Story
We came across a leaked binary executable used by the Roscosmos to communicate with International Space Station. But it seems the executable is keeping on crashing.
Your mission is to find a way around it.
Solution
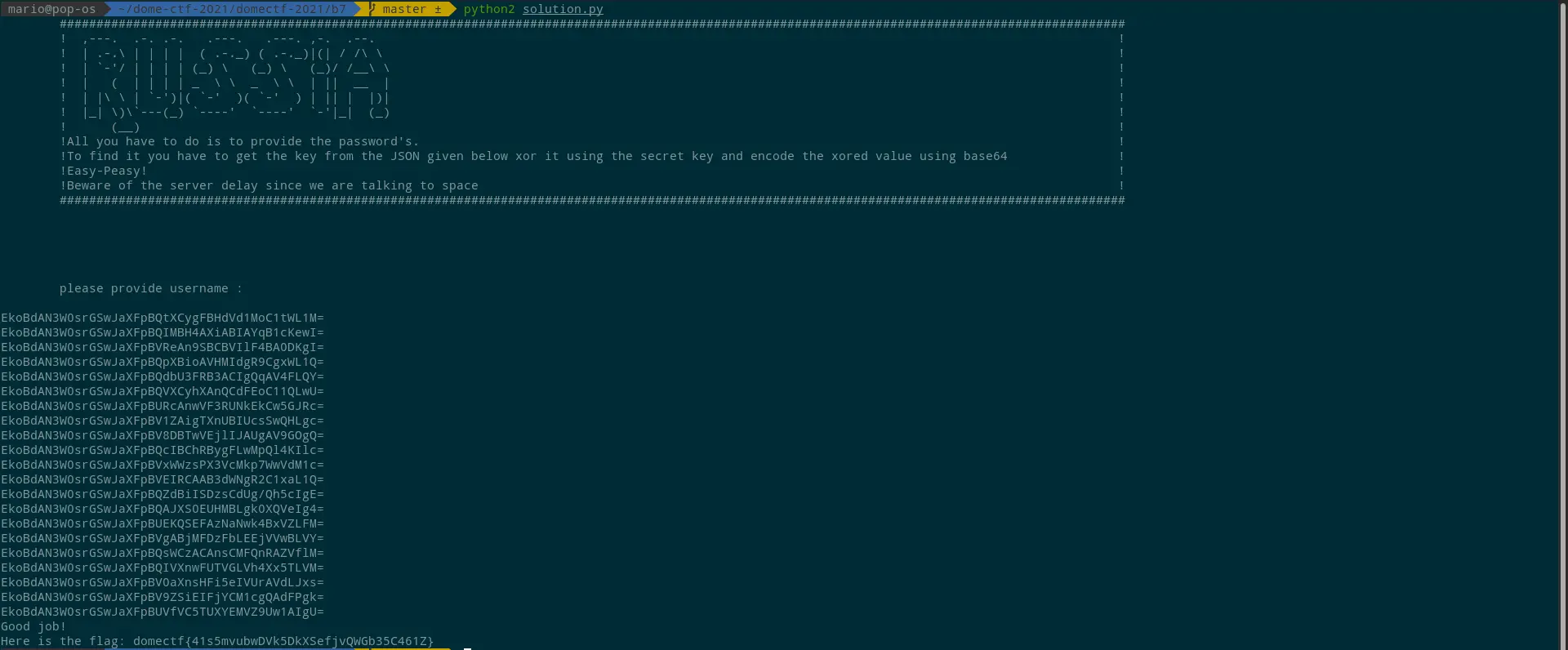
On executing the provided executable, they will ask you to input the country’s name.
Since Russia is the country where the challenge is hosted, we should add it as the country.
Once it is given, the application crashes and won’t exit, as shown below.

On capturing the network traffic using Wireshark, we can observe a connection from the local machine to a Public IP 158.85.213.163 with port 31337.
And on connecting the server using Netcat, a banner with instructions is given, which asks to enter the username.
Once the username ‘kipchoge’ (from “Hello kipchoge” in the first prompt) is given, the server returns a JSON, as shown below.
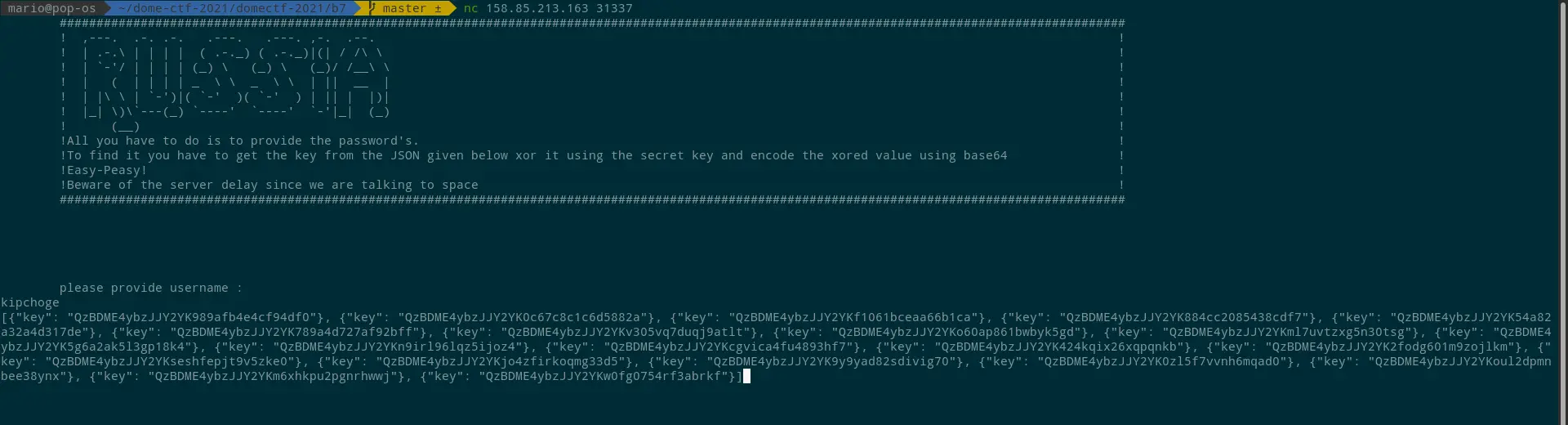
On inspecting the values in JSON, every value has a common string as the first part.
For example:
The value QzBDME4ybzJJY2YK989afb4e4cf94df0 can be separated into two parts, each 16-bit string. And QzBDME4ybzJJY2YK is the same for all the 20 values provided in the JSON.
This string is a base64 encoded string. On decoding this, you will get a value, C0C0N2o2Icf, which is the secret key mentioned in the banner.
For the sake of time, let us keep that aside.
As per the instruction given in the banner, “to find the password, you need to get the key from the JSON given below, and XOR it using the secret key, and then encode the XORed value to base64.”
Given below is the python script to do both the functions and send it over to the server.
#!/usr/bin/env python
from itertools import izip, cycle
import base64
jsonf = [
{"key": "QzBDME4ybzJJY2YK989afb4e4cf94df0"},
{"key": "QzBDME4ybzJJY2YK0c67c8c1c6d5882a"},
{"key": "QzBDME4ybzJJY2YKf1061bceaa66b1ca"},
{"key": "QzBDME4ybzJJY2YK884cc2085438cdf7"},
{"key": "QzBDME4ybzJJY2YK54a82a32a4d317de"},
{"key": "QzBDME4ybzJJY2YK789a4d727af92bff"},
{"key": "QzBDME4ybzJJY2YKv305vq7duqj9atlt"},
{"key": "QzBDME4ybzJJY2YKo60ap861bwbyk5gd"},
{"key": "QzBDME4ybzJJY2YKml7uvtzxg5n30tsg"},
{"key": "QzBDME4ybzJJY2YK5g6a2ak5l3gp18k4"},
{"key": "QzBDME4ybzJJY2YKn9irl96lqz5ijoz4"},
{"key": "QzBDME4ybzJJY2YKcgvica4fu4893hf7"},
{"key": "QzBDME4ybzJJY2YK424kqix26xqpqnkb"},
{"key": "QzBDME4ybzJJY2YK2fodg601m9zojlkm"},
{"key": "QzBDME4ybzJJY2YKseshfepjt9v5zke0"},
{"key": "QzBDME4ybzJJY2YKjo4zfirkoqmg33d5"},
{"key": "QzBDME4ybzJJY2YK9y9yad82sdivig70"},
{"key": "QzBDME4ybzJJY2YK0zl5f7vvnh6mqad0"},
{"key": "QzBDME4ybzJJY2YKoul2dpmnbee38ynx"},
{"key": "QzBDME4ybzJJY2YKm6xhkpu2pgnrhwwj"},
{"key": "QzBDME4ybzJJY2YKw0fg0754rf3abrkf"}
]
def xor_crypt_string(data, key = 'C0C0N2o2Icf', encode = False, decode = False)
if decode:
data = base64.decodestring(data)
xored = ''.join(chr(ord(x) ^ ord(y)) for (x,y) in izip(data, cycle(key)
if encode:
return base64.encodestring(xored).strip()
return xored
ADDRESS = '158.85.213.163'
PORT = 31337
TIME_TO_WAIT = 0.60
import socket, time
clientsocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
clientsocket.connect((ADDRESS,PORT))
buf = clientsocket.recv(4096).decode()
print(buf)
clientsocket.sendall('\n'.encode())
for item in jsonf:
value = item["key"]
val = xor_crypt_string(value, encode = True)
print(val)
clientsocket.sendall(val.encode())
time.sleep(TIME_TO_WAIT)
print(clientsocket.recv(128).decode())
By giving the encoded values, the server will provide the flag, as shown below.