
What is XML Injection?
XML Injection is an injection attack technique used to manipulate or compromise the logic of an XML application or document. It occurs when user-supplied input is not properly escaped or sanitized before being added to a web application’s XML documents.
The injected data will be processed and then executed, which completes the attack.
Different Types of XML Injection Attacks
There are several types of attacks that comes under this category of attack:
1. XML Entity Expansion (XEE)
XML Entity Expansion injection attacks are performed by taking advantage of a vulnerability in the XML specification that allows XML documents to define entities that reference other entities defined within the document.
2. XML External Entity
In XML External Entity injection, attacks are performed by exploiting an application’s ability to process user-supplied XML documents without disabling external resource references. XML parsers usually allow external references by default, even though they are rarely used by applications normally.
3. XPath Injection
XPath injection is a type of XML injection attack in which malicious data or commands are sent via an XPath expression to an XML document or database. By doing so, it is possible to modify or add elements to the XML enabled database or document or even perform other actions on the server.
4. Blind XPath Injection
This type of XML injection attack is employed when the attacker lacks knowledge of the XML document’s structure or when errors may be suppressed. It only allows the attacker to extract one piece of information at a time by using true/false questions (booleanized queries).
5. XQuery Injection
An attacker can add unauthorised information to your XML-enabled database or files by using a malicious XQuery input to carry out a malicious command. With the use of XML query language characters, XQL injections can access or change sensitive data that is included in your XML documents or database.
How does an XML injection attack work?
It is performed by inserting unauthorized information into existing XML files or data streams. This is done by utilizing the special characters (metacharacters such as <, >. “ and &) contained within XML documents that can be used to add or edit data or XML syntax. Usage of these characters can allow an attacker to carry out desired operations in a target server.
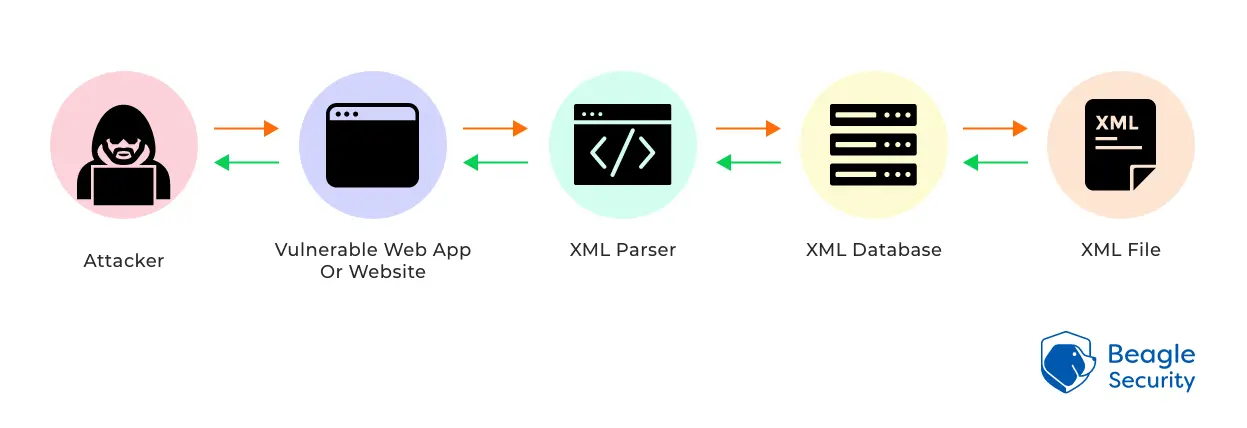
Below is a quick overview as to how this attack works, where the attacker intends to read a file on the target server:
- An attacker enters illegitimate input on a website
This is done by creating an XML query, or by uploading a malicious or improperly formatted XML document to the web application.
- This unvalidated input will either cause an error, or it will send the input into the database
Your web app server sends the malicious payload to your server and then your database for processing without having suitable parsing and validation procedures in place.
- The database then tries to process the query
Usually, the server receives information from this and responds to the query. A DoS attack could overload your XML parser if the malicious query contains information that is repeated.
- The server then responds to your query with the requested information
Typically, this means adding your desired information to the resource or sharing any information that is already present.
What is the impact of an XML injection?
XML Injection exploits are performed to compromise sensitive data from a target server. The vulnerable server can also be subject to Server-Side Request Forgery (SSRF) attacks. SSRF can be exploited if the server-side application can be forced to make HTTP requests to any URL that the server can access.
How do you find XML injection vulnerabilities in your application?
Testing needs to be performed to test for the ability to inject an XML document into your application. The vulnerabilities can be identified by using the following guidelines:
- Identify data input fields and check if metacharacters such as
<, >. “and&are allowed as input.
To identify XXE vulnerabilities, one can use the following input
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE beagle [ <!ELEMENT beagle ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<beagle>&xxe;</beagle>
This test can crash the web server (on a UNIX system), if the XML parser attempts to substitute the entity with the contents of the /dev/random file.
How to remediate an XML injection?
Before putting user input into an XML file or SOAP message, the application should validate or sanitise it. Any input that contains XML metacharacters like <, <. “ and &may be blocked. Alternatively, these characters can be replaced with the corresponding entities: < and >.


![Acunetix vs Nessus: Which is right for you? [2026] Acunetix vs Nessus: Which is right for you? [2026]](/blog/images/acunetix-vs-nessus-which-is-right-for-you-2026-cover.webp)
![OpenVAS vs Nessus: Which is the best choice for you? [2025] OpenVAS vs Nessus: Which is the best choice for you? [2025]](/blog/images/openvas-vs-nessus-which-is-the-best-choice-for-you-2025-cover.webp)


![Top enterprise application security tools [2026] Top enterprise application security tools [2026]](/blog/images/blog-banner-four-cover.webp)
![Top vendor application security testing tools [2026] Top vendor application security testing tools [2026]](/blog/images/blog-banner-six-cover.webp)
![Best API security tool for developers [2026] Best API security tool for developers [2026]](/blog/images/blog-banner-five-cover.webp)

![Top Bright Security alternatives [2026] Top Bright Security alternatives [2026]](/blog/images/blog-banner-one-cover.webp)