
Story
A new case of Wadiya’s national security arrived at Michael’s table. According to the intelligence report, they used this website to share some national secret. What is the secret?
Solution
Some lines of HTML are commented in “contact.html”. The user needs to analyse the code and find something in the javascript code.
In javascript, there is a “contact.js” file which is different from others.
But the javascript file is minified and there is some code commented.
You can uncomment and unminify using https://www.unminify2.com/
In javascript code
$("#contact_form").each(function(){
$.get( "requestcheckout.php", function( data ) {
$( ".result" ).html( data );
output = '<div class="error">'+response.text+'</div>';
});
});
});
requestcheckout.php A GET API call to the backend so we can call that API using any API client.
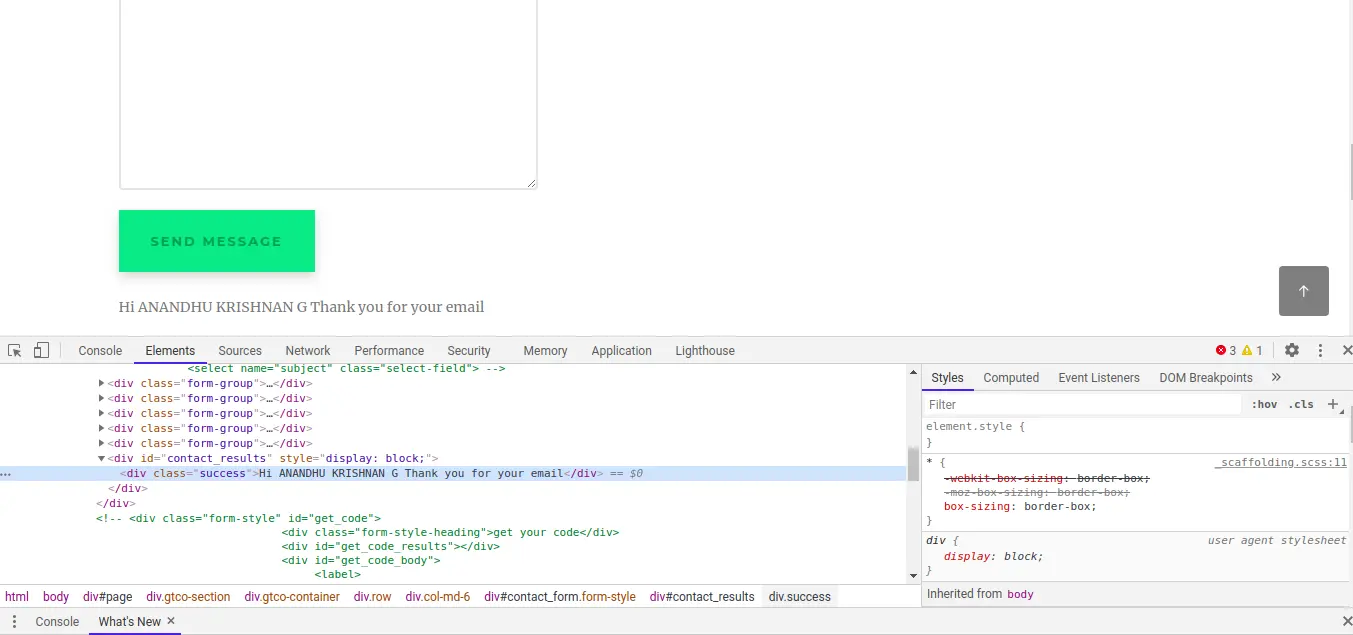
The response of that API is a .zip file. Then, the user needs to open it and it will show some error.
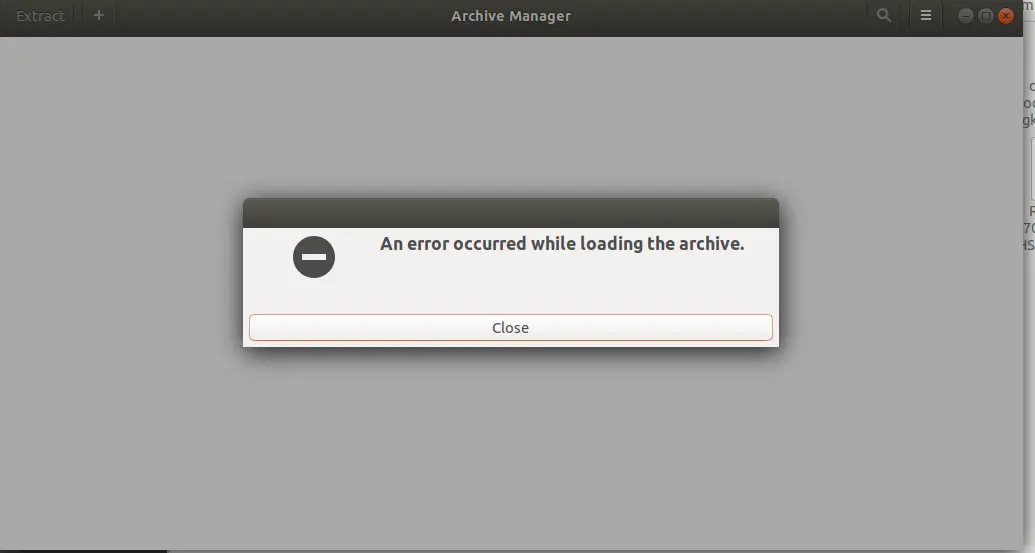
So something is missing. Open that file in any hex editor.
hexedit file.zip
Zip Archive pk hex 50 4B 04 03 is in the file but it was 50 4B 03 04. Edit this value in that file and save (change magic bytes ‘5B 40 04 03’ to ‘5B 40 03 04’)
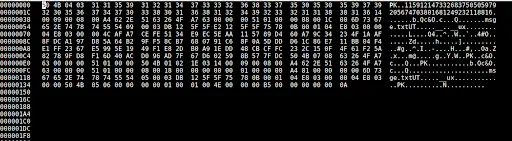
sudo nano file2.zip

But the file is not opening so again we check with hex editor and we find a decimal string ‘115912147332683750505979205674703801681249232118816’
So when we decode the decimal string we get a hex value. When we decode the hex value we get a string - “OOps! Flag not found”
Therefore, we need to remove the decimal string.
“PK^C^D115912147332683750505979205674703801681249232118816^T^@ “ to
“PK^C^D^T^@”
After this step, the file will be open but the password is not produced. We need to find the password.
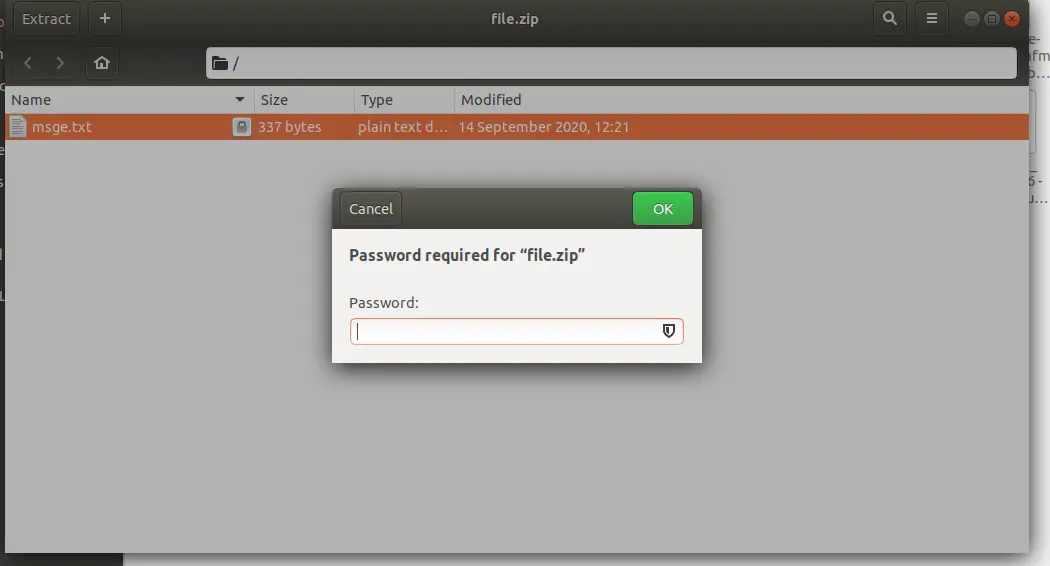
fcrackzip -u -v -D -p rockyou.txt file2.zip
After some time, PASSWORD FOUND!!!!: pw == Astra123
We can enter the password but the file:
Nb!!NN!NNN!!N!!!!N!!N!!N!N!!NN!N!N!!NNN!!N!!!N!NNN!!NN!!NN!!!!N!!N!!N!!N!N!!N!NNNN!!!N!NNN!!!NNNNN!!NN!N!N!!!N!!NNN!!NNN!NN!!!NNNN!!!NNNNNN!!NNNNN!!N!!N!NN!!N!!NNN!!!NNNN!!NNN!NN!!!NNN!N!!!!NNNNN!!N!!NN!NNN!!NNN!!!NNNNN!!N!!!N!NN!!!NN!N!N!!!N!!N!NNNNN!!NN!NN!NN!!!!N!!!N!!!N!!N!!N!N!NNN!!NNN!!NNN!N!NNNNN!N!!N!NNNN!!N!NN!N!!!!!N!NNNN!N!N
This value needs to be converted to binary. We need to replace ‘N’, ‘!’ with binary ‘0’, ‘1’
Python program to convert
import os
# Decode
d = "Nb!!NN!NNN!!N!!!!N!!N!!N!N!!NN!N!N!!NNN!!N!!!N!NNN!!NN!!NN!!!!N!!N!!N!!N!N!!N!NNNN!!!N!NNN!!!NNNNN!!NN!N!N!!!N!!NNN!!NNN!NN!!!NNNN!!!NNNNNN!!NNNNN!!N!!N!NN!!N!!NNN!!!NNNN!!NNN!NN!!!NNN!N!!!!NNNNN!!N!!NN!NNN!!NNN!!!NNNNN!!N!!!N!NN!!!NN!N!N!!!N!!N!NNNNN!!NN!NN!NN!!!!N!!!N!!!N!!N!!N!N!NNN!!NNN!!NNN!N!NNNNN!N!!N!NNNN!!N!NN!N!!!!!N!NNNN!N!N"
for i in range(0, len(d)):
# print("loop")
if d[i] == chr(78):
d = d.replace(d[i], '0')
if d[i] == chr(33):
d = d.replace(d[i], '1')
print(d)
binary_int = int(d, 2)
byte_number = binary_int.bit_length() + 7 // 8
binary_array = binary_int.to_bytes(byte_number, "big")
text = binary_array.decode()
print(text)
Output will be:
0b11001000110111101101101011001010110001101110100011001100111101101101101011010000111010001110000011001010111011000110001001110000111000000110000011011010011011000111000011000100111000101111000001101100100011000111000001101110100111001010111011010000011001001001111011101110110110101000110001100010100000101101000011010010111110100001010
ASCII value of the binary will be the flag: domectf{mhtpev18p0m68bqx6F87NWh2OwmF1Ahi}














