With the rise of cloud-native architectures and continuous integration/continuous deployment (CI/CD) practices, ensuring the security of applications throughout the software development lifecycle has become more challenging yet crucial than ever before.
Traditional security testing methods are no longer sufficient to keep pace with the speed of modern software delivery.
Dynamic Application Security Testing (DAST) is a vital component of any robust security strategy. It involves probing an application in its running state to identify potential vulnerabilities and security weaknesses.
By simulating real-world attacks, DAST provides valuable insights into the security posture of applications, helping organizations identify and remediate vulnerabilities before they can be exploited by malicious actors.
Integrating DAST into your CI/CD pipeline is essential to ensure that security is not an afterthought but an integral part of the software development process.
Whether you’re a DevOps engineer looking to enhance the security posture of your CI/CD pipelines or a security professional seeking to embed security into the software development lifecycle, this guide will provide you with practical insights and actionable steps to effectively integrate DAST into your AWS CodePipeline.
Benefits of DAST for your application security
Conducting random static tests on code is an initial measure to uncover various vulnerabilities that may jeopardize its security. However, once a web application is deployed, it becomes susceptible to a new range of potential attacks, including code injection vulnerabilities and flaws in authentication mechanisms.
Dynamic Application Security Testing (DAST) addresses this by employing penetration testing techniques on running applications. This process occurs post-deployment, while the applications are in production.
Operating as a black-box security testing technique, DAST scrutinizes the application without exposing its source code or architectural details.
This approach illuminates runtime issues that might elude detection during static analysis, such as authentication lapses, server configuration weaknesses, and vulnerabilities that manifest only when authenticated users interact with the system.
DAST tools function by executing on the operational code to scrutinize various elements including interfaces, requests, responses, scripting, data injection, sessions, and authentication processes.
Leveraging fault injection methods, they insert diverse malicious data into the software to pinpoint common security vulnerabilities like SQL injection and cross-site scripting.
In essence, DAST serves as a vital tool for identifying runtime problems that static analysis alone may overlook, offering insights into authentication mechanisms, server configurations, and vulnerabilities that surface during user interactions.
What is secure deployment?
Secure deployment is the process of ensuring that a software system or application is released into a production environment in a manner that prioritizes security.
This involves a combination of practices, tools, and methodologies designed to protect the system from potential threats and vulnerabilities.
Key aspects include rigorous testing and code reviews to identify and remediate security issues before deployment, implementing robust access controls to prevent unauthorized access, and utilizing encryption to protect sensitive data.
Additionally, secure deployment encompasses the configuration of the environment to adhere to security best practices, continuous monitoring for suspicious activities, and the regular updating and patching of the system to address new vulnerabilities.
This comprehensive approach ensures that the deployed software operates securely and reliably, minimizing the risk of security breaches and maintaining the integrity and confidentiality of data.
What is AWS CodePipeline?
AWS CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service provided by Amazon Web Services (AWS). It automates the build, test, and deployment phases of your release process for software applications and infrastructures updates.
AWS CodePipeline allows you to define and visualize your release process workflow, which typically includes stages such as source code retrieval, build, test, and deployment to various environments like staging and production.
It integrates with other AWS services such as AWS CodeCommit, AWS CodeBuild, AWS CodeDeploy, and third-party tools, enabling seamless automation of your software release process.
With CodePipeline, developers can streamline their development workflows, improve release velocity, and ensure consistency and reliability in software deployments.
Integrating DAST into your AWS Code pipeline?
With the combination of AWS CodePipeline and Beagle Security, you can integrate security testing into your continuous delivery pipeline. Here, we’ll walk through the steps to set up a CodePipeline stage that automatically triggers security tests using Beagle.
1. Setting up your page
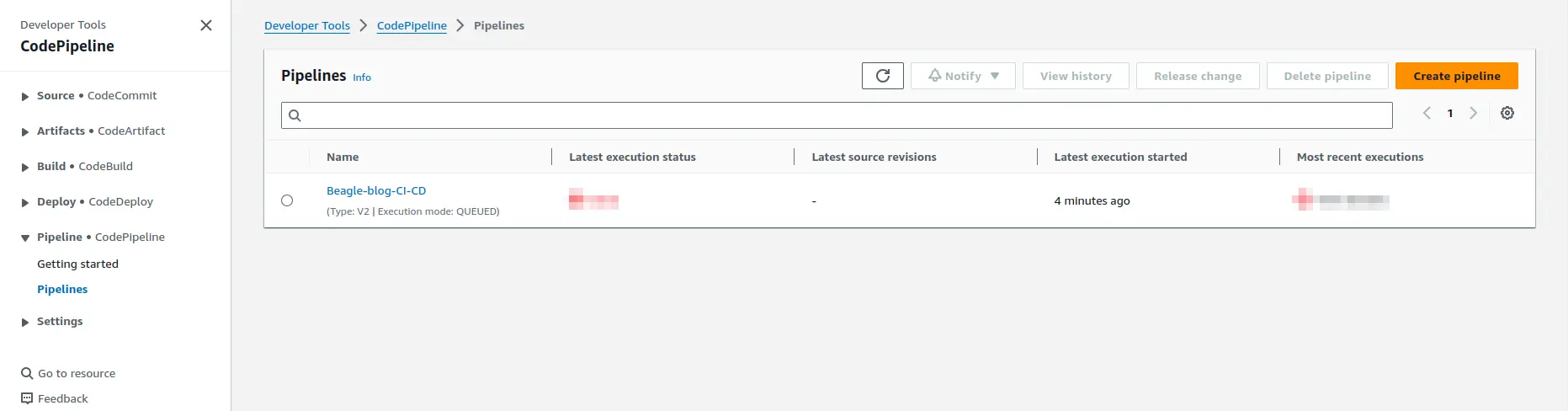
Access CodePipeline: Log in to your AWS account and navigate to CodePipeline. Select your pipeline and click on “Edit”.
Add stage: Click on “Add stage” and set the name as “beagle-test-trigger”.
Add action group: Within the newly created stage, click on “Add action group” and set the Action name to “test-trigger”. Choose “AWS CodeBuild” as the Action Provider.
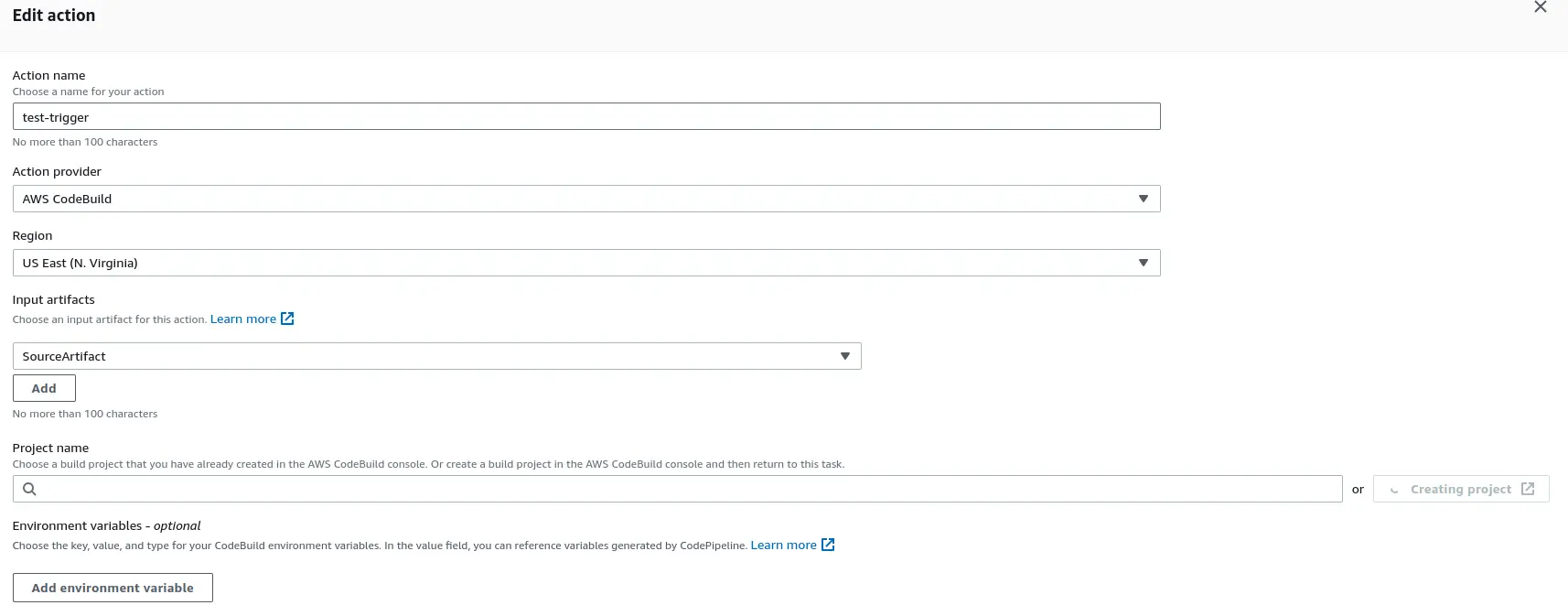
- Input Artifacts: Under “Project Name”, click on “Create Project”.
2. Configure build environment
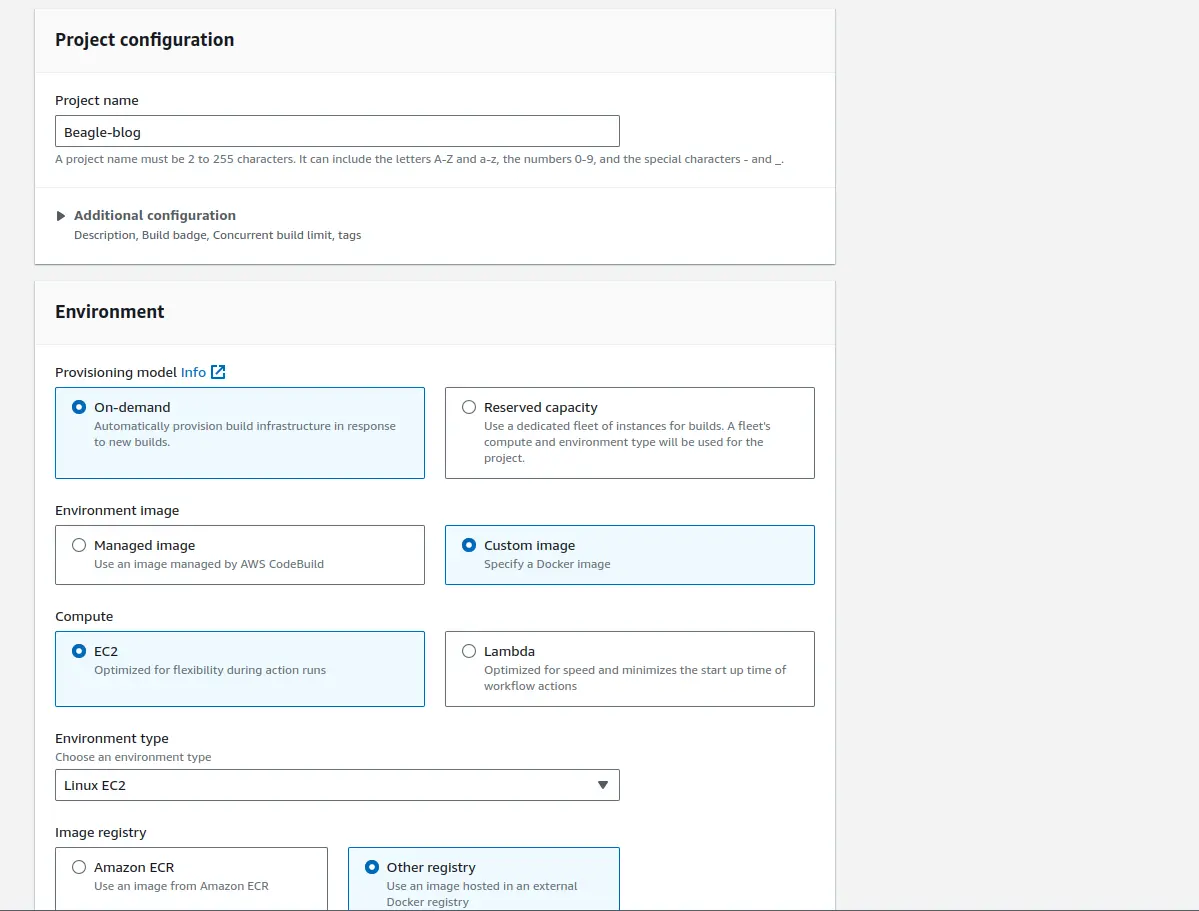
Environment image: Select “Custom Image”.
Environment type: Choose “Linux”.
Image registry: Set it to “Other Registry”.
External registry URL: Enter “beaglesecurity/beagle-test-trigger-common”.
3. Generating access token in Beagle Security
You can locate your Personal Access Token by accessing the Profile drop-down menu.
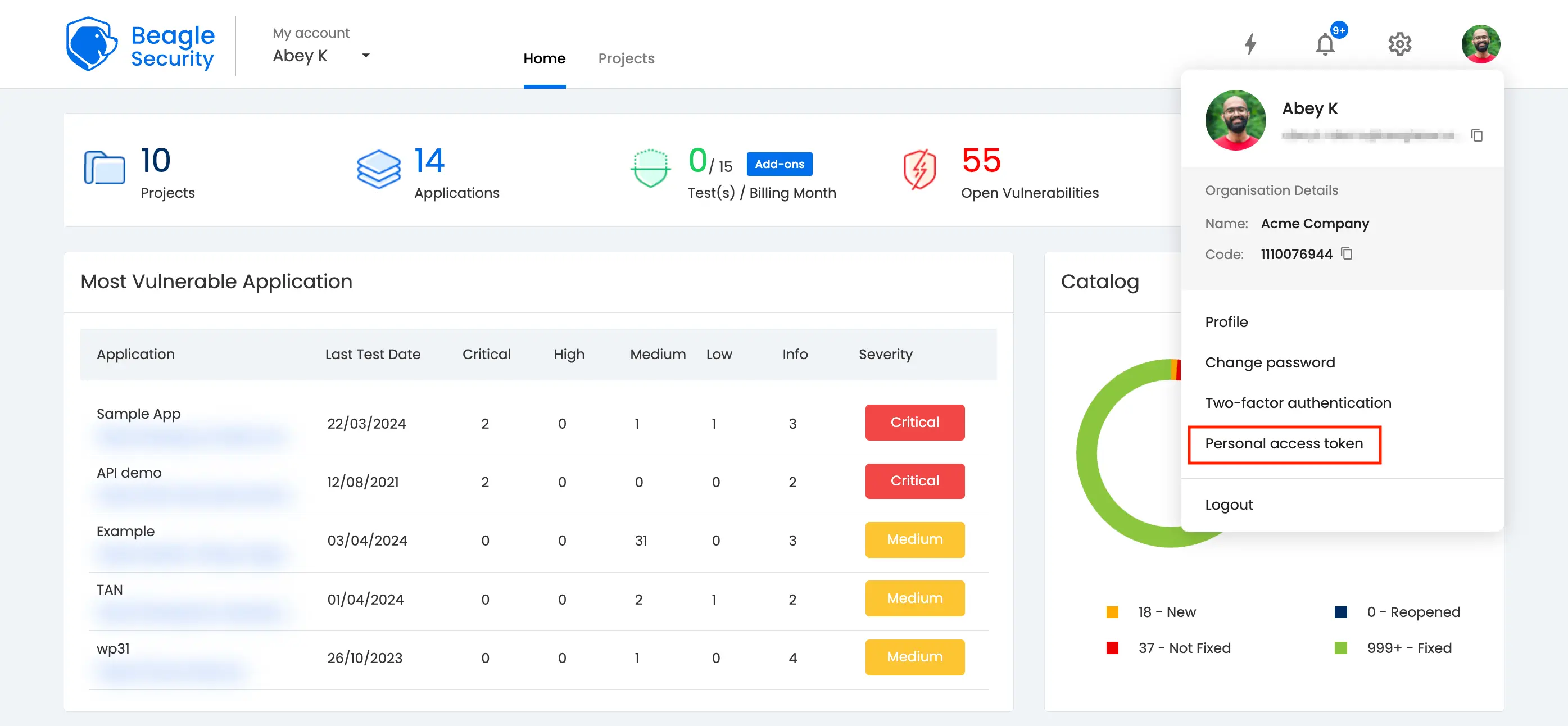
Click on the New personal access token button to generate a fresh one.
Name the access token and optionally set an expiry date.
Define the token’s scope based on your specific requirements.
Once created, you’ll receive a unique access token that can be copied for use.
4. Where can you find the application token in Beagle Security?
To get the application token, you must first add the URL as an application within Beagle Security.
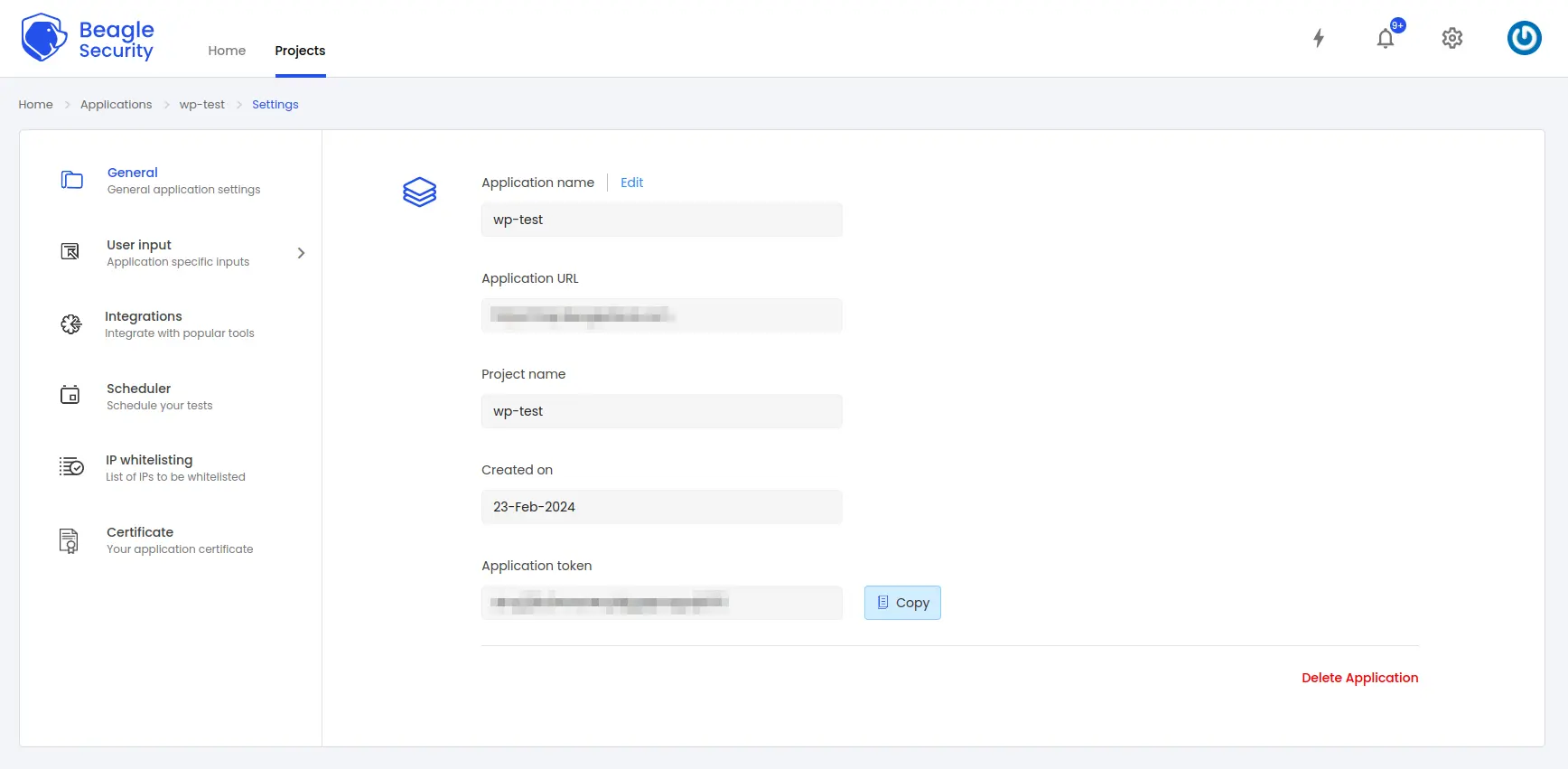
Go to the Application and navigate to its Settings.
Select the General tab.
You’ll be able to copy the Application token for the specific application from there.
5. Set environment variables
Click on “Create parameter” for each of the following:
Name: ACCESS_TOKEN, Value: Your access token generated from Beagle Security.
Name: APPLICATION_TOKEN, Value: Your application token generated from Beagle Security.
Reference these parameters as environment variables in your build settings.
Build spec: Select “Insert Build Commands” and type trigger-test as the build command.
Configure logging: Set your preferred log preferences.
Finalize: Click on “Continue to CodePipeline” and then click on “Done”.
6. Viewing vulnerabilities in Beagle Security after DAST
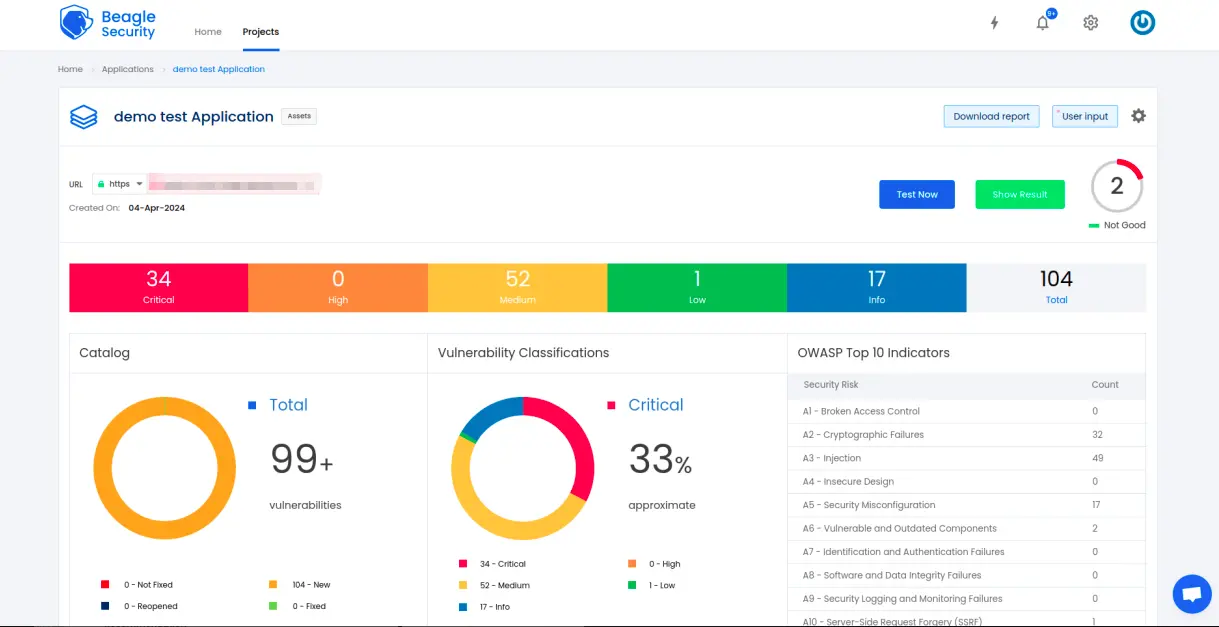
Once the DAST is completed for your AWS CodePipeline, you can view the results from your Beagle Security dashboard.
You’ll be able to see the following details in the application dashboard:
Security score of the application
Vulnerability classification based on criticality
Graphs for vulnerability catalog & vulnerability classification
OWASP Top 10 indicator mapping
Security posture of the application over a period
Vulnerability fixing rate graph
Past test sessions
Check out a demo application dashboard in Beagle Security.
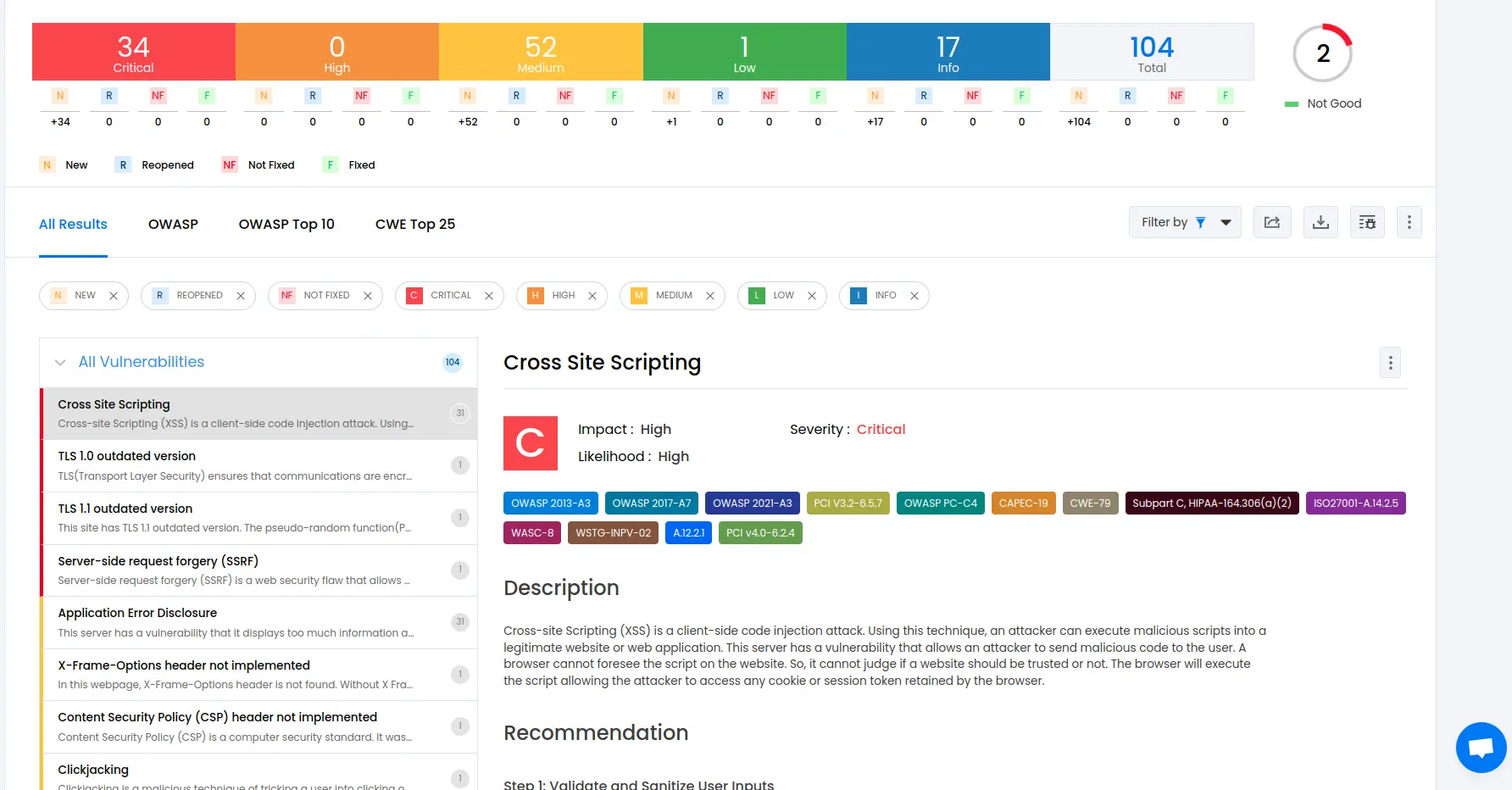
To delve deeper into the vulnerabilities, you can go to the detailed results dashboard of a particular test session. The results dashboard will include the following information:
Detailed listings of all vulnerability findings
Vulnerability tags and classification for each vulnerability finding against security standards
Detailed description, contextual recommendation, proof of exploit and occurrences of each vulnerability finding
Classification of vulnerability findings against OWASP, OWASP Top 10 & CWE Top 25
You can also download these results as PDF reports against OWASP, HIPAA, GDPR & PCI DSS standards
Check out a demo results dashboard in Beagle Security.
Summing up
Incorporating DAST into your AWS CodePipeline is crucial for identifying and addressing security vulnerabilities early in the development process.
Beagle Security provides a comprehensive suite of features, allowing you to run automated penetration tests automatically within your AWS CodePipeline environment.
With Beagle Security’s DAST integrated into your CI/CD pipeline, you can identify and remediate security issues early in the development lifecycle, reducing the risk of potential breaches and ensuring that your applications are resilient against evolving threats.
![Top 10 SDLC tools [2025] Top 10 SDLC tools [2025]](/blog/images/blog-banner-three-cover.webp)


![Best rated DAST tools [2025] Best rated DAST tools [2025]](/blog/images/top-rated-dast-tools-cover.webp)