
A remote code execution (RCE) attack allows an attacker to run malicious code on an organization’s computers or network. This capability can be exploited for numerous purposes, such as deploying additional malware or stealing sensitive data.
RCE is caused by attackers creating malicious code and injecting it into the server via input points. The server unknowingly executes the commands, and this allows an attacker to gain access to the system.
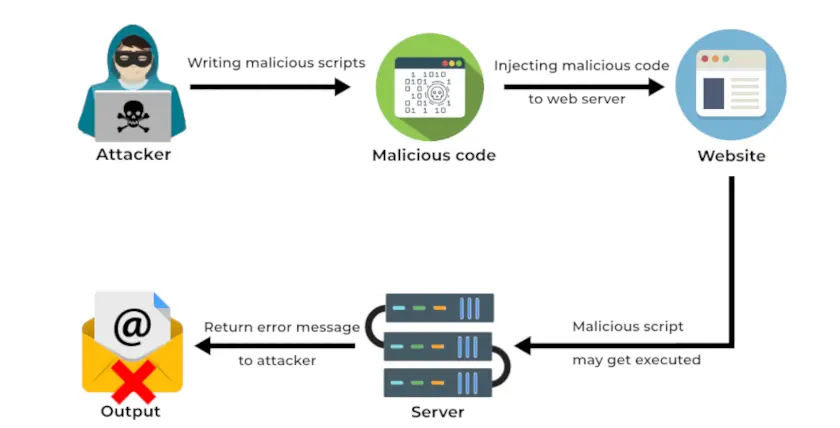
After gaining access, the attacker might try to escalate privileges. This can completely compromise a vulnerable system.
Source code from third-party applications, libraries, and plugins might be utilizing functions prone to RCE vulnerability.
Types of RCE vulnerabilities
There are several RCE vulnerabilities. Each of these vulnerabilities poses a serious threat to the security of an application, potentially allowing attackers to take full control of the system remotely.
1. Injection vulnerabilities
- SQL injection or Command injection: These vulnerabilities arise from inadequate input sanitization. If an attacker provides specially crafted malicious input, some of the data can be interpreted as executable commands, allowing the attacker to run their code on the vulnerable system.
2. Insecure deserialization
- Serialization: This process simplifies data transmission by packing it into a single string of bits for unpacking by the recipient system. If the structure of serialized data is poorly defined, an attacker can craft an input that is misinterpreted during unpacking. This misinterpretation can lead to code execution, depending on how the data is processed and stored.
3. Out-of-bounds write
- Buffers: Fixed-size memory allocated to store data can be exploited if data reads or writes are insecure. An attacker can place data outside the buffer’s intended boundaries, where it may be interpreted as executable code or critical control flow information.
4. File management
- File uploads: Applications that allow users to upload files to a server can be exploited if attackers upload files containing malicious code. The attacker can then trick the application into executing this code.
What are the impacts of RCE vulnerabilities?
Remote Code Execution (RCE) vulnerabilities can have severe impacts on both the security and functionality of a system. Some of the key impacts include:
1. Malware deployment
Attackers can use RCE vulnerabilities to deploy various types of malwares, such as ransomware, spyware, or trojans. This malware can further compromise the system, encrypt data for ransom, steal sensitive information, or provide a backdoor for ongoing access.
2. Data breach and theft
RCE vulnerabilities can be exploited to access, steal, or corrupt sensitive data. This can include personal identifiable information (PII), financial data, intellectual property, and other confidential information, leading to significant financial and reputational damage.
3. System compromise
By executing malicious code, attackers can gain control over the compromised systems. This control can be used to alter system settings, install additional malicious tools, or disrupt normal operations.
4. Denial-of-Service (DoS) attacks
Attackers can exploit RCE vulnerabilities to perform DoS attacks, either by directly executing code that overloads system resources or by deploying malware designed to flood the system with traffic, rendering services unavailable.
5. Lateral movement
Once inside a network, attackers can use RCE vulnerabilities to move laterally, compromising additional systems and expanding their control and access across the network. This can lead to a more extensive breach and greater damage.
6. Financial loss
Organizations may face significant financial losses due to RCE attacks. This can include costs associated with incident response, system restoration, legal fees, regulatory fines, and potential loss of business due to downtime and damaged reputation.
7. Reputational damage
A successful RCE attack can damage an organization’s reputation, leading to loss of customer trust and confidence. This can have long-term effects on business relationships and market position.
8. Operational disruption
RCE vulnerabilities can disrupt normal business operations by causing system outages, data corruption, and service interruptions. This disruption can affect productivity, customer service, and overall business continuity.
In short, RCE vulnerabilities pose a critical threat to the security and functionality of systems and networks. The ability of attackers to execute arbitrary code remotely can lead to extensive damage, from financial and reputational loss to operational disruption and legal consequences.
How can you prevent remote code execution (RCE) vulnerabilities?
Preventing remote code execution (RCE) vulnerabilities involves implementing a combination of best practices, security measures, and proactive monitoring. Here are key strategies to prevent RCE vulnerabilities:
1. Input validation and sanitization
Validate inputs: Ensure that all inputs from users are strictly validated against expected formats and ranges.
Sanitize inputs: Cleanse input data to remove or neutralize any potentially malicious content. Use libraries and frameworks that automatically handle input sanitization.
2. Use secure coding practices
Parameterize queries: Use parameterized queries for database interactions to prevent SQL injection attacks.
Avoid Eval: Avoid using Eval or similar functions that execute code dynamically, as they can be exploited if fed with malicious input.
Least privilege principle: Implement the least privilege principle by granting minimum required access permissions to users and processes.
3. Regular patching and updates
Update software: Keep all software, libraries, and dependencies up to date with the latest security patches and updates.
Patch management: Implement a robust patch management process to ensure timely application of security patches.
4. Secure deserialization
Validate deserialization: Ensure that only trusted data is deserialized. Validate and enforce strict schemas for serialized data.
Use safe libraries: Use libraries and frameworks that offer safe serialization and deserialization mechanisms.
5. Memory safety
Buffer management: Implement proper buffer management techniques to prevent buffer overflows and out-of-bound writes.
Memory safe languages: When possible, use memory-safe programming languages that inherently protect against common memory-related vulnerabilities.
6. Secure file handling
File upload security: Validate and restrict file types that can be uploaded. Use secure locations and permissions for storing uploaded files.
Execute permissions: Disable execute permissions on directories where user-uploaded files are stored.
7. Use Web Application Firewalls (WAF)
- Deploy a WAF to filter and monitor HTTP requests for malicious patterns and payloads, helping to block attempts to exploit RCE vulnerabilities.
8. Implement security testing
Static analysis: Use static code analysis tools to detect and fix vulnerabilities in the source code.
Dynamic analysis: Perform dynamic application security testing (DAST) to identify vulnerabilities in running applications.
Penetration testing: Regularly conduct penetration tests to uncover and address security weaknesses.
By implementing these measures, organizations can significantly reduce the risk of RCE vulnerabilities and enhance the overall security posture of their systems and applications.





