With cyber threats constantly evolving, developers and organizations are forced to adopt proactive measures to identify and mitigate vulnerabilities early in the development process.
This is where Dynamic Application Security Testing (DAST) comes into play. Incorporating DAST, ensure that your applications are rigorously scanned for vulnerabilities in real-time, right from the moment of code commit to deployment.
By integrating DAST into Continuous Integration/Continuous Deployment (CI/CD) pipelines, developers can automate security testing, identify issues early, and streamline the deployment process without compromising security.
What is DAST and why do you need it for your organization?
Dynamic Application Security Testing (DAST) is an automated testing methodology crafted to pinpoint security vulnerabilities within a web application.
Its methodology involves simulating attacks on the application and scrutinizing the responses. Unlike static testing, which scrutinizes an application’s code, DAST evaluates the application’s real-time functioning, rendering it a potent tool for fortifying live web applications.
DAST operates as a black box testing approach, devoid of any insight into the internal architecture of the application under test. Instead, it scrutinizes the application externally, akin to a potential attacker.
This methodology enables DAST to unearth vulnerabilities that may elude detection through other testing methods, thus establishing it as a pivotal element of a comprehensive security framework.
The chief objective of it is to uncover potential security loopholes before malicious actors can exploit them.
These vulnerabilities may encompass issues such as SQL Injection, Cross-Site Scripting (XSS), and other vulnerabilities that could facilitate unauthorized access to sensitive data.
What are secure development practices?
Secure development practices refer to a set of methodologies, techniques, and guidelines aimed at building software applications with robust security measures from the ground up.
These practices are essential for ensuring that software systems are resilient to cyber threats and vulnerabilities throughout their lifecycle.
By adhering to secure development practices, organizations can systematically identify and address potential vulnerabilities throughout the software development lifecycle, from conception to deployment and maintenance.
These practices encompass various facets such as threat modeling, code review, input validation, authentication, secure communication, error handling, patch management, and security testing.
Implementing secure development practices not only secures applications against potential attacks but also instills confidence among users and stakeholders, thereby fostering trust, enhancing reputation, and ensuring regulatory compliance.
What is Bitbucket?
Bitbucket is a web-based platform for hosting and collaborating on Git repositories. It provides tools for version control, issue tracking, and code review.
With Bitbucket, teams can securely store their code, manage access permissions, track changes made by team members, and facilitate collaboration through features such as pull requests and inline commenting.
It supports both public and private repositories, allowing teams to work on proprietary code securely.
How to integrate DAST into your Bitbucket pipeline?
Integrating automated security testing into your Bitbucket pipelines can help you identify vulnerabilities early in the development lifecycle.
In this tutorial, we’ll walk you through the steps to integrate Beagle Security into your Bitbucket pipelines, ensuring that your web applications are secure before deployment.
Step 1: Log in to Bitbucket
- First, log in to your Bitbucket account.
Step 2: Select your repository/project
- Navigate to the repository or project where you want to integrate Beagle Security tests.
Step 3: Configure bitbucket-pipelines.yml
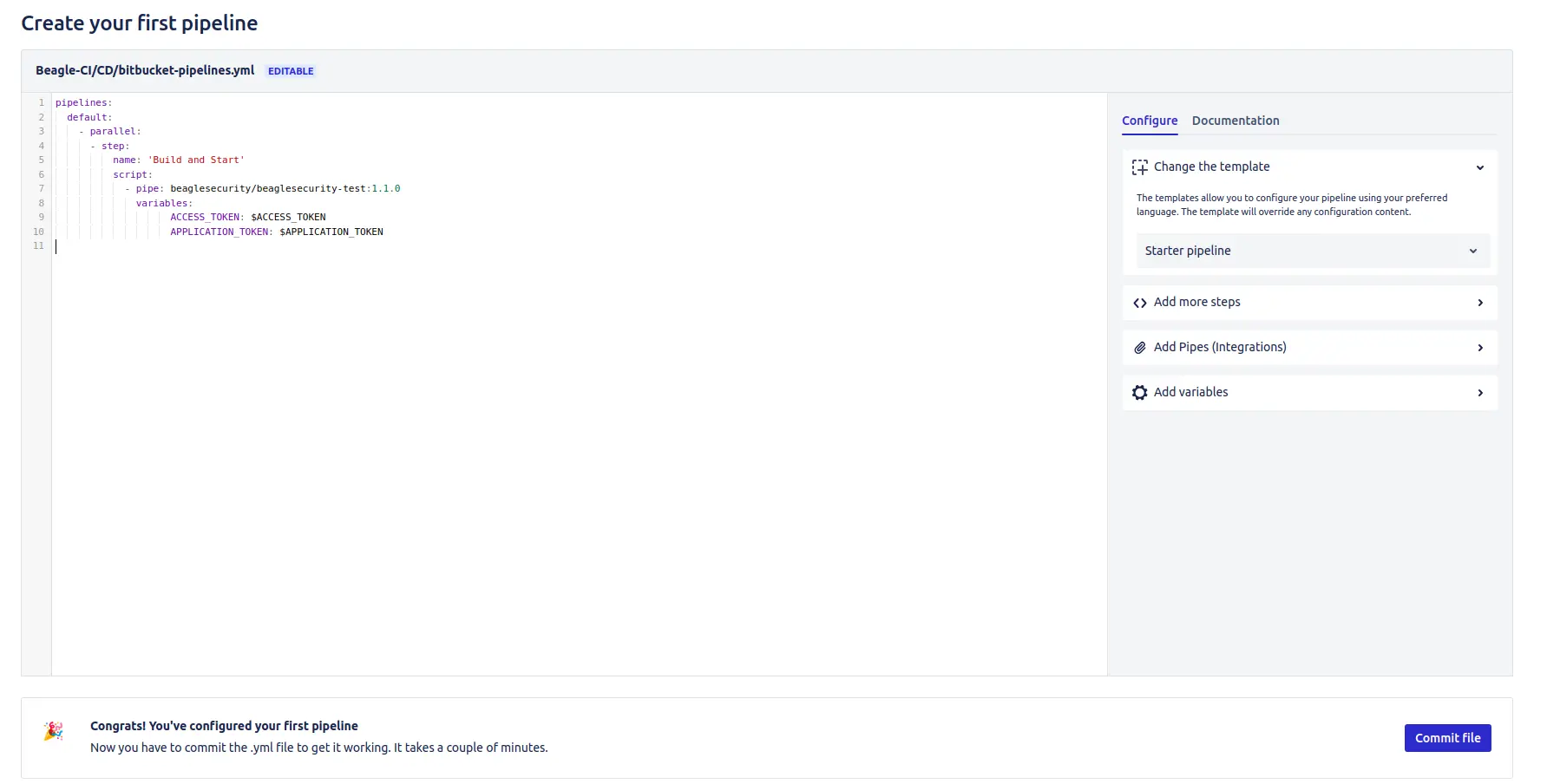
If your repository/project already has a Bitbucket pipeline configured, skip to Step 6. Otherwise, follow these steps to create a new pipeline:
Select “Pipelines” from the side menu.
Navigate to “Choose a language template” and click on “Starter Pipeline”.
Configure the bitbucket-pipelines.yml file as follows:
image: node:12.18.3 # Or choose an appropriate Docker image for your project
pipelines:
default:
- step:
name: Run Beaglesecurity Tests
script:
- pipe: beaglesecurity/beaglesecurity-test:1.1.0
variables:
ACCESS_TOKEN: $ACCESS_TOKEN
APPLICATION_TOKEN: $APPLICATION_TOKEN
Step 4: Generating access token in Beagle Security
- You can locate your Personal Access Token by accessing the Profile drop-down menu.
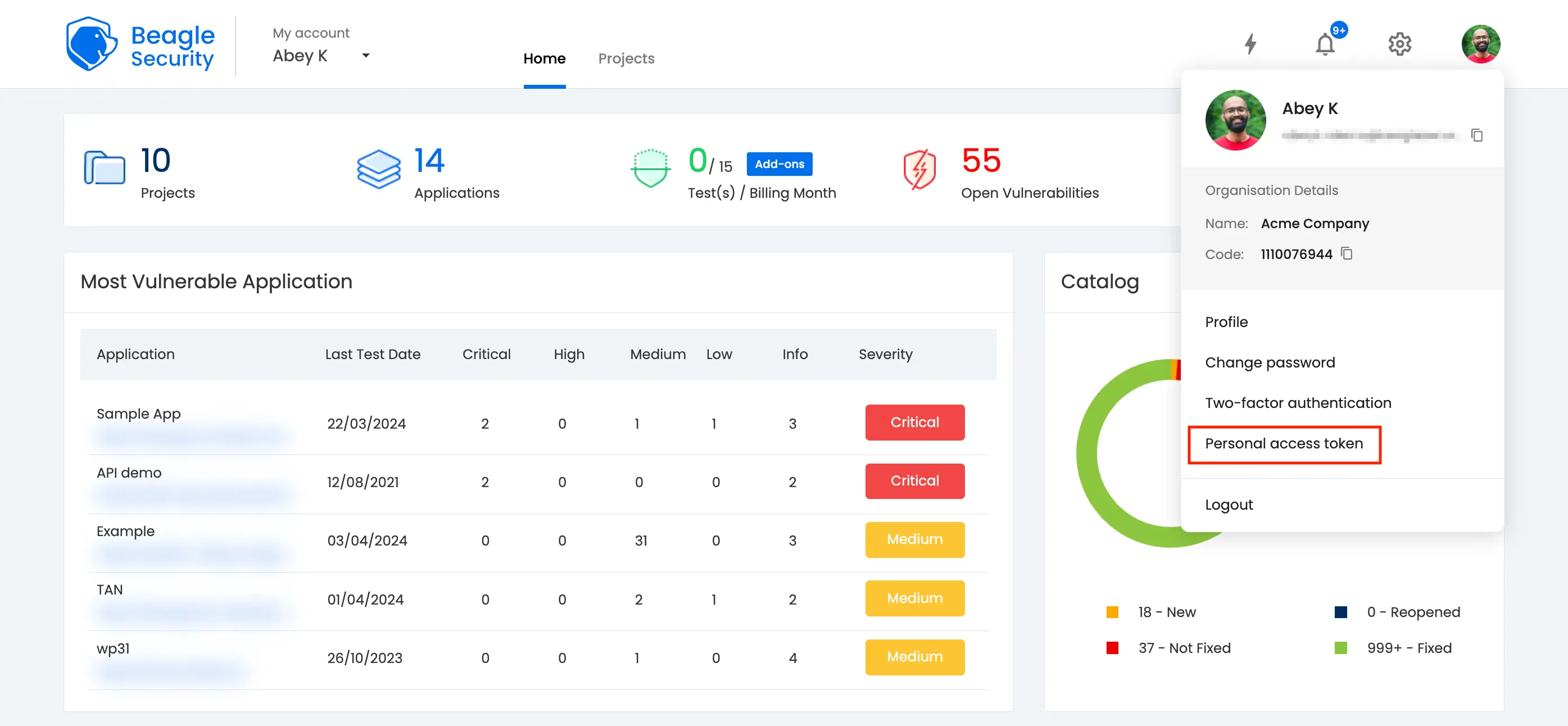
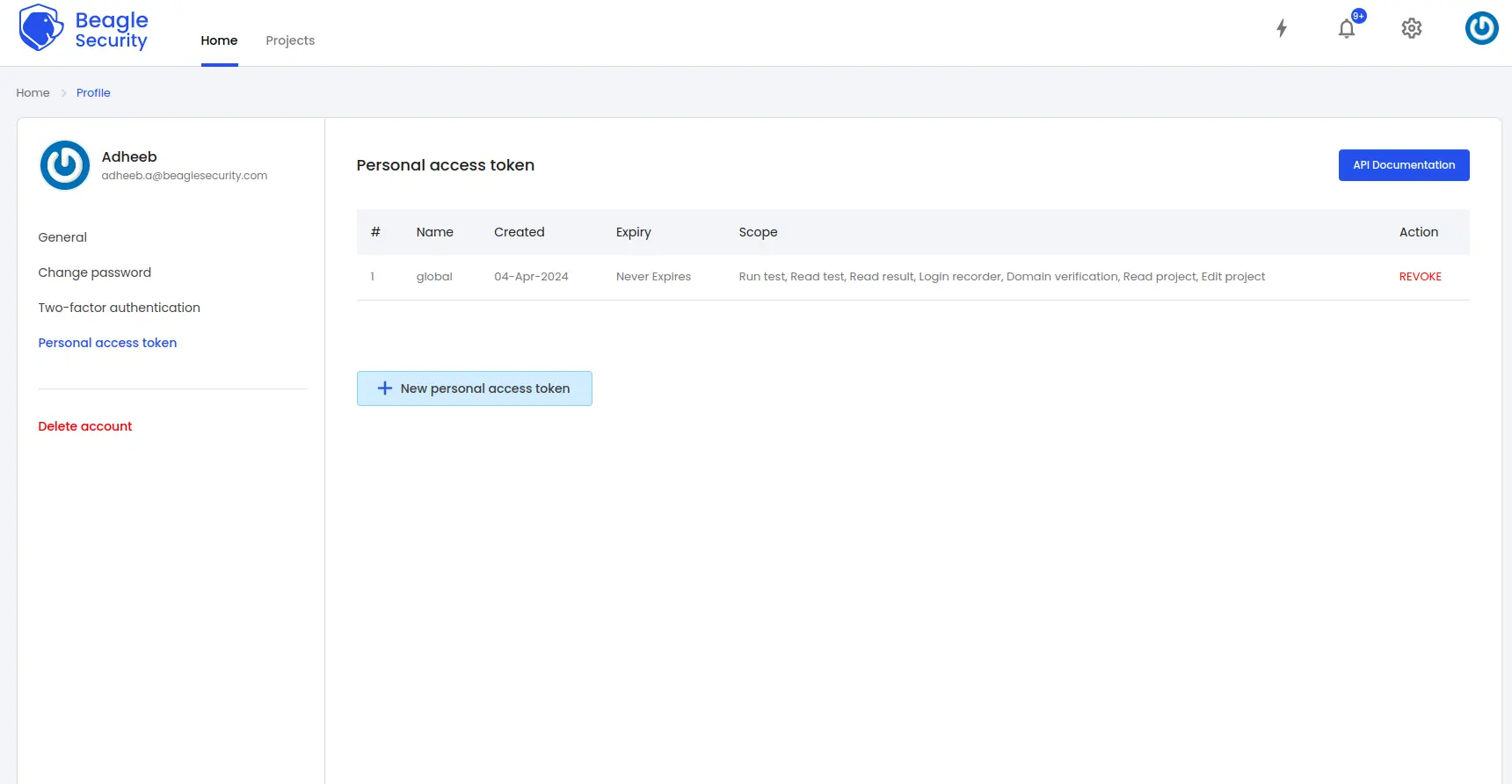
Click on the New personal access token button to generate a fresh one.
Name the access token and optionally set an expiry date.
Define the token’s Scope based on your specific requirements.
Once created, you’ll receive a unique access token that can be copied for use.
Step 5: Where can you find the application token in Beagle Security?
To get the application token, you must first add the URL as an application within Beagle Security.
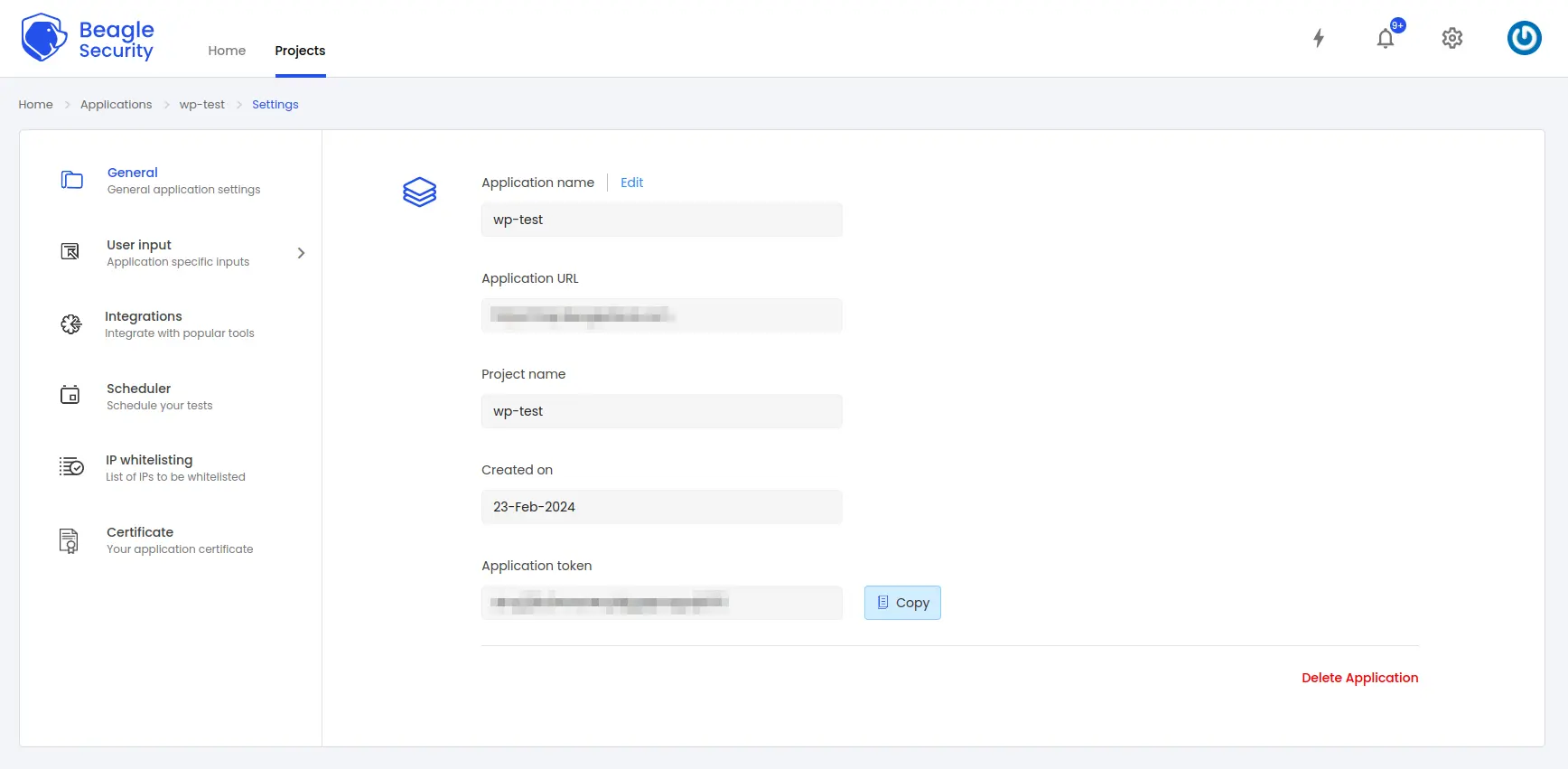
Go to the Application and navigate to its Settings.
Select the General tab.
You’ll be able to copy the Application token for the specific application from there
Step 6: Add repository variables
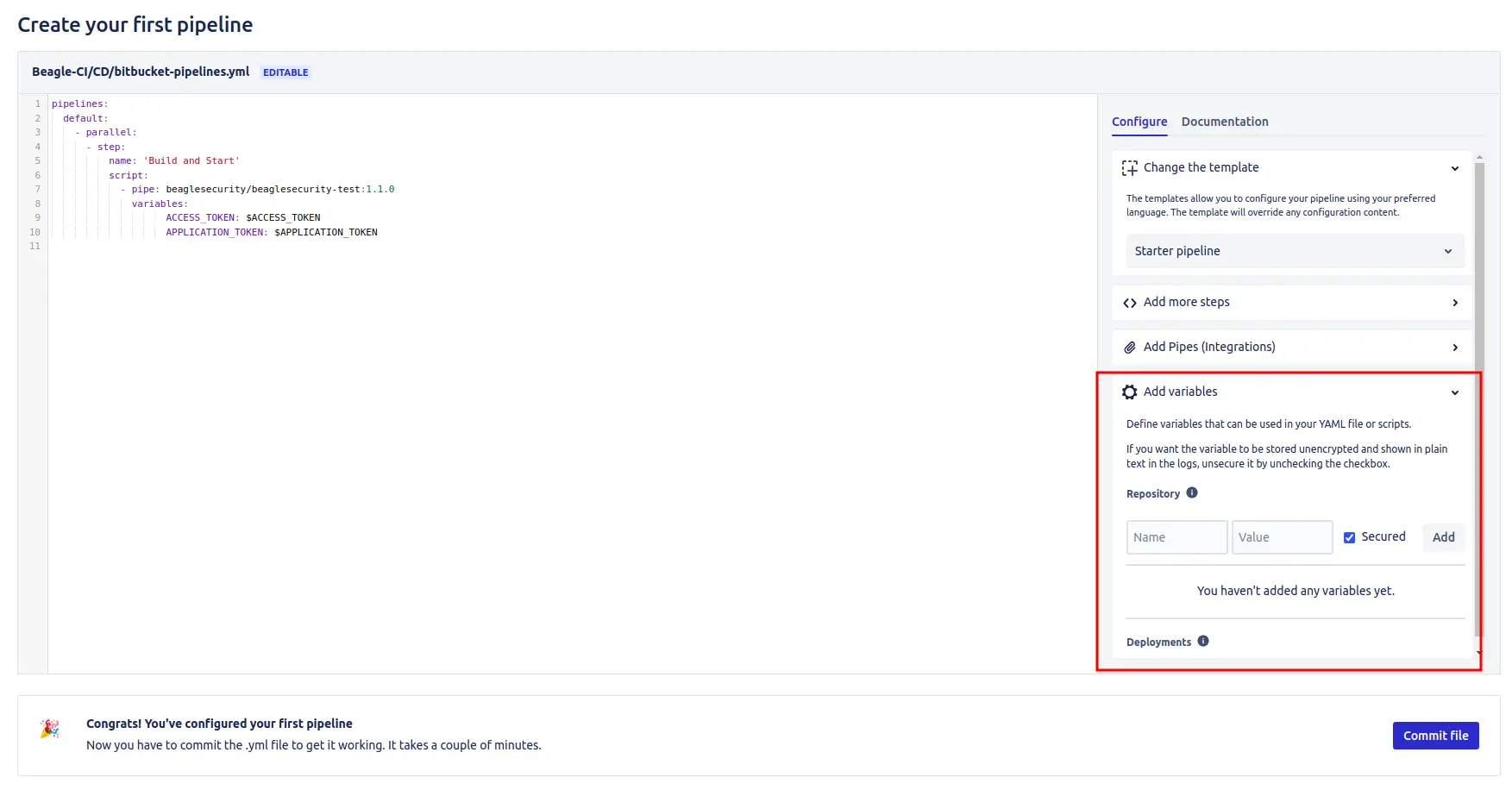
To securely store your Beagle Security access tokens in Bitbucket pipelines, follow these steps:
Click on the Settings icon in the Bitbucket interface.
Select “Repository variables”.
Add the following variables:
Name: ACCESS_TOKEN
Value: [Access token generated from Beagle Dashboard]
Check “Secured” to keep the token secret.
Name: APPLICATION_TOKEN
Value: [Application token generated from Beagle Dashboard]
Check “Secured” to keep the token secret.
- Click on “Commit” to save the changes.
Step 7: Run Beagle Security tests
Your Bitbucket pipeline is now configured to run Beagle Security tests on your application build.
Every time you push changes to your repository, the pipeline will automatically trigger and execute the security tests, helping you identify any vulnerabilities.
By integrating Beagle Security tests into your Bitbucket pipelines, you can ensure that your application is secure and reliable before deploying it to production.
This proactive approach to security can save you time and effort by catching potential issues early in the development process.
Step 8: Viewing vulnerabilities in Beagle Security after DAST
Once the DAST is completed for the Bitbucket CI/CD pipeline, you can view the results from your Beagle Security dashboard.
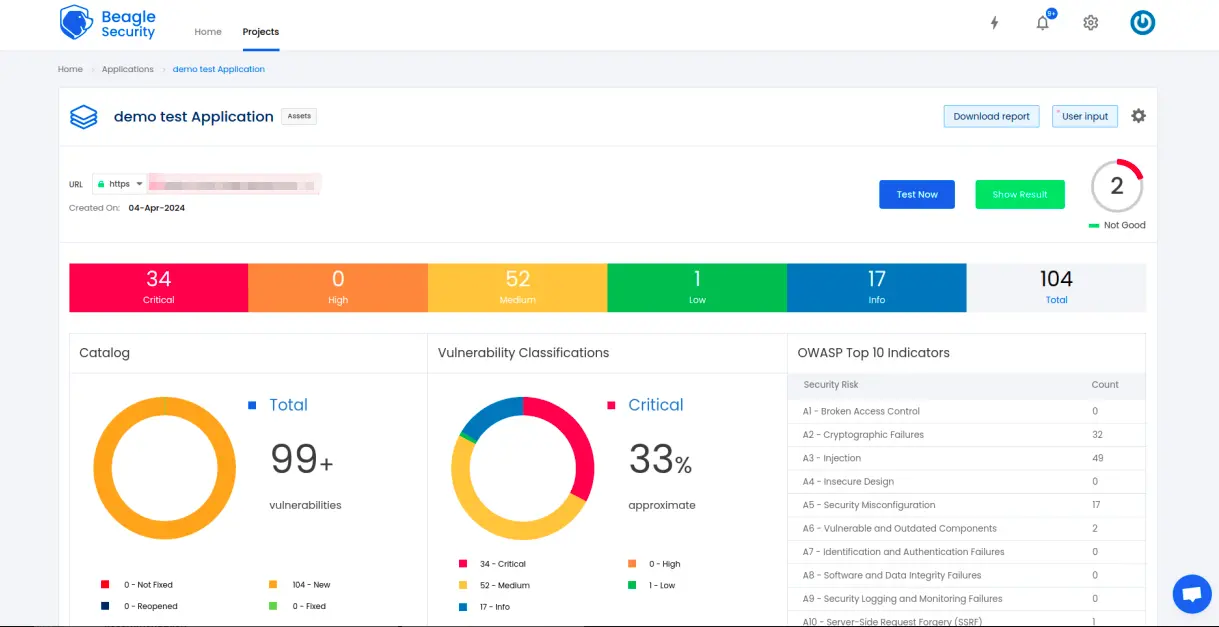
You’ll be able to see the following details in the application dashboard:
Security score of the application
Vulnerability classification based on criticality
Graphs for vulnerability catalog & vulnerability classification
OWASP Top 10 indicator mapping
Security posture of the application over a period
Vulnerability fixing rate graph
Past test sessions
Check out a demo application dashboard in Beagle Security.
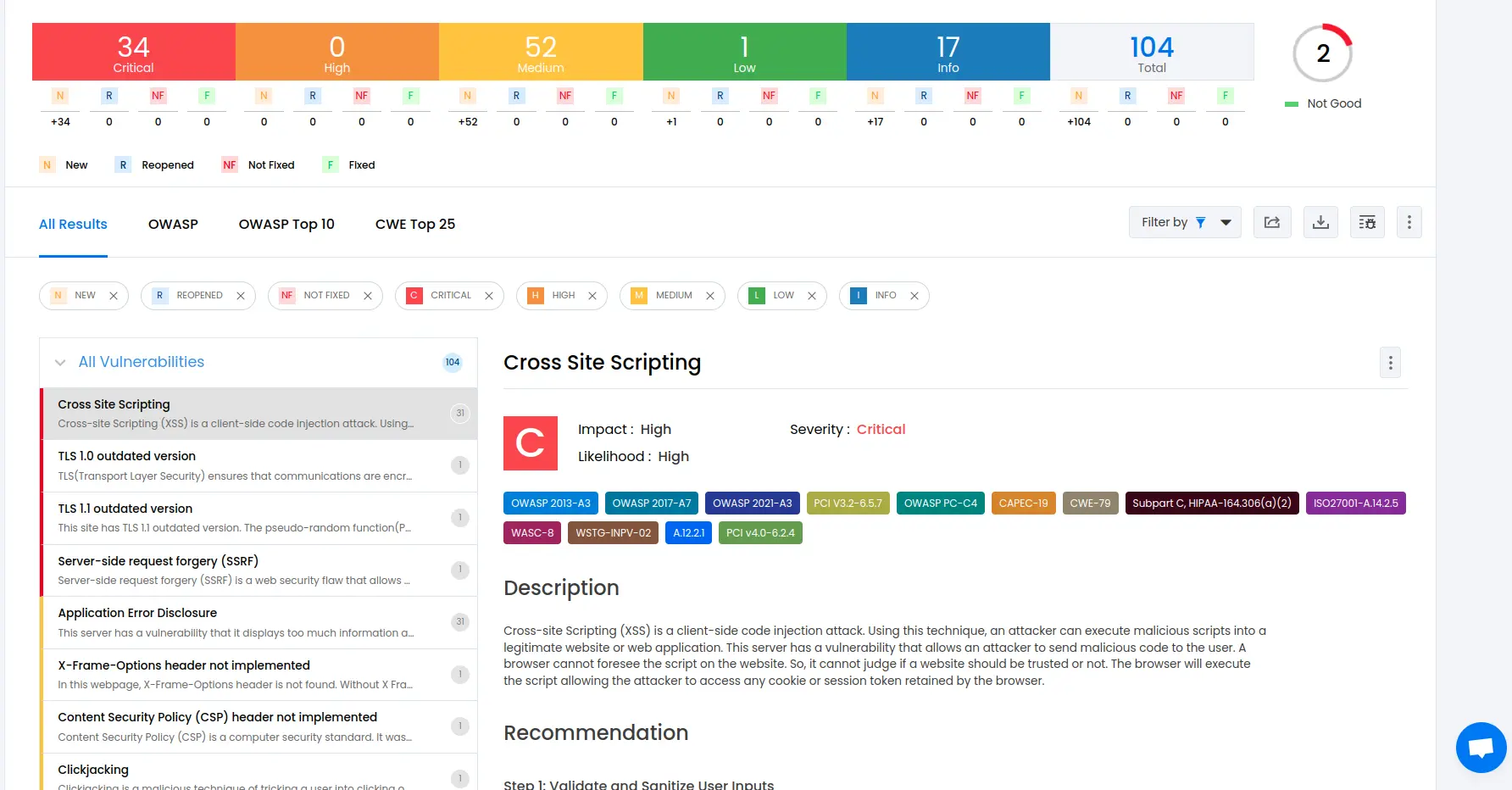
To delve deeper into the vulnerabilities, you can go to the detailed results dashboard of a particular test session. The results dashboard will include the following information:
Detailed listings of all vulnerability findings
Vulnerability tags and classification for each vulnerability finding against security standards
Detailed description, contextual recommendation, proof of exploit and occurrences of each vulnerability finding
Classification of vulnerability findings against OWASP, OWASP Top 10 & CWE Top 25
You can also download these results as PDF reports against OWASP, HIPAA, GDPR & PCI DSS standards
Check out a demo results dashboard in Beagle Security.
Summing up
Incorporating DAST into your Bitbucket CI/CD pipeline is crucial for identifying and addressing security vulnerabilities early in the development process.
Beagle Security provides a comprehensive suite of features, allowing you to run automated penetration tests automatically within your Bitbucket environment.
With Beagle Security’s DAST integrated into your CI/CD pipeline, you can identify and remediate security issues early in the development lifecycle, reducing the risk of potential breaches and ensuring that your applications are resilient against evolving threats.
![Top 10 SDLC tools [2025] Top 10 SDLC tools [2025]](/blog/images/blog-banner-three-cover.webp)


![Best rated DAST tools [2025] Best rated DAST tools [2025]](/blog/images/top-rated-dast-tools-cover.webp)