DevOps has evolved from “how fast can we ship” to “how fast can we ship securely.” In 2025, security must be embedded in every step of the software delivery pipeline.
This means investing in tools that scan code, detect vulnerabilities, secure dependencies, manage secrets, protect infrastructure, and more. The right toolset enables speed, trust, and resilience.
Here are my picks for the top DevOps security tools in 2025, each leading in its category, with strong ratings and pricing models that suit different types of teams and organizations:
Best DAST tool for web application & API penetration testing: Beagle Security
Best SAST tool for code security: Semgrep
Best SCA tool for supply chain security: Trivy
Best IaC security tool for scanning configuration files: Checkov
Best secrets management and detection tool: GitGuardian
Best container and cloud security tool: Wiz
Best all-in-one platform for integrated security capabilities: GitLab
Top 10 DevOps security tools in 2025 detailed list
Beagle Security
Beagle Security provides AI-driven automated penetration testing for web applications and APIs. Unlike traditional scanners, it simulates real-world attacks and handles complex authentication flows with ease. Its strength lies in reducing false positives while giving developers actionable remediation guidance.
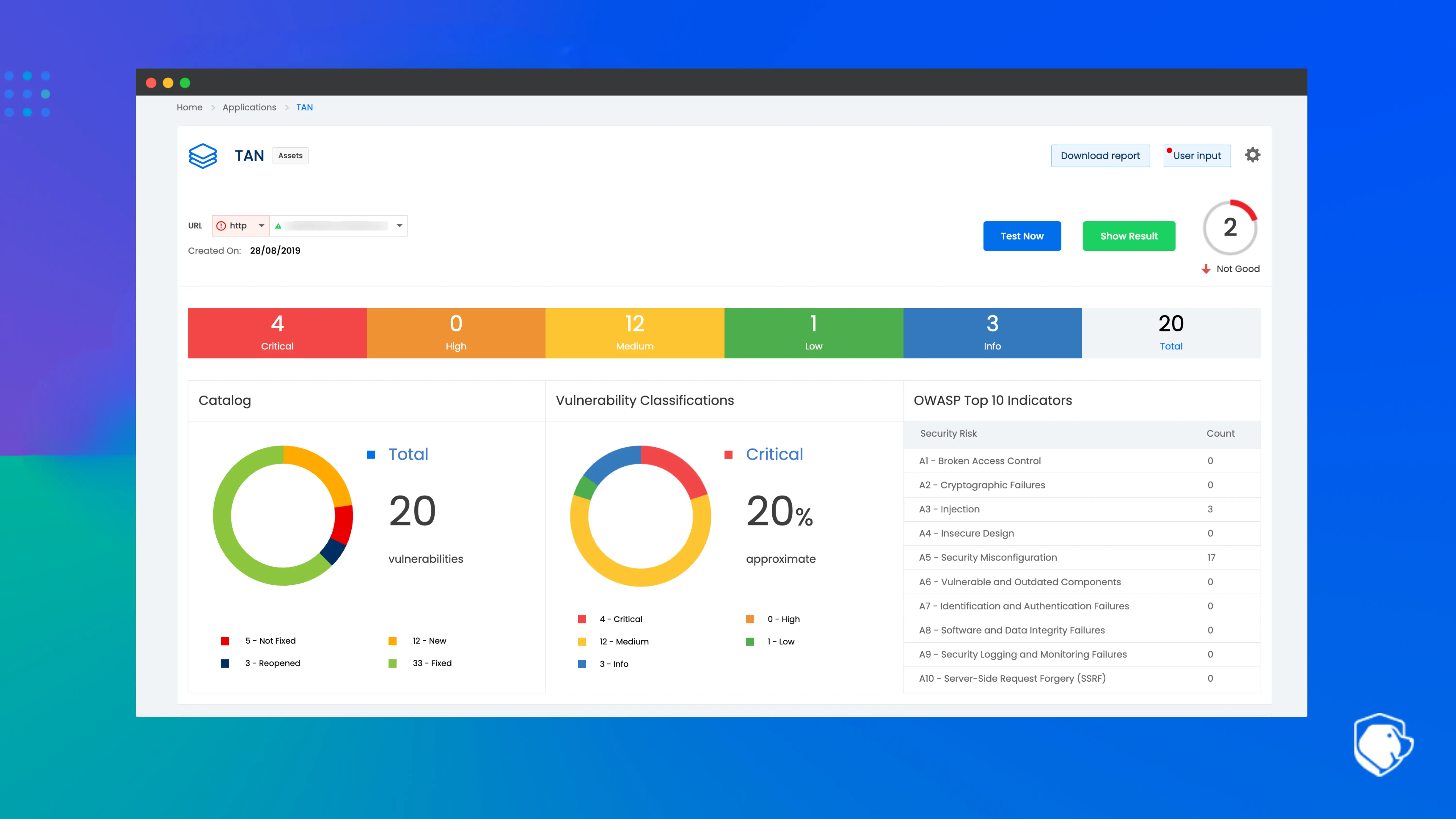
Key highlights:
Automated DAST with real-world attack simulation
Advanced API and GraphQL support
Compliance-ready reports (OWASP, HIPAA, PCI DSS)
Seamless CI/CD integration
Pricing: Plans begin at $119/month
Semgrep
Semgrep is a lightweight, developer-first static analysis tool. It helps catch security flaws early by scanning source code against customizable rules. Its flexibility and speed make it popular for teams that want effective SAST without heavy overhead.
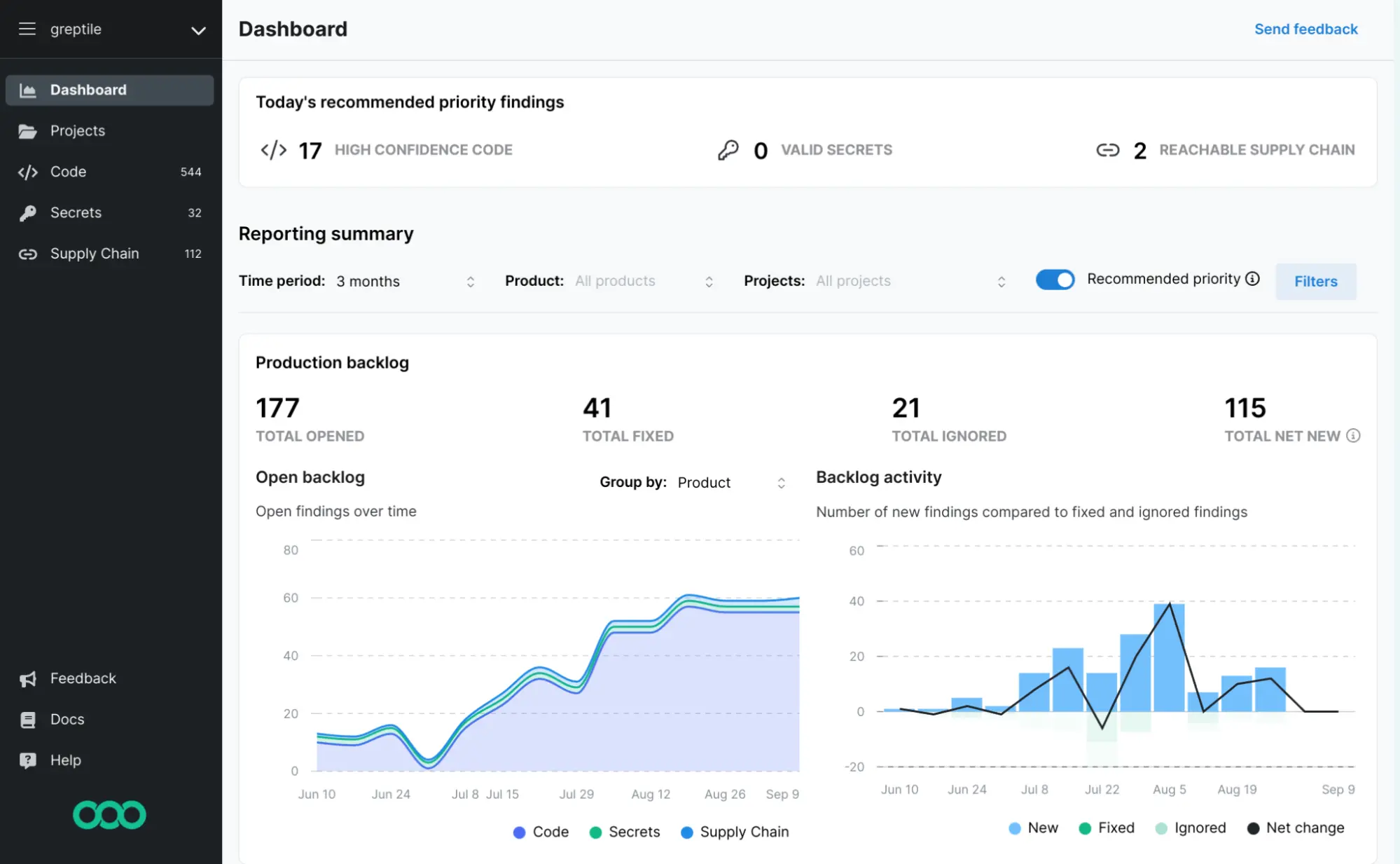
Key highlights:
Language-aware, customizable rule sets
Strong developer community
CI/CD friendly
Free and enterprise editions available
Pricing: Has a free tier. Paid plans start around $40 per contributor/month for more advanced features.
Trivy
Trivy is an open-source Software Composition Analysis (SCA) tool by Aqua Security that identifies vulnerabilities in open-source dependencies, container images, and Infrastructure-as-Code templates. It’s widely used for securing the software supply chain.
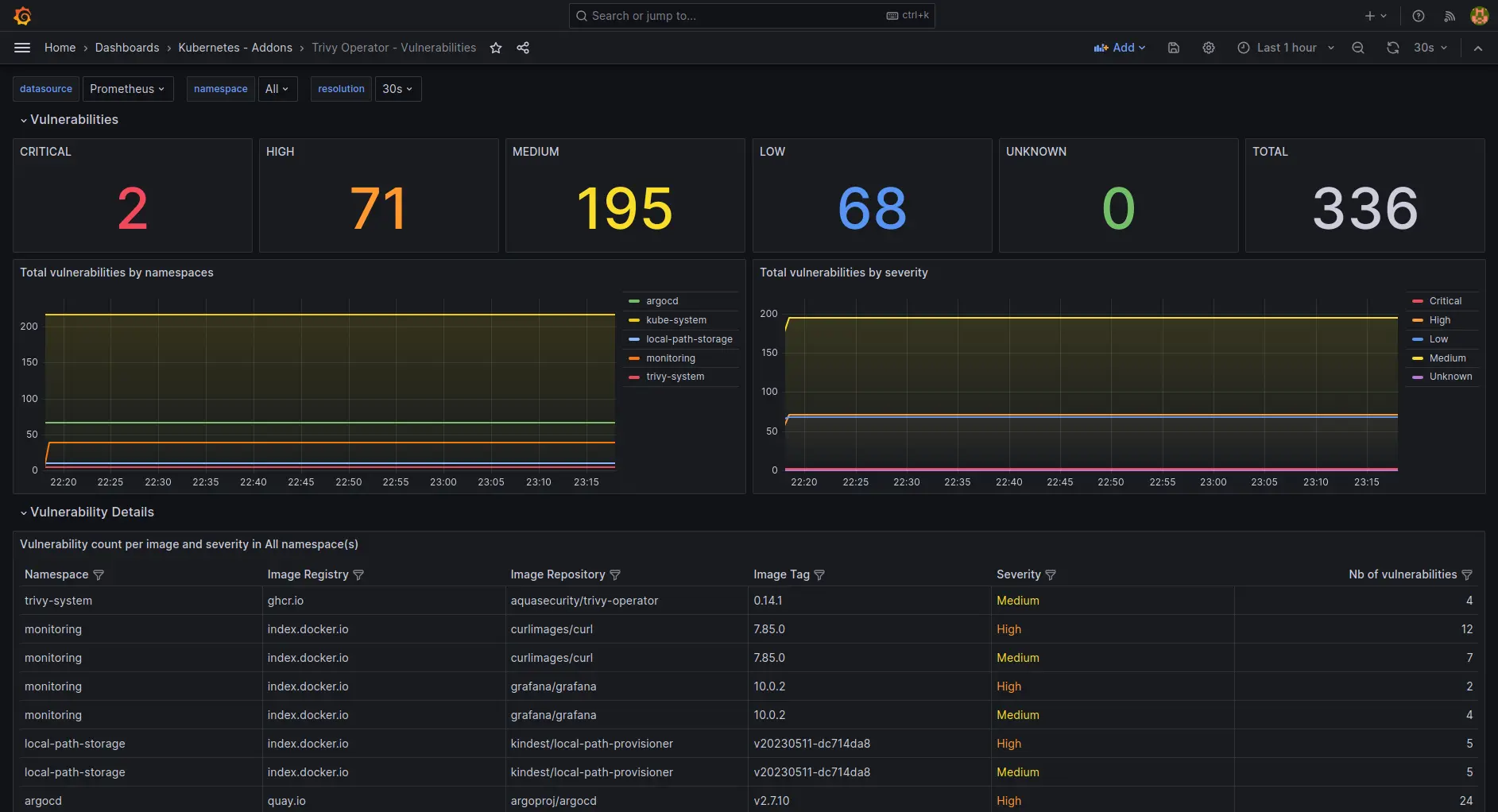
Key highlights:
Scans containers, OS packages, and IaC files
Detects known vulnerabilities (CVEs)
Compliance and misconfiguration checks
Lightweight and easy to integrate
Pricing: Open-source tool that’s free to use.
Checkov
Checkov is an open-source platform managed by Prisma Cloud that specializes in securing Infrastructure-as-Code (IaC) by scanning Terraform, CloudFormation, Kubernetes, and Helm files for misconfigurations before deployment.
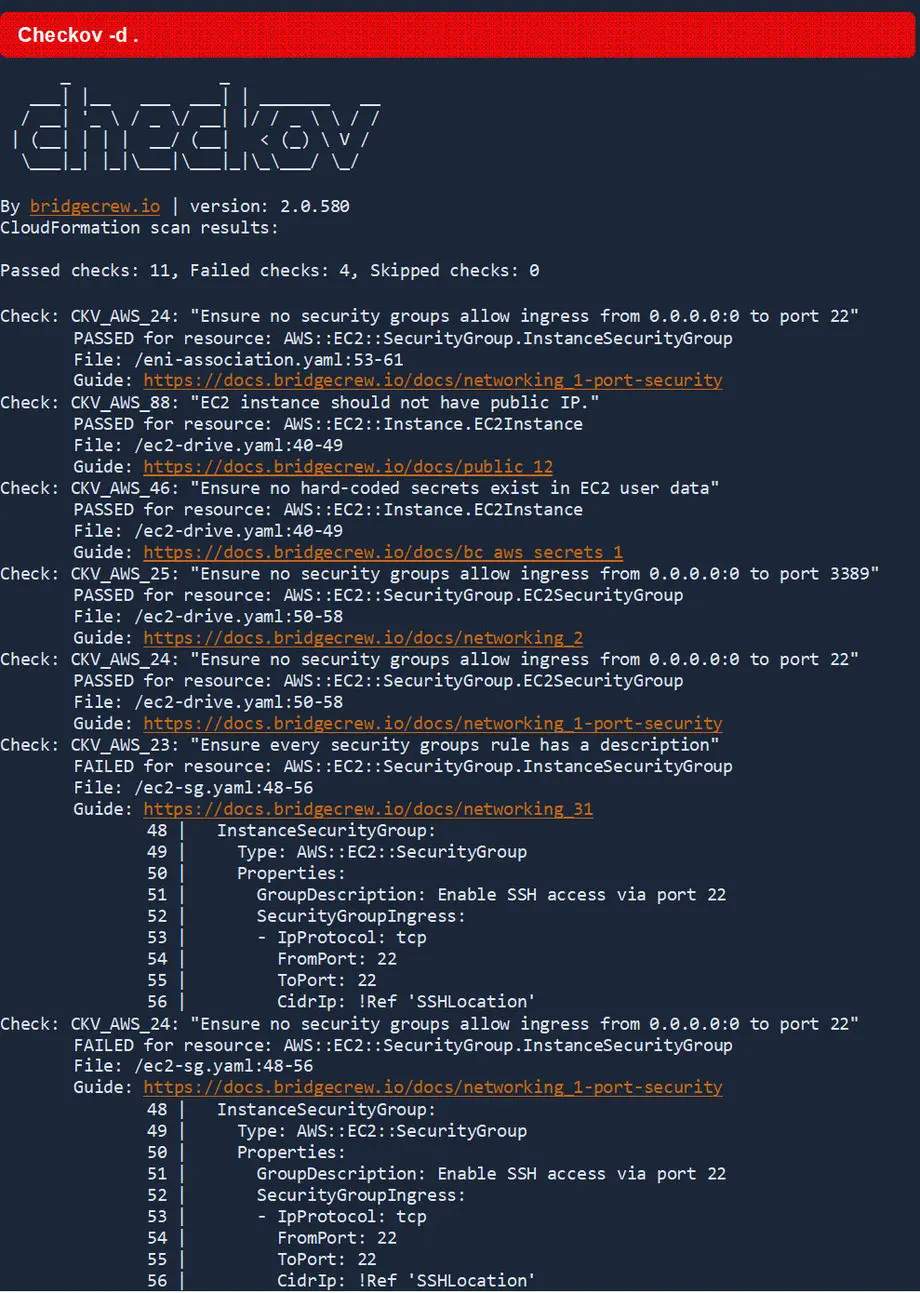
*Checkov output visualised on Prisma Cloud
Key highlights:
Policy-as-code with pre-built checks
Cloud-agnostic support (AWS, Azure, GCP)
Prevents misconfigurations at the commit stage
Integrates into CI/CD pipelines
Pricing: Open source.
GitGuardian
GitGuardian helps teams prevent secrets sprawl by detecting hardcoded API keys, credentials, and other sensitive data in source code and logs.

Key highlights:
Real-time secrets detection
Monitors public and private repositories
Incident remediation workflows
Developer-friendly dashboards
Pricing: Free plan for smaller teams; higher plans are quote-based.
Wiz
Wiz is a leader in cloud and container security, providing deep visibility into workloads across AWS, Azure, GCP, and Kubernetes. It helps organizations detect risks at runtime with context-aware prioritization.
Key highlights:
Agentless scanning of workloads and VMs
Detects vulnerabilities, misconfigurations, and secrets
Cloud-native security posture management (CSPM)
Prioritized risk insights
Pricing: Quote-based; depends on number of cloud accounts, workloads, features enabled.
GitLab
GitLab integrates DevOps and DevSecOps into one platform. Its security features span SAST, DAST, dependency scanning, and container security, making it an all-in-one option for teams that want simplicity.
Key highlights:
Built-in SAST, DAST, and dependency scanning
Container scanning support
Merge request–level vulnerability reporting
End-to-end DevOps + security workflows
Pricing: Free tier available; premium/enterprise plans priced per user or per seat, higher cost for more advanced security modules.
Spectral
Spectral is a developer-first security tool designed to secure codebases, configuration files, and developer environments. It focuses on secrets detection, sensitive data leakage, and IaC misconfigurations, helping teams prevent breaches before deployment.
Key highlights:
Real-time secrets detection and policy enforcement
Scans code, IaC templates, and developer environments
Detects sensitive data leaks in repos and CI/CD pipelines
Developer-friendly integration with IDEs and workflows
Pricing: Starts at $475/month for 25 contributors. A free plan exists for smaller teams.
Anchore
Anchore specializes in container image security and compliance. It helps organizations secure their software supply chain by scanning images for vulnerabilities, validating against compliance standards, and enforcing policies in CI/CD pipelines.
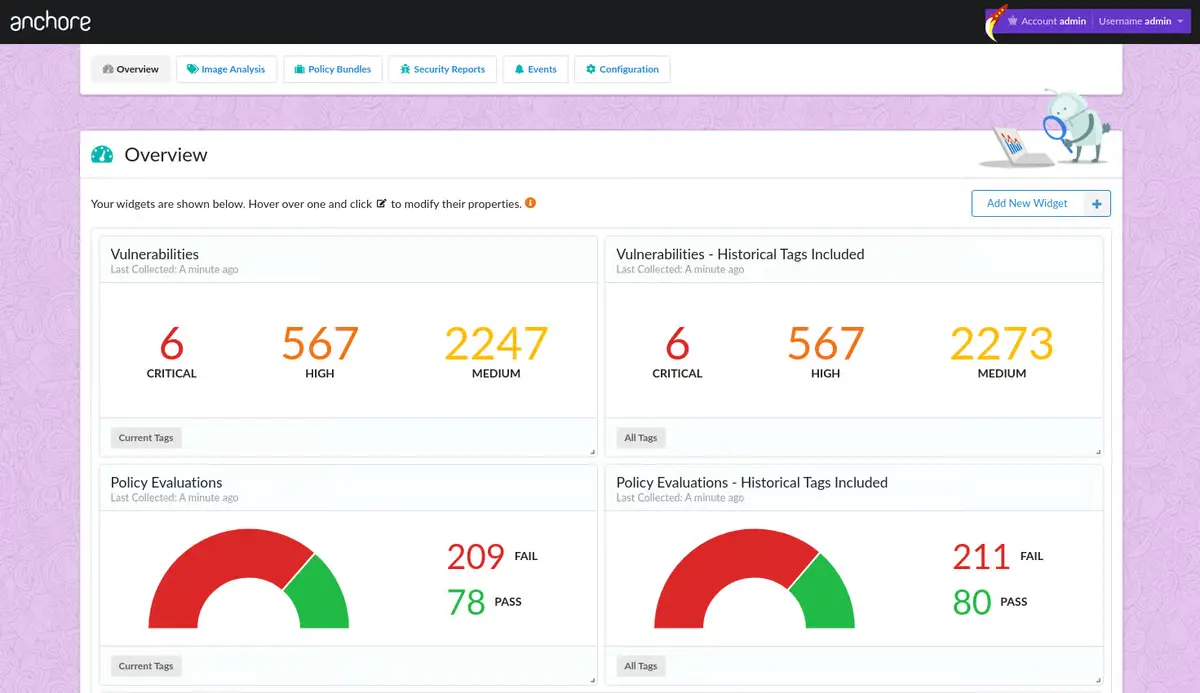
Key highlights:
Container image vulnerability scanning
Software Composition Analysis (SCA) for open-source dependencies
Image signing and policy enforcement
CI/CD pipeline integration for automated checks
Pricing: Open-source edition available for free; enterprise plans are quote-based and scale with container workloads.
SonarQube
SonarQube is one of the most widely adopted platforms for code quality and security. It combines static analysis with maintainability metrics, helping organizations catch vulnerabilities and enforce coding standards across multiple languages.
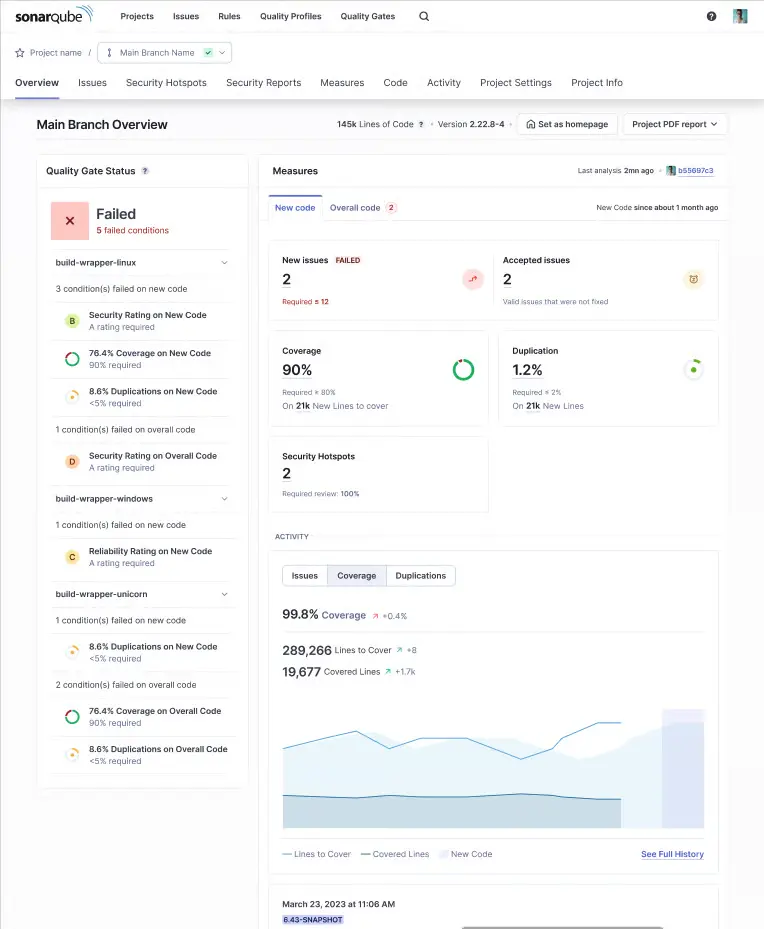
Key highlights:
Static Application Security Testing (SAST) for 20+ languages
Detection of bugs, vulnerabilities, and code smells
Quality gates to enforce secure coding standards
Team dashboards and reporting for collaboration
Pricing: Pricing starts at $32/month. They also have a community edition.
Types of DevOps Security Tools
SAST (Static Application Security Testing)
SAST tools analyze the source code, bytecode, or binaries of an application without executing it. They identify insecure coding patterns, bugs, and vulnerabilities early in the software development lifecycle (SDLC). By integrating directly into IDEs and CI/CD pipelines, they enable developers to catch issues before code is merged or deployed.
Best for: Catching security flaws in code as it’s written
Common vulnerabilities detected: Injection flaws, insecure APIs, unsafe library calls
Example tools: Semgrep, SonarQube
DAST (Dynamic Application Security Testing)
DAST tools test applications from the outside in, simulating real-world attacks while the application is running. Unlike SAST, they don’t need access to the source code. They help detect vulnerabilities that appear only in execution, such as authentication bypasses or logic flaws.
Best for: Validating security of web applications and APIs in staging or production
Common vulnerabilities detected: SQL injection, cross-site scripting (XSS), broken authentication
Example tools: Beagle Security, Invicti
SCA (Software Composition Analysis)
Modern applications rely heavily on open-source libraries and third-party components. SCA tools scan these dependencies to detect known vulnerabilities (CVEs), licensing risks, and outdated packages. With supply chain attacks on the rise, SCA is now essential to reduce dependency-related risks.
Best for: Managing risks from open-source components and external dependencies
Common vulnerabilities detected: Outdated packages with CVEs, license conflicts, risky dependencies
Example tools: Trivy, Anchore
IaC (Infrastructure as Code) Security
IaC security tools analyze configuration files like Terraform, CloudFormation, and Kubernetes manifests. They ensure infrastructure is provisioned securely and prevent misconfigurations before deployment. This is critical as cloud misconfigurations remain one of the top causes of data breaches.
Best for: Preventing insecure cloud configurations at the commit stage
Common issues detected: Open storage buckets, weak IAM policies, unencrypted data flows
Example tools: Checkov, Spectral
Secrets management and detection
Secrets management tools prevent sensitive credentials (API keys, tokens, passwords) from leaking into source code or logs. Secrets detection platforms continuously scan repositories, pipelines, and environments to catch accidental exposure, while secrets vaults securely manage credentials.
Best for: Preventing credential leaks and reducing the blast radius of breaches
Common issues detected: Hardcoded API keys, leaked access tokens, credentials in Git history
Example tools: GitGuardian, Spectral
Container and cloud Security
Container and cloud security platforms provide visibility and protection for cloud-native workloads. They scan container images for vulnerabilities, monitor Kubernetes clusters, and enforce compliance across AWS, Azure, and GCP. Advanced platforms also offer runtime detection and prioritization.
Best for: Enterprises running Kubernetes and multi-cloud environments
Common risks detected: Vulnerable container images, misconfigured cloud services, runtime threats
Example tools: Wiz, Anchore
The bottom line
DevOps without security is a risk multiplier. In 2025, organizations must embed security tools across the SDLC to keep pace with attackers.
Beagle Security stands out as the best DAST solution for web apps and APIs, with its AI-driven approach and developer-friendly reporting.
Semgrep, Trivy, and Checkov are excellent for securing code, dependencies, and infrastructure before deployment.
GitGuardian, Wiz, and GitLab ensure secrets, cloud workloads, and DevOps workflows are continuously protected.
The right combination of these tools depends on your stack, scale, and maturity. But what’s clear is that DevOps security is the foundation of resilient software delivery in 2025.
![Top 10 SDLC tools [2025] Top 10 SDLC tools [2025]](/blog/images/blog-banner-three-cover.webp)


![Best rated DAST tools [2025] Best rated DAST tools [2025]](/blog/images/top-rated-dast-tools-cover.webp)