Story
Elysium faced a ransomware attack and all the server data got encrypted by the adversary. They’re asking a big ransom to carry out their plan. We’re not willing to pay the ransom but we need to get the data back.
Solution
The challenge is to decrypt the given files. In order to decrypt, you need to find a private key.
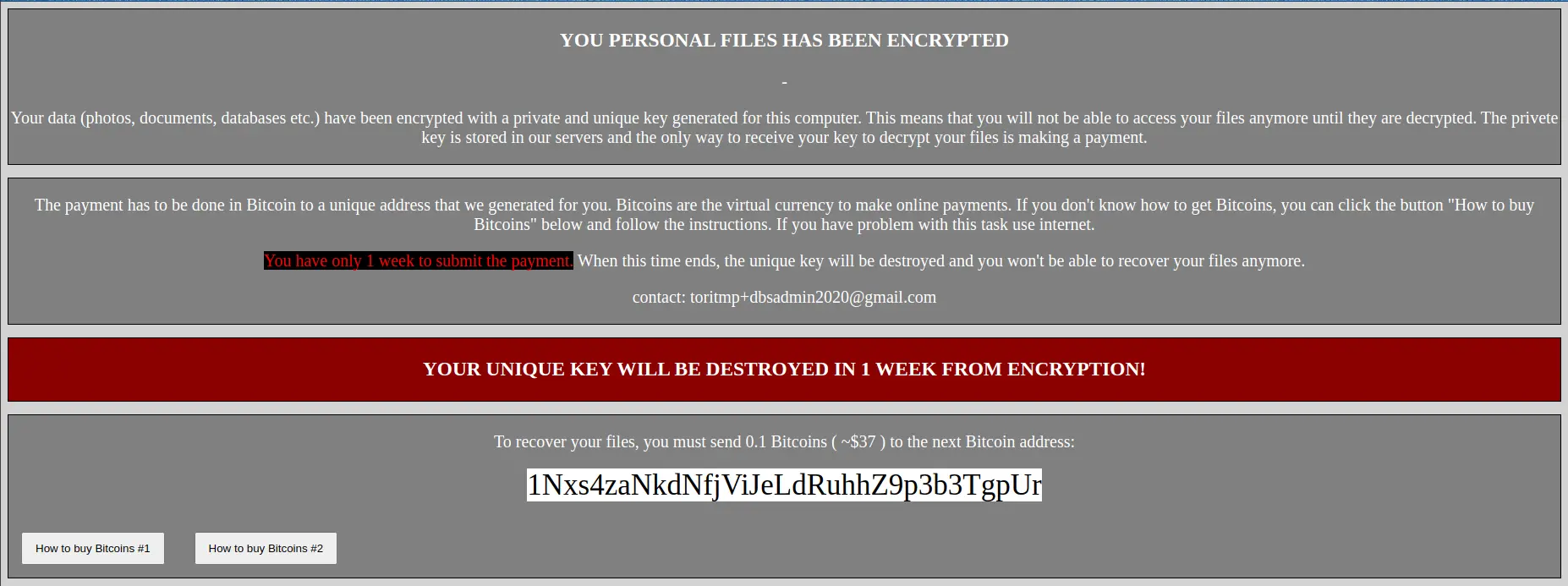
The key part of this challenge is the bitcoin address and the email id. The provided email is a temporary email address. By searching “toritmp” you can find the website that provides those temporary emails.
By accessing the mail you can see the following emails in it.
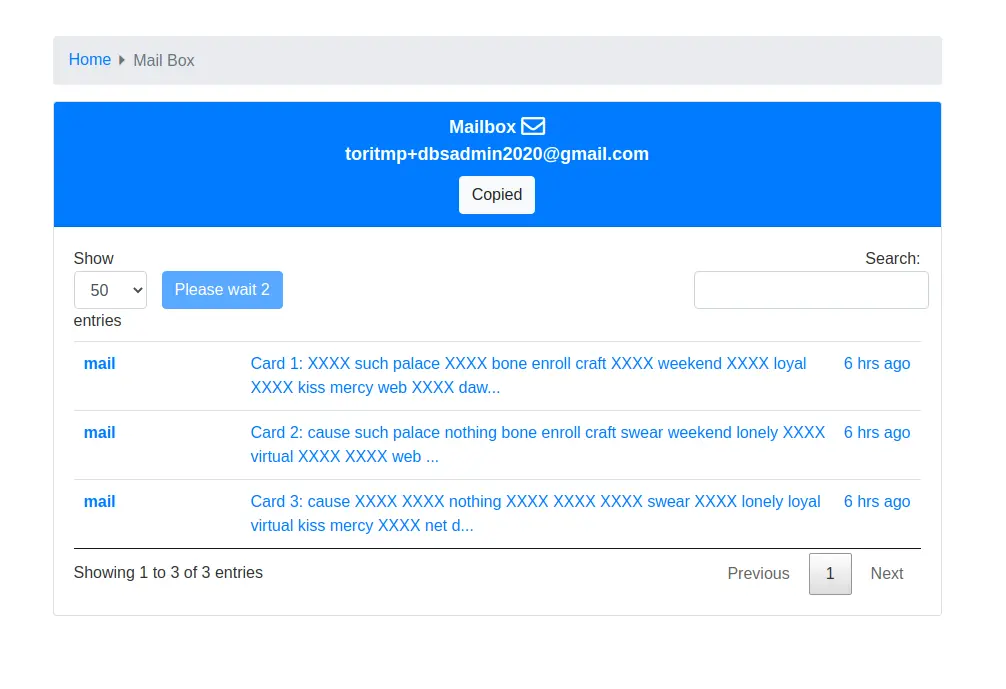
Those are BIP39 Split Mnemonic. BIP39 Mnemonic phrase is a list of words that store all the information needed for the recovery of a Bitcoin wallet. With that you can get the public key and private key of the bitcoin address.
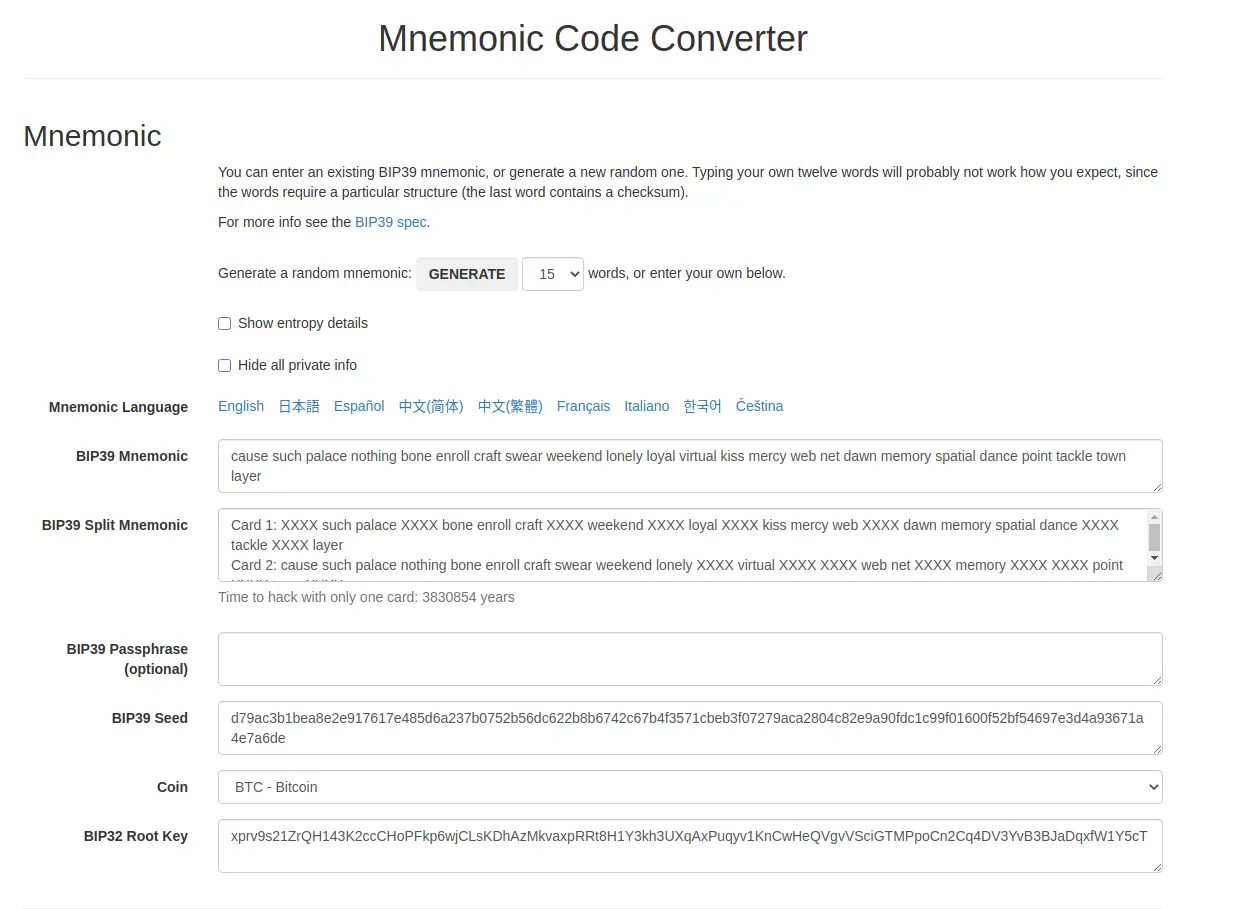
Using the site https://iancoleman.io/bip39/ will provide you the list of addresses, private key and password.
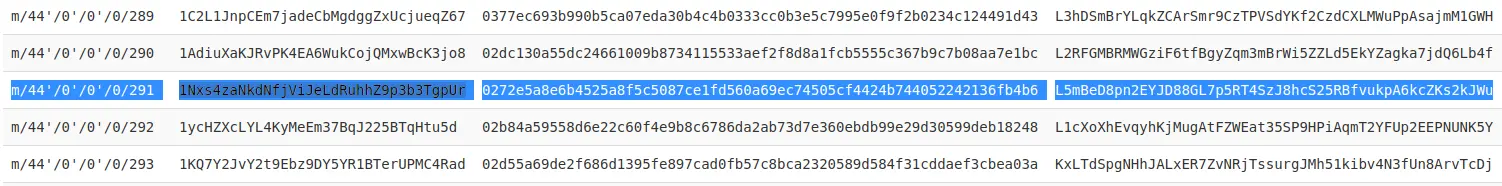
Now, we have the public key and the private key of the address.
Elliptic Curve Digital Signature Algorithm or ECDSA is a cryptographic algorithm used by bitcoin to ensure that funds can only be spent by their rightful owners.
Elliptic Curve Cryptography (ECC) can do public key encryption. Encrypted files are encrypted using ECC with the public key of the bitcoin Address. For decrypting, the private key of the bitcoin address can be used. The hint was a new generation of ransomware. Searching the hint on google will give a hint of ECC.
Using the eccrypto node module these files can be decrypted with given script:
var eccrypto = require("eccrypto");
var fs = require('fs');
async function decrypt(encryptedFileName, decryptedFileName, privateKey) {
try{
let encrypted = JSON.parse(fs.readFileSync(encryptedFileName, 'utf8'))
for (let key in encrypted) {
encrypted[key] = Buffer.from(encrypted[key],'hex')
}
let plaintext = await eccrypto.decrypt(Buffer.from(privateKey, 'hex'), encrypted)
fs.writeFileSync(decryptedFileName, plaintext);
}
catch(err){
console.log(err);
};
};
(async function () {
var myArgs = process.argv.slice(2);
// simple input sanity check
if (myArgs.length != 3) {
console.log("Usage: node decrpyt.js encryptedFileName decrptedFileName privateKey ")
process.exit(1);
}
await decrypt(myArgs[0], myArgs[1], myArgs[2])
console.log(" ")
console.log("Successfully decrypted ", myArgs[0], " into ", myArgs[1])
})()
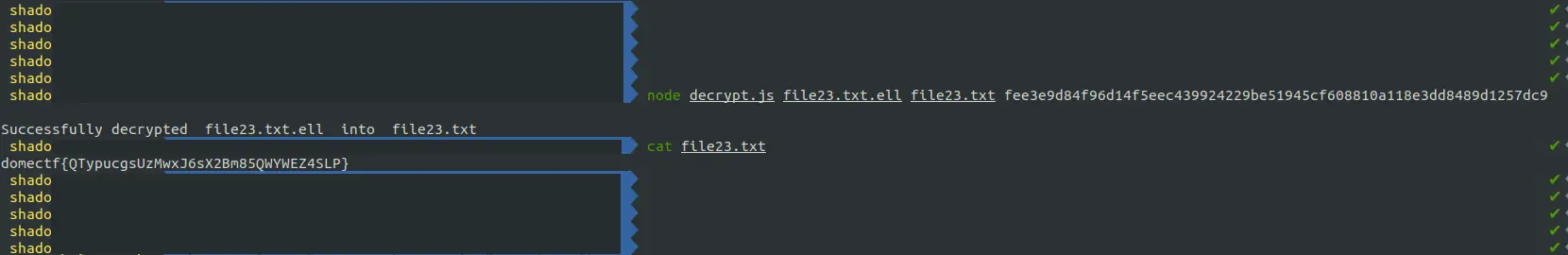
Using the bitcoin-tool, convert the private key to hex format. You will get it as “fee3e9d84f96d14f5eec439924229be51945cf608810a118e3dd8489d1257dc9”
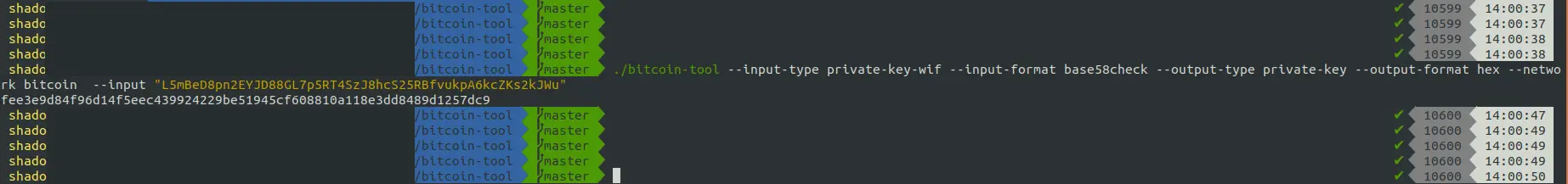
Finally, it’s time to decrypt the flag!