Story
“We found a file from the city terminal office. Hackers are using this file to hack into the office. Collect the secret data from the city terminal office before it ends up in the wrong hands.”
Solution
The participant is given an executable and image of Secretariat of Kerala which is situated in Trivandrum.
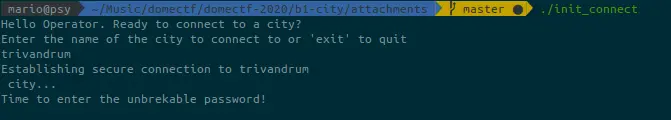
While running the init_connect file, the program asks to enter the city name which is Trivandrum. Upon giving the city name, the program connects to the city server and asks for the unbreakable password.
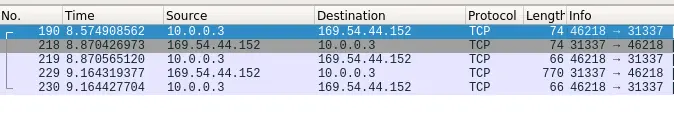
Inspecting the packets from the machine we will come to see that a connection is made to the IP 169.54.44.152:31337.
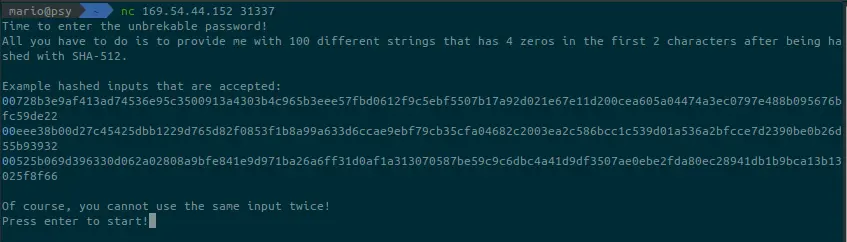
Connecting to the server using Netcat, instructions are given as banner. As the password, we have to give 100 strings that are hashed with SHA-512 and always having 4 zero’s as the first two characters. We have to write a script for that.
The working solution is given below.
#!/usr/bin/env python
ADDRESS = '169.54.44.152'
PORT = 31337
TIME_TO_WAIT = 0.05
import socket, hashlib, random, time
def generate():
string = ''
for i in range(random.randint(20,100)):
string += chr(random.randint(97,122))
return string
try:
clientsocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
clientsocket.connect((ADDRESS,PORT))
buf = clientsocket.recv(4096).decode()
print(buf)
clientsocket.sendall('\n'.encode())
for i in range(100):
buf = clientsocket.recv(128).decode()
print(buf,end='')
while True:
value = generate()
if '\n' in value:
pass
elif hashlib.sha512(value.encode('utf-8')).hexdigest()[:2] == '00':
break
print(value)
clientsocket.sendall(value.encode())
time.sleep(TIME_TO_WAIT)
print(clientsocket.recv(128).decode())
except socket.error as e:
print('Cannot connect')
except Exception as e:
print(e)
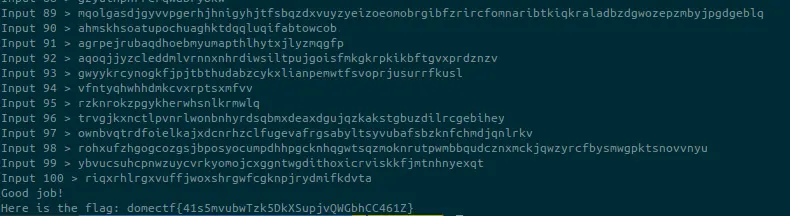
After providing 100 strings the server will display the flag.