Story
Susan was found dead in her apartment. The investigation officer found a thumb drive from the crime scene. On examining the thumb drive, the officer found some images of food items are arranged in a particular order. This made him suspicious. “Your task is to help him decode the images.”
Solution
We have sent you a zip file that contains a set of folders of images with names ‘if_you_need_use_me’ and ‘predict_me’.
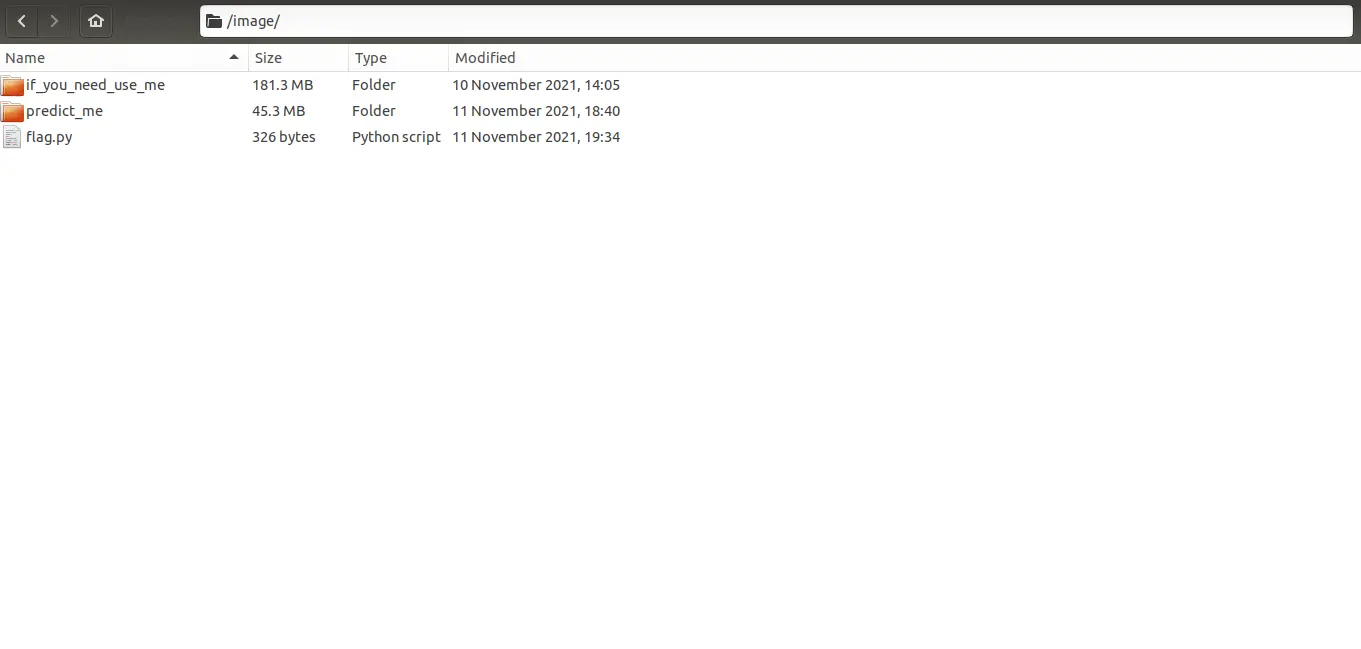
In the folder ‘if_you_need_use_me’, there will be 2 folders named ‘Dessert’ and ‘Soup’.

Each folder (DESSERT and SOUP) contains 2000 images that can be used for the training process. The ‘predict_me’ folder contains 1000 images of dessert and soups.
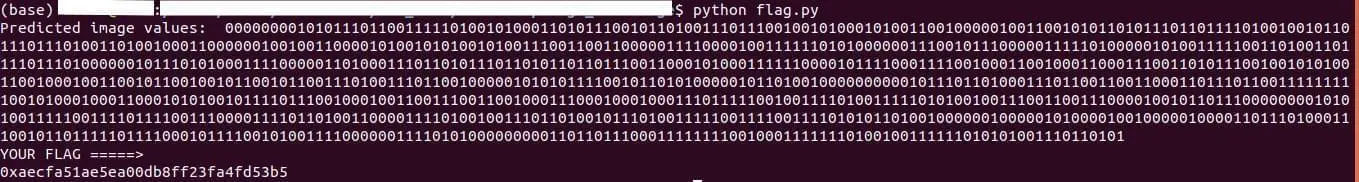
To get the flag, predict the images in the ‘predict_me’ folder correctly without changing the image order and feed it to the python file ‘flag.py’.

On giving a look at the images in the ‘predict_me’ folder, we can see the presence of two kinds of data (images of desserts and soups) forming a binary classification problem.
The sequence of dessert and soup is forming a message. Say that desserts are 1 and soups are 0.
In order to capture the flag, you have two choices:
Find a training model to predict these images
Train a model yourself
In order to train the models, you may search for online tutorials on binary classification.
After reducing each image to 0 or 1, you will get a sequence of bytes as a string by feeding the predicted bits to the python file ‘flag.py’ which will show you the flag.
Output: