DAST tools dynamically analyze running applications by simulating attacks and pinpointing potential weaknesses. Now, imagine weaving this security net directly into your CI pipeline through a plugin?
With its flexibility and extensibility, CircleCI becomes the perfect stage for orchestrating your security dance.
By integrating DAST seamlessly into your CircleCI workflow, you transform security from a gatekeeper to a partner in your development journey. In this blog we will show you how you can integrate DAST into your CircleCI pipeline.
Why does your organization need DAST?
Dynamic Application Security Testing (DAST) is a crucial component of any organization’s security strategy for several compelling reasons:
DAST dynamically analyzes running applications from the outside, simulating real-world attacks.
Unlike static analysis tools that inspect source code, DAST evaluates applications in their deployed state. This means it tests how the application behaves in a real-world environment, considering factors such as server configurations, runtime dependencies, and user inputs, resulting in more realistic security testing outcomes.
By incorporating DAST into your development workflow, vulnerabilities can be detected early in the software development lifecycle. This allows teams to address security issues promptly, minimizing the potential impact and cost of remediation.
DAST helps organizations to ensure compliance with data protection and privacy regulations.
Now DAST has become an irreplaceable tool in the arsenal of a lot of organizations’ application security programs.
In this article we will learn how to automate your secure deployment by integrating DAST into your CircleCI pipeline, leveraging the powerful capabilities of Beagle Security.
As a trusted leader in application security, Beagle Security offers an advanced DAST platform designed to enhance the security posture of your applications while seamlessly integrating into your existing DevOps workflows.
What is secure deployment?
Secure deployment refers to the process of deploying software or applications in a manner that minimizes security risks and ensures the integrity, confidentiality, and availability of the deployed system.
It encompasses a series of practices and procedures designed to protect the application and its underlying infrastructure from potential security threats throughout the deployment process.
Implementing secure settings, disabling unnecessary services, and applying patches and updates regularly to address known vulnerabilities ensures that all components are deployed securely.
What is CircleCI?
CircleCI is a cutting-edge continuous integration and continuous delivery (CI/CD) platform that revolutionizes the software development lifecycle. It automates the process from code commit to deployment, ensuring efficiency and reliability throughout.
With CircleCI, teams can build, test, and deploy applications, all while minimizing manual errors and accelerating time-to-market.
Additionally, CircleCI facilitates seamless continuous delivery by automating the deployment of applications to various environments post-testing.
Integrating DAST into your CircleCI pipeline
Integrating DAST into your CircleCI pipeline is a strategic move towards bolstering your application’s security posture.
Two major prerequisites must be met before integration:
Access to a CircleCI account and project.
Access to a Beagle Security account with valid access and application tokens.
Step 1: Configure your CircleCI project
Sign in to your CircleCI account.
Select your project: Navigate to the project for which you want to enable Beagle Security’s automated penetration tests.
Configure config.yml:
Create a .circleci folder in your project repository if it doesn’t exist.
Within the .circleci folder, create or modify the config.yml file.
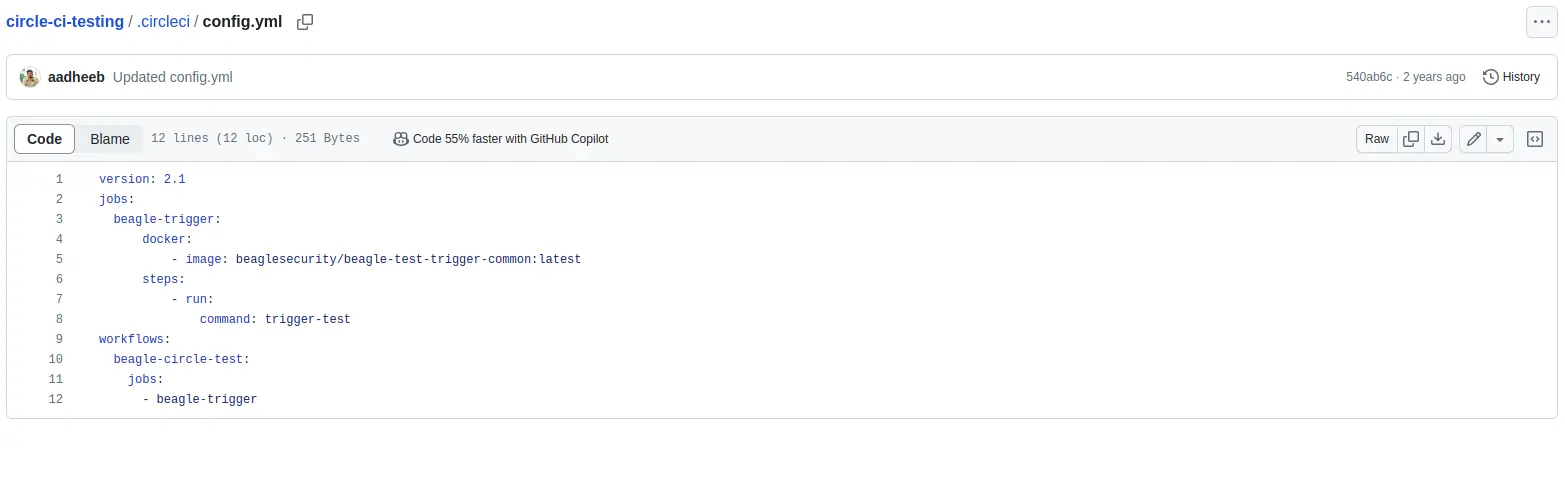
Step 2: Add Beagle trigger job to Config.yml
- Add the following snippet to the jobs: section of your config.yml file:
jobs:
beagle-trigger:
docker:
- image: beaglesecurity/beagle-test-trigger-common:latest
steps:
- run:
command: trigger-test
Step 3: Configure workflow
Add the beagle-trigger job to the jobs: section of your workflow:
workflows:
version: 2
your-workflow-name:
jobs:
- job-1
- job-2
- beagle-trigger
Replace your-workflow-name with the name of your CircleCI workflow and ensure that job-1 and job-2 represent your existing jobs.
Step 4: Set environment variables
Add the required environment variables (ACCESS_TOKEN and APPLICATION_TOKEN) to your CircleCI project:
Click on the gear icon in your CircleCI project.
Navigate to environment variables and click on Add Variable.
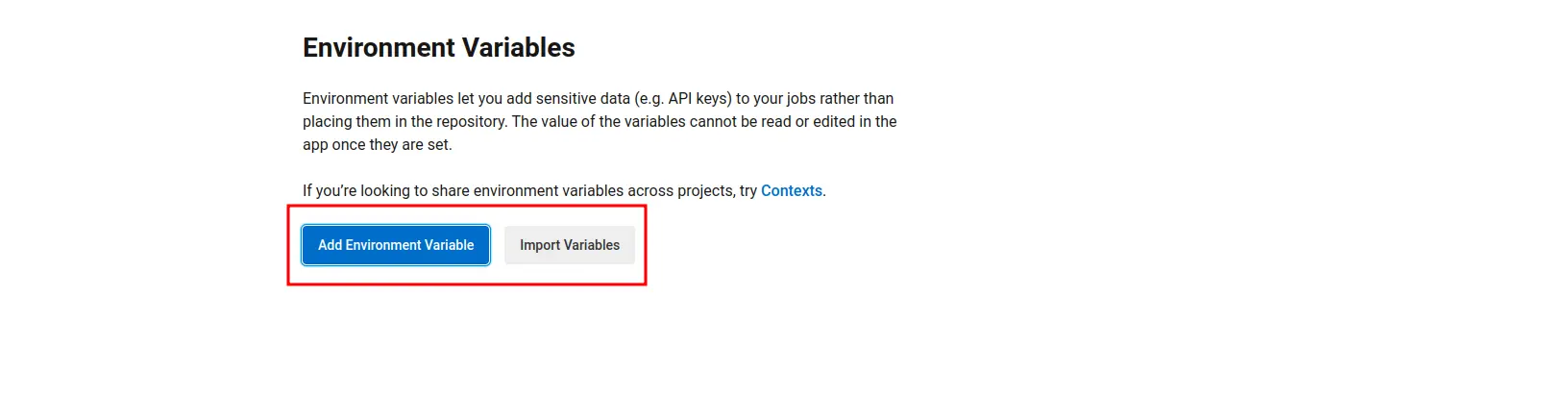
- Ensure that the variable names are set as follows: ACCESS_TOKEN and APPLICATION_TOKEN.
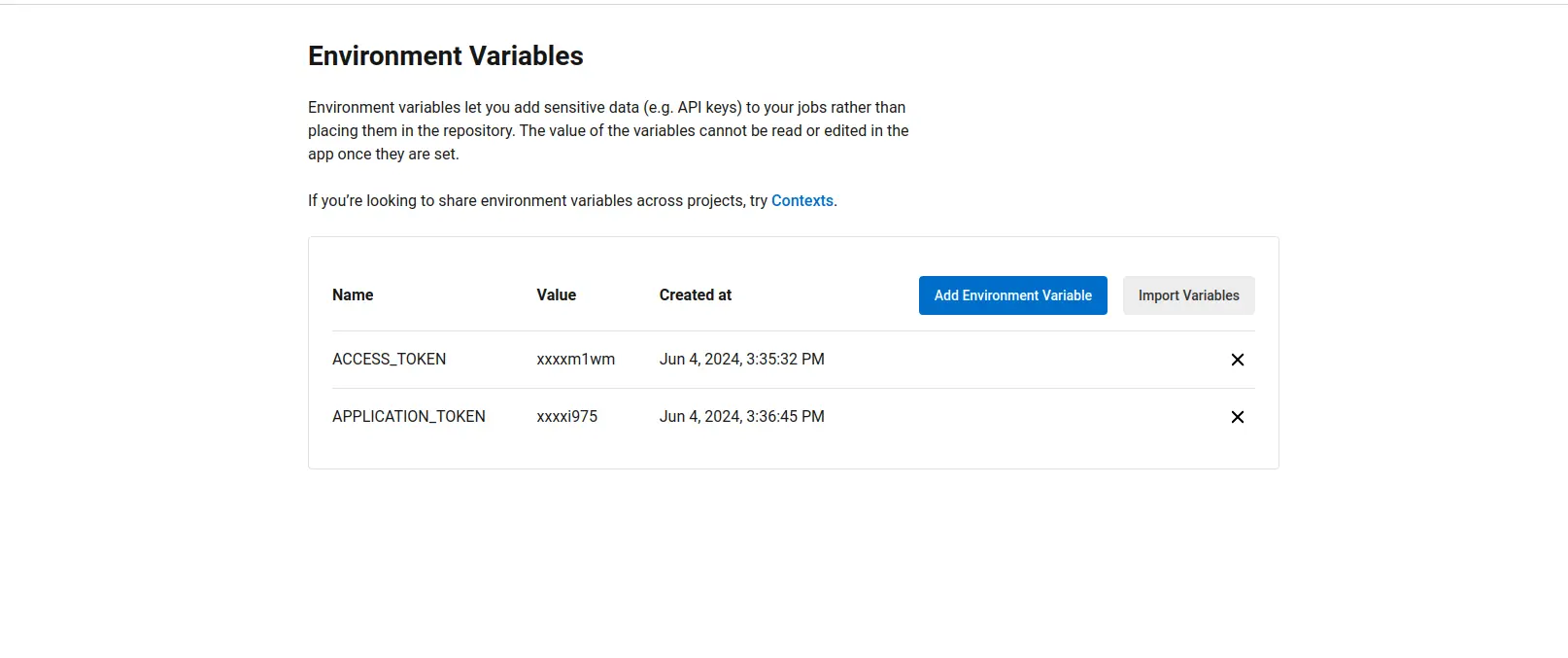
Set their corresponding values to your Beagle Security access token and application token, respectively.
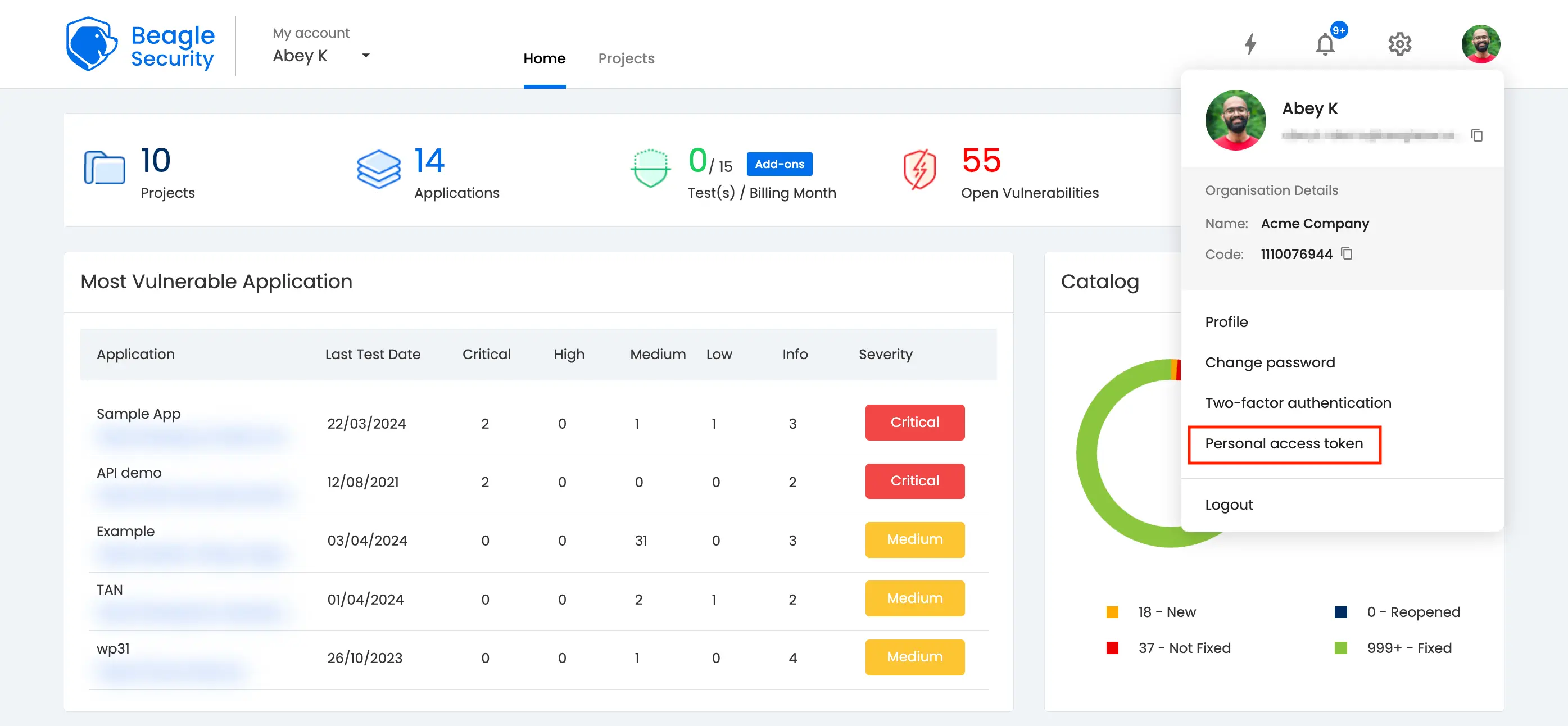
Step 5: Generating access token in Beagle Security
- You can locate your Personal Access Token either by accessing the Profile drop-down menu or by navigating to the Profile section.
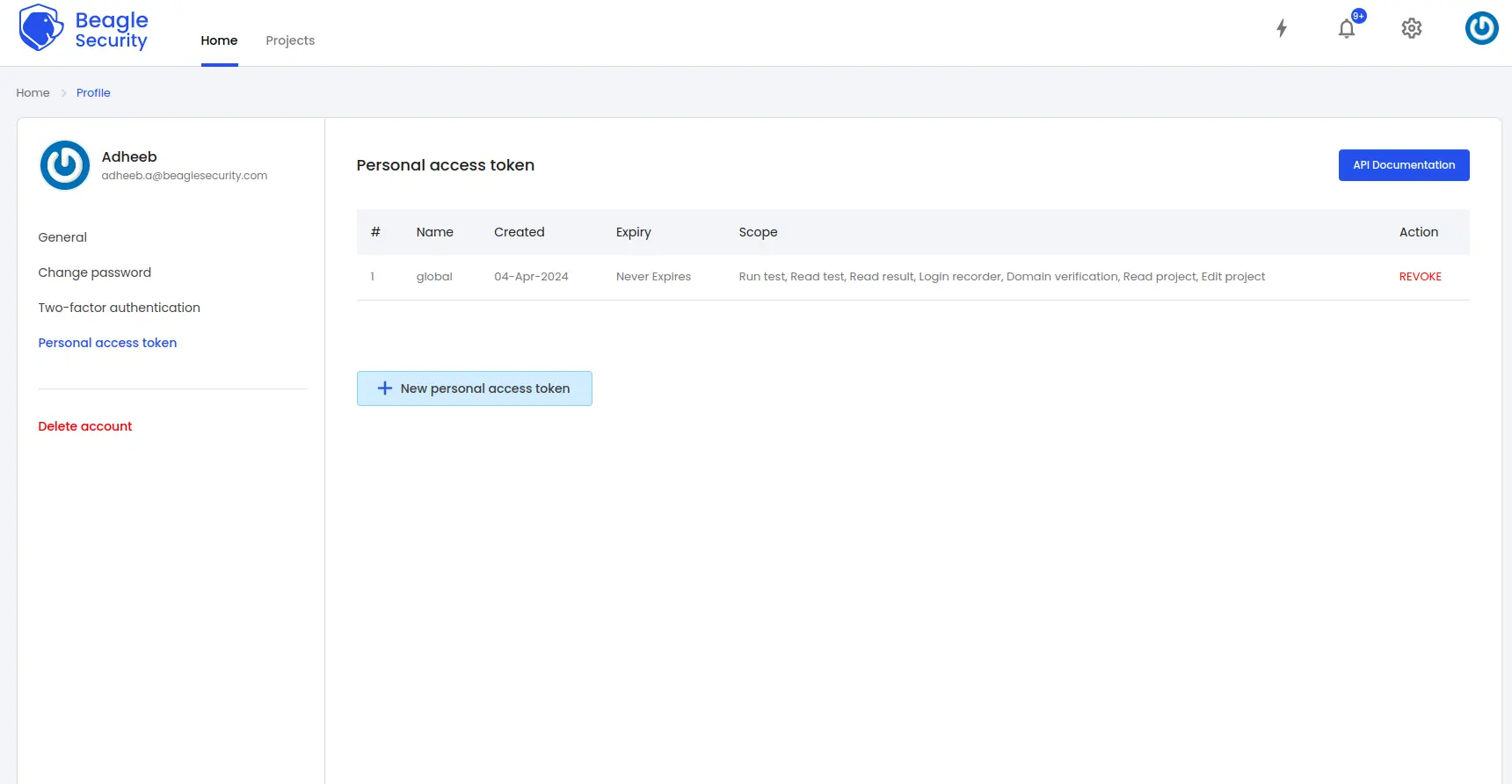
Click on the New personal access token button to generate a fresh one.
Name the access token and optionally set an expiry date.
Define the token’s Scope based on your specific requirements.
Once created, you’ll receive a unique access token that can be copied for use.
Step 6: Where can you find the application token in Beagle Security?
To get the application token, you must first add the URL as an application within Beagle Security.
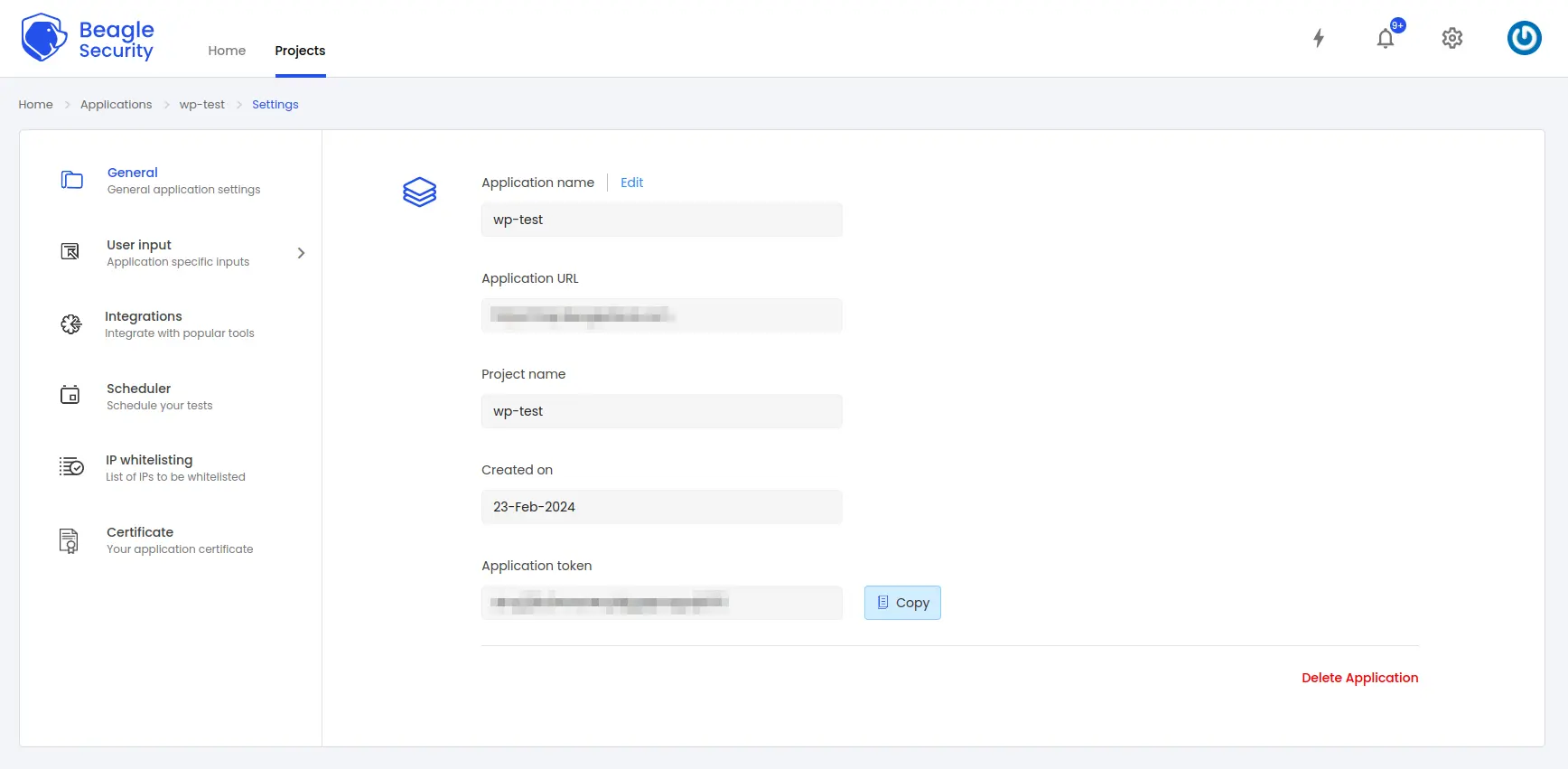
Go to the Application and navigate to its Settings.
Select the General tab.
You’ll be able to copy the Application token for the specific application from there
Step 6: Trigger the build
- Now, trigger your CircleCI build, either through a code push, pull request, or manually via the CircleCI dashboard.
Step 7: Monitor Beagle trigger workflow
- Once the build is triggered, monitor the CircleCI dashboard to observe the beagle-trigger job executing. This job will initiate Beagle Security’s automated penetration test on your application.
Step 8: Viewing vulnerabilities in Beagle Security after DAST
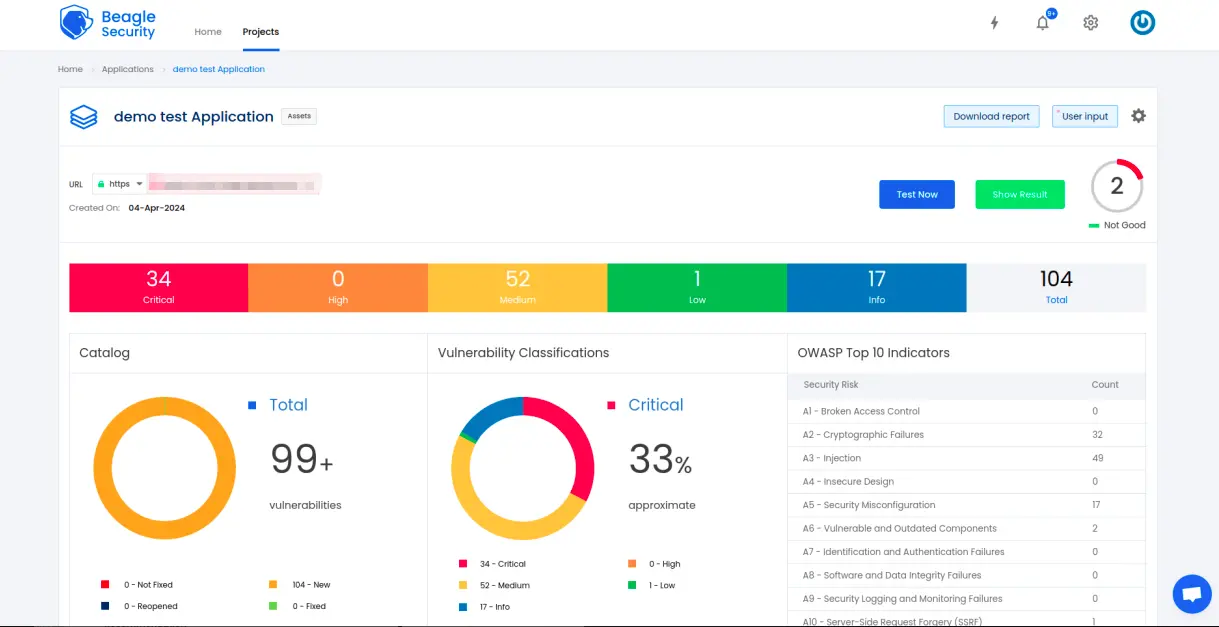
Once the DAST is completed for the CircleCI pipeline, you can view the results from your Beagle Security dashboard.
You’ll be able to see the following details in the application dashboard:
Security score of the application
Vulnerability classification based on criticality
Graphs for vulnerability catalog & vulnerability classification
OWASP Top 10 indicator mapping
Security posture of the application over a period
Vulnerability fixing rate graph
Past test sessions
Check out a demo application dashboard in Beagle Security.
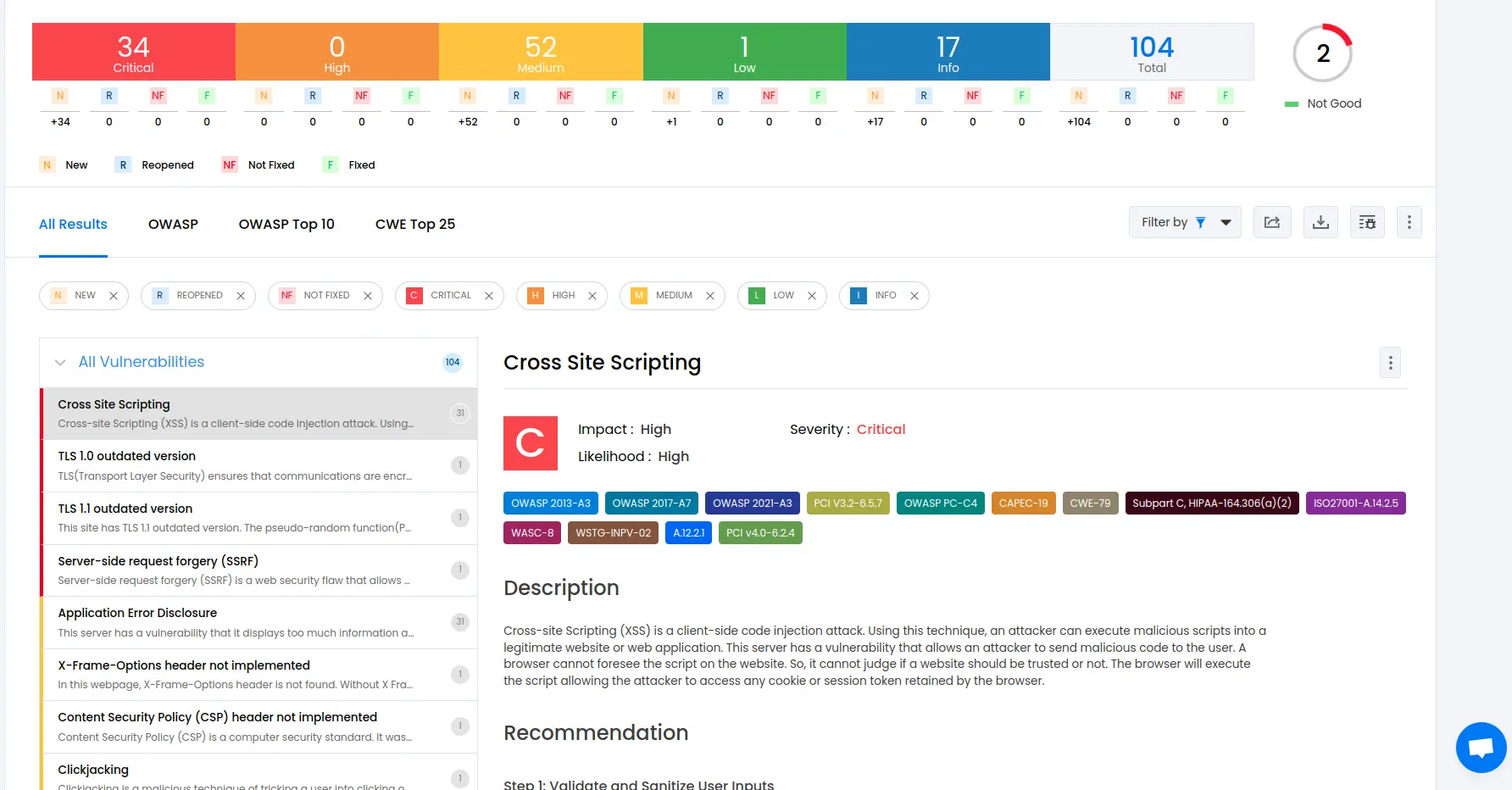
To delve deeper into the vulnerabilities, you can go to the detailed results dashboard of a particular test session. The results dashboard will include the following information:
Detailed listings of all vulnerability findings
Vulnerability tags and classification for each vulnerability finding against security standards
Detailed description, contextual recommendation, proof of exploit and occurrences of each vulnerability finding
Classification of vulnerability findings against OWASP, OWASP Top 10 & CWE Top 25
You can also download these results as PDF reports against OWASP, HIPAA, GDPR & PCI DSS standards
Check out a demo results dashboard in Beagle Security.
Summing up
Integrating Beagle Security’s DAST into your CircleCI pipeline automation is a strategic decision that fortifies your application’s security while streamlining your development workflow.
It fosters a culture of security-conscious development within your team, where security considerations are integrated into every code change and deployment.
You can automate DAST scans, receive actionable insights into potential security risks, and accelerate the delivery of secure and reliable software to your users with Beagle Security.
Ultimately, by prioritizing security within your CircleCI pipeline, you demonstrate a commitment to delivering high-quality products that instill trust and confidence among your customers and stakeholders.
![Top 10 SDLC tools [2025] Top 10 SDLC tools [2025]](/blog/images/blog-banner-three-cover.webp)


![Best rated DAST tools [2025] Best rated DAST tools [2025]](/blog/images/top-rated-dast-tools-cover.webp)










