools focus on identifying issues within the code or infrastructure, the real test lies in how an application performs under real-world attack scenarios. That’s where solutions like Beagle Security add a critical layer, by continuously simulating penetration tests and uncovering business logic flaws that other scanners often miss.
In 2025 and beyond, the strongest DevSecOps strategies will be built on a combination of automation, proactive testing, and continuous monitoring.

![Top 10 SDLC tools [2025] Top 10 SDLC tools [2025]](/blog/images/blog-banner-three-cover.webp)


![Best rated DAST tools [2025] Best rated DAST tools [2025]](/blog/images/top-rated-dast-tools-cover.webp)